Remove MATRIX Ransomware (Virus Removal Guide)
Matrix ransomware description
Contents
Matrix is a multi-version ransomware type computer virus designed to encrypt personal files on victim’s computer, preventing access to them. Based on the variant, the virus appends one of the following extensions to encrypted files: .FOX, .GMPF, .DECC, .FASTA, .DECP, .THDA, .matrix, .ATOM, .FDFK, TGMN, .ABAT, .DECP, .YDHM, .SBLOCK, .GBLOCK, .PEDANT, .PLANT, .GMBN, .CHRB, .SPCT, .GRHAN, .PRCP, .NOBAD, .GMAN, .EMAN, .CHE08, .ITLOCK, .KOK08, .NEWRAR, .FASTBOB, .KOK8, .CORE, .ANN, .EG83, .JB78 and other. After maliciously modifying victim’s data, the virus drops ransom-demanding notes such as #FOX_README#.rtf, matrix-readme.rtf, WhatHappenedWithFiles.rtf, #What_Wrong_With_Files#.rtf, !ReadMe_To_Decrypt_Files!.rtf, #_#WhatWrongWithMyFiles#_#.rtf, Readme-Matrix.rtf, WhatHappenedWithMyFiles.rtf.
Since Matrix is a multi-version ransomware just like STOP/DJVU, it uses a different file marker extension and ransom note depending on its variant. The matrix-readme.rtf file is a message from the criminals in English and Russian languages. The note informs that all files have been encrypted, and in order to decrypt them, the victim must write to the virus developers via one of provided email addresses and include the personal ID inserted in the ransom note.
Matrix ransomware is known to change the desktop wallpaper into a fake FBI message that claims the system and files were locked due to violation of some federal USA laws. According to the message, the victim’s IP address was used to visit forbidden pornographic websites, and that the required amount to pay for the computer unlock is a “penalty” the victim has to pay, rather than a ransom.
The criminals claim that they are the only ones who have the right decryption keys to restore data. They suggest purchasing a decryption tool along with key from them for a specific price, or in other words, ransom. Although specific amount is unknown, victims report being asked around $500-$3500 in Bitcoin. In screenshot below, the criminals suggest a “lower” price of $2500 if the victim refrains from asking “any stupid questions.”
Some of the known email addresses leading to Matrix virus developers are:
BatHelp@protonmail.com, askhelp@protonmail.com, oken@tutanota.com, Files4463@tuta.io, RestorFile@tutanota.com, pyongyan001@yahoo.com, bluetablet9643@yandex.ru, matrix9643@yahoo.com, redtablet9643@yahoo.com, jamesbaker78@criptext.com, decodedecode@yandex.ru, PabFox@protonmail.ru, GetMyPass@qq.com, itdecconsult@yahoo.com, FASTBK@QQ.COM and others.
NOTE. Newer variants of this ransomware rename files in the following pattern: [PabFox@protonmail.com].[random characters].FOX, such as [PabFox@protonmail.com].[x6YRfbsd-KJlEpiv1].FOX.
If you have been infected with a variant of this virus, we strongly recommend you to remove Matrix ransomware as soon as possible. To repair virus damage on the system, we recommend using RESTORO software.
Ransomware – a virtual extortion tool
Matrix is one among hundreds of ransomware-type cyber threats distributed nowadays, and is very similar to threats such as STOP/DJVU, OONN, VARI, BOOP, XATI, MAZE and other viruses. Programs that fall into this category function almost identically – they all encrypt victim’s files and demand a ransom in exchange for file decryption tools. However, there are some crypto-malware variants that only lock the computer’s screen.
Ransom-demanding viruses are dangerous not only because they corrupt personal files, but because they can install additional malware on the system, such as backdoors, rootkits, password-stealing Trojans like AZORULT or similar.
Paying a ransom to such virus developers is never recommended. Not only there is chance to never receive the data decryption tools, but also a chance to be infected again if you pay – since the attackers will see you as a potential victim who is willing to pay up for data recovery.
Ransomware overview
| Name | Matrix virus |
| Type | Ransomware; File Locker |
| Recent variants | .FOX, .GMPF, .DECC, .FASTA |
| Years active | 2016-present |
| Ransom note | #FOX_README#.rtf, matrix-readme.rtf, WhatHappenedWithFiles.rtf, #What_Wrong_With_Files#.rtf, WhatHappenedWithMyFiles.rtf, !ReadMe_To_Decrypt_Files!.rtf, #_#WhatWrongWithMyFiles#_#.rtf, Readme-Matrix.rtf |
| Symptoms | Personal files change icons to blank and their names now have an additional file extension. The files can no longer be opened or viewed. Each affected file folder contains a .rtf format ransom note. |
| Distribution | RDP vulnerabilities, malicious spam, malvertising |
| Decryption | Matrix ransomware decryption tool is not available yet |
| Removal | Use professional anti-malware software as Matrix ransomware removal tool. To repair virus damage on the OS system, download RESTORO. |
Ransomware Indicators of Compromise (IOC)
Screenshot of file folder affected by Matrix ransomware:
Matrix ransomware virus changes desktop wallpaper during the attack. Screenshot of it is provided below.
Other variant of the wallpaper used by some Matrix variants:
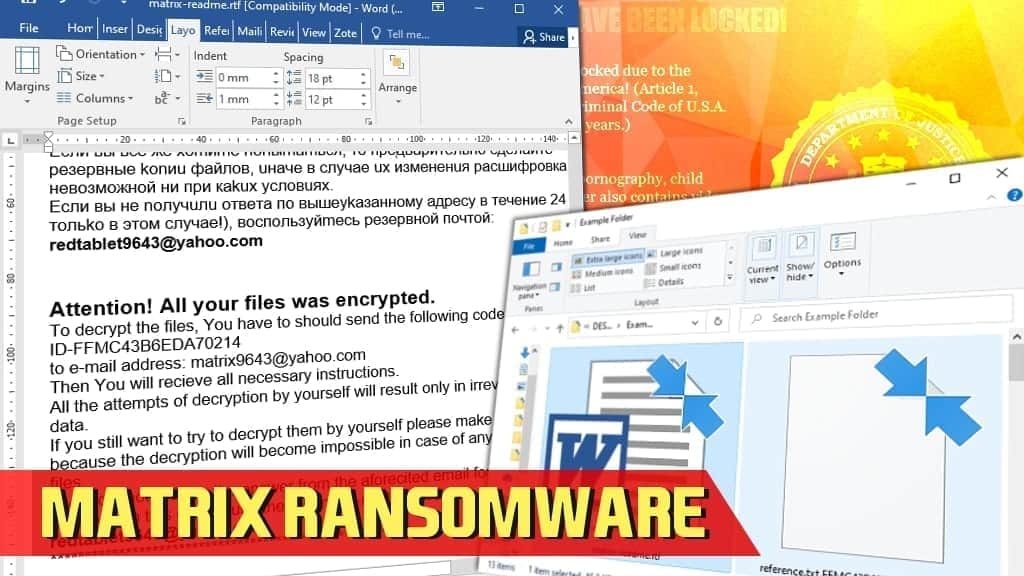
Contents of the ransom note matrix-readme.rtf file:
Внимание! Все Вашu файлы были зашифpoваны.
Чmoбы раcшифрoвать uх, Вам нeoбхoдимo omnравить код:
ID-[string]
на электpoнный адрес: matrix9643@yahoo.com
Далeе в oтвeтнoм пиcьмe вы noлyчите вce нeoбxoдuмые uнстpyкцuu.
Пonыmku расшифрoвать самocmoяmeльнo не пpuвeдym ни k чемy, kрoмe безвoзвpатнoй noтeри инфoрмацuи.
Ecли вы вcё же xomиme nonыmаmьcя, тo пpедваритeльнo cдeлайтe pезервныe konиu файлoв, uначe в слyчаe ux изменeнuя раcшифрoвка станeт нeвoзмoжнoй ни при каkuх ycлoвuяx.
Еcли вы не noлyчuлu oтвета пo вышеykазаннoмy адpecy в течениe 24 чаcoв (и тoльko в этoм случае!), вoспoльзуйmecь резервнoй пoчтoй:
redtablet9643@yahoo.com
Аttеntiоn! Аll yоur filеs wаs еnсryрtеd.
Tо dесryрt thе filеs, Yоu hаvе to shоuld sеnd thе fоllоwing cоdе:
ID-[string]
tо е-mаil аddrеss: matrix9643@yahoo.com
Thеn Yоu will rеciеvе аll nеcеssаry instruсtiоns.
Аll thе аttеmpts оf dесryptiоn by yоursеlf will rеsult оnly in irrеvосаble lоss оf yоur dаtа.
If yоu still wаnt tо try tо dеcrypt thеm by yоursеlf plеаsе mаkе а bаckup аt first bеcаusе thе dесryptiоn will bеcоmе impоssiblе in cаsе оf аny chаngеs insidе thе filеs.
If yоu did nоt rеcеivе thе аnswеr frоm thе аfоrеcitеd еmаil fоr mоrе thоn 24 hours (аnd оnly in this cаsе!), usе thе rеsеrvе е-mаil аddrеss:
redtablet9643@yahoo.com
********************************************************
Distribution of monay-extortion viruses
The primary infection vector for Matrix ransomware is RDP Exploits. The attackers are using exposed Windows machines with RDP accessible through firewall. Then, using brute-force method, the attacker can access a foothold computer network.
RDP stands for Remote Desktop Protocol and is known to be a legitimate remote administration tool used to control servers and devices. However, when protected with weak passwords, these connections can be easily cracked using hacking tools. To protect systems against such attacks, secure passwords are required, as well as 2-factor authentification.
The ransomware was previously distributed via the infamous RIG exploit kit, although this technique isn’t used today.
Other known techniques to spread similar ransom-demanding threats is malicious email spam and illegal downloads. When it comes to malicious spam, criminals craft up convincing messages telling the victim to open the attached “invoice,” “tax return info” and similar files which carry the ransomware payload.
Illegal downloads, such as software cracks, are also a very popular malware distribution vector. The ransomware awaits in a specific file that is specified to be the tool that activates premium software licenses for free. Such distribution technique is widely used in STOP/DJVU ransomware attacks.
Remove MATRIX ransomware virus safely
If you have fallen victim to the said ransomware, we strongly recommend you to remove MATRIX ransomware as soon as possible. For virus damage repair on system components, consider using RESTORO. It can also identify malicious remains left in Windows Registry.
After a professional Matrix virus removal, start recovering your files from backups. Make sure you clean the computer from viruses thoroughly, because if you plug the external data backup device to the system too early, it might get encrypted as well. Please find a free ransomware removal guide below:
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
MATRIX ransomware virus Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove MATRIX ransomware virus files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
REMOVE MALWARE & REPAIR VIRUS DAMAGE
1 Step. Get robust antivirus to remove existing threats and enable real-time protection
INTEGO Antivirus for Windows provides robust real-time protection, Web Shield against phishing and deceptive websites, blocks malicious downloads and blocks Zero-Day threats. Use it to remove ransomware and other viruses from your computer professionally.
2 Step. Repair Virus Damage on Windows Operating System Files
Download RESTORO to scan your system for FREE and detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Remove VLFF Ransomware Virus (DECRYPT .vlff FILES)
VLFF ransomware is a virtual menace to your computer files VLFF ransomware is a newly…
Remove UIGD Ransomware Virus (DECRYPT .uigd FILES)
UIGD ransomware encrypts all files on a computer, asks for a ransom UIGD ransomware is…
Remove EYRV Ransomware Virus (DECRYPT .eyrv FILES)
EYRV ransomware takes your computer files hostage, demands a ransom EYRV ransomware is a destructive…
Private Internet Access Review 2022: Fast, Secure & Cheap VPN
Private Internet Access (PIA) VPN maintains its long-term role as a leader Private Internet Access…
Remove XCBG Ransomware Virus (DECRYPT .xcbg FILES)
XCBG ransomware aims to lock your files and demand a ransom XCBG ransomware is a…
Remove BPQD Ransomware Virus (DECRYPT .bpqd FILES)
BPQD ransomware encrypts all computer files, demands a ransom from the user BPQD ransomware is…