Remove Sodinokibi Ransomware Virus (2022 Guide)
Sodinokibi ransomware activity continues
Contents
Sodinokibi ransomware (alternative names: REvil and Sodin ransomware) is a computer virus that encrypts files on the infected system. The purpose of encryption is to prevent the victim from accessing these files and push him to pay a ransom worth from $2500 to $5000. Professional security researchers have already proved that the virus is developed by the recently active GandCrab ransomware creators. The ransomware is also known to threaten victims to publish their data online if they refuse to pay a ransom.
The ransomware can be identified by unique file markers it appends to original filenames – for example, a file called Report.xls becomes Report.xls.796t1hbn91 and the ransom note gets called 796t1hbn91-HOW-TO-DECRYPT.txt, meaning that the victim’s unique file extension will be included in the note’s filename.
After encrypting all of victim’s files, Sodinokibi virus changes desktop background image.
The desktop image says:
You are infected! Read kjd730i_HOW-TO-DECRYPT.txt!
As shown above, the virus includes the ransom extension in the beginning of the ransom note file name. Random file extensions are mostly used to confuse the user and make it difficult to search for related ransomware removal and decryption information online. However, you can always identify the malware using the handy ID Ransomware tool.
| Virus name | Sodinokibi, also known as Sodin, REvil |
| Virus type | Ransomware |
| Process name | Showing Mcga Wmv Photo Ramsey Married |
| Detection names (VT) | Win32:RansomX-gen [Ransom] (Avast, AVG), DeepScan:Generic.Ransom.Sodinokibi.0A43E2C0 (BitDefender), Trojan-Ransom.Sodinokibi (A) (Emsisoft), Ransom.Sodinokibi (Malwarebytes) and many others |
| Damage | Personal files are encrypted without possibility to restore them, unless the victim pays a ransom. The attackers might threaten to publish victim’s data online |
| Distribution methods | Malvertising, hacked websites, spam emails containing malicious links, software vulnerabilities |
| Ransom demand | $2500-$5000 in Bitcoin |
| Decryption methods | Not available |
| Removal | Remove while in Safe Mode using instructions provided below |
Updated August 7, 2019: Currently, Sodinokibi decrypt is not available. None of antivirus or security researchers succeeded in creating a decryption tool yet. Once such tool is available, we will update the article. Meanwhile, take actions to remove the ransomware as soon as possible.
Despite that no possible decryption methods are available, you must take actions to complete Sodinokibi removal immediately. Keeping ransomware remains on the computer, or even continuing to use a compromised computer is a strictly NOT recommended practice. You can find a guide on how to safely delete the virus from your computer below this article.
Sodinokibi infection explained
The installation phase
The very first Sodin / REvil attack method observed was email phishing. The attackers would send out thousands of malicious emails with deceptive links leading to ransomware in a ZIP archive file. The archive contains a JavaScript file, which, once double-clicked by the user, activates itself via WScript.
The malicious script contains more deobfuscated information. To be precise, it contains a PowerShell script, which is later saved in Windows temp directory.
The script is full of unnecessary exclamation marks, later removed by PowerShell command which also executes the script to run it. Consequently, a list of malicious scripts begin running, deobfuscating and executing themselves (check a more detailed description by Cybereason). This is done in order to bypass detection by common antivirus solutions. Finally, it loads a module Install1 into memory, which works as a loader for Sodinokibi ransomware.
The malicious loader attempts to get highest privileges to decrypt and execute a portable malware executable. This functions as a second loader module.
Surprisingly, the malware checks if AhnLab antivirus is present on the infected machine, if so, attempts to find autoup.exe process, which contains security flaws.
Reportedly, Gandcrab developers were angry about the Anti-Gandrab vaccine created by AhnLab security vendor. This is yet another reason to believe that Sodinokibi developers are the same people. The malware attempts to inject Sodinokibi payload into the autoup.exe process.
If the computer doesn’t have AhnLab installed on it, the ransomware executes via a PowerShell process.
The release of a malicious payload
Sodinokibi ransomware saves cryptographically secured config data in a separate file. It contains information describing what data to encrypt and exclusion rules, ransom note contents and rules to exploit CVE-2018-8453 vulnerability.
In this phase, the malware checks for the main keyboard language, and kills itself in case one of the listed languages is found: Romanian, Russian, Ukrainian, Belarusian, Estonian, Latvian, Lithuanian, Tajik, Persian, Armenian, Azeri, Georgian, Kazak, Kyrgyz, Turkmen, Uzbek, Tatar.
Otherwise, the malware executes, deletes Volume Shadow Copies, encrypts files and starts dropping ransom notes. Finally, the desktop wallpaper changes to inform the victim about the attack.
Following a successful encryption, Sodinokibi virus attempts to establish connection with C2 server. It starts iteration through a list of domains from the aforementioned config file and generates an URL for the C2. The way this ransomware generates random URLs is yet another relation between it and GandCrab.
Generated URLs receive information about usernames, PC names, language, OS type, CPU architecture and domain names.
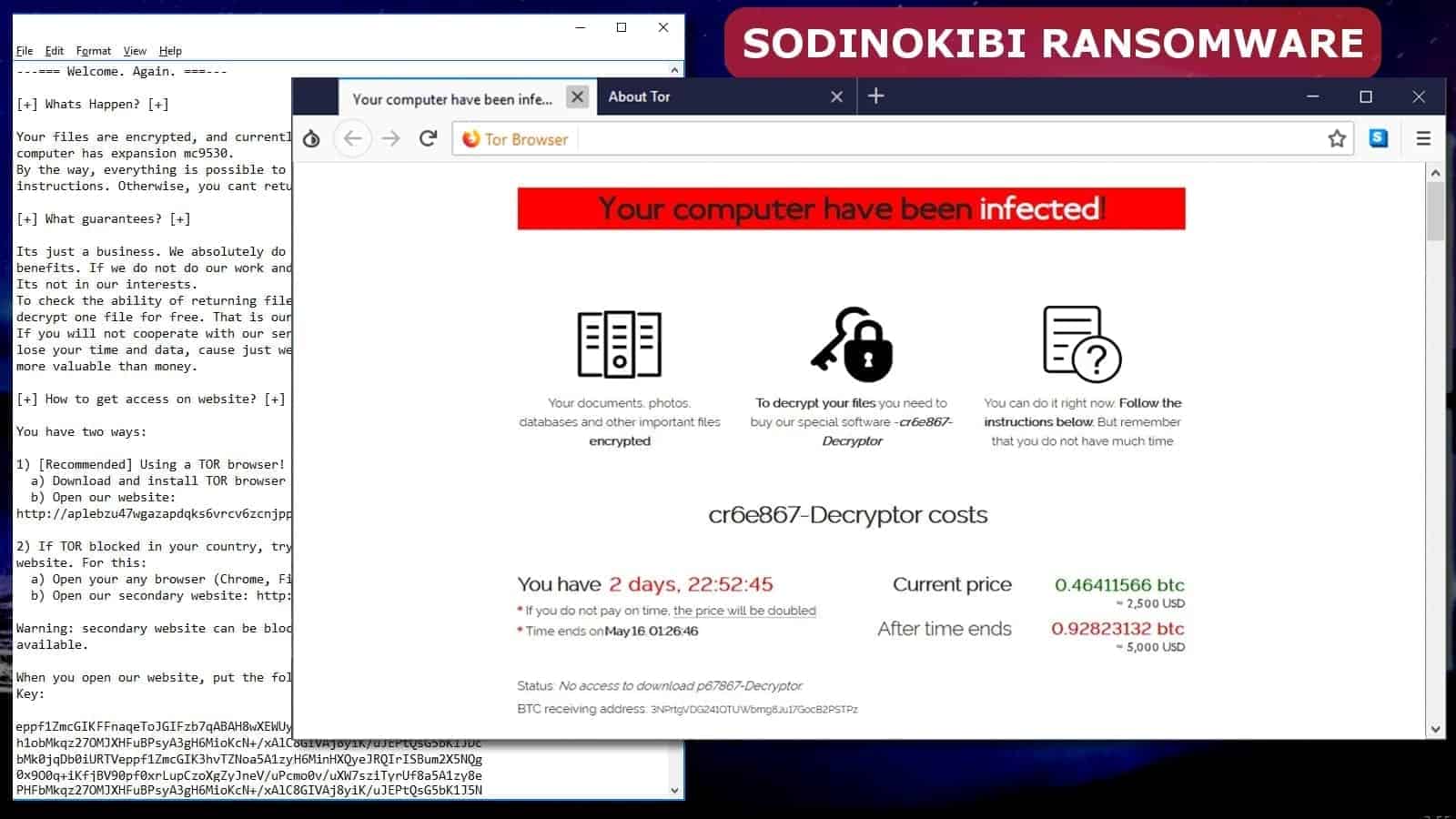
The ransom note leads to payment website
The Sodinokibi virus’ ransom note informs about data encryption and clarifies that files were made unavailable. According to the note, the only way to restore files is to pay money to cybercriminals in an untrackable way. In order to pay, the victim has to access a special website (typically only available via Tor browser), enter a given key (a lengthy string of symbols, letters and digits) and also enter the unique file extension name.
The website displays the price of the Sodinokibi decryptor, which costs approximately 2.500 USD. The ransom must be paid in Bitcoin currency. However, malware developers urge the victim to pay until a given date, or the ransom price skyrockets to 5.000 USD. The Bitcoin receiving address is 324VH5nPXCKCUGAMAn23nogm2Z6ph97evh.
Of course, we strongly encourage you NOT to pay the ransom. Not because the criminals cannot decrypt your files; they most likely do. However, don’t encourage them by paying, and instead wait until malware researchers find a way to decrypt those files for free.
It is not always possible; however, in some cases, data decryption is possible. It mostly depends on the operation and structure of the virus. If it has flaws, files can be decrypted.
Timeline of Sodinokibi updates
May 3rd, 2019. Sodinokibi developers start exploiting the CVE-2019-2725 vulnerability in Oracle Server to push the ransomware alongside various Trojans, miners, and malware used to enroll computers into botnets. The Oracle later released a patch to the vulnerability, closing the gate for the ransomware distribution.
July 3rd, 2019. The ransomware gets an update which allows exploitation of Windows Win32k.sys file and exploits the CVE-2018-8453 vulnerability. The ransomware uses the vulnerability to elevate its privileges on infected host. The ransomware now also uses a combination of encryptions to lock victim’s data. Since this update, decryption requires two keys, not one.
September 3rd, 2019. The ransomware developers hijacks WordPress websites and injects malicious JavaScript codes to infect visitors with Sodinokibi ransomware. In particular, the attackers injected fake Q&A forums containing deceptive administrator’s answers containing a link to the ransomware installation file.
October 21, 2019. Emsisoft along with Coveware discover a workaround that allows restoring victim’s data for free. The victims are asked to contact the companies individually for help.
December 27th, 2019. The attackers release a Christmas-themed update to Sodinokibi virus. The ransom note now wishes victims “merry Christmas.” The payment website is slightly tweaked now, too. You can see the text presented in the ransom note below.
January 23rd, 2020. Sodinokibi ransomware developers decide to step up their threatening game and promise victims to publish their personal files online if they fail to contact them and pay the ransom. In this case, they threaten an automotive group called GEDIA, which has production plants in China, Germany, Hungary, India, Poland, Mexico, Spain, Hungary, and USA. This technique of leaking victim’s data is also used by MAZE ransomware developers.
GandCrab group announces retirement plans, then changes their minds
The cyber criminals behind GandCrab ransomware (one of the most widespread viruses of 2019) have recently announced a shutdown of their operations. The ransomware took a share of 40% ransomware attacks worldwide. The announcement along with the explanation was posted on a dark web forum.
All the good things come to an end.
For the year of working with us, people have earned more than $2 billion. […] We have personally earned 150 million dollars per year. We successfully cashed this money in various spheres of white business in real life and on the Internet.
We are leaving for a well-deserved retirement.
GandCrab, a forum member
However, security researchers shortly began speculating whether Sodinokibi ransomware is a re-branded and more private RaaS. In the beginning of May, someone with a nickname “Unknown” was noticed on two top cyber crime forums making deposits of digital currencies worth $130.000. The individual introduced the new ransomware-as-a-service program as meant for a small, yet highly professional circle of cybercriminals.
According to Unknown, the program will be offered to five affiliates only. The criminal also specified “We have been working for several years, specifically five years in this field. We are interested in professionals.” However, he didn’t disclose the name of the ransomware, saying that “it was mentioned in media reports” already.
The new ransomware cannot be installed to computers in the CIS, Commonwealth of Independent States, including Armenia, Belarus, Kyrgyzstan, Kazakhstan, Moldova, Tajikistan, Russia, Turkmenistan, Uzbekistan and Ukraine. It also excludes Baltic region countries, such as Latvia, Lithuania and Estonia. According to Kaspersky Lab, Sodinokibi virus also excludes Syrian computer users.
Interestingly, GandCrab developer has also shown mercy to Syrian computer users in the past, after a Syrian man tweeted a message about virus encrypting photos of his deceased children. Following the tweet, the ransomware developer has released decryption key for Syrian victims only.
Ways to get infected and preventive measures
Currently known Sodinokibi distribution techniques:
- Malvertising that leads to RIG EK;
- Spam emails;
- Outdated software security flaws;
- Managed Service Provider (MSP) hacks;
- Hacked legitimate sites.
Sodinokibi ransomware virus has been distributed using Oracle WebLogic Server security flaw (CVE-2019-2725), which also helped in distribution of GandCrab and other malicious software.
However, in June, security researchers noticed a new, although a standard and typical malware distribution tactic known as malvertising which leads to RIG exploit kit. This exploit kit is known to be the most popular EK used to deliver malicious payloads. In other words, it has been used to distribute numerous Trojans, miners, ransomware and other malicious software.
A recent report from Infoblox also describes Sodin ransomware distribution campaign. The attackers attempt to imitate Booking.com reservation emails and invite the victim to view the booking details in the attached file.
The infected attachment says that the document was created with a more recent Word version, and in order to view the contents, the user has to enable Macros (which are disabled by default in Word). If enabled, these will execute a malicious code which downloads and runs REvil (Sodinokibi ransomware) on the computer.
Yet another distribution method was observed. It appears that criminals behind the said ransomware have hacked italian distributor of WinRAR software website and started pushing the malicious software instead of the legitimate one. The site has been taken down and restored since the hack.
Quick tips to prevent Sodinokibi infection:
- Avoid clicking suspicious pop-ups that appear on your screen when browsing hardly trustworthy websites;
- NEVER download suspicious files to your system;
- Only download files from trustworthy sources;
- Keep a backup of your files on an external drive;
- ALWAYS keep all your software up to date (OS, browsers and other programs).
We also strongly encourage you to read our in-depth guide on how to prevent ransomware attacks.
Remove Sodinokibi ransomware for free
Sodinokibi virus can be removed manually. Of course, if you have an antivirus program that is capable of detecting it, go ahead and use it for the ransomware deletion. We recommend updating your antivirus first; this way, you’ll update the program’s detection database.
However, if you do not have an antivirus program, we encourage you to follow these self-help guidelines given below. For Sodinokibi decryption tool news, we suggest you to follow NoRansom or NoMoreRansom project websites which regularly update information about available free tools.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
Sodinokibi Ransomware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove Sodinokibi Ransomware files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
REMOVE MALWARE & REPAIR VIRUS DAMAGE
1 Step. Get robust antivirus to remove existing threats and enable real-time protection
INTEGO Antivirus for Windows provides robust real-time protection, Web Shield against phishing and deceptive websites, blocks malicious downloads and blocks Zero-Day threats. Use it to remove ransomware and other viruses from your computer professionally.
2 Step. Repair Virus Damage on Windows Operating System Files
Download RESTORO to scan your system for FREE and detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
This post was originally published on July 16, 2019, and updated on August 7, 2019.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Private Internet Access Review 2022: Fast, Secure & Cheap VPN
Private Internet Access (PIA) VPN maintains its long-term role as a leader Private Internet Access…
Remove XCBG Ransomware Virus (DECRYPT .xcbg FILES)
XCBG ransomware aims to lock your files and demand a ransom XCBG ransomware is a…
Remove BPQD Ransomware Virus (DECRYPT .bpqd FILES)
BPQD ransomware encrypts all computer files, demands a ransom from the user BPQD ransomware is…
Remove KQGS Ransomware Virus (DECRYPT .kqgs FILES)
KQGS ransomware is a hostile computer virus designed to encrypt all of your files KQGS…
Remove VTYM Ransomware Virus (DECRYPT .vtym FILES)
VTYM ransomware description: a virtual menace to your files stored on the computer VTYM ransomware…
Remove FOPA Ransomware Virus (DECRYPT .fopa FILES)
FOPA ransomware is a new threatening computer virus that encrypts your files FOPA ransomware virus…