Remove DPD Delivery Email Virus (Free Removal Guide)
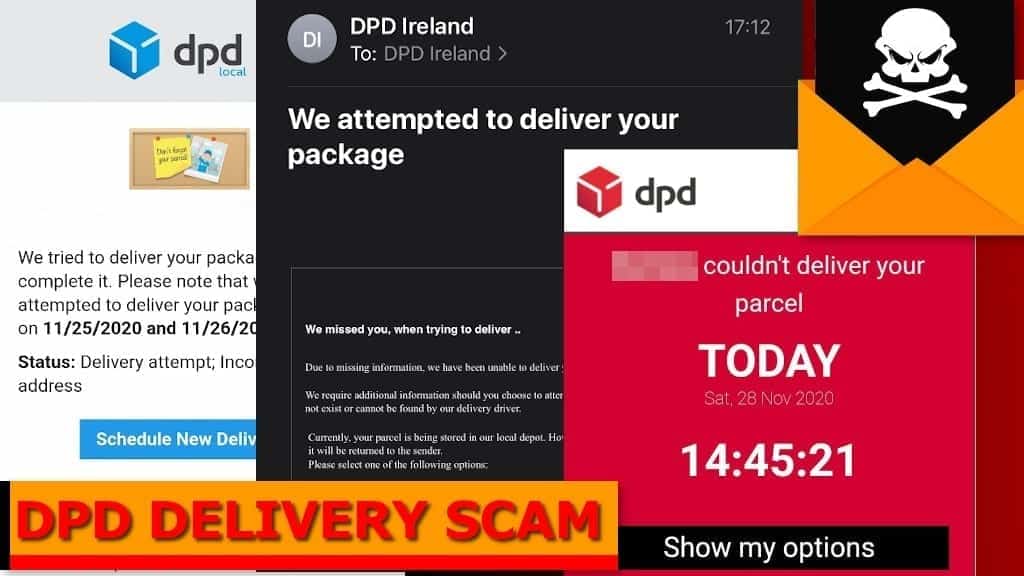
DPD Delivery Email virus targets Christmas Shoppers in 2020
Contents
DPD Delivery Email virus is an alternative name for DanaBot Trojan that is commonly distributed via fake DPD Delivery email scam campaigns. Alternatively, criminals craft these mails to swindle money or information from unsuspecting victims. The scammers behind these emails create deceptive subject lines, such as “Your Parcel is on hold,” “Reassuring parcel delivery,” “You have missed a parcel” or “Your parcel is on its way,” “To schedule a new delivery, a shipping fee must be paid” while the message body is designed to look like it was actually sent by the international parcel delivery company. The message typically suggests clicking Run Parcel Track or Show my options.
Opening a deceptive email message can end in several scenarios – from landing on a phishing page or a domain serving a JavaScript file that downloads automatically. If the victim opens this file, the malicious script inside of it downloads DanaBot Trojan and executes it on the system.
Similar email scam campaigns are widely used by attackers during Black Friday, Cyber Monday and Christmas season as thousands of computer users shop online. Therefore, after receiving a message from a legitimate parcel delivery company such as DPD seems like an awaited and natural event. Sadly, clicking on the provided links will lead to an installation of a highly dangerous password-stealer or a redirect to a phishing page.
Versions of DPD email scams
There are several scam scenarios that crooks have prepared for you. We will list each of them and explain the technique in detail.
Review information – To Schedule a new delivery, a shipping fee must be paid scam
This scam tries to trick the victim that the courier tried to deliver the parcel once or twice but the recipient “wasn’t here or there was no safe place to leave it.” The message suggests that recipient’s action is required, and since the first and second delivery attempt was free of charge, now the recipient must pay a fee. Beware that these messages do not come from legitimate DPD, but from a scammer who tries to impersonate it. An example of a scam email is shown below.
Another example of the same scam, taking the victim to a phishing website that asks entering credit card details:
Malware distributed via email can steal your banking information
The most recent DPD Delivery Email Scam is made to infect computers with DanaBot Trojan, a virus with a rich set of features. The virus itself might hide in several locations throughout the message – in the “Run Parcel Track” button, as well as in the “Find out more” one, which supposedly should download the DPDgroup app.
The DanaBot Trojan was first noticed in 2018, and has significantly evolved since then. It sends detailed information about the infected system to its Command & Control server, as well as user’s desktop screenshot. It also uploads the list of files on the user’s hard disk. The uploaded information, as well as all downloads, are encrypted with MS CryptAPI AES256.
The main functionality of this Trojan is recognition of popular websites and creating fake forms on them. Victims are then prompted to enter login or credit card details.
The Trojan also employs another method, abusing the p.a.c.k.e.r. framework to compress and obfuscate malicious code for creating communication way with the Command & Control server.
Web injections is a common technique used by banking Trojans like Gozi or Zeus. Stolen information (such as login names, email addresses, passwords, credit card numbers, PIN codes, etc.) can be used to hijack user’s accounts, rob the victim financially, or use for extortion later.
That said, if you suspect that you have unintentionally opened a malicious file or a phishing domain, we strongly recommend you to remove DPD Delivery Email virus as soon as possible. For identifying and removing this malware, we recommend using anti-malware software of your choice. To repair virus damage on the system and registry, we recommend running a scan with SYSTEM MECHANIC ULTIMATE DEFENSE . Finally, if you disclosed some of your banking details, we recommend contacting your bank immediately.
| Name | DPD Delivery Email Virus |
| Type | Scam, Phishing, Banking Malware, Trojan |
| Subject lines used in spam campaigns | Your Parcel is on hold, Reassing parcel delivery, You have missed a parcel, Your parcel is on its way, Your DPD parcel will be delivered tomorrow, DPD – Pending delivery, Review information – To Schedule a new delivery, a shipping fee must be paid |
| Distributed malware | DanaBot malware |
| Attachments/links | Attached link or file leads to a malicious .js file download or phishing page |
| Detection names | Trojan:Win32/Casdet!rfn (Microsoft), Trojan.MalPack.GS (Malwarebytes), Trojan.GenericKD.44441555 (BitDefender), see full list on VirusTotal |
| Distribution | Email scam campaigns, mostly disguised behind legitimate parcel delivery company names |
| Removal | Remove the malware using robust anti-virus software. For after-removal care, scan with SYSTEM MECHANIC ULTIMATE DEFENSE |
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
How criminals distribute DPD Delivery Email virus?
DPD Delivery Email Virus (DanaBot) is distributed via various spam campaigns. Therefore, the criminals behind it have to do a little preparation before sending out thousands of emails. They tend to use email or mobile number lists made available on dark web forums during data breaches, public email lists, and other locations. Using an automated script, they can even customize the deceptive email to insert target’s name into the message body.
As described previously, the criminals tend to compose and design a message that looks like it was sent by a legitimate, well-known and trustworthy company such as DPD. In this recent case, the criminals disguise the malware download link behind the DPD tracking button as well as the “Find out more” link.
The criminals may also use the exec=run parameter to trigger the automatic malicious JS download.
How to avoid getting infected with email malware?
First of all, to avoid getting infected with DPD Delivery
DPD does not charge for redelivery, and the legitimate service offers a choice of leaving the parcel at your chosen alternative location or neighbour. If you received an email stating that a shipping fee must be paid to schedule new delivery, it is a scam and you should delete such email immediately.
To contact DPD, go to its official website https://www.dpd.com/
Email virus, we strongly recommend inspecting the email you received before clicking any links attached. The first thing that you should pay attention to is sender’s email address. If you notice any suspicious spelling mistakes or typos in the sender’s name, close such email and move it to Trash instantly. However, scammers nowadays know techniques that can help to spoof the legitimate email address, and it is harder for a regular user to notice such trickeries.
Next, we recommend inspecting the design and contents of such email. If you notice that the background, details, or other elements are misaligned, faulty, or the whole design does not look up-to-date, avoid clicking on attached links, no matter what. The criminals are not very good at grammar, either – so if you notice some mistakes, or the whole message body looks “unnatural,” stay away from it.
Another advice is to open a legitimate email from DPD you received earlier (if you already had deliveries from this company) and compare the emails.
Next, even if you manage to accidentally get infected with this malware, do not fill any forms that arise on various e-shopping or banking websites unexpectedly. Finally, if you believe that you have already entered some details into these fake forms, we strongly suggest contacting your bank as soon as possible, and inform them about such incident. You may even need to block your card and get a new one.
Remove DPD Delivery Email virus from your PC
It is extremely important to remove DPD Delivery Email virus from your computer as soon as possible. To identify components of this deeply-rooted malware, we strongly recommend running a system scan with a well-known anti-malware solution. Additionally, once you perform full removal of this virus, we suggest scanning with SYSTEM MECHANIC ULTIMATE DEFENSE to entirely repair damage done to your operating system (Windows).
Finalize DPD Delivery Email virus removal by protecting your security. We recommend changing all your login credentials for websites you visited and encountered the suspicious forms generated by DanaBot Trojan. Next, ensure that your bank card is secure – call your bank and inform them about the malware that has infected your computer.
Frequently Asked Questions
DPD does not charge for redelivery, and the legitimate service offers a choice of leaving the parcel at your chosen alternative location or neighbour. If you received an email stating that a shipping fee must be paid to schedule new delivery, it is a scam and you should delete such email immediately.
To contact DPD, go to the company’s official website https://www.dpd.com/ and choose your country to access Contact Us page. You might be automatically redirected to corresponding country’s page.
If you have opened the file, then yes, your computer was infected. However, if you didn’t, you should delete the file and empty the Recycle bin in your computer instantly. Such email came from a cyber criminal who simply tried to disguise himself as a DPD representative. Legitimate company emails never contain suspicious files that install malware on computers.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
DPD Delivery Email virus Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in Safe Mode with Networking, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to start Windows in Safe Mode:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove DPD Delivery Email virus files. It is very hard to identify files and registry keys that belong to the virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. We recommend using SYSTEM MECHANIC ULTIMATE DEFENSE , which can also restore deleted files. Additionally. we recommend repairing virus damage using RESTORO.
Special Offer
Compatibility: Microsoft Windows
See Full Review
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before the malware infiltration.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Private Internet Access Review 2022: Fast, Secure & Cheap VPN
Private Internet Access (PIA) VPN maintains its long-term role as a leader Private Internet Access…
Remove XCBG Ransomware Virus (DECRYPT .xcbg FILES)
XCBG ransomware aims to lock your files and demand a ransom XCBG ransomware is a…
Remove BPQD Ransomware Virus (DECRYPT .bpqd FILES)
BPQD ransomware encrypts all computer files, demands a ransom from the user BPQD ransomware is…
Remove KQGS Ransomware Virus (DECRYPT .kqgs FILES)
KQGS ransomware is a hostile computer virus designed to encrypt all of your files KQGS…
Remove VTYM Ransomware Virus (DECRYPT .vtym FILES)
VTYM ransomware description: a virtual menace to your files stored on the computer VTYM ransomware…
Remove FOPA Ransomware Virus (DECRYPT .fopa FILES)
FOPA ransomware is a new threatening computer virus that encrypts your files FOPA ransomware virus…