Remove KODG Ransomware Virus (Decryption Guide 2021)
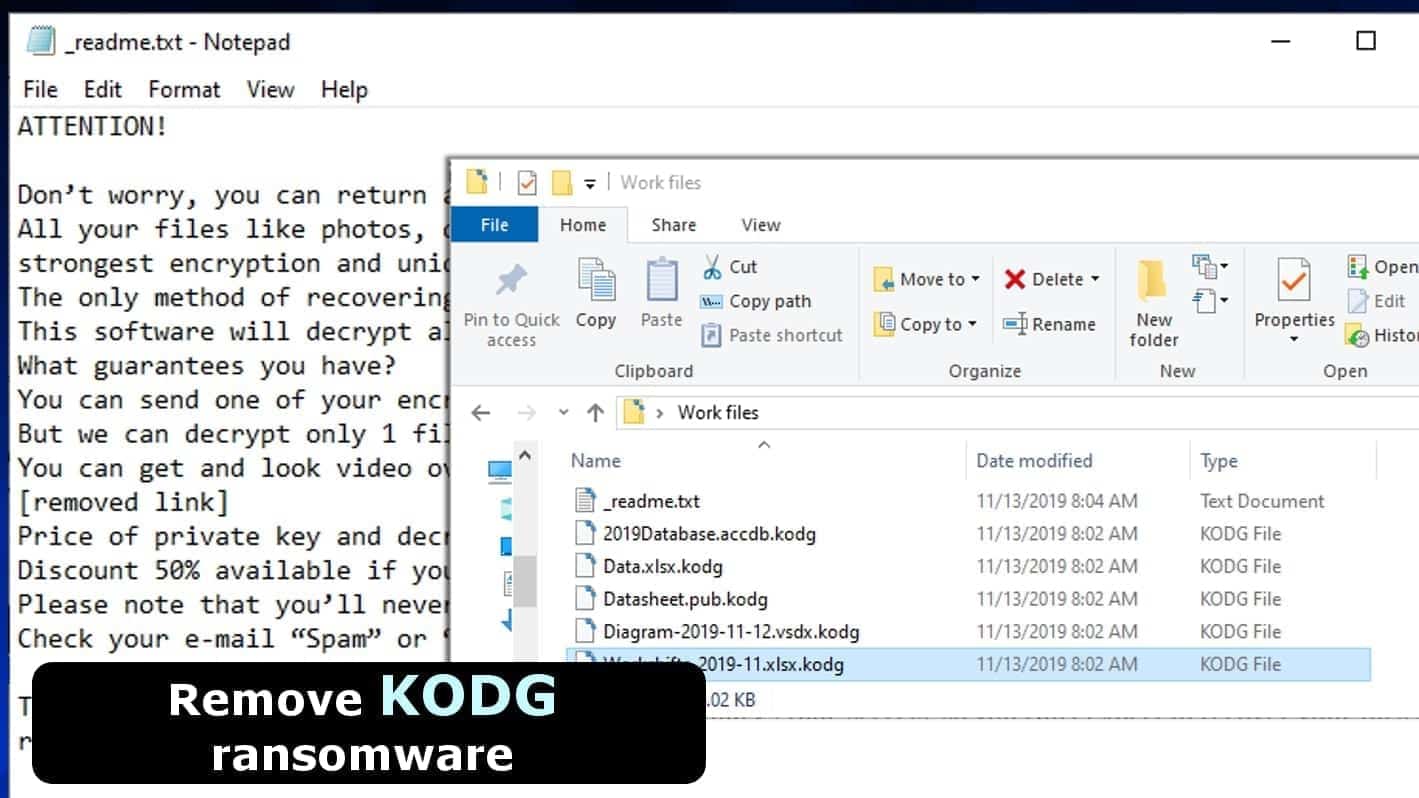
KODG ransomware makes personal files inaccessible to demand a ransom
Contents
KODG ransomware is a malicious computer virus which encrypts files using RSA cryptography and demands a ransom from the victim. This virus originates from STOP DJVU ransomware family. Once run, the virus disables firewalls, encrypts files adding .kodg file extensions to original data names, and leaves ransom-demanding notes called _readme.txt. The notes suggest contacting the criminals via restorefiles@firemail.cc or gorentos@bitmessage.ch for instructions how to buy STOP decryption tool for $980 or $490 in Bitcoin.
The virus uses either online or offline keys to encrypt data. It depends whether the virus manages to connect to its remote server during the encryption phase. An indication that it used offline key to encrypt data is t1 at the end of your personal ID in the ransom note _readme.txt. Victims of offline key attacks have a chance to restore some files in the future (read the FAQ below). Unfortunately, the same cannot be said about victims affected by the online keys.
The attackers lock files safely as they want to force you to pay up
If your files were encrypted and you can’t find a way to open .kodg extension files, you must know that DJVU ransomware uses an exceptionally complex way to encode data.
There is no way to recover it using any third-party tools. For example, similar encryption is used to secure military-grade secrets, so you can’t expect to recover your files no matter how important they were. Currently, the only way to restore files is to use data backups or pay up, which we do not recommend doing.
The attackers suggest sending one file for decryption as they want to prove that they actually are capable of restoring the data if the ransom is paid. However, please remember that all they want is money and they might not restore your files even if you pay.
One of the victims reported that KODG file virus developers were quick to respond with one decrypted file, but disappeared as soon as the victim asked for more time to collect the ransom sum.
Threat Summary
| Name | KODG ransomware virus |
| Threat Type | Ransomware (originates from STOP/DJVU Family) |
| Ransom | $490-$980 |
| Encryption Used | RSA-2048 |
| Decryption | Impossible. Recover files using a backup or wait for the offline key. The last option is to pay the ransom |
| Distribution | Illegal software activation tools such as software cracks, keygens (typically downloaded from various shady file sharing sites) |
| Additional information | Installs Azorult Trojan (password-stealing virus) |
| Removal | Remove using a trustworthy antivirus software of your choice |
FAQ: Understand data recovery options
The primary goal for every KODG ransomware victim is to recover files. Hundreds of victims are looking for solution to restore years of memories, personal files, work documents and other relevant information lost in a blink of an eye. However, you must realize that all of that happened due to a mistake you made to download illegal files online, as the only way used for DJVU distribution is illegal software activation tools.
Now that your files are encrypted, here’s a fact sheet you need to know presented in a form of Frequently Asked Questions.
You can recover .kodg files using data backups as soon as you remove the ransomware from your PC.
KODG ransomware uses online or offline key to encrypt data, depending if it manages to establish connection with its remote server. Files encrypted with offline key might be possible to decrypt in the future as soon as the security researchers will succeed in extracting the key. If encrypted with online key, free data recovery is nearly impossible.
We recommend removing this ransomware using a trustworthy antivirus tool. The vast majority of antivirus programs can identify and successfully delete the said ransomware along with Azorult Trojan.
To protect yourself after this variant of DJVU and Azorult Trojan attack, scan your computer with trustworthy security software while in Safe Mode. Then change all of your passwords, ESPECIALLY those saved in your browser.
The only factor that determines whether you can restore your data is the ending of your personal ID. If it ends with t1, it means that an offline key was used to lock your files. Please be patient and wait for and update for STOP decryptor by Emsisoft.
It means that part of your files were encrypted with online and part with offline key.
If you want to learn more about data recovery options for DJVU ransomware victims, please check this guide.
If you have become a victim of this DJVU ransomware variant, please read the instructions provided below and remove KODG file virus safely.
The virus reaches victims via illegal downloads
KODG ransomware is distributed via online downloads that help to activate premium software without paying the subscription fee. In other words, DJVU variants such as KODG, PEET, MBED and others are waiting for victims in a form of software cracks and keygens. You may also install it along with some KMSPico downloads.
It is understandable why the ransomware developers use this technique to infect victims. Such downloads are extremely popular and computer users tend to ignore security experts’ warnings about dangers originating from interaction with them.
Remove KODG virus and take actions to recover your data
Please remove KODG ransomware virus before taking any actions regarding data recovery. Please do not plug your data backup into your computer before the malware is completely eliminated from your PC. Otherwise, the virus can corrupt your data backup as well.
We recommend using KODG removal guidelines presented below. These will help you to boot your computer in a safe environment. This way, you’ll succeed to run your antivirus without any interruptions.
As mentioned earlier, there are no decryption tools for this STOP/DJVU malware variant. However, if you can see an indication of offline key attack, you can hope to restore some files in the future. Meanwhile, concentrate on searching for data backups and changing your passwords.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
KODG Ransomware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove KODG Ransomware files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
REMOVE MALWARE & REPAIR VIRUS DAMAGE
1 Step. Get robust antivirus to remove existing threats and enable real-time protection
INTEGO Antivirus for Windows provides robust real-time protection, Web Shield against phishing and deceptive websites, blocks malicious downloads and blocks Zero-Day threats. Use it to remove ransomware and other viruses from your computer professionally.
2 Step. Repair Virus Damage on Windows Operating System Files
Download RESTORO to scan your system for FREE and detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Remove UIGD Ransomware Virus (DECRYPT .uigd FILES)
UIGD ransomware encrypts all files on a computer, asks for a ransom UIGD ransomware is…
Remove EYRV Ransomware Virus (DECRYPT .eyrv FILES)
EYRV ransomware takes your computer files hostage, demands a ransom EYRV ransomware is a destructive…
Private Internet Access Review 2022: Fast, Secure & Cheap VPN
Private Internet Access (PIA) VPN maintains its long-term role as a leader Private Internet Access…
Remove XCBG Ransomware Virus (DECRYPT .xcbg FILES)
XCBG ransomware aims to lock your files and demand a ransom XCBG ransomware is a…
Remove BPQD Ransomware Virus (DECRYPT .bpqd FILES)
BPQD ransomware encrypts all computer files, demands a ransom from the user BPQD ransomware is…
Remove KQGS Ransomware Virus (DECRYPT .kqgs FILES)
KQGS ransomware is a hostile computer virus designed to encrypt all of your files KQGS…