Decrypting files affected by ZWER ransomware might not be that simple
Contents
ZWER ransomware is a malicious virus originating from STOP/DJVU ransomware group. The malware is configured to encrypt all personal files on target Windows systems or computer networks, marking data with .zwer file extension. For example, file called document.doc will appear as document.doc.zwer after the cyber attack. In addition, the virus drops _readme.txt ransom note in every affected folder. This note contains a money-demanding message from the DJVU creators.
ZWER file virus is similar to the latest DJVU versions, such as KKLL, SQPC, MZLQ, PEZI and others. It stealthily infects the computer system, usually alongside user-downloaded software cracks or illegally obtained copyright-protected files, and displays a fake Windows update screen (created by fake winupdate1.exe process). In addition, it installs a password-stealing malware, called AZORULT, and modifies Windows HOSTS file to block access to various Internet websites. As shown by VirusTotal report, the malware executable sample was called 79e5.tmp.exe, although it might differ slightly.
If you have been infected with this virus, rush to remove ZWER ransomware virus safely. First, boot into Safe Mode with Networking, then run a system scan using malware-removal software of your choice. When it comes to virus damage repair, our top pick is RESTORO, which can fix the HOSTS file damaged by the malware.

_readme.txt note contains a message from the criminals
As described previously, ZWER ransomware aims to restrict victim’s access to personal files and force him/her to pay a ransom to retrieve such rights back. This is explained in the ransom note (_readme.txt), which contains the following message:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-gSEEREZ5tS
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoreadmin@firemail.cc
Your personal ID:
[Personal ID string]
The ransom note suggests that all files, databases and other important files are encrypted. It steals the victim’s right to open, edit, or view contents of such files instantly, causing panic for the victim. However, the criminals offer a solution – the victim needs to pay a ransom for the attackers, which supposedly should return the data.
To confirm their claims, the ransomware developers suggest testing the decryption tool. The victim can send one small encrypted .zwer file to the criminals via one of the provided emails helpmanager@mail.ch and restoreadmin@firemail.cc (or both, if desired) and wait for a response from the criminals along with a decrypted file version.
To decrypt all files, the criminals suggest purchasing a decryption key and tool for $490 if the victim contacts and pays within 3 full days. Later, the ransom price increases to $980.

We DO NOT RECOMMEND paying the ransom. Please don’t do it, or if you do, make sure it is the last option on your choice list. Remember that by paying the criminals, you encourage them to create and distribute even more malicious malware, therefore, infect even more users worldwide, and therefore make even more people miserable.
ZWER ransomware virus

Name: ZWER ransomware
Description: ZWER ransomware is a malicious virus that targets Windows operating systems. It is designed to encrypt all files on the system, mark them with .zwer extension and leave _readme.txt note, which urges paying a ransom to cyber criminals who have the data decryption tools. Once encrypted, files cannot be opened with any program. The virus also installs Azorult Trojan on the system to steal victim's login credentials saved in browsers.
Offer price: $490-$980
Currency: Bitcoin
Operating System: Windows
Application Category: Ransomware
Author: STOP/DJVU developers
-
Damage
(5)
-
Distribution
(5)
-
Encryption Strength
(5)
Overall
5User Review
( votes)Ransomware awaits in malicious online downloads or email attachments
ZWER file virus is known to be packed along illegal downloads, especially various torrents. Numerous victims have reported downloading the malicious payload along game or software cracks, also KMSPico or similar programs.
Usually, all that it takes to get infected with DJVU variants is to download a torrent and simply open it. Often times, such downloads include cracks or keygen files, which also need to be launched in order to use them. Please remember that malware can be run from almost any file time nowadays.
The files, for example, documents can leverage the possibility to use JavaScript or Macros and reference other sources, download and run files on the system. All that it takes is to trick the victim into opening a wrong file once.
There are other methods to distribute malware similar to ZWER. Another popular way of pushing file-encrypting threats to computer users includes social engineering tactics and a bit of an email spam. The criminals craft up legitimate-looking messages and attach malicious files to them, then email them to hundreds of different recipients.
Deceptive messages often ask the victim to review the attached document and reply as soon as possible. The email might suggest that the victim has a massive tax return awaiting, or that the victim has missed an important payment. Once opened, such email attachments can execute ransomware right away.
Our recommendations regarding ransomware protection are:
- Stay away from suspicious or hard-to-believe emails, even if they look like they originate from trustworthy sources. Remember that even sender’s email address can be spoofed and identifying it without certain IT knowledge can be really hard.
- Do not download illegal files or cracked software. It is one of the primary sources for malware infections.
- Use a reliable anti-malware software providing real-time protection. We recommend iolo System Mechanic Ultimate Defense for this matter.
Remove ZWER virus and protect your computer
We recommend you to remove ZWER ransomware virus before taking any further actions to protect your computer and your own privacy. Follow the instructions given below the article to boot your computer in a proper malware-removal environment and then download or run your security software. To repair virus damage done by the virus, use RESTORO.
Next, you should take proper post – ZWER file virus removal steps. We understand that your primary goal is to decrypt your files. Therefore, we explain the whole decryption process in detail at the very end of this article.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software.
REMOVE THREATS WITH ROBUST ANTIVIRUS

Get INTEGO ANTIVIRUS for Windows to remove ransomware, Trojans, adware and other spyware and malware variants and protect your PC and network drives 24/7. This VB100-certified security software uses state-of-art technology to provide protection against ransomware, Zero-Day attacks and advanced threats, Intego Web Shield blocks dangerous websites, phishing attacks, malicious downloads and installation of potentially unwanted programs.
Use INTEGO Antivirus to remove detected threats from your computer.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
ZWER ransomware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
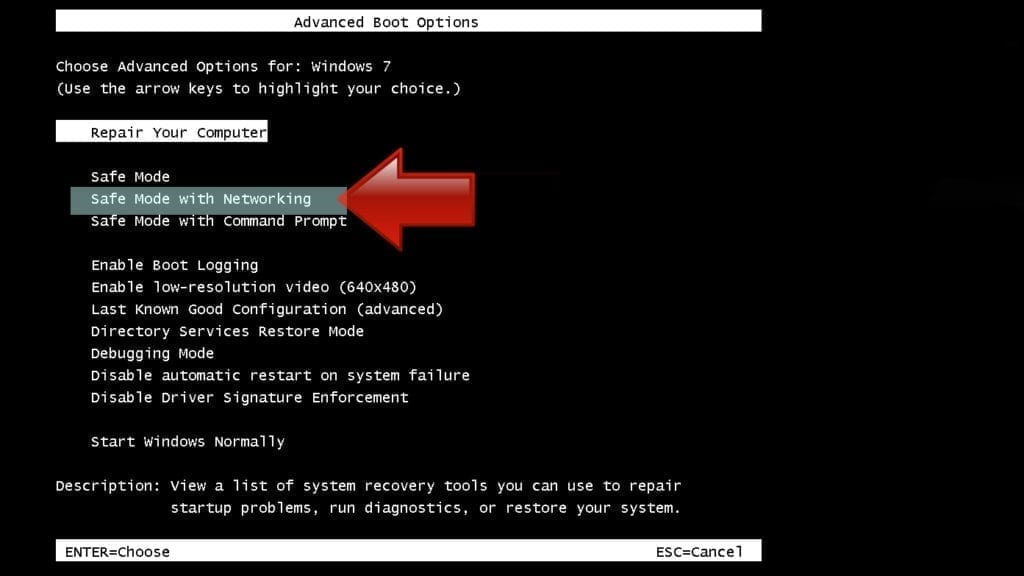
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
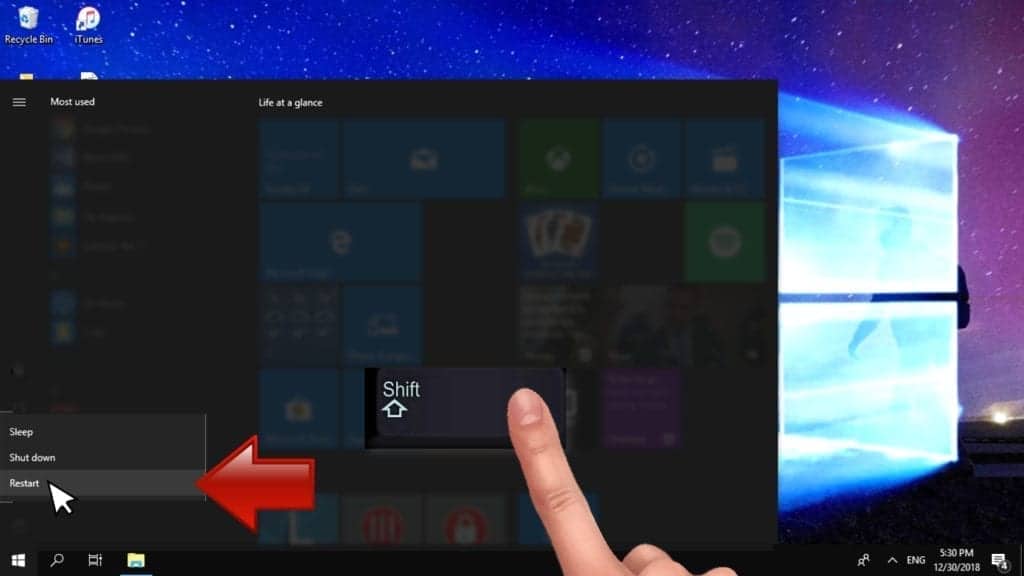
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
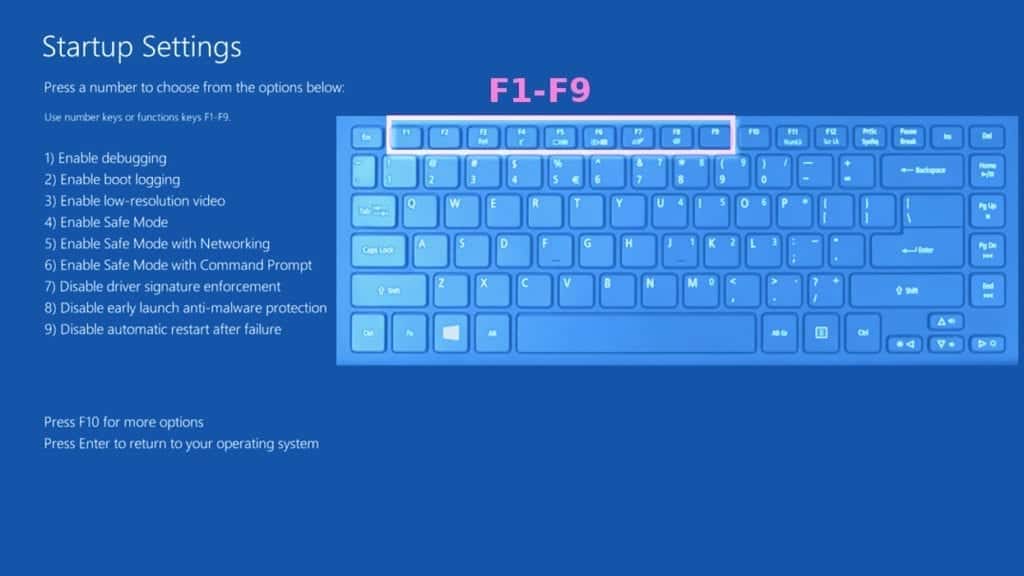
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
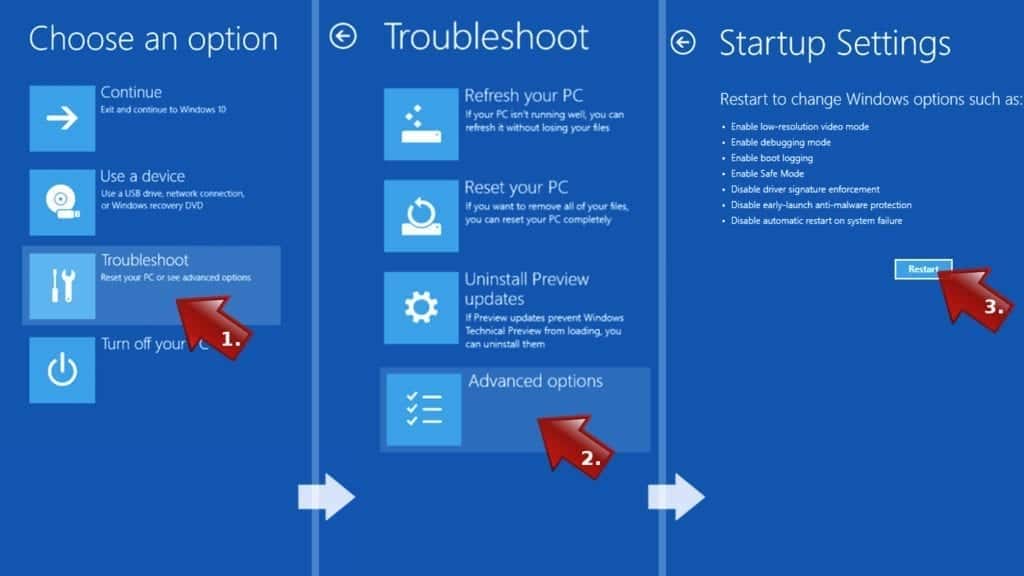
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove ZWER ransomware files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO Antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
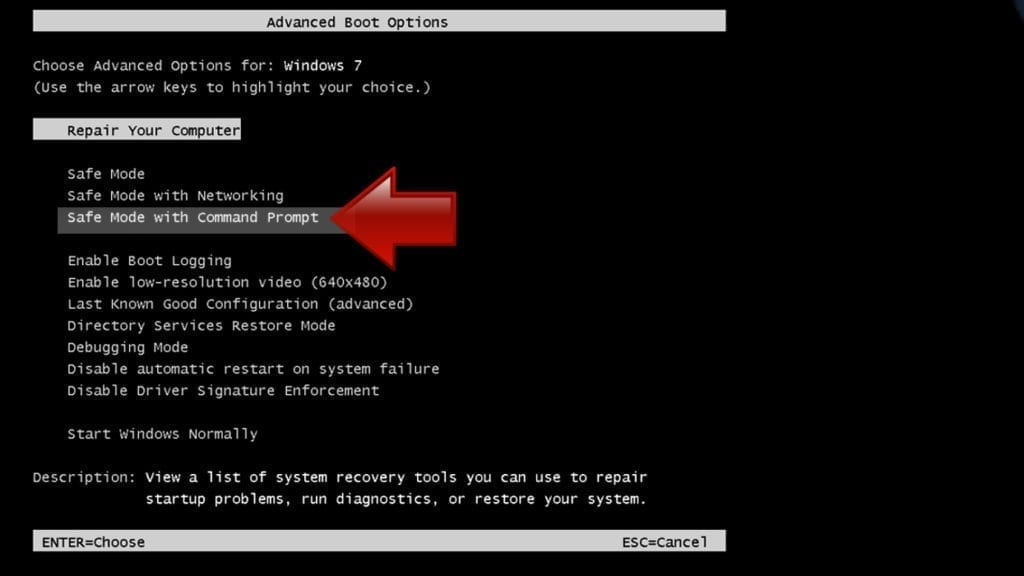
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
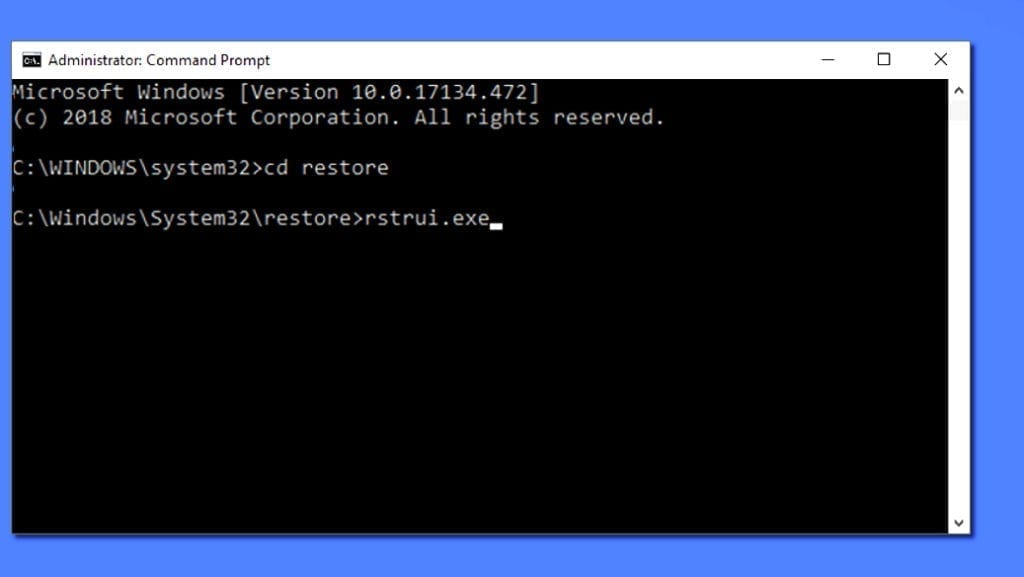
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
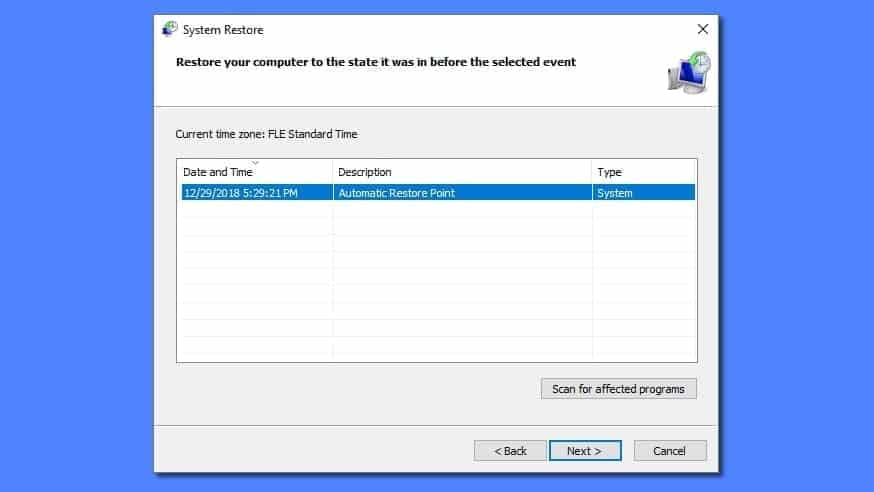
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Guide to Decrypt .ZWER Files
When it comes to data recovery, there are two categories for DJVU versions – old and new. ZWER virus is considered the new version of DJVU. What it means is that victims can now expect to recover their files ONLY if offline encryption was used.
You can read more about the whole decryption procedure in this guide, however, the easiest way to identify offline encryption is to open C:/SystemID/PersonalID.txt file on your computer. It contains an ID, which mostly ends in t1 if the offline encryption was used during the attack. In every other case, online encryption is used.
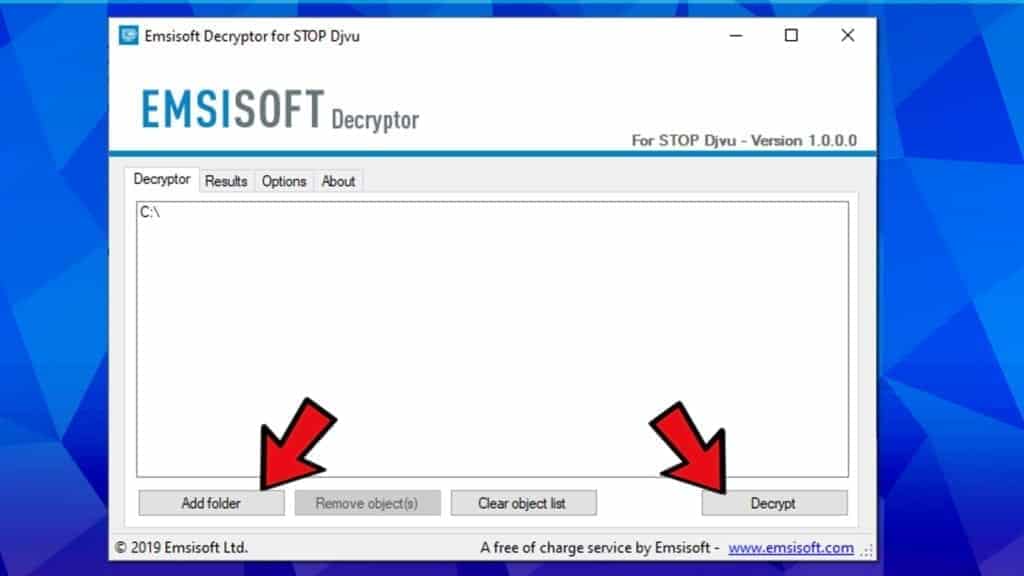
A guide on how to use STOP Decryptor, is provided below. Download the decryption tool by Emsisoft now.
- Once you have the decryptor, run it and check whether you agree to its Terms and conditions.
- Now, add a folder to decrypt, as shown in the picture. Then hit decrypt and be patient until the tool finishes its work. If your files can’t be decrypted, you will receive a message from the tool.
IMPORTANT. The ZWER decryption tool might show certain responses after you attempt to use the decryptor. Check the failure responses, and their meanings, below.
Result: No key for new variant offline ID: [ID]
This ID appears be an offline ID. Decryption may be possible in the future.
If you see this message, it informs about OFFLINE .zwer file virus encryption case, which means that your encryption/decryption pair matches with any other victim affected by offline encryption.
To put it differently, offline encryption is used when the virus fails to obtain individual, and unique key pair from its command&control server. Therefore, once one victim pays the ransom and shares the obtained key with Emsisoft’s researchers, the decryptor will be updated. In short, if you received this message, do not delete your files and stay patient. Check for updates every week here and see when the tool becomes capable of decrypting your files.
Decryption is impossible: an online key is used.
The shown message says that your files were affected by an online encryption, or, in other words, tells you that no one else has the same encryption/decryption key pair. In such case, chances to recover files without paying are close to zero. In fact, the only possible scenario is if the criminals get caught and their computers/servers seized; or if they disclose the decryption keys willingly. None of these scenarios are likely to happen. Therefore, online encryption victims should rely on data backups only.
Frequently Asked Questions
You can only decrypt .zwer files by using a decryption tool, but you need to have a decryption key to do so. The key is held by cyber criminals, who demand ransom payment. Alternative way to recover your files is to use STOP Decrypter by Emsisoft, or use data backups.
ZWER virus is a new STOP/DJVU variant. For the offline decryption key to be added to the decryptor software, one victim affected by the offline encryption has to pay the ransom and share the received keys with Emsisoft’s developers. This might take some time to happen. What is more, the decryptor operators might not upload the key instantly to keep the victim who disclosed the key anonymous. In other words, please stay patient and check for updates.
There is no way to open these files until they are decrypted. To decrypt your files, you need to run STOP Decrypter. If it won’t recover your files, check the message that it shows, whether you were affected with online or offline encryption. If you’re affected by online encryption, there are no chances to recover your files without paying.
We provide a free ZWER virus removal guide and explain the chances to recover your files, and how to identify the encryption type. For more details about the encrypted data recovery, please read this guide: Decrypt files locked by STOP/DJVU ransomware variants.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
were you able to decrypt the files that were infected with the virus?
Mangird , which way were you used exactly? Did you pay for some of tool that mentioned here? Which one?
Thank you!!! I have managed to clean my system successfully using your recommended tool.