Remove TABE Ransomware Virus (.tabe File Virus Decryption Guide)
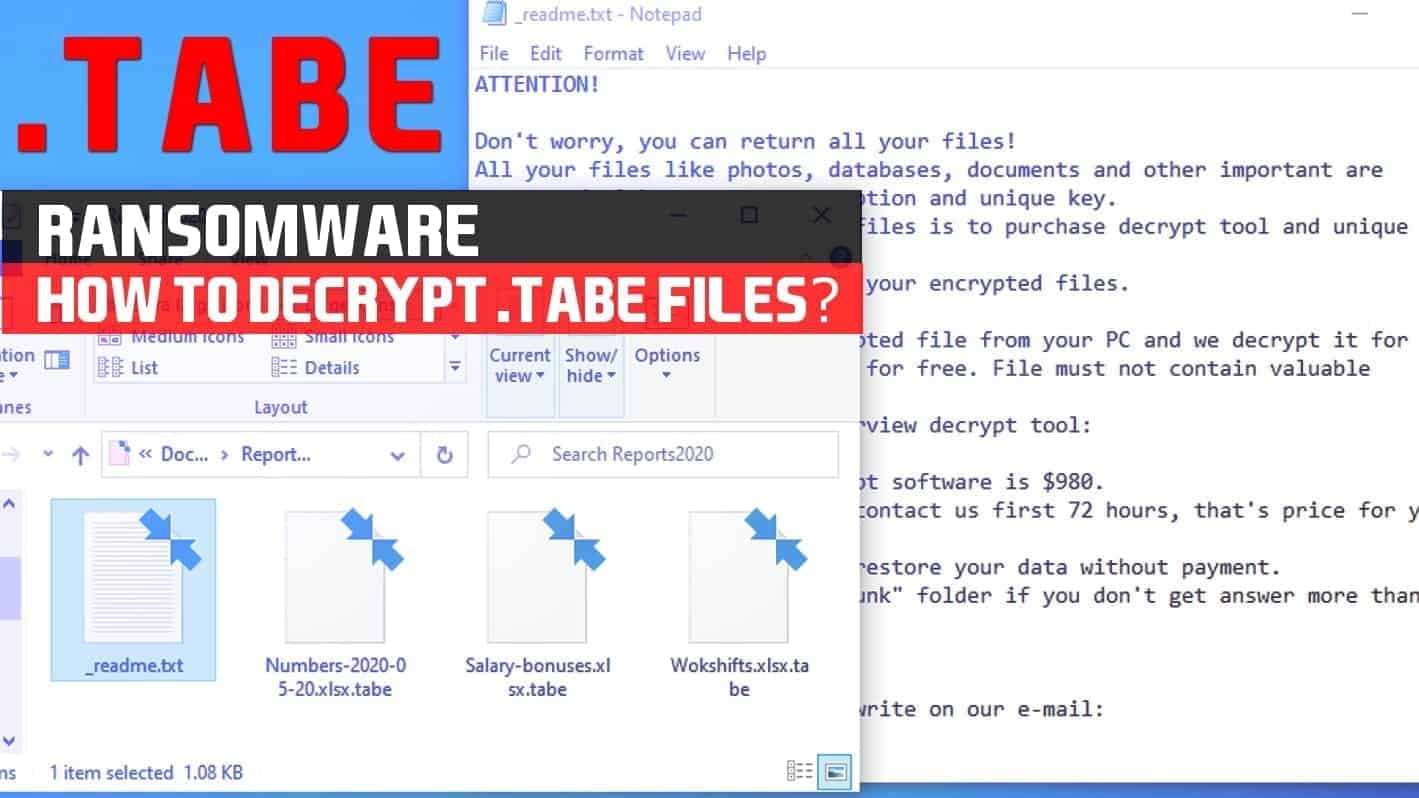
TABE virus — another hit from STOP/DJVU ransomware family
Contents
TABE ransomware virus is a dangerous file-encrypting cyber threat that belongs to STOP/DJVU ransomware family. It is currently the 234nd and the latest version of the original malware. This ransomware uses .tabe extension to encrypt the data on the targeted computer and asks the victims to contact via helpmanager@mail.ch and restoreadmin@firemail.cc e-mail addresses for decryption options.
Just as previous versions, including USAM, PEZI, NLAH, ZIPE, NYPD, this cyber threat imitates a fake Windows update screen when encrypting all information on the infected computer. The targeted data ranges from photos, videos, audio files, to important documents and other information. Later, victims receive a ransom note in the form of _readme.txt file.
The text file explains about the infection and damage made to the information on the affected computer. Criminals point out that the corrupted data can only be restored with a TABE ransomware decryption tool. Unfortunately, it is a completely unique sequence of numbers and characters that cannot be duplicated.
In other terms, only the attackers can provide a decryption key to restore encrypted files and they ask to pay for it. Victims are demanded to pay $490 in Bitcoins within the first 72 hours of the infection. It is considered to be a period for a 50% discount. After the given period, victims must pay $980 to regain access to their documents.
Even though collaborating with cybercriminals might seem the only option to fix the damage that ransomware has caused, it highly irresponsible. Many victims have already reported that even when they agreed to pay up for the attackers, they never received the promised decryption tool.
Furthermore, this cyber threat not only targets to encrypt all information stored on the computer but also to install other malware. In particular, it delivers AZORULT, also known as an infamous password stealer. This Trojan horse collects all social media and other accounts’ passwords and transfers them to the attackers.
Geek’s Advice team warns that if you try to minimize the damage caused to your files by paying the ransom, you risk not only to suffer from enormous financial losses but also your privacy. The attackers can gain access to your other accounts, including online banking, and steal even more money.
Therefore, it is essential that you act quickly once you notice the first symptoms of the infection. Our recommendation would be to get a professional malware removal software to remove Tabe ransomware along with the password-stealing Trojan.
Our experts believe that the best option for TABE removal is RESTORO. This robust malware-removal tool can quickly identify the locations of malware components and eliminate them without hesitation. It is a safe and only option available for regular computer users to deal with dangerous ransomware.
Ransomware description
| Name | TABE ransomware |
| Type | File-encrypting virus |
| Family | STOP/DJVU |
| Version | 234th |
| Other variants | USAM, PEZI, ZIPE, NLAH |
| Extension | .tabe |
| Ransom note | _readme.txt |
| Contact e-mails | helpmanager@mail.ch and restoreadmin@firemail.cc |
| Amount of the ransom | $490 as a 50% discount within first 72 hours, $980 later |
| Symptoms | Displays an imitation of Windows update screen while encrypting files on the targeted computer; Documents are appended with file-marking extension and become no longer accessible; Also, it installs AZORULT password stealer |
| Distribution | Reaches the targeted computer via fake Adobe update pop-up or via fraudulent software downloads on peer-to-peer (P2P) file-sharing websites |
| Elimination | You can only get rid of the threat with trustworthy malware removal software. We suggest using RESTORO |
Threat Review
Name: TABE ransomware virus
Description: Tabe ransomware is a malicious computer program that encrypts all files on the system with a purpose to extort the computer owner. During the attack, it marks all files with .tabe file extension to mark affected data. The virus' developers use _readme.txt ransom note to inform the victim about the attack and provide two contact emails for those willing to pay ransom to decrypt all files.
Offer price: $490-$980
Currency: Bitcoin
Operating System: Windows
Application Category: Ransomware
Author: STOP/DJVU developers
- DAMAGE (5)
- DISTRIBUTION (5)
- ENCRYPTION STRENGTH (5)
Overall
5User Review
( votes)Tabe ransomware attack on file folder demonstrated below.
Tricks used to distribute file-encrypting viruses
Usually, criminals employ deceptive techniques to trick unaware computer users into downloading the ransomware. The most popular example would be the creation of fake pop-up ads with a warning to update well-known software, such as Adobe Flash Player.
Cybercriminals develop the deceptive ad to exactly resemble the actual software and embed a malicious code to trigger an automatic ransomware installation once clicked. Users who browse suspicious websites can be redirected to such pop-ups and either click the ad by accident or be lured into doing so.
Another widely used ransomware distribution technique is to place a file-encrypting virus executable file on a peer-to-peer (P2P) page with the name of legitimate software. Since many people are browsing for application cracks or ways to download paid software for free, they are often tricked to install ransomware instead.
The best way to protect your computer from such infections is to avoid visiting suspicious websites and never click on ads. More importantly, carefully check if software updates come as notifications from the actual program installed on your computer or as malicious pop-ups. If it is a trick to lure you into downloading malware, never click on any buttons except the one to close the window.
However, most importantly you should only install programs that are downloaded from official websites or authorized distributors. Never attempt to get software cracks or easier download options on unverified websites. This way you will protect your system from further attacks of ransomware or potentially unwanted programs (PUPs).
Learn to uninstall TABE virus and restore encrypted files
It is important to understand how dangerous ransomware is — you can only remove TABE file virus by scanning your computer files with a professional antivirus. This way you will find all malware-related components and uninstall the virus completely.
If you try manual elimination, TABE ransomware removal might be unsuccessful or worse, cause even more damage to your system. Use RESTORO as it can not only help you get rid of the virus but also fix the damage it has caused.
However, uninstalling this cyber threat will not automatically restore your files to the primary state. For that, you must either use the latest backup from the Cloud or try alternative recovery methods explained in the STOP/DJVU decryption article.
Finally, before you head to the removal steps below, we want to warn you about fake decryption tools offered online. Be aware that other frauds try to benefit from ransomware victims and you should never download and use unverified to tools to decrypt data.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
TABE ransomware virus Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove TABE ransomware virus files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
REMOVE MALWARE & REPAIR VIRUS DAMAGE
1 Step. Get robust antivirus to remove existing threats and enable real-time protection
INTEGO Antivirus for Windows provides robust real-time protection, Web Shield against phishing and deceptive websites, blocks malicious downloads and blocks Zero-Day threats. Use it to remove ransomware and other viruses from your computer professionally.
2 Step. Repair Virus Damage on Windows Operating System Files
Download RESTORO to scan your system for FREE and detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Scott Bolton is a senior content strategist in our Geek’s Advice team. He is exceptionally passionate about covering the latest information technology themes and inspire other team members to follow new innovations. Despite the fact that Scott is an old-timer among the Geeks, he still enjoys writing comprehensive articles about exciting cybersecurity news or quick tutorials.
Recent Posts
Remove KXDE Ransomware Virus (DECRYPT .kxde FILES)
KXDE ransomware uses encryption to lock all files on a computer KXDE ransowmare is a…
Remove WDLO Ransomware Virus (DECRYPT .wdlo FILES)
WDLO ransomware uses encryption to lock your personal files WDLO ransomware is a malicious computer…
Why You Need a VPN and How Does It Protect You?
What is a VPN and how does it work? The term VPN stands for Virtual…
Remove PPHG Ransomware Virus (DECRYPT .pphg FILES)
PPHG ransomware encrypts your computer files, threatens to keep them locked until a ransom is…
Remove SSOI Ransomware Virus (DECRYPT .ssoi FILES)
SSOI ransomware aims to lock all of your data on a computer and then extort…
Remove KKIA Ransomware Virus (DECRYPT .kkia FILES)
KKIA ransomware sneakily encrypts your files KKIA ransomware is a newly emerged computer virus that…
View Comments
Thanks fir recommending removal software and decryptor- saved my life!!