Trust Wallet Scam: Crypto Phishing Scam Explained
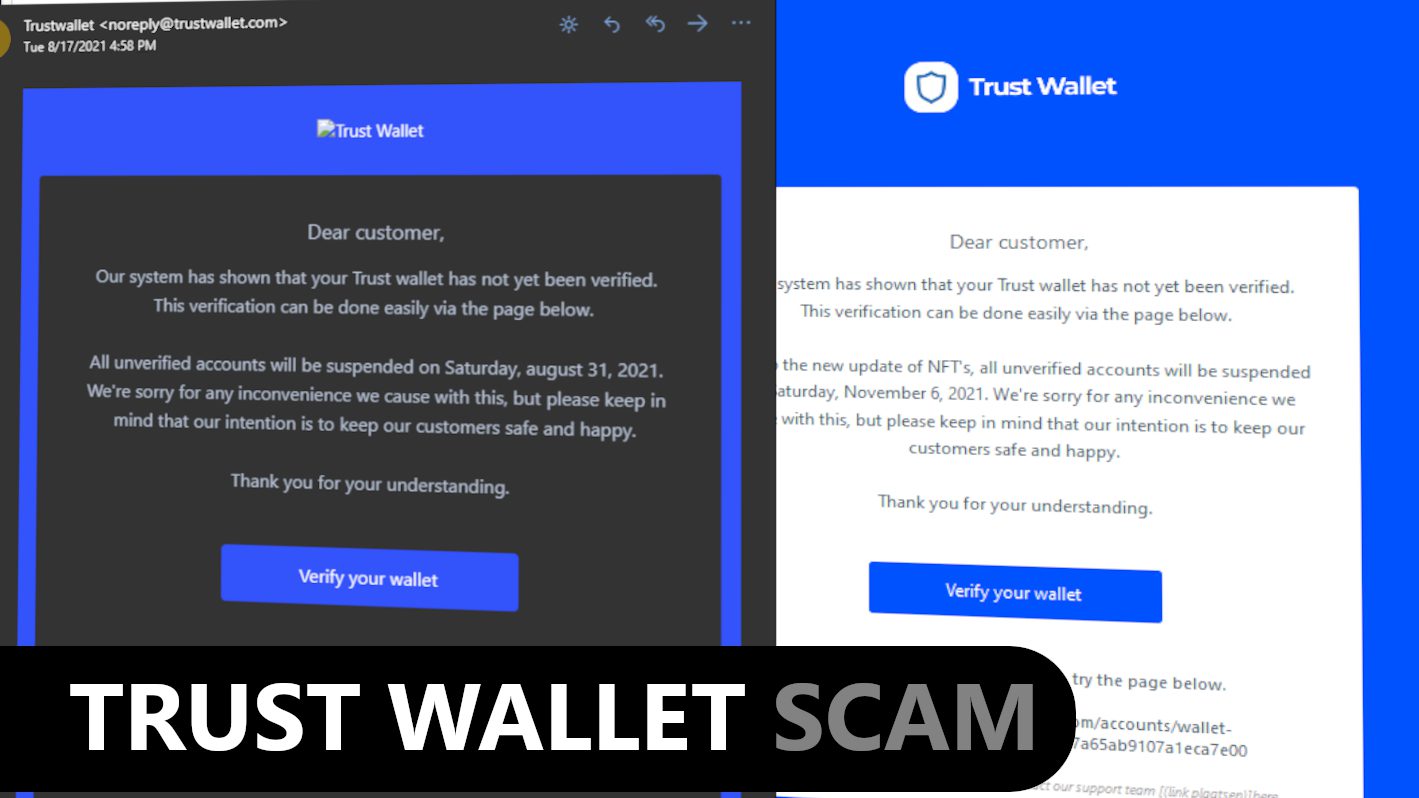
Trust Wallet Scam seeks to extract sensitive information from victims
Contents
Trust Wallet is a legitimate and well-known non-custodial cryptocurrency wallet that supports over 1 million different cryptocurrencies and allows users to buy, send and receive coins or buy and sell NFTs. However, lately cybersecurity experts noticed a growing number of fraudsters trying to scam Trust Wallet users via phishing emails asking to verify their wallets. These emails contain a malicious link leading to a phishing website that requests to enter Trust Wallet Recovery Phrase. With their hands on the user’s seed phrase, scammers can hack the cryptocurrency wallet.
Trust Wallet scam sites are promoted via phishing emails. Scammers design these emails to make them look like they were sent by the actual Trust Wallet. The discovered samples had deceptive subject lines, such as:
- Your wallet will be suspended!
- Our system has shown that your Trust Wallet has not yet been verified;
- Updates!!!;
- Verify your account;
- We have an urgent message regarding your assets.
Although the email message text differs depending on the phishing campaign used, they all deliver the same message to the victim. The scammers usually claim that the Trust Wallet’s system identified the user hasn’t verified the wallet which can lead to the account suspension. The phisher asks to verify the wallet via provided link.
Malicious link in the email leads to different phishing sites
One of the analysed phishing websites related to Trust Wallet Crypto Scam claim users can earn Shiba Coins (SHIB) for free. These sites ask the user to complete a form to start earning coins for free.
The form asks how long the user has been a member of Trust Wallet and then asks to fill in Trust Wallet’s Recovery Phrase. Lastly, there is a button stating “Earn Now” which does nothing else but sends the private data the user entered to fraudsters.
Another reported email scam campaign leads the user to a phishing website that’s designed to impersonate the official Trust Wallet website. The phishing site showcases a 10-second countdown to allegedly “open a secure Internet environment.” This is nothing else but a deceptive act to gain user’s trust in the website’s security and reputation. Once the countdown is complete, the site triggers a redirect to a deceptive site asking to enter the recovery phrase for the wallet.
Some of other observed phishing sites had slightly different designs but they all were made with the same purpose – to collect user’s recovery phrase (also known as the seed-phrase) which allows the hackers to take control over the victim’s wallet.
Victims should also remember that such phishing sites tend to have short-lifespan as scammers tend to use them for a period of time and then create new deceptive domains that are used in scam campaigns. On top of that, such sites might trigger redirects to other malicious websites once the required information is provided by the user. This way, the user might end up on other scam sites or download malicious files to the computer without realising the consequences. For this reason, anyone who has fallen victim to the Trust Wallet Scam are advised to scan their computers for malware.
Threat Summary
| Name | Trust Wallet Scam |
| Type | Email Scam, Phishing Email/Site, Crypto Scam |
| Email subject line | Your wallet will be suspended! Our system has shown that your Trust Wallet has not yet been verified; Updates!!!; Verify your account; Your account is not yet KYC verified; Start your day by verifying your trust wallet crypto app; We have an urgent message regarding your assets. |
| Phishing domains | trust-shibawallet.web.app, verify.mytrust-wallet.[random digits].plesk.page, axie-infinity-shard.xyz, trustcryptowallet.net, trustwallet.net, trustwallet.com.erc-20-tokens-gift.com, https://trustwallet.token-airdrop.space, programvipshib.github.io and others |
| Deceptive statement | Our system has shown that your Trust Wallet has not yet been verified |
| Scammers’ email addresses | supportdesk.trustwallet@protonmail.com, admin@space.org, noreply@trustwallet.net and many others |
| Potential damage | If the victim enters the Trust Wallet Recovery Phrase into the form presented by the phishing site, fraudsters can hack the user’s wallet. Additionally, phishing sites might trigger redirects to other malicious sites or trigger downloads and potentially infect one’s computer. |
| Distribution | Email spam campaigns |
| Removal | If you suspect that scammers dropped malware on your computer, remove it from your PC using trustworthy software. To repair virus damage on Windows OS files, consider scanning with RESTORO (secure download link). |
REPAIR VIRUS DAMAGE
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
See some examples of the phishing sites pushing Trust Wallet Crypto Scam. These sites always ask for user’s Recovery Phrases.
See the first example below.
Second example:
In this last example, scammers promise a SHIBA INU (SHIB) gift for the user and also require the user’s seed phrase.
How online crypto scams are promoted and how to avoid falling victim to them?
Online crypto scams are on the rise, so users should be extremely vigilant. The most common techniques used to promote these scams involve social media or email spam campaigns and potentially unwanted programs (PUPs).
To promote deceptive online sites impersonating official websites of cryptocurrency exchange platforms, the cybercriminals take advantage of email spam by distributing thousands of messages to potential targets. Some of the things that users should look out for are overly-general greeting line, such as “Dear customer/user/client” and grammar or typo errors in the email or the linked website. Additionally, users should inspect the sender’s email. For example, the official Trust Wallet website is trustwallet.com, meanwhile, the scammers use a scam domain trustwallet.net, as well as create email addresses on this domain. Scammers also tend to use long domain names, such as hxxp://trustwallet.com.erc20-tokens-gift.com, hxxp://trust-shibawallet.web.app or trustcryptowallet.net that are a little easier to spot and identify as deceptive.
Another common trick used by scammers to promote crypto scams is creating fake social media profiles and pushing deceptive posts to users. Usually, these posts include too-good-to-be-true claims, such as giveaway of cryptocurrencies or other freebies. These fake claims may appear in a form of posts or even ads on social media platforms and various websites. They will contain a link to a site where the user can allegedly “claim the reward.”
However, the site will demand some sensitive information in exchange for the “gift” which simply does not exist and will not be issued by the scammers. Again, users should remember that legitimate crypto services do not ask to reveal your private keys or password.
Users might also run into phishing or malicious sites in case they have potentially unwanted programs (PUPs) or malware installed on their computers. These programs tend to trigger pop-up ads or redirects during user’s browsing sessions. Other potentially unwanted programs associated with crypto scams are known as clipboard hijackers and are developed to identify whenever the user accesses a cryptocurrency exchange platform and replace user’s clipboard data with cybercriminals’ wallet address so that the user would transfer funds to a wrong wallet address.
Remove malware from your computer
If you suspect that interactions with phishing emails or websites could result in a computer infection, or if you suspect that your computer was previously infected with an adware serving you malicious ads, we strongly recommend that you scan your computer with trustworthy antivirus. For Mac users, we recommend INTEGO, while Windows users can try RESTORO (download link) to identify unwanted software and repair virus damage to Windows OS files.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software and then using the following tool to repair virus damage to Windows system files:
REPAIR VIRUS DAMAGE TO YOUR COMPUTER
RESTORO provides a free scan that helps to identify hardware, security and stability issues and presents a comprehensive report which can help you to locate and fix detected issues manually. It is a great PC repair software to use after you remove malware with professional antivirus. The full version of software will fix detected issues and repair virus damage caused to your Windows OS files automatically.
RESTORO uses AVIRA scanning engine to detect existing spyware and malware. If any are found, the software will eliminate them.
Read full review here.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
malware Removal Tutorial
To remove the unwanted program from your computer, use these instructions below to uninstall associated programs or apps from your Windows or Mac computer. Then scroll down for instructions how to clean each affected web browser individually.
Remove malware from Windows
Windows 10/8.1/8 users
Click on the Windows logo to open Windows menu. In search, type control panel and select the matching result. Then go to Programs and Features.
Windows 7 users
First, open Windows menu by clicking on the icon in the lower left corner of the screen. Then go to Control Panel and find section called Programs. Click on the Uninstall a program option under it.
Windows XP users
In Windows XP, click Start > Control Panel > Add or Remove Programs.
Uninstall unwanted programs
Once in Programs and Features, look through the list of installed programs. You can click on Installed on tab to sort the programs by their installation date.
Right-click on suspicious programs you can't remember installing and choose Uninstall. Follow instructions provided by the Uninstall Wizard, click Next and finally Finish to uninstall the unwanted program from your PC.
Remove malware from Mac
- Click on Finder.
- Go to Applications folder.
- Look for suspicious applications you can't remember installing. Right-click them and select Move to Trash.
- After moving all suspicious apps to Trash, right-click the Trash bin in Mac's Dock and select Empty Trash.
Remove using INTEGO ANTIVIRUS for Mac (includes scanning for iOS devices). The one-of-a-kind security suite provides VirusBarrier X9 real-time protection against Mac and Windows-based malware, removes existing threats and scans for malware in popular e-mail clients. Includes NetBarrier X9, an intelligent firewall for home, work and public connections.
Remove malware from Google Chrome
Remove suspicious Chrome extensions
- Open Chrome and type chrome://extensions into address bar and press Enter.
- Here, look for suspicious extensions, and Remove them.
- Don't forget to confirm by pressing Remove in the confirmation pop-up.
Change Start Page settings
- In Chrome address bar, type chrome://settings and press Enter.
- Scroll down to the On startup section. Check for suspicious extensions controlling these settings, and Disable them.
- Additionally, you can set browser to Open a specific page or set of pages via these settings. Simply choose this option, click Add a new page, enter your preferred URL (f.e. www.google.com) and press Add.
Change default search settings
- In Chrome URL bar, type chrome://settings/searchEngines and press Enter. Make sure you type searchEngines, not searchengines. Additionally, you can go to chrome://settings and find Manage search engines option.
- First, look at the list of search engines and find the one you want to set as default. Click the three dots next to it and select Make Default.
- Finally, look through the list and eliminate suspicious entries. Right-click the three dots and select Remove from the list.
Remove push notifications from Chrome
If you want to get rid of the annoying ads and so-called push-notifications viruses, you must identify their components and clean your browser. You can easily remove ads from Chrome by following these steps:
- In Google Chrome, press on Menu (upward arrow) in the top-right corner of the window.
- Select Settings.
- Go to Privacy and Security > Site Settings.
- Open Notifications.
- Here, go to the Allow list and identify suspicious URLs. You can either Block or Remove by pressing on the three vertical dots on the right side of the URL. However, we suggest the Block option, so the site won't ask you to enable the notifications if you ever visit it again.
Reset Google Chrome browser
- The final option is to reset Google Chrome. Type chrome://settings in the URL bar, press Enter and then scroll down until you see Advanced option. Click it and scroll to the bottom of the settings.
- Click Restore settings to their original defaults.
- Click Restore settings to confirm.
Remove malware from Mozilla Firefox
Remove unwanted add-ons from Firefox
- Open Firefox and type about:addons in the URL bar. Press Enter.
- Now, click on Extensions (in the left section).
- Click Remove next to every suspicious browser add-on that you can't remember installing.
Change Firefox Homepage
- In Firefox address bar, type about:preferences and hit Enter.
- Look at the left and click the Home tab.
- Here, delete the suspicious URL and type or paste in the URL of a website you'd like to set as your homepage.
Alter preferences in Firefox
- Type about:config in Firefox address bar and hit Enter.
- Click I accept the risk! to continue.
- Here, type in the URL which has taken over your browser without your knowledge. Right-click each value that includes it and choose Reset.
Remove annoying push notifications from Firefox
Suspicious sites that ask to enable push notifications gain access to Mozilla's settings and can deliver intrusive advertisements when browsing the Internet. Therefore, you should remove access to your browser by following these simple steps:
- In Mozilla Firefox, click on Menu (the three horizontal bars) on the top-right corner of the window, then choose Options.
- Click on Privacy and Security, then scroll down to Permissions section.
- Here, find Notifications and click Settings button next to it.
- Identify all unknown URLs and choose to Block them. Click Save Changes afterward.
Reset Mozilla Firefox
- In Firefox, type about:support in the address bar and press Enter.
- Click on Refresh Firefox...
- Click Refresh Firefox again to confirm.
Remove malware from Microsoft Edge
Remove suspicious extensions:
- Open MS Edge browser and click on the three dots button in the top right corner, then click on Extensions.
- Look through the list of installed extensions and find the ones you can't remember installing or simply suspicious-looking ones. Right-click on them and choose Uninstall. Then confirm by pressing Uninstall again.
Change MS Edge Start Page and default search engine:
- Click on the three dots again and go to Settings. First, make sure that you choose to Open Microsoft Edge with A specific page or pages option. Then click the X next to suspicious URLs and type in the one you want to set as your homepage. Click the Save icon to confirm.
- Click on the three dots > Settings. Scroll down and click on Show Advanced Settings. Then scroll down until you find Change search engine button. Click it. Here, select the search engine you prefer using and click Set as default.
Additionally, we recommend selecting and Removing suspicious search engines.
Turn off push notifications in Edge
If you keep receiving pop-up ads or other promotional content while browsing on Microsoft Edge, your browser might be corrupted by a potentially unwanted program (PUP). You have to clean it — follow these easy instructions:
- In Microsoft Edge, open Menu (three horizontal dots) in the top-right corner of the screen and click Settings;
- Click on Advanced settings.
- Scroll down to the Website permissions section. Here, click Manage permissions.
- Find Notifications and Remove all suspicious websites.
Clear browsing data
- Click on the three dots in the top right corner again and click on Settings. Find Clear browsing data section and click Choose what to clear button.
- In the next window, select all options and click Clear.
Remove malware from Safari
Uninstall suspicious Safari extensions
- Open Safari and click on Safari button in the top left corner. Select Preferences in the menu that appears on the screen.
- Now, go to Extensions tab. Look at the left to see all installed extensions, click on suspicious ones and hit that Uninstall button as shown in the picture. Confirm your choice by clicking Uninstall again. Repeat until you get rid of all unwanted extensions.
Change Safari Homepage and default search engine
- In Preferences, open the General tab. Here, check what URL is set as your homepage. Delete it and type in whatever URL you want to set as your Safari Start Page.
- Next, go to the Search tab. Here, choose what Search engine you want to set as default.
- Next, click on Manage websites... then Remove all... and then Done.
Remove push notifications on Safari
Some suspicious websites can try to corrupt your Safari by asking to enable push notifications. If you have accidentally agreed, your browser will be flooded with various intrusive advertisements and pop-ups. You can get rid of them by following this quick guide:
- Open Safari and click on Safari button in the top-left corner of the screen to select Preferences;
- Go to Websites tab and navigate to Notifications on the left side toolbar.
Reset Safari
- Click on Safari > Clear History...
- Then choose to clear All history and hit Clear History button to confirm.
- Go to Safari > Preferences and then open Privacy tab.
- Click Manage Website Data... then Remove All. To finish, click Done.
- Finally, clear Safari cache. In Safari Menu, click Develop > Clear Cache.
Remove malware from Internet Explorer
TIP: If you are still using IE, we strongly advise using Microsoft Edge or a different browser because Microsoft is no longer providing technical or security support for IE browser.
Remove suspicious extensions from IE
- Now, go back to Toolbars and Extensions.
- Below Show:, select All add-ons.
- Right-click suspicious extensions and choose Disable, or, if available - Remove.
- If any pop-up appears, confirm your choice.
Change default search provider and remove suspicious ones
- Open Internet Explorer and click on the gear icon in the top right of the window.
- Then select Manage Add-ons.
- Here, click on Search Providers tab.
- Here, we recommend setting Bing, Google or another trusted and well-known search provider as default. To do it, right-click the provider and choose Set as default.
- Now you can right-click suspicious search providers and choose Remove.
Change IE Home Page
- In Internet Explorer, click the gear icon in the top left corner.
- Choose Internet Options.
- Change Home Page URL to whatever page you want to use as your homepage.
- Click Apply.
- Click OK.
Block pop-up notifications on Internet Explorer
Suspicious websites can gain access to your Internet Explorer browser through push notifications. If you enable them even by accident, you will start receiving numerous annoying ads and other advertising content while browsing. The easiest way to remove push-notification viruses is by performing the following steps:
- In Internet Explorer, click on the Menu (the gear button) on the top-right corner of the window, then select Internet Options.
- Go to the Privacy tab;
- Look for Pop-up Blocker section and select Settings;
- Scroll through all URLs and you can Remove them one by one or all at the same time. Click Close.
Reset Internet Explorer
- Click the gear icon in IE menu > Internet Options. Now click on Advanced tab.
- Under Reset Internet Explorer settings, click Reset...
- Click on the checkbox next to Delete personal settings.
- Click Reset.
- To finish, click Close.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Remove VVWQ Ransomware Virus (DECRYPT .vvwq FILES)
VVWQ Ransomware Virus & Why You Need To Keep Your Computer Safe VVWQ ransomware virus…
Remove VVEO Ransomware Virus (DECRYPT .vveo FILES)
VVEO Ransomware Virus & How It Infects Computers VVEO ransomware is a file-encrypting computer virus…
Remove VVEW Ransomware Virus (DECRYPT .vvew FILES)
VVEW Ransomware Virus Spread & Why You Should Protect Your Computer VVEW ransomware virus is…
Remove HHYU Ransomware Virus (DECRYPT .hhyu FILES)
HHYU Ransomware Virus Is Being Distributed For Extortion Purposes HHYU ransomware is a highly destructive…
Remove OOXA Ransomware Virus (DECRYPT .ooxa FILES)
OOXA Ransomware Virus Is a New Threat to Computer Users OOXA ransomware virus is a…
Remove OORI Ransomware Virus (DECRYPT .oori FILES)
OORI ransomware is a severe threat to files stored on computers OORI ransomware is a…