AZORult malware analysis: highly dangerous threat
Contents
AZORult is a malicious program which is categorized as a Trojan virus. In the past it was known to be based on Delphi programming language but later on it was redeveloped using C++ (AZORult++). Its main purpose is to collect various personal data, which is later used to gain certain benefit at victim’s expense, typically financial. Usually this virus spreads through spam email campaigns. These emails contain deceitful information to trick users into opening/downloading attached files. The files may come in various formats, even MS Office documents, therefore they might seem harmless. As soon as you open them, attachments execute certain commands which penetrate the virus into your system.
Malicious functionality explained
Immediately after the opening of the file, AZORult malware is installed into your system. This Trojan-Spyware develops a connection between its C&C (“command and control”) servers and your system – this linkage is used to leak your information later on. This virus is capable of stealing various data from victim’s computer, including, but not limited to:
Data that AZORult stealer is capable of capturing:
- Account information used in different File Transfer Protocol clients or file manager software;
- Machine’s globally unique identifier (GUID), also details about victim’s computer (system language, user name, OS version, installed software, etc.);
- Email credentials from all victim’s mail clients;
- Bitcoin wallets, including, but not limited to Monero or uCoin;
- Whole variety of usernames, passwords and hostnames from your browsers;
- Steam or Telegram login details;
- Recording, taking Skype screenshots, chat history, and the list goes on.

It is worth mentioning that redeveloping AZORult Trojan on C++ resulted in various flaws and deficiencies compared to previous versions, such as no loader functionality and no support for stealing passwords from certain browsers. In addition, researchers found flaws in virus’ string configuration but that might slipped through due to the fact, that project seems to be in early development stages – going forward, these bugs are expected to be resolved and the functionality of malware expanded.
On the other hand, the virus might be even more threatening than previous versions, since it collects stolen data in RAM instead of the hard drive, thus managing to hide its activity. It also possesses ability to establish a remote connection to the desktop by creating an additional administrator account in the system. So, this intrusion might leave ordinary user in unenviable position, since it might lead to substantial finance and private information losses. Therefore, if you suspect that your PC has been infected with this virus, remove AZORULT malware instantly. We recommend using RESTORO for repairing the mess left by the virus.
Threat Summary
| Name | AZORult malware |
| Type | Trojan; Password-stealer; Banking malware |
| Detection names | PWS:Win32/Stimilina.E!bit, W32/AutoIt.OM.gen!Eldorado, Trojan.GenericKD, Trojan-Spy.Azorult and others |
| Danger | Extremely dangerous. Steals private victim’s data such as banking details, login credentials, can execute malicious commands on victim’s computer (backdoor), install additional malware |
| Symptoms | Typically functions silently; the victim might notice changes in bank accounts or that personal accounts are no longer accessible |
| Distribution | Spreads via deceptive payment information emails containing a malicious attachment (usually a .doc or .pdf file), also arrives alongside STOP/DJVU ransomware variants and other malware |
| Removal | After virus removal, run a system scan using with RESTORO (secure download link) to repair virus damage on the system. |
How did I get infected?
As previously mentioned, the AZORult virus, just like Wacatac Trojan, typically spreads through emails and malicious files attached to them. Spam email campaign is a relatively simple social engineering construct, which is aimed at internet users who tend to read emails irresponsibly. The emails might trick the victim by really straightforward schemes (i. e. fake CV’s, business requests, offers, invoice documents, payment information requests etc.).

The fact that similar or same designs to hack internet users are being used for a long period of time means that this problem is still relevant and there are people who accidentally run into this issue. Of course, there is a chance of getting infected through other sources i. e. untrustworthy download sites, file sharing networks such as uTorrent, eMule, etc.
Any of these actions might jeopardize your system’s security. If you remember any instances of opening suspicious email attachments, or see “sAMsUNg” process in Windows Task Manager, there is a high chance that your system is infected already.
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
Trojan distributed via STOP/DJVU ransomware
AZORULT Trojan has been noticed to come as a bonus alongside DJVU ransomware variants. The ransomware, which currently has over 200 different variants, is known to hide in software cracks and keygens.
Once installed, the ransomware also downloads and runs the described password-stealer on the system. Therefore, all victims subject to this ransomware infection should check and delete the malware from their computers immediately.
The latest DJVU variants known to be distributing Azorult are KAAA, BGJS, BGZQ (find full list here).
Another known source of Azorult’s distribution is a fake coronavirus map. It appears that hackers have cloned a legitimate map created by Johns Hopkins University for malicious purposes. The fake downloadable map, instead of providing useful information about COVID-19 cases worldwide, installs a computer virus on the system instead.

It is believed that the malicious map version spreads via fake links on social media. Such social-engineering attack is extremely effective nowadays due to the panic and havoc the medical virus has caused worldwide.
Remove AZORULT malware completely
AZORULT malware removal is essential in order to protect your private data. In order to do it, you need to use trustworthy and legitimate antivirus or anti-malware software. To ensure that, we highly recommend checking out our reviews on them.
Bypass malware installation in the future by following these recommendations: browse through internet very cautiously and analyze every email, download or attachment (and its source) comprehensively before downloading/opening it. To remove AZORult stealer virus completely from your computer, follow the steps below.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software.
REMOVE THREATS WITH ROBUST ANTIVIRUS

Get INTEGO ANTIVIRUS for Windows to remove ransomware, Trojans, adware and other spyware and malware variants and protect your PC and network drives 24/7. This VB100-certified security software uses state-of-art technology to provide protection against ransomware, Zero-Day attacks and advanced threats, Intego Web Shield blocks dangerous websites, phishing attacks, malicious downloads and installation of potentially unwanted programs.
Use INTEGO Antivirus to remove detected threats from your computer.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
AZORULT malware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in Safe Mode with Networking, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to start Windows in Safe Mode:
Instructions for Windows XP/Vista/7 users
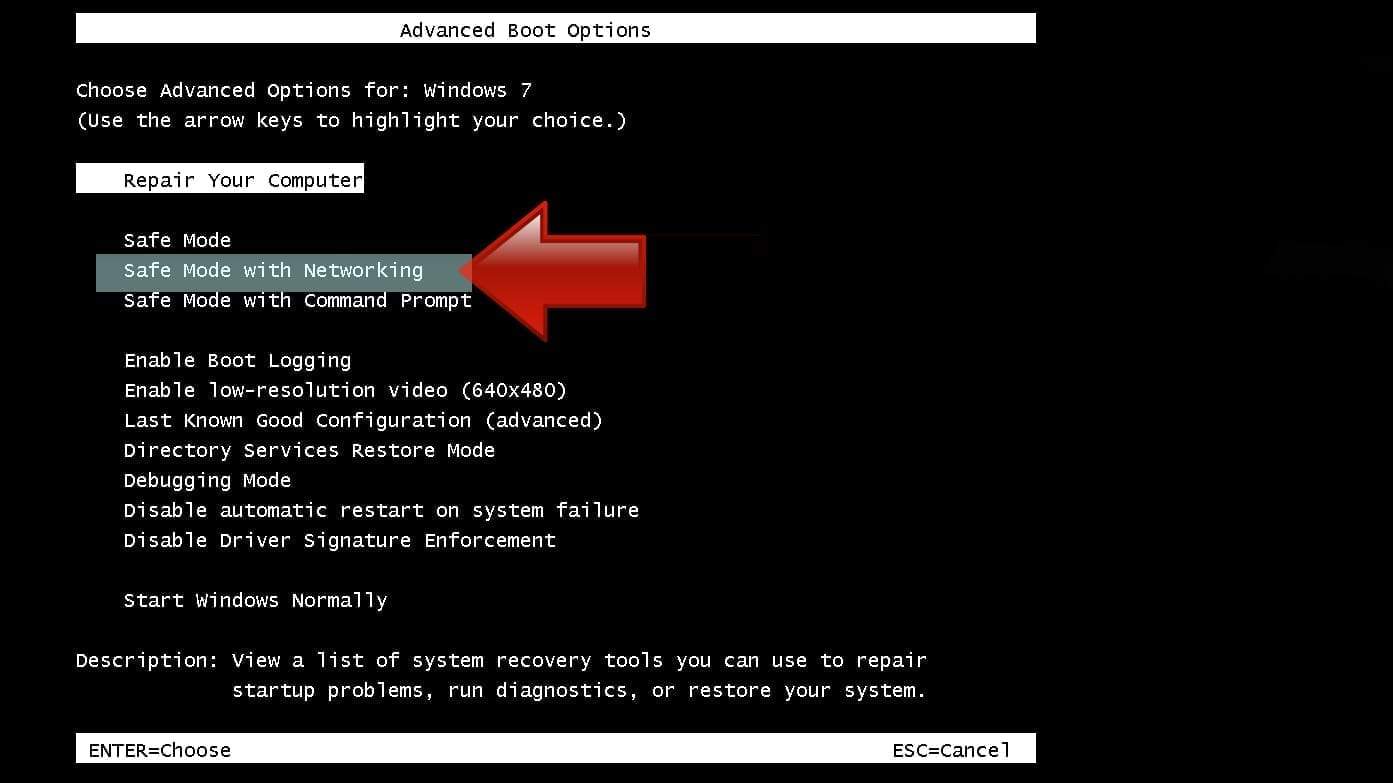
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
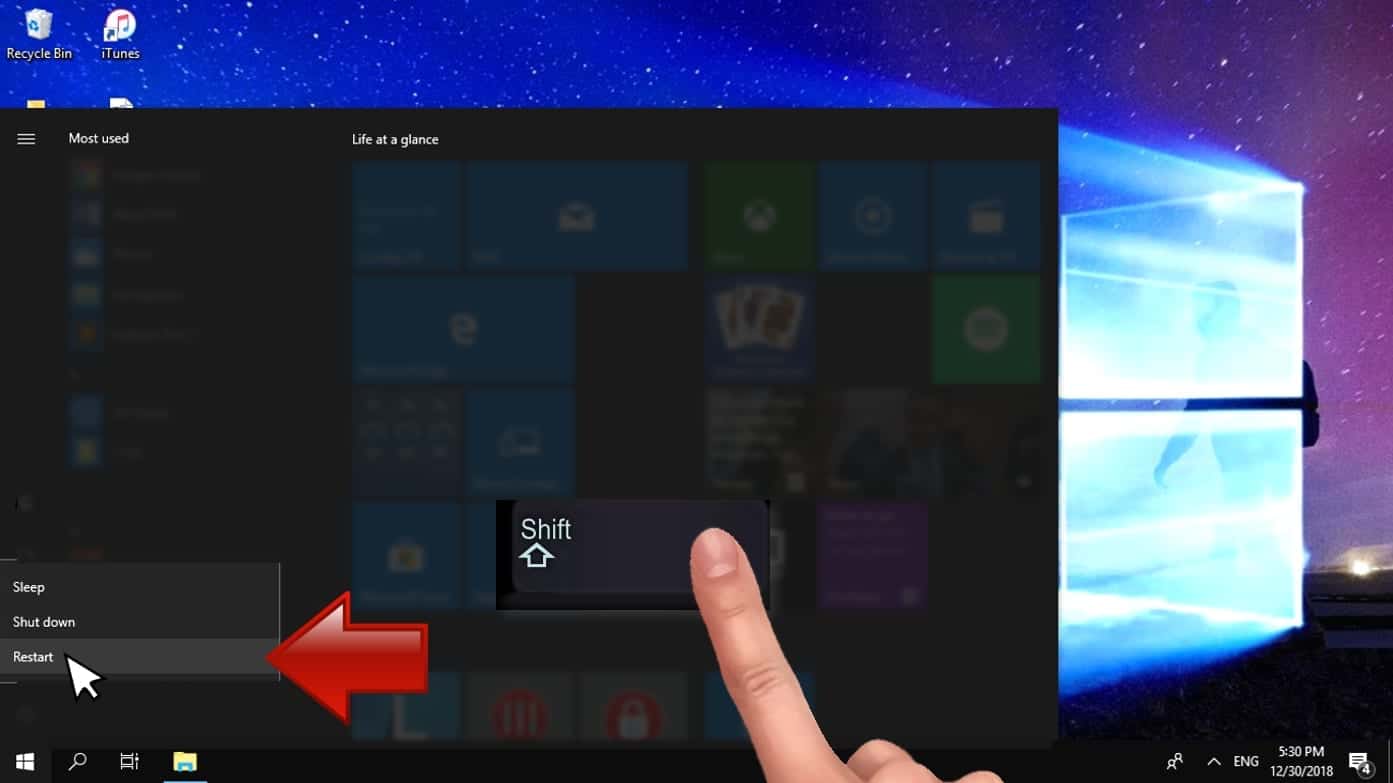
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
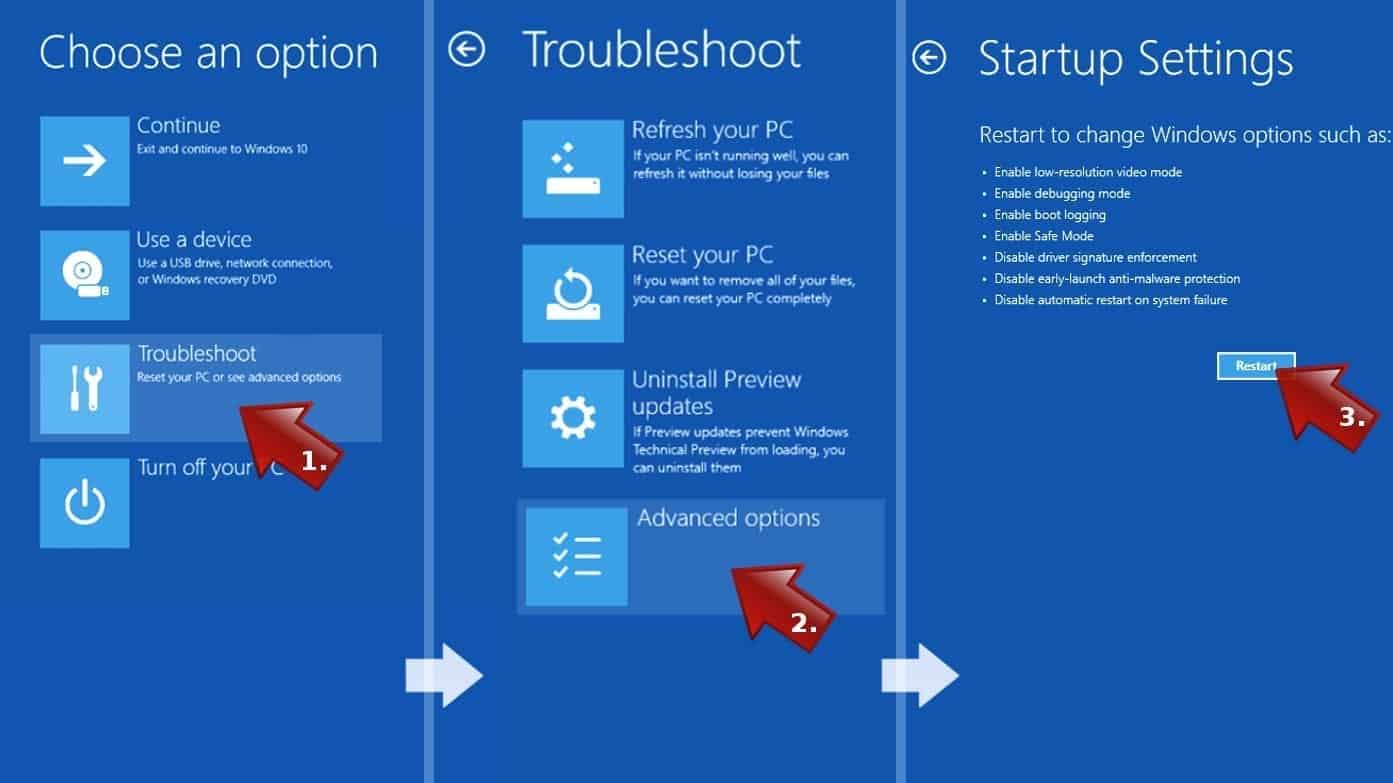
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
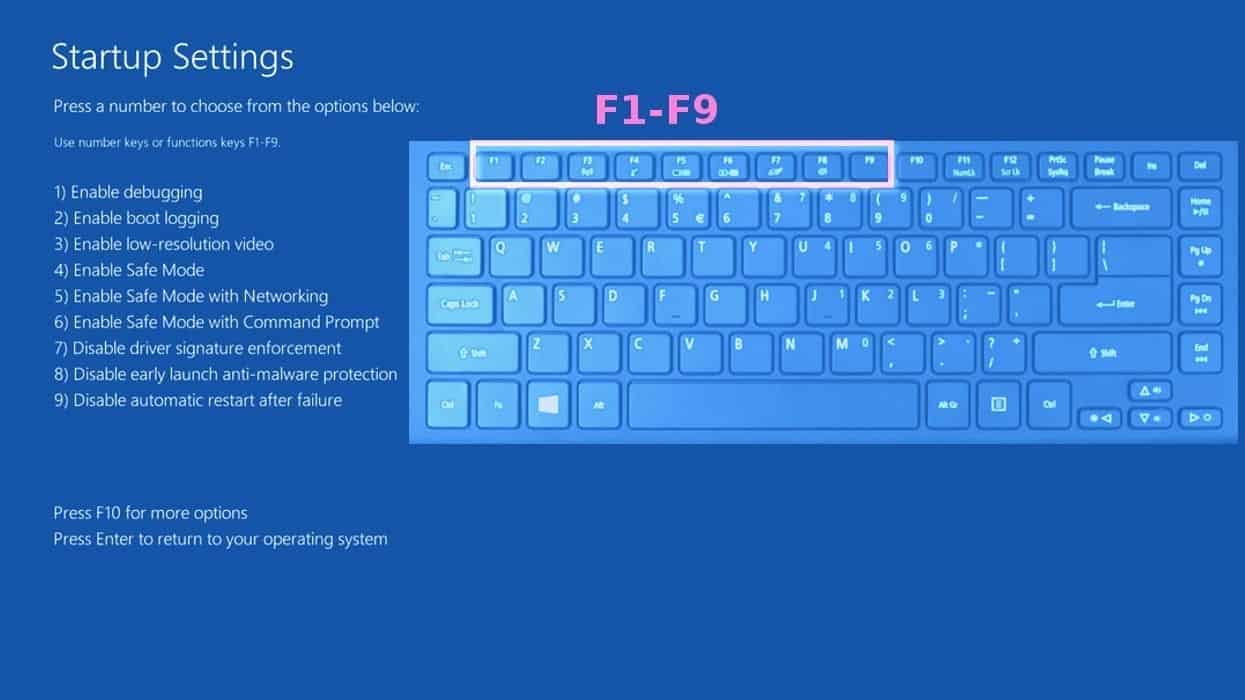
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove AZORULT malware files. It is very hard to identify files and registry keys that belong to the virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. We recommend using SYSTEM MECHANIC ULTIMATE DEFENSE , which can also restore deleted files. Additionally. we recommend repairing virus damage using RESTORO.
Special Offer
Compatibility: Microsoft Windows
See Full Review
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
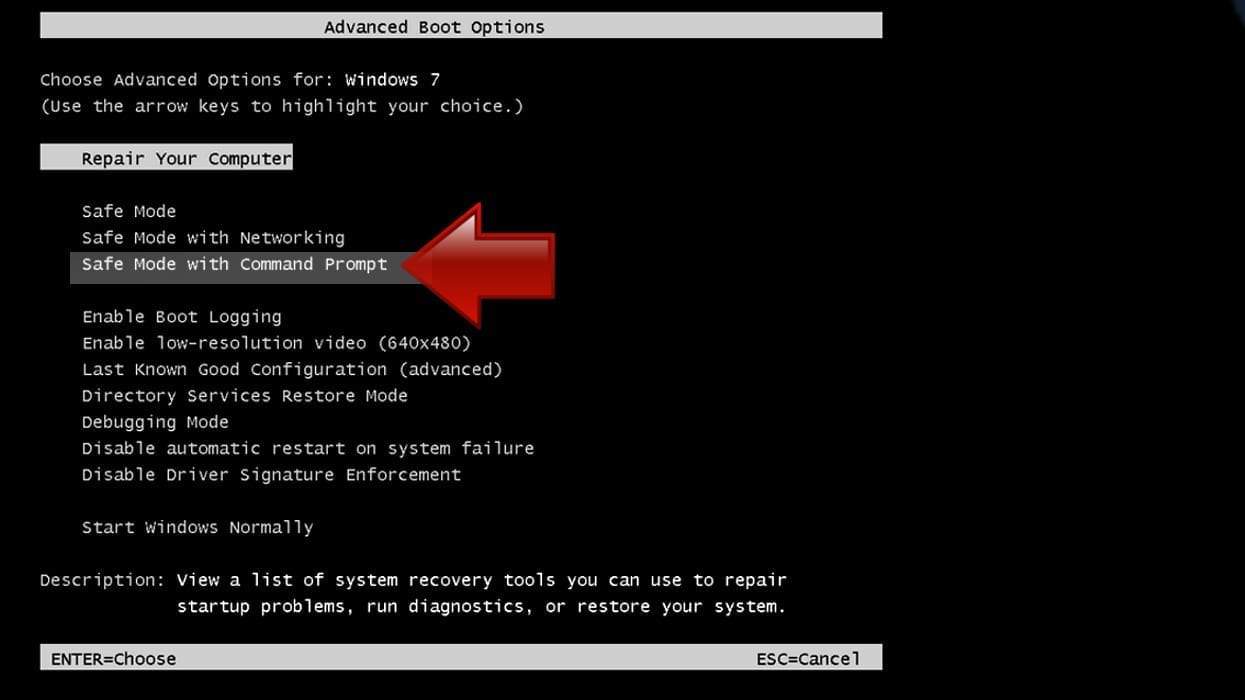
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.

- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before the malware infiltration.
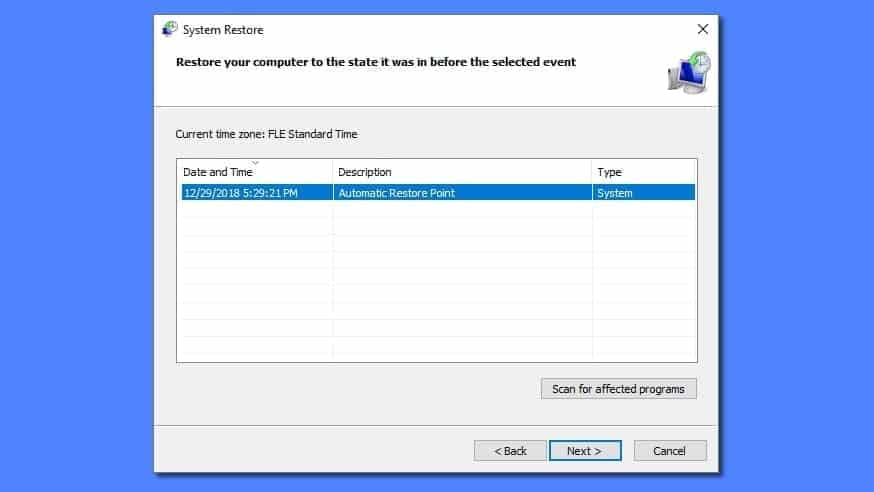
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Leave a Reply