Remove Drive-By Exploit Email Scam (2022 Guide)
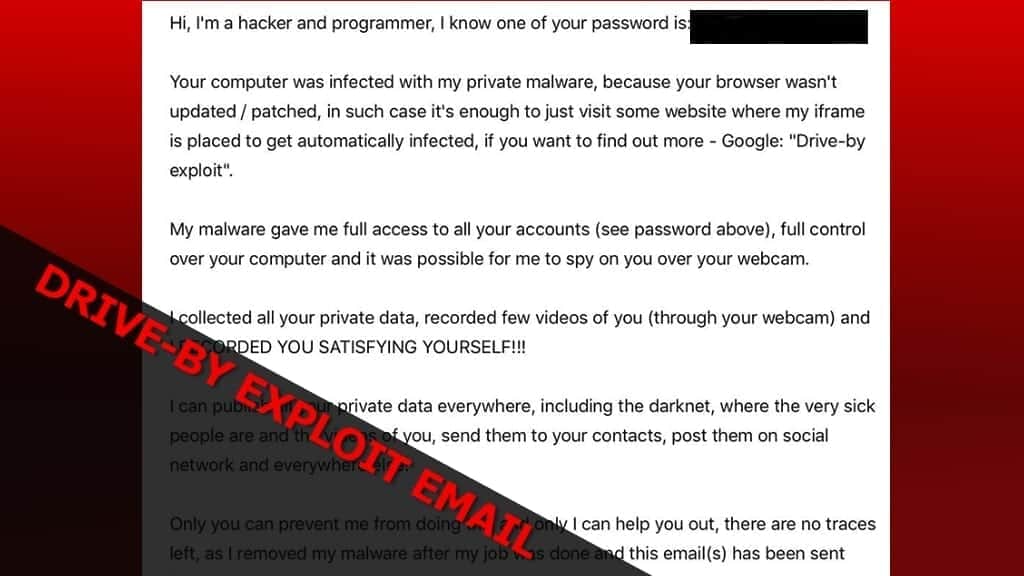
Drive-by exploit email claims to know victim’s passwords and more
Contents
Drive-by exploit email is an email scam campaign which claims that victim’s computer has been infected with hacker’s private malware. The email states that a hacker and programmer knows one of victim’s passwords and more. Following that, the message threatens to expose victim’s activities online if one refuses to pay $800-$1200 in Bitcoin. The described email is also known as sextortion scam, since the attackers claims to have recorded the victim “satisfying oneself.” The scam targets Windows, Mac and Android users.
Such threatening Drive by Exploit Bitcoin Email might scare and leave the recipient in a hopeless situation – personal information seems jeopardized, and the only way out seems to be cooperation with the intruder. It is crucial to get acquainted to the context and possible solutions of this blackmailing scheme in order to secure your personal information and finances.
Drive-by exploit isn’t real – learn why
However, you should calm down because Drive -by exploit certainly isn’t real. It is a term used in the scam campaign to frighten the victims who are not tech-savvy. The actual terms for the attack method are drive-by download or drive-by install.
However, if you’re convinced that the alleged hacker has access to your private data just because he mentioned your password in the email, you should check if the password was exposed in one of the recent online data leaks. You can do so by visiting HaveIBeenPwnd website. If it was, it is highly likely that the attacker has bought your email address along with login names and passwords from the dark web and now uses such information to threaten you.
Threat Summary
| Name | Drive By Exploit Email |
| Attack type | Social engineering; Scam |
| Statements | The attackers claims that victim’s computer was infected with private malware. As a consequence, all accounts were accessed and the attacker was able to spy and record the victim via webcam. The attacker asks to pay a ransom in Bitcoin to avoid being exposed on the dark web. |
| Ransom price | $800-$1200 |
| Distribution | Spreads via deceptive email campaigns |
| Attacker email (spoofed) | kevin.garvey@eypuk.co.uk |
| Bitcoin wallet address | 13yAsTuS6MyjNUYde4EBabTZJFfZBRTZu1, 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ, 1MnUgqSkToq3j7ozwjSh54m1WxWZ3Xqym6 and others |
| Recommended actions | Change the exposed passwords on all accounts, delete the scam email message and scan your system for malware |
| Removal | Remove Drive-By Exploit Email, then run a full system scan using anti-malware such as System Mechanic Ultimate Defense |
Full text presented in the deceptive email:
Hi, I’m a hacker and programmer, I got access to your account – [password]
Your device was infected with my private malware, because your browser wasn’t updated / patched,
in such case it’s enough to just visit some website where my iframe is placed to get automatically infected, if you want to find out more – Google: “Drive-by exploit”.
My malware gave me full access to all your accounts, full control over your OS and it was possible for me to spy on you over your webcam.
I collected all your private data, recorded few videos of you (through your webcam) and I RECORDED YOU SATISFYING YOURSELF!!!
I can publish all your private data everywhere, including the darknet, where the very sick people are and the videos of you,
send them to your contacts, post them on social network and everywhere else!
Only you can prevent me from doing this and only I can help you out, there are no traces left,
as I removed my malware after my job was done and this email(s) has been sent from some hacked server…
The only way to stop me, is to pay exactly 726$ in bitcoin (BTC).
It’s a very good offer, compared to all that HORRIBLE **** that will happen if you don’t pay!
You can easily buy bitcoin on the next services: paxful, coinbase or check for bitcoin ATM near you, or Google for other exchanger.
You can send the bitcoin directly to my wallet, or create your own wallet first here: blockchain com, then receive and send to mine.
My bitcoin wallet is: 14LYbckmC9gKJ6LR1JAWaKSsCojZfURbzH, 1MYJjmYScwmFfthAQNXWb5fhNMRVcAiZd, 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ
Copy and paste it, it’s (cAsE-sEnSEtiVE)
You got 72 hours time.
As I got access to this email account, I will know if this email has been read.
Next time update your browser before browsing the web!
The scammer knows one of your passwords due to data breach
The majority of victims are worried about the attackers claims because he/she has included a real password in the message. However, it is STILL not a factor to start panicking. Let us explain why.
As mentioned previously, the composer of the deceptive message states that by taking full control of your system he managed to record you in a sensitive context. Criminal’s demands, which usually are financial, then follow, and victim is informed that without response, all of this material will be publicized.
But even though your old password is accessible to cyber criminals, it is important to realize that these kinds of leakages occur due to a security breach in the website on which the password was used. You can check whether your password was breached previously on haveibeenpwned.com. If you’re still worried, consider implementing Drive-by exploit removal using trustworthy anti-malware such as System Mechanic Ultimate Defense and scan your system for dangerous software.
In fact, sometimes the criminals dig up password which you used years ago. It is worth mentioning that typically the sites that have been breached do not sustain high security standards, (i. e. forums, blog sites etc.). So, as long as you are not using the same password on every internet account, you should be fine.
In other words, the criminal is just trying to scam – persuade the person into believing that his system is breached completely, even though usually that is not the case. Despite that, we still recommend visiting the aforementioned page and changing login information for the breached accounts.
Typically, the breaches in your system security happen due to Trojan malware, which can be downloaded through drive-by downloads with or without the user’s consent. This should especially concern those who tend to download inattentively using various file sharing networks and file-hosting sites (i.e. uTorrent, eMule, zippyshare, etc.), open links in deceitful emails etc.
Notably, Trojan is widely known as a malware which can impose various abhorrent actions on victim’s PC, often leaving the system completely useless until appropriate fix is done. Hence, every user should periodically take certain actions in order to secure the PC and especially after getting these kinds of threats.
How to Remove Drive-by exploit safely
Although the email you received is simply a scam, most likely you still want to scan your system just to calm down and be sure. In such scenario, you can remove Drive-by exploit automatically and detect various spyware/malware remains using anti-malware software like System Mechanic Ultimate Defense.
Likewise, drive-by exploit removal should also concern Android and Mac users, since this scam is not restricted only to Windows PCs. Even if the previously mentioned actions did not take place, it is important to delete the email immediately and follow the steps on how to remove any malicious programs or viruses.
While the drive-by exploit password is not a threat in itself, there is still a possibility that the victim’s system has been targeted directly. This might happen in various ways, including opening malicious links or files attached to the email.
A full system scan is highly recommended and should be performed regularly because you can never be sure if your system is not breached, since the symptoms of having particular malware in your system could come to light only when it is too late. The removal of drive-by exploit and other viruses should be done using only trustworthy antivirus or anti-malware software. In order to ensure that, we recommend checking our reviews on them. To completely terminate any virus from your system follow the steps below:
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
DRIVE-BY EXPLOIT Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in Safe Mode with Networking, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to start Windows in Safe Mode:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove DRIVE-BY EXPLOIT files. It is very hard to identify files and registry keys that belong to the virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. We recommend using SYSTEM MECHANIC ULTIMATE DEFENSE , which can also restore deleted files. Additionally. we recommend repairing virus damage using RESTORO.
Special Offer
Compatibility: Microsoft Windows
See Full Review
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before the malware infiltration.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Remove RGUY Ransomware Virus (DECRYPT .rguy FILES)
Description of RGUY ransomware which is designed to encrypt files on computers worldwide RGUY ransomware…
Remove MMUZ Ransomware Virus (DECRYPT .mmuz FILES)
MMUZ ransomware arises from the infamous STOP/DJVU data-encrypting malware group MMUZ ransomware is a dangerous…
Remove VLFF Ransomware Virus (DECRYPT .vlff FILES)
VLFF ransomware is a virtual menace to your computer files VLFF ransomware is a newly…
Remove UIGD Ransomware Virus (DECRYPT .uigd FILES)
UIGD ransomware encrypts all files on a computer, asks for a ransom UIGD ransomware is…
Remove EYRV Ransomware Virus (DECRYPT .eyrv FILES)
EYRV ransomware takes your computer files hostage, demands a ransom EYRV ransomware is a destructive…
Private Internet Access Review 2022: Fast, Secure & Cheap VPN
Private Internet Access (PIA) VPN maintains its long-term role as a leader Private Internet Access…