NOSU ransomware blocks access to your own files
Contents
NOSU ransomware is a file-encrypting virus which is the 197th version of STOP/DJVU malware. Once installed on the system, it starts applying asymmetric encryption on victim’s files stored on the computer, computer network or connected devices. Each encrypted file gets marked with .nosu file extension. The virus removes all means of data recovery possibilities immediately, for example, it deletes system restore points and leaves no traces of private decryption key. Next, it creates _readme.txt note with instructions on paying the ransom to cybercriminals ($490-$980 in Bitcoin). To get further information, the attackers suggest contacting them via helpmanager@firemail.cc or helpmanager@iran.ir (same email used in the KODC ransomware variant).
NOSU file virus is extremely dangerous because it corrupts important personal documents, videos, databases and other files which are essential to the victim’s work or personal life. What is even worse, the ransomware tends to install AZORULT password-stealing Trojan on the system. This malicious virus can extract all saved passwords from your browsers and possibly track your keystrokes. Therefore, a removal of such malware is essential.

The ransom note threatens to pay the ransom ASAP
The ransom note created by NOSU virus tells the victim that all important files have been encrypted. This is true – and the attackers are the only ones who have the decryption keys. To get the decryption key, the attackers suggest paying the ransom, which can cost $490 if paid within 3 days, or $980 if later. First of all, paying the cybercriminals is NEVER a recommended practice as they may never return access to your files; second, such sum of money is simply ridiculous.
The note explains that the victim must write to helpmanager@firemail.cc or, if no reply within 6 hours, try writing to alternative address, helpmanager@iran.ir. The attackers are quick to respond when it comes to convinving the victim to pay up. However, they might vanish once the money is in their cryptocurrency wallet.
The note also explains what is victim’s personal ID – however, there is another file on the computer containing ACTUAL ID, or IDs. Now, let us get into the ID matter further.

Free decryption possibilities
NOSU ransomware, just like the previous versions of STOP/DJVU, tend to use online OR offline keys to encrypt victims files. This, in fact, determines your chances to recover files for free. See instructions below to figure out your .nosu extension data recovery chances.
In order to figure out the real victim’s IDs, one must go to C:/SystemID/ and find a file called SystemID.txt here.
If you are victim of NOSU ransomware virus, you should check the IDs stored in that file and see if any of these IDs end in t1. If so, it means that some part of your data was encrypted with an offline encryption key, which means that there are chances to restore such data for free. For the IDs ending in any other character combination, free decryption is impossible. You can learn more about that here – STOP decrypter guide.
Threat Summary
| Name | NOSU ransomware virus |
| Type | File-encrypting computer virus |
| Origins | STOP/DJVU (197th version) |
| Targeted systems | Windows |
| Behavior | Encrypts files on the computer or network and connected devices, installs AZORULT Trojan |
| Extension | Appends .nosu file extension to files |
| Ransom note | _readme.txt |
| Ransom demand | $490-$980 |
| Emails | helpmanager@firemail.cc or helpmanager@iran.ir |
| Distribution | Spreads alongside illegal online downloads such as software cracks or keygens |
| Decryption tools | STOP Decryptor doesn’t support this extension at the moment |
| Removal | Remove using antivirus while in Safe Mode (see instructions below) |
STOP ransomware variants spread alongside illegal software activators
You might install NOSU file virus or other DJVU ransomware variant if you attempt to activate paid software versions illegally. For example, people often to try to obtain software licensed versions via software cracks, key generators (also known as keygens) or other activation tools such as KMSPico. You must keep in mind that such tools are cybercriminals’ go-to when it comes to malware distribution.
They simply compress their illegal programs alongside such tools, or even name their viruses accordingly to deceive the unsuspecting victims. What is even worse is that people tend to ignore security software warnings NOT to open such illegal tools. Once launched, the malware infects the computer rapidly.
How to remove NOSU ransomware virus effectively
NOSU ransomware removal is your top priority after becoming a victim to such cyber attack. You must delete all remains of the file-encrypting virus as well as Azorult’s files, too. Doing so manually can be tricky. Therefore, we recommend using a trustworthy antivirus or anti-malware when in Safe Mode for the elimination of malicious software traces.
Remove NOSU Ransomware Virus using instructions provided below. This will ensure a thorough cleanse of your computer system. Next, we suggest changing ALL of your passwords immediately. Finally, start searching for data backups – but do not plug these external devices to your computer unless the malware is completely gone. Otherwise, your backup might get corrupted, too.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software.
REMOVE THREATS WITH ROBUST ANTIVIRUS

Get INTEGO ANTIVIRUS for Windows to remove ransomware, Trojans, adware and other spyware and malware variants and protect your PC and network drives 24/7. This VB100-certified security software uses state-of-art technology to provide protection against ransomware, Zero-Day attacks and advanced threats, Intego Web Shield blocks dangerous websites, phishing attacks, malicious downloads and installation of potentially unwanted programs.
Use INTEGO Antivirus to remove detected threats from your computer.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
NOSU Ransomware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
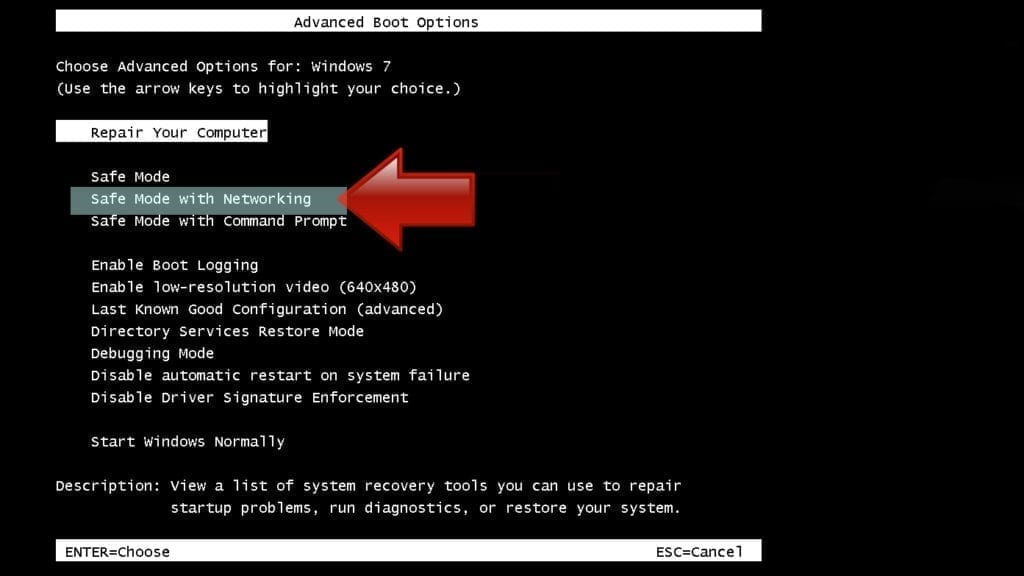
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
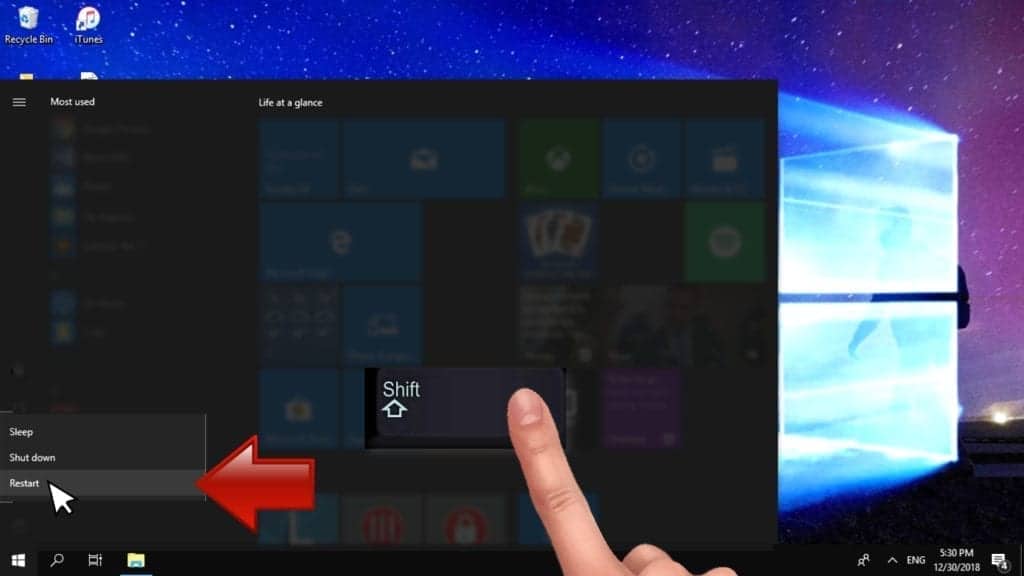
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
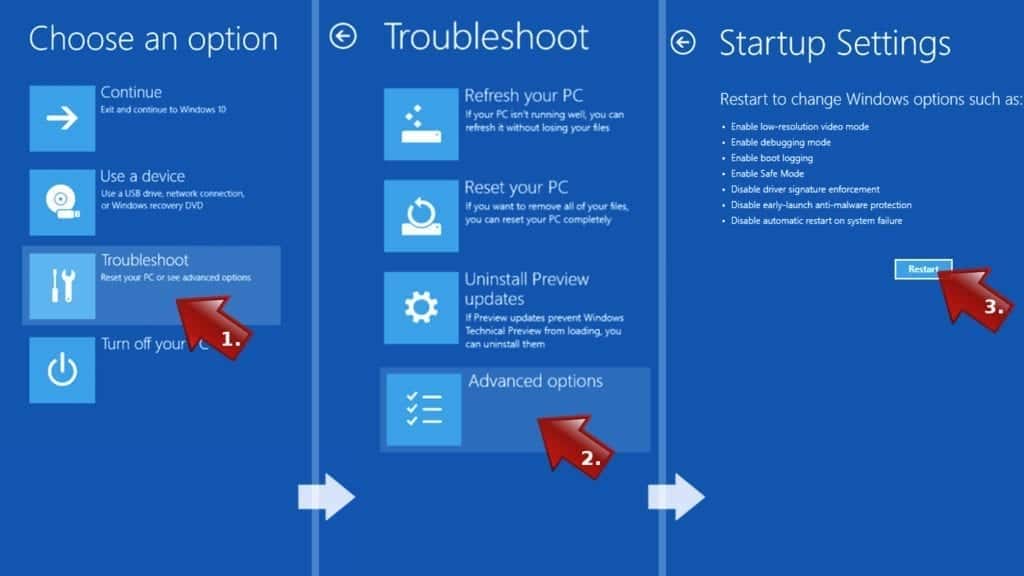
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
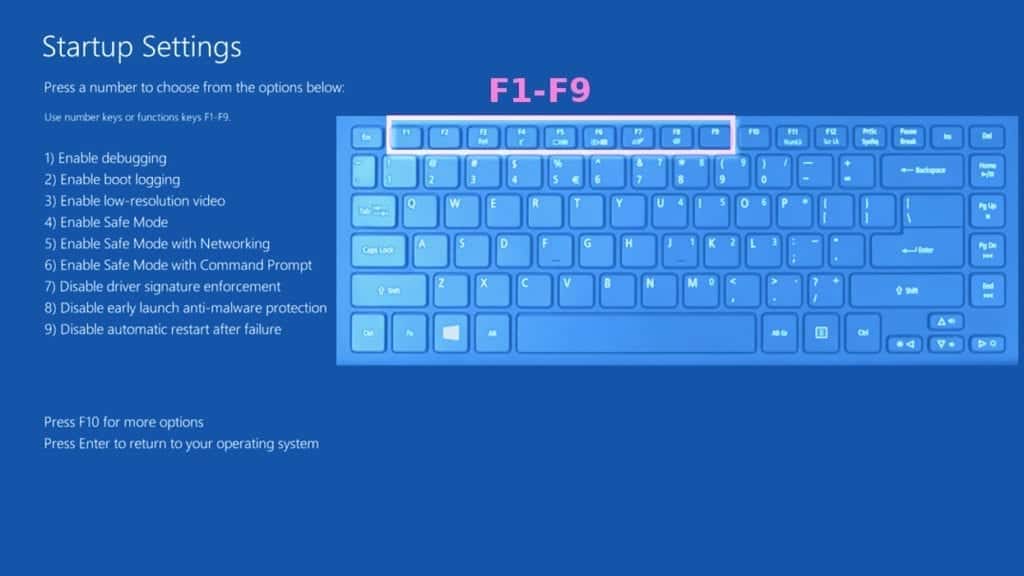
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove NOSU Ransomware files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO Antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
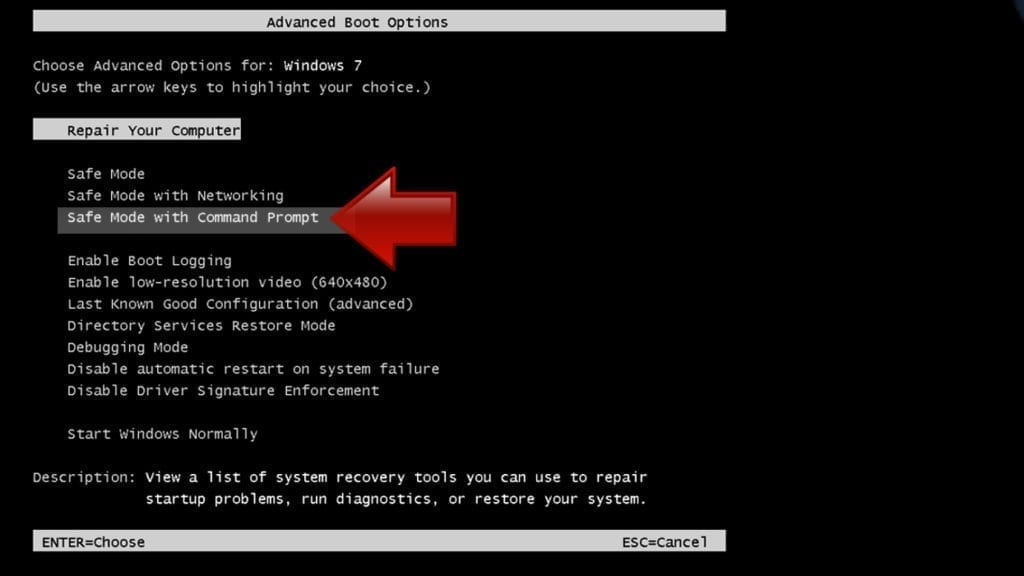
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
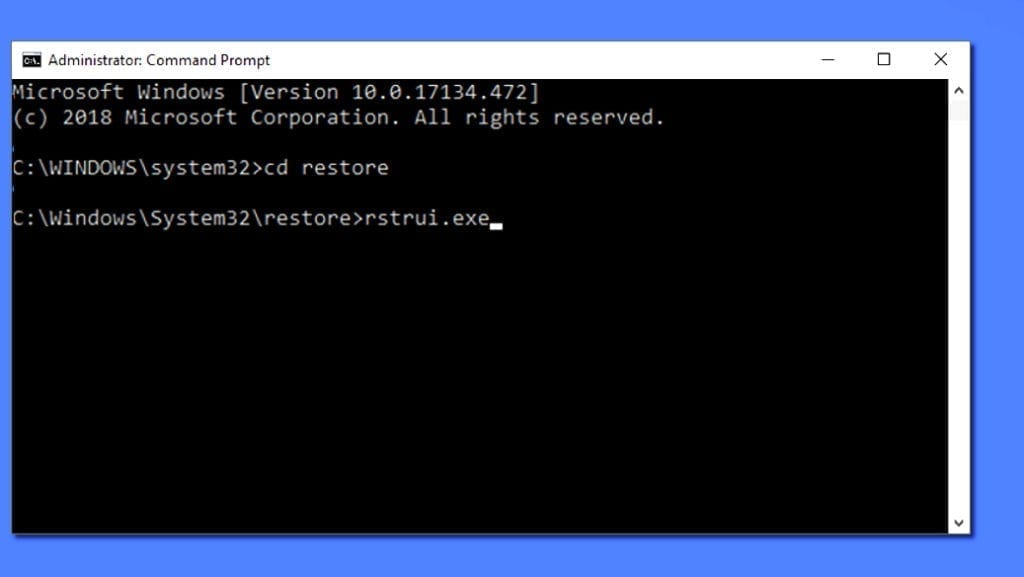
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
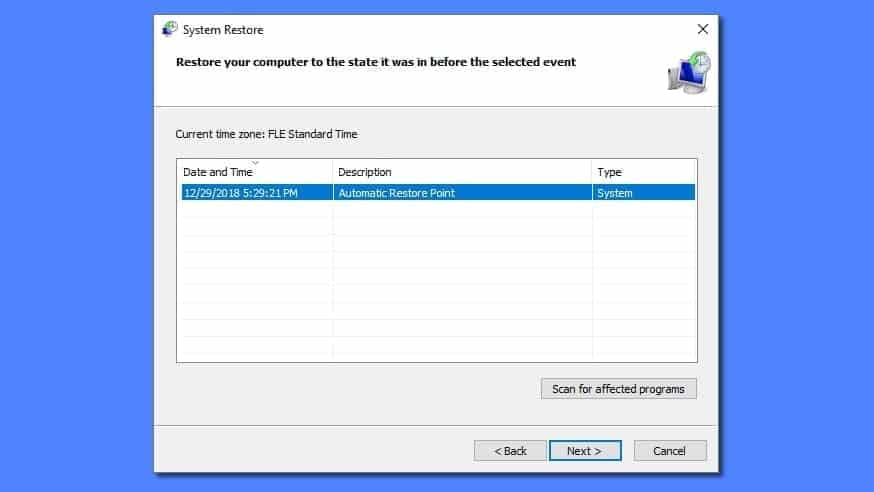
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Leave a Reply