Kuub ransomware victims can’t open files anymore
Contents
Kuub ransomware is a malicious computer virus that encodes personal files and seeks to extort victims. It is the v0168 version from STOP/DJVU malware group. Once it makes a file inaccessible, it also ads .kuub file extension to it. Following that, the virus leaves a ransom note ( _readme.txt) to instruct the victim on how to pay a ransom in exchange for data decryption software. They provide two emails – gorentos@bitmessage.ch and gerentoshelp@firemail.cc so that the victims could contact them.
This ransomware variant emerged after NESA and BOOT, but before RECO ransomware version. These are the latest and updated crypto-malware versions that cannot be decrypted that simply because they use a proper combination of AES/RSA crypto-algorithms to corrupt data on the computer. Once encoded, the data can be restored only using the private key owned by the attackers.

During the encryption process, .Kuub file extension virus communicates with its Command&Control server, which serves it the ONLINE key. In case the virus cannot reach the C&C server, the files will be encrypted using an OFFLINE key, which gives hope for possible data recovery options (more on that in the main article about DJVU malware).
Currently there is no Kuub decryption software available. However, please stay patient – security experts might come up with one soon. For now, you can only restore your files using data backups.
The ransom note left by the criminals contains demands regarding the ransom payment. According to the cybercriminals, they can provide victims with KUUB decryption software if the victim pays the specified amount of money in Bitcoins. They ask for $490 if the victim pays within 72 hours from the infection moment; $980 for all the ones who decide to pay later.
A full ransom note is provided below.
ATTENTION!
Message from KUUB ransomware developers
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
[removed link]
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
gorentos@bitmessage.ch
Reserve e-mail address to contact us:
gerentoshelp@firemail.cc
Your personal ID:
983mhflGeRsMTHVpwfk4tlm4RWx1y69zcacA5hSp3l60BnYwdtr
It is unknown whether the attackers provide the decryption software after receiving the payment, so we do not recommend paying the ransom under any circumstances.
It is impossible to recover files from Volume Shadow Copies because the malware executes these commands to destroy them and any other means of data restoration:
sc stop VVS
sc stop wscsvc
sc stop WinDefend
sc stop wuauserv
sc stop BITS
sc stop ERSvc
sc stop WerSvc
cmd.exe /C bcdedit /set {default} recoveryenabled No
cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
C:\Windows\System32\cmd.exe” /C vssadmin.exe Delete Shadows /All /Quiet
If you have fallen victim to this cyberthreat, you must remove KUUB ransomware virus instantly. Security experts inform that it spreads together with Azorult Trojan which steals private data such as passwords and possibly can empty your bank account quickly. To delete the malware, we recommend using a robust anti-virus solution.
Threat Summary
| Name | KUUB Ransomware Virus |
| Type | Ransomware (STOP/DJVU family) |
| Ransom note | _readme.txt, _openme.txt |
| Ransom demand | $490 or $980 |
| Encryption | AES/RSA combination |
| Decryption | No tools available |
| Distribution | Malicious spam, illegal software cracks, keygens |
| Removal | Remove using antivirus software |
Distribution tricks
Kuub virus managed to infect thousands of users worldwide using standard ransomware proliferation tactics. It employs malicious spam and malicious bundling techniques to reach its potential victims on a daily basis. Victims have reported receiving the malicious payload along with software cracks, keygens, and other officially illegal files.
You must pay attention to the fact that criminals will use such free goods as bait to serve malware to you. Additionally, they tend to exploit victims’ curiosity by packing the malware into malicious spam attachments or links.
If you wish to avoid being hit by ransomware from STOP/DJVU family, PHOBOS, OmniSphere or any other, we strongly recommend reading these ransomware prevention guidelines.
KUUB ransomware removal guidelines
To remove Kuub ransomware virus, you must use a trustworthy antivirus software. Do not settle with suspicious so-called malware removers – only choose the one with great reviews. There are good paid and free alternatives on the market.
You can also use self-help guide provided below for manual KUUB ransomware removal. However, you should still run a system scan afterwards to check whether all malware remains were wiped out.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
KUUB ransomware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
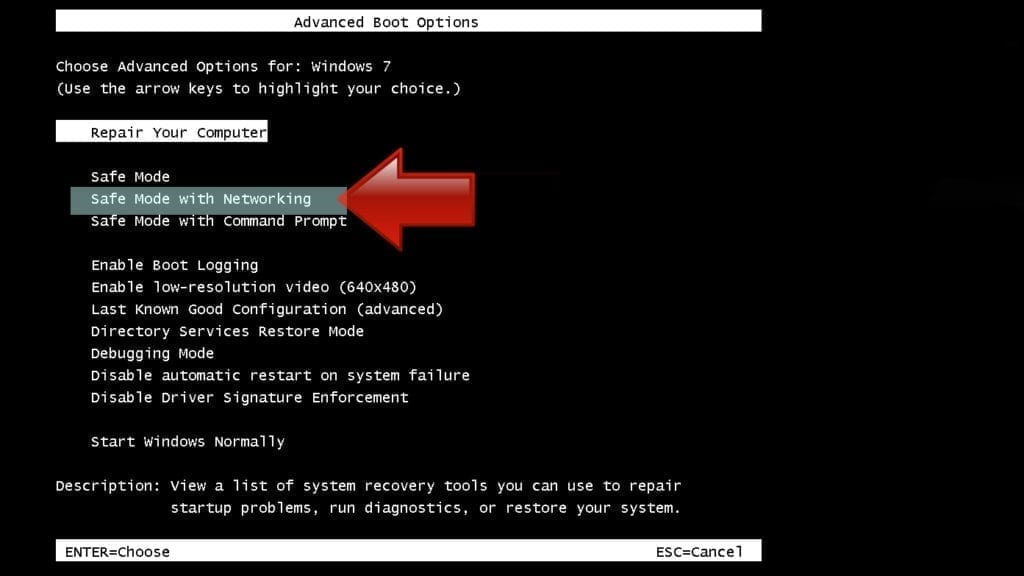
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
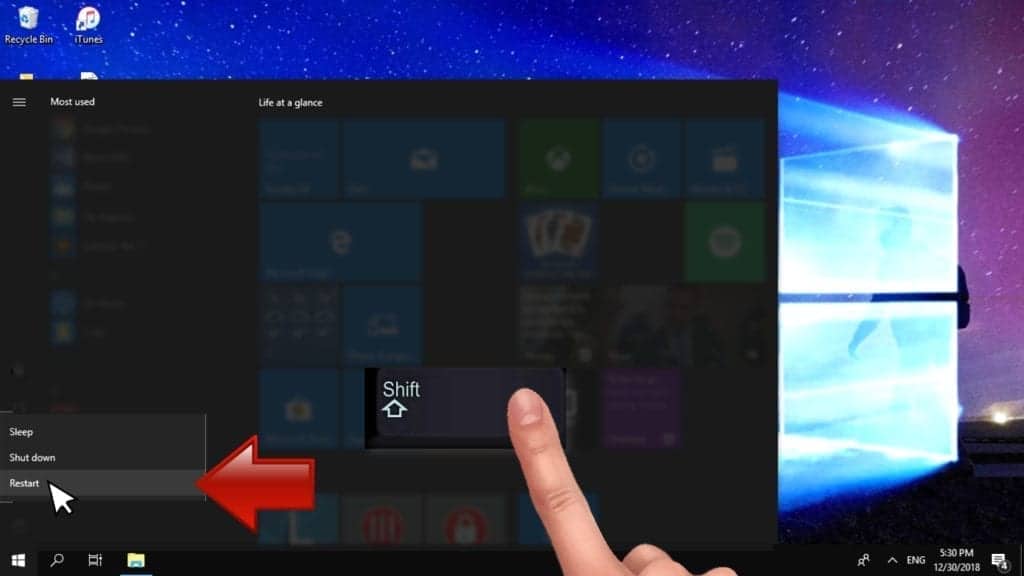
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
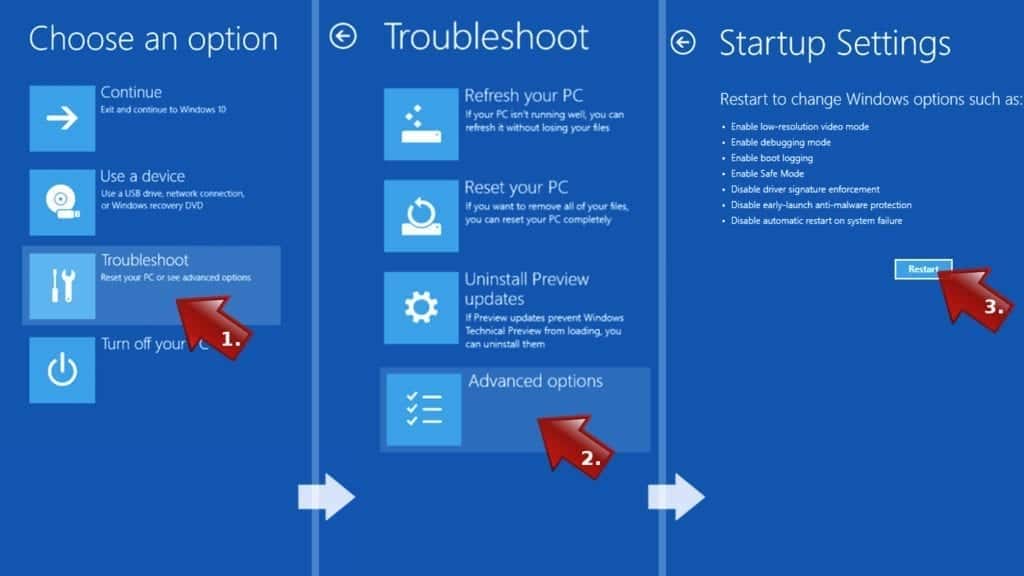
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
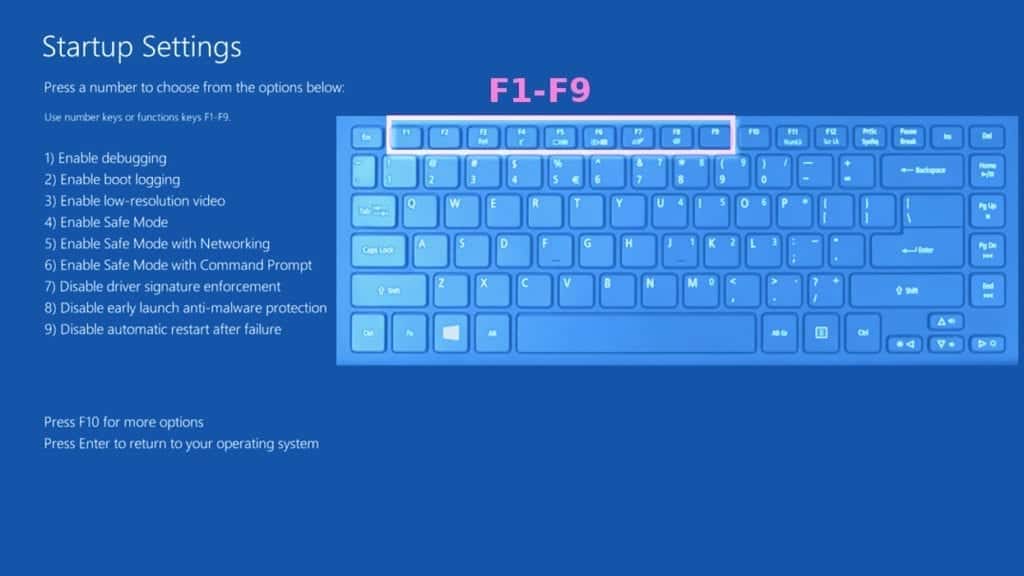
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove KUUB ransomware files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO Antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
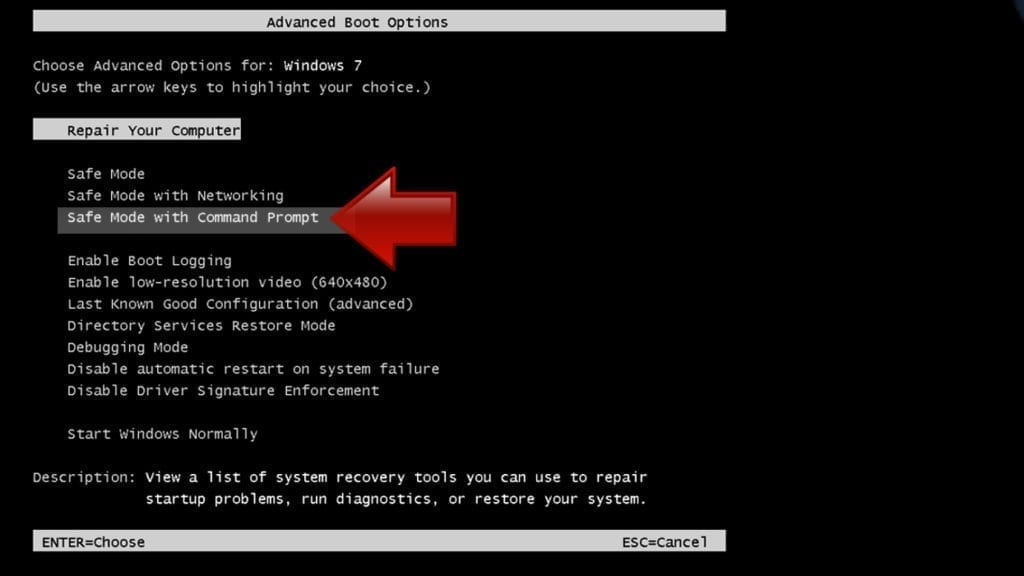
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
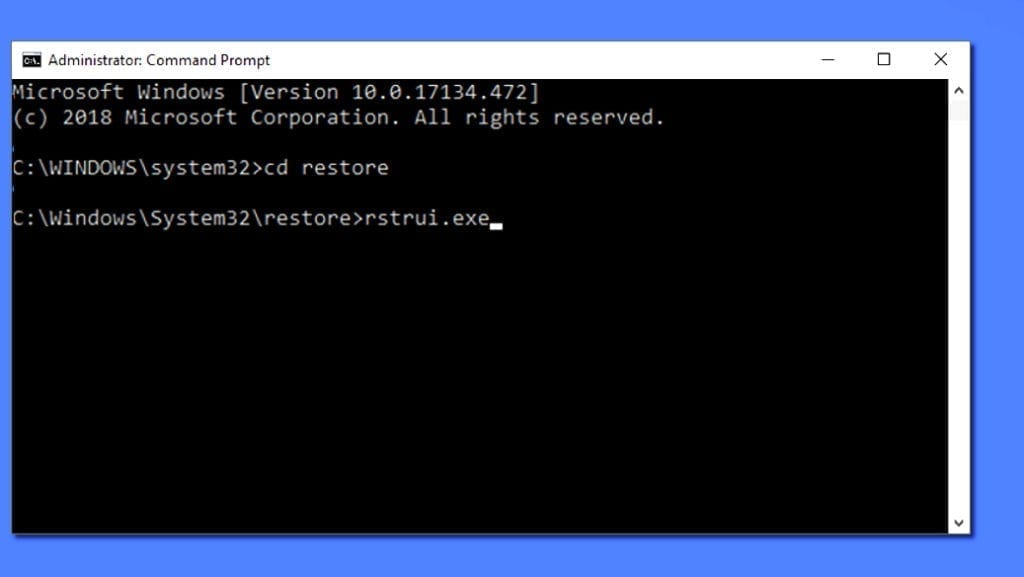
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
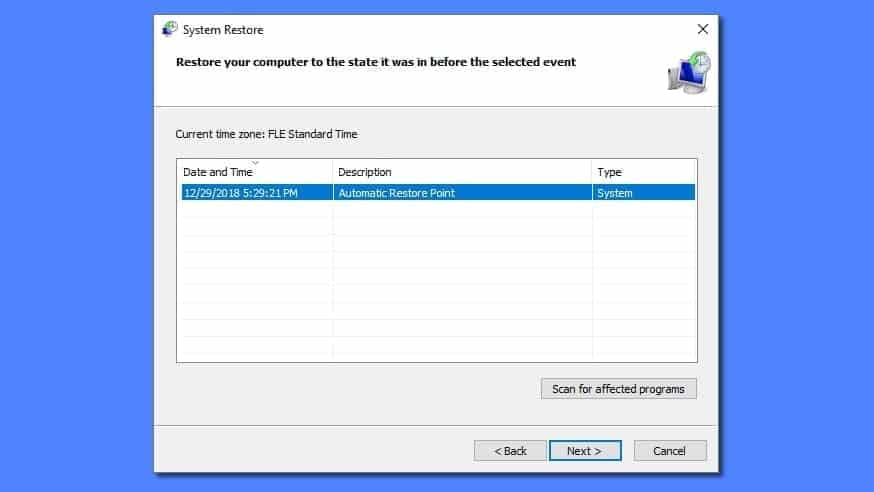
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.


Leave a Reply