Remove BOZON Ransomware Virus (DECRYPT .bozon FILES)
BOZON ransomware is a malicious virus that encrypts all data on infected computers
Contents
BOZON ransomware is a malicious computer virus that seeks to encrypt all files on target computers and demand ransoms from their users. Our researchers suggest that users typically download this threat via websites providing cracked software versions. After being launched on the target system, the ransomware encrypts all files on it and connected drives and marks each file with .bozon extension. To illustrate, a file originally named 1.jpg becomes 1.jpg.bozon and the same process will be repeated on all data. The virus also saves a ransom note file called FILE RECOVERY.txt on victim’s desktop.
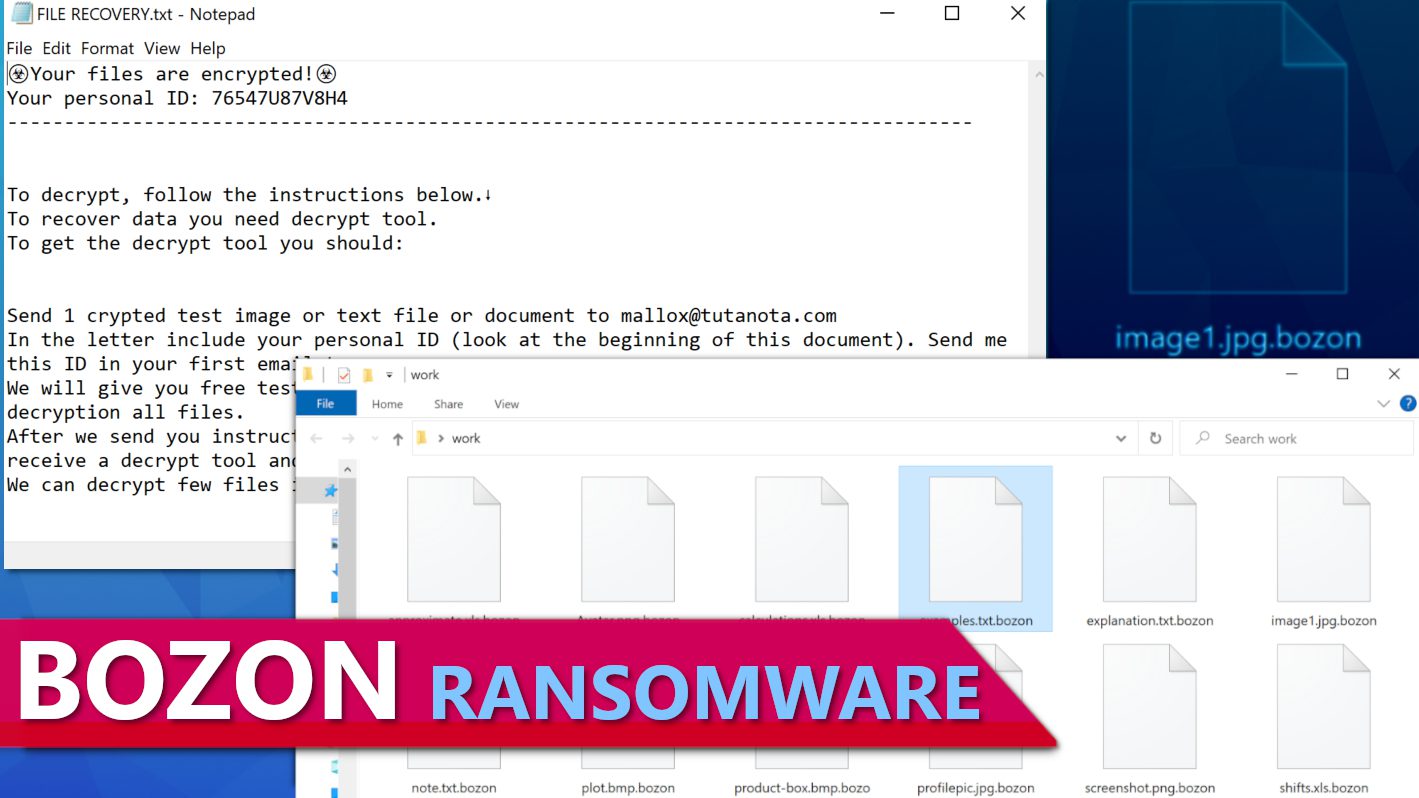
The aim of BOZON ransomware virus is to extort computer users after taking all of their personal files hostage. The ransom note called FILE RECOVERY.txt contains a message from the cybercriminals behind the attack who suggest that the only way to decrypt files is paying a ransom. They instruct the victim to send an email using a provided email address (mallox@tutanota.com) and attach one encrypted test image or text file for test decryption. They also instruct to include the victim’s personal ID (provided in the ransom note) in the email.
The criminals promise to respond quickly and send back decrypted file to prove that they’re capable to decrypt all of victim’s files. On top of that, they promise to provide the ransom amount they demand.
No matter the circumstances, you should NOT TO PAY THE RANSOM. It rarely helps to restore access to lost files, moreover, by paying up, you would help cybercriminals to fund further criminal operations and infect more people. Finally, cybercriminals tend to have a habit of targeting victims who are willing to pay the ransom. For more information regarding ransomware response, check the official FBI recommendations.
Ransomware-type viruses often travel along other malware, such as password-stealing Trojans or cryptocurrency miners. For this reason, we recommend that you remove BOZON ransomware virus and related threats without a delay. In order to restore your computer to clean state, boot your PC in Safe Mode with Networking (use instructions provided below) and run an up-to-date antivirus to ensure complete malware removal. Afterward, we recommend downloading RESTORO and performing a full system scan to identify files that can be repaired from virus damage.
Ransomware Summary
| Name | BOZON Ransomware Virus |
| Type | Ransomware; Crypto-malware; Virtual Extortion Virus |
| Family | BOZON |
| Extension | .bozon |
| Cybercriminal emails | mallox@tutanota.com |
| Damage | The ransomware encrypts all files, marks them with .bozon extension and drops FILE RECOVERY.txt ransom note on computer’s desktop. The virus deletes Volume Shadow Copies from the system to prevent easy data recovery for the victim. It may intentionally infect victim’s computer with additional malware. |
| Ransom note | FILE RECOVERY.txt |
| Ransom demand | $400-$900 in Bitcoin |
| Distribution | Spreads via illegal torrent downloads, software cracks, key generators, tools like KMSPico and phishing email attachments |
| Detection names | Trojan:Win32/Sabsik.FL.B!ml (Microsoft), Gen:Trojan.Mardom.MN.9 (B) (Emsisoft), HEUR:Trojan-Downloader.MSIL.Seraph.gen (Kaspersky), Gen:Trojan.Mardom.MN.9 (BitDefender), Trojan.Downloader.MSIL.Generic (Malwarebytes), ML.Attribute.HighConfidence (Symantec) see all detection name variations on VirusTotal |
| Removal | Remove ransomware and related malware from your PC using trustworthy software. To repair virus damage on Windows OS files, consider scanning with RESTORO (secure download link). |
REPAIR VIRUS DAMAGE
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
Screenshot of FILE RECOVERY.txt ransom note dropped by this ransomware.
Screenshot of data folder containing files encrypted by BOZON ransomware.
How ransomware-type viruses are distributed
Ransomware-type computer threats like BOZON virus usually await for potential victims in illegal online downloads, mostly pirated software versions. Victims tend to download them via peer-to-peer file sharing clients or directly from rogue websites offering password-protected .ZIP or .RAR archives. After opening the alleged installation setup, the malicious program begins modifying system settings, dropping additional executables, ransom notes, and encrypting victim’s files stored on the computer.
Avoid searching for free versions of premium software versions as these are packed with malware most of the time. When you’re in need of specific program, check its official developer’s website or look for deals in confirmed partners’ websites.
Another typical ransomware distribution method relies on phishing emails composed to look like they’re coming from a trustworthy entity, such as well-known company or even government. The criminals tend to create malware-injected documents that may come in DOCX, PDF, XLS, JS and other formats. Once launched, the malicious script injected in these files activates to download and run the ransomware payload on the computer.
For this reason, stay away from emails you did not expect to receive. Also ignore emails that raise even the slightest suspicion to you, for instance, if you can spot many typo mistakes, suspicious greeting line or a spoofed email address.
Finally, victims may get infected if they click on suspicious ads online, especially those that aggressively claim you need to install some software updates. Fake software update tools are typically used to spread junkware or severe malware, so you should bypass them at all costs. If you want to install legitimate and secure software updates, you should check for them via your software’s settings directly or head to its official developer’s website.
Remove BOZON Ransomware Virus and Decrypt Your Files
In case you’ve fallen victim to a ransomware attack, it is important to stop the malware before it does more damage to your system. For this reason, we recommend you to remove BOZON ransomware virus and related malware from your computer using instructions provided below. Booting the PC in Safe Mode with Networking helps to neutralize malicious processes and make them unable to stop your security software from identifying dangerous files.
Additional tool we recommend using after BOZON ransomware virus removal can be downloaded here – RESTORO. It is an excellent tool for identifying and repairing virus damage on Windows OS files. If you have a drive containing a data backup, then you can restore your files using it, but make sure you plug it in your computer only after removing all threats from your computer.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software and then using the following tool to repair virus damage to Windows system files:
REPAIR VIRUS DAMAGE TO YOUR COMPUTER
RESTORO provides a free scan that helps to identify hardware, security and stability issues and presents a comprehensive report which can help you to locate and fix detected issues manually. It is a great PC repair software to use after you remove malware with professional antivirus. The full version of software will fix detected issues and repair virus damage caused to your Windows OS files automatically.
RESTORO uses AVIRA scanning engine to detect existing spyware and malware. If any are found, the software will eliminate them.
Read full review here.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
BOZON Ransomware Virus Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove BOZON Ransomware Virus files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
REPAIR VIRUS DAMAGE
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Remove UYJH Ransomware Virus (DECRYPT .uyjh FILES)
UYJH ransomware seeks to encrypt all of your personal files UYJH ransomware is a computer…
Remove TUID Ransomware Virus (DECRYPT .tuid FILES)
TUID is a ransomware-type virus that encrypts all files on a computer TUID ransomware is…
Remove UDLA Ransomware Virus (DECRYPT .udla FILES)
UDLA ransomware attacks computers to encrypt all files in them UDLA ransomware is a newly…
89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ Malware (Clipboard Hijacker)
Overview of 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ is a malicious program that falls into clipboard hijacker category.…
Remove GTYS Ransomware Virus (DECRYPT .gtys FILES)
GTYS ransomware is a malicious computer virus created to extort you GTYS ransomware is a…
Remove MPAG Ransomware Virus (DECRYPT .mpag FILES)
MPAG ransomware locks files on the computer, demands a ransom MPAG ransomware is a new…