Remove VoidCrypt Ransomware Virus (Removal Guide)
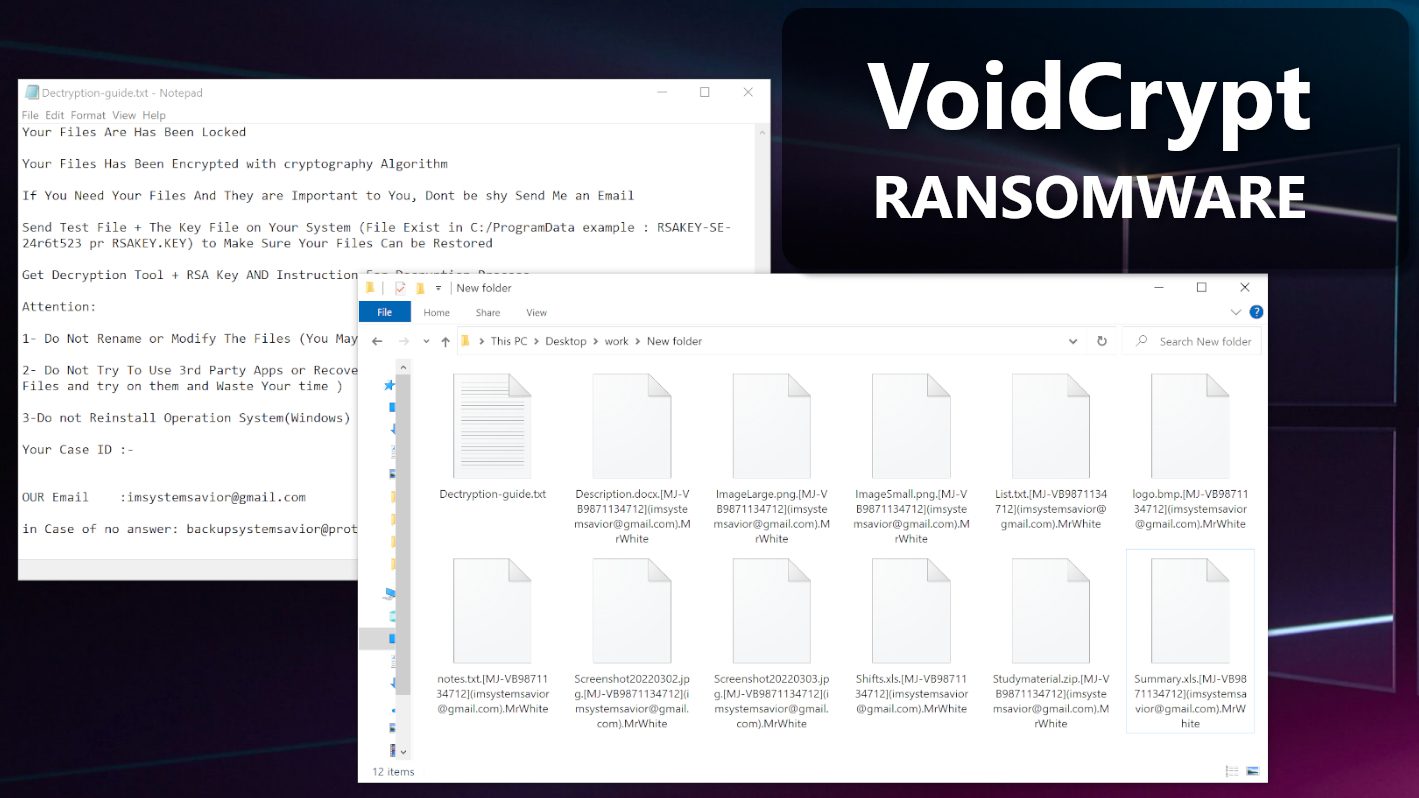
VoidCrypt ransomware blocks access to your own files by encrypting them
Contents
VoidCrypt ransomware (also known as Void) is a computer virus that encrypts files on target systems and demands the user to pay a ransom. This malware was initially spotted in 2020 and remained active to this day. VoidCrypt malware typically uses different strings to mark the names of encrypted data. These strings usually consist of the victim’s ID, cybercriminal’s email address and additional extension. Example of extension syntax: .[cybercriminal’s email address].[victim’s ID].[extension]. The lattest spotted versions append .MrWhite, .GOGO, .Zendaya, or .RYKCRYPT extensions to locked files.
The malware also creates ransom notes in each folder. Depending on the ransomware variant, these notes will be named as INFO.txt, unlock-info.txt, Decrypt-info.txt, Decryption-Guide.txt and Decryption-Guide.HTA, or Decrypt-me.txt.
After being run on a compromised computer, this ransomware initiates the following activities:
- Encrypts all personal files stored on it by using RSA and AES algorithms using hardcoded public key;
- Creates and saves copies of the ransom notes;
- Disables firewall;
- Deletes local backups;
- Disables recovery mode;
- Ends active operating system processes.
Ransom note overview
This ransomware strain typically leaves either text notes only, or a combination of text notes and .hta files that appear in a pop-up window. These notes usually start with a line “Your Files Has Been Encrypted” followed by explanation that RSA+AES algorithms were used to encrypt files. The note suggests that user needs to pay decryption price (a ransom) to cybercriminals in order to get files back. Threat actors instruct to contact them via email address provided in altered filenames also suggest sending some files to them (less than 1 MB in size) for test decryption. The note restricts sending files that contain valuable data, such as Excel sheets or backups.
Next, the criminals warn that decryption price will be doubled after 48 hours, and inform that the victim should rush to contact them ASAP. The threatening message also says that attempts to use recovery tools or third-party applications can damage encrypted files and also increase the demanded ransom amount.
The note then provides three steps that the user should take in order to get data back:
- Contact the criminals using provided email addresses, send the ID provided in modified file names, and settle the ransom amount with the attackers.
- Send some files for test decryption.
- Pay the ransom and receive the decryption tool.
Why you should not pay the ransom
Paying a ransom is simply not worth it, and there are numerous reasons to support this statement. Here are the reasons why you shouldn’t pay money to the cybercriminals:
- Paying the ransom encourages the cybercriminals to continue their illegal activities.
- It also doesn’t guarantee data recovery.
- Complying with the attackers’ demands can make you a target in future attacks, as they may perceive you as an easy target.
- Some countries prohibit ransom payments.
In case your computer has been compromised by the described malware, you should secure your computer without a delay. To remove VoidCrypt ransomware virus, follow the instructions provided below this article. If you’re in need for a robust antivirus software to delete malicious files for you, our team strongly recommends INTEGO Antivirus.
Ransomware Summary
| Name | VoidCrypt (Void) Ransomware Virus |
| Type | Ransomware; Crypto-malware; File Locker; Virtual Extortion Virus |
| Encryption type | RSA + AES |
| Extensions used | .void, .wixawm, .Angry, .exploit, .dark, .help, .MrWhite, .eking, .lockedFile, .Rar, .cypher, .tsar, .GOGO, .RYKCRYPT, .Zendaya |
| Cybercriminal emails/Telegrams | alix1011@mailfence.com, alixxm1011@protonmail.com, ekingm2023@outlook.com, ekingm2023@onionmail.org, stevenxx134@gmail.com, steven77xx@mail.ru, steven77xx@protonmail.com, coronavirus19@tutanota.com, Darksight@tutanota.com, darksight@mailfence.com, faq.mail@tutanota.com, ghostmax@cock.li, cypherteam@mail.com, cypherteam@mailfence.com, sleepme134@protonmail.com, sleepme134@gmail.com, sleepme134@mail.ru, decodetsar@gmail.com, decodetsar@mailfence.com, get.files@tutanota.com, 6lilium6@protonmail.com, 6lilium6@tutanota.com, imsystemsavior@gmail.com, galivertones@aol.com, hosomhelp@aol.com, yooufiles@gmail.com, files.you@mailfence.com, lordgarson@aol.com, drhelmes@aol.com, marcosmelborn@aol.com, recoverfiles1@tuta.io, easyrecovery@tuta.io, spystar1@onionmail.com and @Rar_support (Telegram), senha116@keemail.me, senha120@onionmail.org, helpcenter2008@gmail and many others |
| Damage | The ransomware encrypts files and appends a lengthy extension that contains unique ID, cybercriminals’ email address. The virus then drops ransom notes with a message for the computer user. The malware deletes local backups, terminates system processes, disables firewall. |
| Ransom note names | INFO.txt, unlock-info.txt, Decrypt-info.txt, Decryption-Guide.txt, Decryption-Guide.HTA, Decrypt-me.txt |
| Distribution | Victims often download this ransomware along illegal torrent downloads, cracked software, activators, key generators or malicious email attachments. Cybercriminals also use RDP attacks to infect unprotected systems with this ransomware. |
| Detection names | Ransom:Win32/Taleb.PAA!MTB (Microsoft), DeepScan:Generic.Ransom.AmnesiaE.CE2C (Emsisoft), HEUR:Trojan-Ransom.Win32.Generic (Kaspersky), DeepScan:Generic.Ransom.AmnesiaE.CE2C9 (BitDefender), Generic.Spyware.Stealer.DDS (Malwarebytes), Downloader (Symantec) see all detection name variations on VirusTotal |
| Removal | Remove ransomware and related malware from your PC using trustworthy software like INTEGO Antivirus. To repair virus damage on Windows OS files, download and try RESTORO (secure download link). |
Intego Antivirus for Windows
Award-winning antivirus solution for your PC.
Robust security software that provides robust 24/7 real-time protection, Web Shield that stops online threats/malicious downloads, and Prevention engine that wards off Zero-Day threats. Keep your PC safe and protected against ransomware, Trojans, viruses, spyware and other forms of dangerous programs.
Examples of different VoidCrypt ransomware variants
Example of VoidCrypt ransomware using .void extension to mark encrypted files:
The ransom note displayed by this ransomware (Decryption-Info.HTA) is shown below.
Another example of files encrypted by a different ransomware sample using .wixawm extension is shown below. This virus uses a slightly different extension syntax than other variants.
Below, you can see both of ransom notes dropped by this ransomware variant (Decryption-Guide.txt and Decryption-Guide.HTA).
Another sample of VoidCrypt ransomware, dubbed MrWhite virus, drops a ransom note called Dectryption-guide.txt and also appends a lengthy extension to each file.
How is this ransom-demanding malware distributed?
Ransomware-type viruses like VoidCrypt can be distributed in multiple ways. First of all, it is important to stay away from untrustworthy online resources, especially those that urge you to install something in order to access content. For example, if you want to download some mods for computer games and the website asks you to download something before providing the file you requested, you should stay away from it. The same applies for aggressive online ads asking to install updates or freeware as installers for these can turn out to contain unwanted software bundles.
Moreover, computer users should stay as far as possible from websites offering cracked software downloads. Most of these are filled with various malware. Some of these websites successfully appear in Google search results, so you may want to read this guide on how to identify them and avoid them. Ideally, you should only download desired computer programs and games from official websites only.
Another common way to spread file-encrypting malware is via malicious email attachments. Beware of links and files attached to unsolicited emails, especially if the message urges you to open them – as this can lead to a severe computer infection. A general rule of a thumb is not to open emails that you weren’t expecting to receive and if the sender isn’t someone you communicate with regularly. In addition, look out for tell-tale details such as overly generic greeting line (such as Dear client/customer instead of your full name), urgent message tone and grammar mistakes.
Finally, cybercriminals often try to breach systems by using brute-force RDP attacks. These types of attacks focus on automatically guessing username and password combinations until the attacker gains access to the target system. Afterward, the criminals can install malware on it, steal private information and perform other damaging activities. It is important to use strong passwords and also change them regularly. Robust authentication methods should also be implemented, and the number of open ports should be limited in order to increase security of remote logins.
Remove VoidCrypt ransomware virus and recover your files
If your computer has been compromised, we suggest that you remove Voidcrypt ransomware virus right now. Below, you can find detailed instructions how to delete such kind of malware from your computer effectively. If you’re in need for an antivirus recommendation, then you might want to try INTEGO Antivirus, which is highly praised by our team.
The best way to restore files locked by VoidCrypt is using data backups. However, do not plug them to your computer before the malware is entirely removed – otherwise, your backup can get encrypted as well.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
VoidCrypt Ransomware Virus Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove VoidCrypt Ransomware Virus files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO Antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Remove Up 2 Date Browser Hijacker (Free Instructions)
Up 2 Date hijacks browser settings to promote a fake search engine Up 2 Date…
Remove Gosearches.gg Redirect (Virus Removal Guide)
Gosearches.gg is a fake search engine pushed via browser hijackers Gosearches.gg is a fake search…
Remove Search-alpha.com Redirect from Mac
Search-alpha.com redirects are caused by a browser hijacker Search-alpha.com is a fake search engine that…
Remove COZA Ransomware Virus (DECRYPT .coza FILES)
COZA ransomware is a threat to your personal files COZA ransomware is a malicious computer…
Remove BOTY Ransomware Virus (DECRYPT .boty FILES)
BOTY ransomware encrypts files, demands a ransom BOTY ransomware is a computer virus that uses…
Remove KITZ Ransomware Virus (DECRYPT .kitz FILES)
KITZ ransomware attacks and encrypts files stored on a computer KITZ virus is a ransomware-type…