Remove Cerber Ransomware (In-Depth Guide)
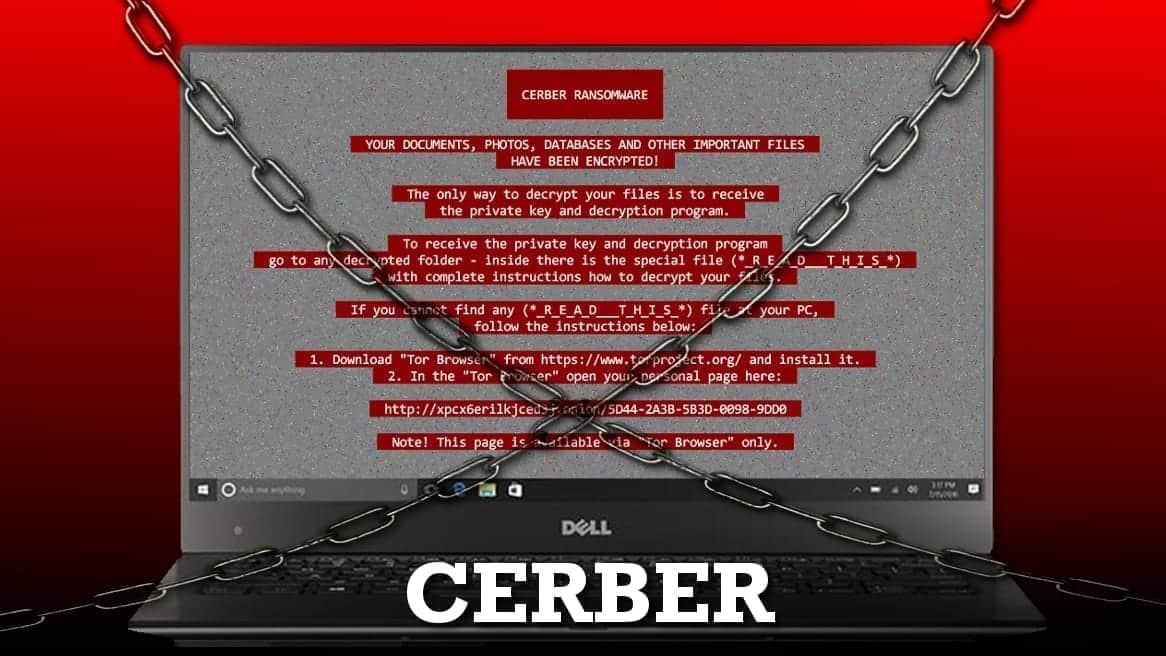
Cerber virus encrypts files on computer system and demands a ransom.
Cerber ransomware in 2019: virus distribution is passive
Contents
Cerber ransomware is a malicious computer virus that encrypts files on target PC. After the encryption, the user can no longer open or use these files. Virus then leaves a ransom-demanding note, saying that files will be decrypted as soon as the ransom is paid. The malware usually plays an audio message and marks encrypted files with .cerber, .cerber2, .cerber3 or random 4-digit extensions. The ransomware was actively distributed in 2016-2017.
Depending on a virus version, the victim may found ransom notes saved as #DECRYPT MY FILES#.html, #DECRYPT MY FILES#.txt, and #DECRYPT MY FILES#.vbs. Updated Cerber versions use _READ_THI$_FILE_.hta”, “_READ_THIS_FILE.hta”, “_HELP_HELP_HELP_random.jpg”, “_HELP_HELP_HELP_random.hta”, _R_E_A_D___T_H_I_S___random_.txt, _R_E_A_D___T_H_I_S___random_.hta, _!!!_README_!!!_random_.hta and _!!!_README_!!!_random_.txt.
The virus leaves .HTA, .TXT, .HTML and .VBS files on the desktop and also in every folder that contains at least a few encrypted files. After encrypting all of the files, the virus automatically executes the VBS file that plays an audio message that says:
Your documents, databases and other important files have been encrypted!
The virus then changes desktop’s background with a pixelated image that contains some links pointing to temporary payment websites. Earlier virus’ versions provided the text in green color, and the latest ones provide it in red. Therefore, some security researchers dubbed it as Red Cerber.
It is essential to understand that files encrypted by this ransomware cannot be reverted to their initial condition without having a decryption key. This key is kept by cybercriminals, and they suggest buying it out for a particular price. In other words, ransomware developers demand a ransom.
The ransom demand can be found in the ransom notes. The .txt files will open via Notepad or another text editor, and .hta files will open via your default web browser. The virus points out that the victim has to install a Tor browser and use it to access one of provided .onion websites.
These websites suggest buying CERBER DECRYPTOR, a tool that can decrypt all encrypted files at once. Of course, not for free. Typically, the criminals ask for a ransom that ranges from 0.5 BTC to 2 or even more Bitcoins. If we express this ransom to USD dollars, it would be somewhere between 1200-5000 US dollars.
The payment website suggests choosing language between twelve provided ones. Next, it demands a confirmation that the visitor is a human and not a robot. Therefore, it asks to select images similar to the provided one. Finally, it allows access to the payment page that states the price of the decryptor and time left to pay it.
Criminals agree to provide the decryption tool if the victim pays the ransom within 5 days starting from the infection day. Failure to transmit the payment to criminals’ Bitcoin address within a given period simply increases the ransom price. After 5 days, it doubles.
Behavioral analysis
Cerber ransomware evolved over time, but its main features remained the same. The provided list describes common virus’ infiltration routine.
- Cybercriminals send malware-laden emails to unsuspecting victims. Victim opens the malicious file.
- The Macro function in the file runs Powershell command.
- The malware establishes a connection with a malicious site and downloads the ransomware to the target computer.
- Powershell launches the ransomware.
The ransomware checks the location it is being launched from. If needed, it replicates itself into a right folder and cleans up after itself. What is also interesting about this virus is that it doesn’t infect computers from blacklisted countries. The virus checks the country code of the compromised host machine’s IP.
If the computer is from one of these countries, the virus terminates itself. Cerber doesn’t attack these countries: Russia, Moldova, Kazakhstan, Kyrgyzstan, Georgia, Belarus, Armenia; Azerbaijan, Tajikistan, Ukraine, Uzbekistan, Turkmenistan.
Newer versions of ransomware are even capable of checking if the compromised computer has any security products installed on it. Surprisingly, the virus doesn’t encrypt them. The virus, however, blocks the outbound traffic of all these security programs by changing Windows firewall rules.
Finally, the ransomware contains a delay function that prevents the virus from encrypting files right away. Experts believe that such a trick is used in order to avoid detection in sandbox environments.
Chances to restore files encrypted by Cerber are low
No matter how tragically it sounds, there are very few options speaking of data recovery. Cerber uses RSA and RC4 encryption algorithms to corrupt files. The entire encryption process can be broke down in these three parts:
- The virus generates a random RSA key and encrypts it with a built-in RSA key.
- Then it creates an RC4 key and encodes it with the randomly selected RSA key.
- Finally, the virus locks victim’s files with the RC4 key.
It is important to note that the virus uses different RC4 keys for each victim’s file. Besides, the complex algorithm corrupts only some parts of the file and leaves some pieces of information required in the decryption procedure. Clearly, there is no possibility to recover data locked by the virus because the ransomware authors are the only ones who know the RSA key.
Although some of the first Cerber versions appeared to have some flaws and security researchers have released free decryption tools, they soon became useless. Ransomware authors found their mistake and upgraded the virus. Until now, no one managed to create another decryption tool for it.
Data recovery options
- Recover your files from a backup;
- Pay the ransom (we do not recommend doing so, as you can lose your money and never receive the decryption key);
- Refuse to pay the ransom and start over. If you choose this option, you refuse to pay money to extortionists. We do not recommend you to wipe out the encrypted data – after some time, decryption tools might be released.
Timeline of Cerber ransomware
Cerber first appeared in March 2016 and is still active today. From the very first day since malware analysts spotted this new ransomware strain, it became clear that the virus is developed by very experienced programmers.
August 2016. Shortly enough, virus’ authors updated the initial version and released the second version of the virus. The new virus adds .cerber2 extension on encrypted files and starts using a new background for the victim’s desktop. Around the same time, researchers from TrendMicro manage to create a working decryption tool. Unfortunately, it could help only the victims of the first and the second virus’ versions, because clearly, the cybercriminals updated the virus again.
On top of that, the payment website also received some improvements. Criminals added a Captcha system to prevent automated attempts to enter the site.
September 2016. The criminals release a new version of the infamous ransomware. Security researchers quickly give it a name of Cerber 3, considering that it marks encrypted files with .cerber3 extension. Around the same time, malware authors start distributing the virus using RaaS method. According to reports, the ransomware affiliates managed to infect over 150,000 computers worldwide.
This time, the ransomware hits China and South Korea the hardest. Security experts claim that cyber crooks employed Magnitude exploit kit that identifies weak points of the target operating system and uses them to compromise the machine. The updated version demands 1.24 BTC per one infected PC.
In the middle of September, it became clear that the third version of this malware was distributed via a compromised Ammyy Admin website. According to reports, the site served malware for at least two days until it was fixed. It wasn’t the first time when the indicated domain was used for malware distribution – reports show that the site distributed Lurk, Buhtrap and Ranbyus banking trojans, also Fareit and Corebot spying tools, and NetWire remote access Trojan.
October 31st, 2016. The fourth version of the ransomware surfaces. Cerber 4.1.0 starts using unique file extensions to mark encrypted files. From now on, the virus takes the fourth segment of the MachineGuid value from Windows Registry’s HKLM\Software\Microsoft\Cryptography key. The segment consists of 4 characters, and the virus uses it to mark each encrypted file.
The ransomware now uses Readme.hta name for the ransom note, and no longer drops VBS (the audio file), HTML or BMP file. The virus is improved, and so it stops certain running processes to allow the ransomware to finish the encryption procedure sooner. However, just like in previous versions, it changes the wallpaper, this time containing the number of the ransomware version.
The fourth version spreads using pseudoDarkleech Rig exploit kit, the same one used in CrypMIC ransomware distribution. The ransomware switches to a new range of IP addresses (194.165.16.0/22) that sends UDP packets with statistical information.
This ransomware also performs an HTTP request to a Bitcoin blockchain explorer, which returns a JSON document with information about transactions regarding criminals’ 17gd1msp5FnMcEMF1MitTNSsYs7w7AQyCt Bitcoin address.
On November 1st, developers of the ransomware release an updated Cerber 4.1.1 virus version. The version acts identically as the previous one, except that it displays a different version number on the new desktop wallpaper. It also demands a quite moderate ransom (comparing to other versions) – $85 or $170.
For some reason, the developers of the ransomware decided to skip the 4.1.2 version. It has never emerged online, nor any ransomware victims complained about it.
On November 7th, 2016, Cerber 4.1.3 virus emerges, but not for a long time. On the same day, malware researchers spot the Cerber 4.1.4 version, which spreads via malicious spam that delivers compromised ZIP files with Word documents in them. These documents are named with a random set of digits.
The malicious docs contain a Macro function that needs to be activated by the victim via the “Enable Content” button. This silently runs a Powershell command that executes a base64 encoded string which is responsible for connecting to a remote website and downloading a malicious file to victim’s %AppData% folder. The winx64.exe file is an executable of the ransomware, which, once run, starts encrypting all files on the system immediately.
The 4.1.4 version uses three different IP ranges that send UDP packets – 65.55.50.0/27, 192.42.118.0/27 and 194.165.16.0/22.
On November 8th, 2016, experts spot another updated Cerberus version – Cerber 4.1.5 edition. The ransomware continues to scramble filenames and add extensions according to the fourth segment of the MachineGuid value. Virus still uses Readme.hta file to provide information about the cyber attack, and asks for a ransom worth $500 or $1000.
November 22nd, 2016 is the date when Cerber 4.1.6 stepped in. Again, the virus doesn’t have any significant improvements, except for the slight change in the picture that it sets as victim’s desktop wallpaper. Besides, this version asks for $499 in Bitcoin and $999 if the victim fails to pay in time (5 days starting from the day of the infection). The 4.1.6 variant is also the latest edition of virus’ fourth version.
Only two days after, on November 24th, 2016, the fifth version of the ransomware surfaces, attacking computers with the help of RIG-V exploit kit. Cerber 5.0.1 now calls the ransom note _README_.hta. During the encryption, the ransomware skips first 640 bytes of the target file, while the previous versions used to skip 512 bytes. The new version also targets larger files only – the minimum size of the data to be encrypted has to be 2,560, meanwhile previous versions targeted all files that take more than 1,024 bytes on the disk. The IP ranges used to send UDP packets are also different – 63.55.11.0/27, 15.93.12.0/27 and 194.165.16.0/22.
At the beginning of December 2016, Red Cerber ransomware version emerges. The new malware variant has a lot of modifications, some of which might seem beneficial for the victims. First of all, the ransomware no longer deletes Volume Shadow Copies which means that victims can recover part of the encrypted data for free.
Next, the ransomware prioritizes particular folders on the target system and encrypts files stored on them before turning to the rest of the victim’s data. The malware first encrypts all Microsoft Office documents (Word, Excel, OneNote, PowerPoint, Outlook, and others) and also Bitcoin data.
Red Cerber ignores particular folders, including Program Files and Sample Pictures/Videos/Music folders. It also excludes .bat, .cmd, .cpl, .com, .dll, .msc, .msi, .exe, .hta, .msp, .pif, .scr, .scf and sys extensions from the target list, adding 50 new ones instead. In total, Red CRBR targets 493 different file types.
The new variant appeared right before the holiday season, which is known to be a slow-down season for cybercriminals. However, speaking of Cerber, it wasn’t the case. Right before the Christmas, its developers began sending spam towards thousands of victims, sending fake credit card reports.
The malware comes in a password-protected file, and the password is provided in the message body. The file inside the ZIP attachment is a Word document with Macros in it if the victim clicks the “Enable Content” button after opening the file, the Macro script downloads and launches the ransomware virus in victim’s computer.
A little later, on December 22th, the ransomware gang began compromising legitimate Internet sites by injecting malicious scripts to them. These scripts redirect victim’s web traffic to Pseudo Darkleech (also known as Cerber’s gateway). It soon became clear that the malicious script added to sites was the infamous Nemucod (malware downloader) that was involved in various other malware distribution schemes earlier.
Nemucod was used to connect to certain domains, download and then execute malware on victim’s PC. This was done using vulnerabilities in victim’s machine, mostly those in Microsoft Edge, Silverlight, Internet Explorer and, of course, Flash Player. On top of that, around this time the ransomware used to demand from 1.24 to 2.48 Bitcoins as a ransom.
However, it wasn’t the last methods used to spread the malicious virus. According to Microsoft, the virus used exploit kits to proliferate itself worldwide. The cybercriminals used RIG exploit kit to detect CVE-2015-8651 vulnerability in unpatched Flash Player installations, which allowed the attackers to install and activate the virus instantly. The defined ransomware campaign turned thousands of computer users into victims, especially in Europe and Asia.
In April 2017, Cerber 6 virus shows up. This time, criminals employs malicious spam and social engineering tricks for its distribution. The criminals start a spam campaign delivering fake .ZIP attachments with a JavaScript file inside of it. This file either connects to a certain web address and downloads the virus from there, runs a task to launch the malware after a couple of minutes, or activates an embedded PowerShell script.
The delay function is most likely used to deceive sandbox environments that wait for the final execution of the virus. The new virus also does not have a function that makes it terminate specific processes.
Another update that the sixth version has allows the virus to add Firewall rules to stop the outbound traffic of all the executable binaries of security products present on the computer, including firewalls, antivirus, and also anti-spyware or anti-malware programs. This update prevents computer security programs from stopping the threat or slowing down its activity.
On top of that, Cerber avoids static machine learning detection by using a new packaging and loading mechanism. The malware now arrives in a self-extracting archive, which is uploaded to Dropbox by the ransomware developers. The victim unknowingly downloads the malicious file and opens it. The archive contains a Visual Basic script, a DLL file, and a binary file.
The malware replaces filenames with a different set of characters for each victim. The VB Script activates using Windows Script Host. Then the script loads the DLL file using rundll32.exe.
The DLL file reads the binary file, decrypts one part of it, and executes the decrypted part. The decrypted code is clearly malicious. The binary file contains the malware loader and configuration settings.
The loader has to check whether it is being analyzed by certain programs and whether any security programs are running. If it detects some security software, sandbox or virtual machine environment, the virus stops. If it doesn’t, it injects code in another process that runs the malware on the target computer.
The sixth version also avoids using the combination of RSA and RC4 encryption algorithms because of Cryptographic Application Programming Interface (CryptoAPI). Besides, the virus uses an individual function to read and corrupt victim’s files.
April 7, 2017. Cerber ransomware distributors start testing new distribution technique. This time, the attackers attempted to exploit a vulnerability in Apache Struts ( CVE-2017-5638) on Windows servers.
The flaw allowed the cybercriminals execute system commands using the rights of a user who runs the web server process. The attackers can only attack servers without the latest Struts deployments, so administrators should install the updates as soon as possible. The flaw was noticed and patched on March 8, 2017.
August 03, 2017. Researchers from TrendMicro were first to notify about the latest ransomware update. It seems that now the developers of the most infamous ransomware are testing new methods to monetize their virtual extortion tool.
Cerber is now capable of stealing saved browser passwords and passwords associated with three Bitcoin wallet applications (wallet.dat, *wallet and electrum.dat). Although these files don’t directly give the attackers access to Bitcoins stored in the wallets, with the help of the victim’s passwords, this task can be a piece of cake.
The ransomware grabs all passwords saved in Google Chrome, Mozilla Firefox and Internet Explorer. The ransomware steals the victim’s files and passwords before starting the data encryption process and sends the collected information to a command and control server. Once this task is completed, the virus deletes the wallet files.
October 2017. Magniture exploit kit, previously used to distribute Cerber, starts delivering new crypto-virus later named Magniber (also known as My Decryptor ransomware). Interestingly, the virus only targets South Korean users. Magniber virus gives encrypted files a random file extension consisting of 7-characters and drops a ransom note called READ_ME.txt, _HOW_TO_DECRYPT_MY_FILES_[random_characters]_.txt or READ_ME_FOR_DECRYPT_[victim’s id].txt. This ransomware demands 0.2 BTC as a ransom. Links pointing to Tor websites in the ransom note lead to pages identical to ones provided by Cerber virus.
Distribution methods
Since its debut in 2016, Cerber ransomware was distributed using a variety of malware distribution techniques, including, but not limited to the following:
- Exploit kits (RIG EK, Neutrino EK, Magnitude EK);
- Malvertising;
- Email Spam.
One of the main reasons of the virus’ success is that it in March 2016, Cerber developers started selling the virus on the dark web forums as a ransomware-as-a-service. In other words, wannabe cybercriminals can join the cybercrime gang and help to distribute the ransomware, infect more computers and receive 40% of each ransom paid by victims in return.
According to Check Point’s research, in July 2016, the Cerber RaaS campaign generated a whopping $195,000 profit, $78,000 of these going to the original ransomware developers and the rest to the affiliates. According to the researchers, the ransomware generates $2.3 million in annual revenue. Such a sum is shocking, considering that only 0.3% of all the victims decide to pay the ransom.
In comparison with other ransomware viruses, it uses sophisticated and highly advanced malware distribution techniques. While the majority of infections spread via email spam, the infamous ransomware hits the users via exploit kits and malvertising.
Exploit kits
Exploit kits are basically software packs that run on web servers and scan users’ computers communicating with them for software vulnerabilities. Users are usually redirected to sites hosting exploit kits after clicking a malicious ad or a link.
Malvertising
Speaking of malicious ads (malvertising), we have to point out that these are very alike to exploit kits and usually are the reason why users get redirected to them. In some cases, the victim doesn’t even need to click on the malicious ad in order to get redirected to malicious sites. In the past, legitimate websites like BBC, Forbes, and others used to serve malware because they were showing advertisements from compromised ad networks. To get you a brief overview of the malvertising-based ransomware attack, we have prepared this explanation:
- First of all, criminals sign up with advertising networks as regular advertisers. They have to bid to make ads appear on popular Internet sites. As a consequence, their ads reach a large audience.
- Buying advertising space is an automatic transaction, besides, not every ad network checks advertisements precisely. Typically, the cybercriminals serve legitimate ads for some time to gain advertiser’s trust before starting to serve malware-laden ads.
- Malicious ads use iframes to redirect people to compromised websites containing an exploit kit. The exploit kit then downloads and installs Cerber or another ransomware on the computer.
Email spam
Cerber is no different from other ransomware viruses, and one of the most efficient distribution techniques that its authors have been using is email spam. The virus uses several different methods in spam campaigns.
One of the most used campaigns is The Blank Slate. It got its name from the fact that malicious emails it delivers contain no text in the message body or in the subject of the email. Such emails contain an attached ZIP archive with yet another ZIP file in it.
The final archive contains either a Word document or a JavaScript file. If it’s a Word file, it will ask the victim to enable content in order to see it properly. If it is a JavaScript file, it will only take to open it in order to run a malicious script that connects to a malware-serving domain, downloads, and launches the malware.
Another malspam campaign pushing the virus was sending out messages with no subject and with an attachment that was named with a random set of digits. Some of the attachments were called EMAIL_[random digits]_[recipient].zip. Inside this file, there was yet another ZIP called [random digits]_ZIP.zip. Inside this file, there was a malicious Word document containing Macros. The Word file was entitled with a random set of digits as well.
Cerber virus almost always uses randomly named attachments; usually, the file name consists of a set of digits. The virus might be sending files called as invoice, resume or subpoena. Therefore, it is a must to check if you know the sender (however, you shouldn’t open any untrustworthy looking emails from strangers). Scammers easily spoof the sender’s email to make it appear more legitimate.
The virus was also noticed spreading via fake FedEx/UPS Parcel delivery emails claiming that a courier could not deliver some mysterious parcel to the victim. The email contains a ZIP attachment called as UPS-Parcel-ID-[random digits].zip or Delivery-Details.zip.
The ZIP attachment contains another ZIP and JavaScript file inside of it, both with identical names as the attachment itself. The malicious JS file connects to a remote host, downloads Cerber (exe1.exe) and Kovter(exe2.exe, disguised under Winamp’s icon), and executes them on the target system.
The right way to remove Cerber from your computer
Cerber removal is a highly complex task. Inexperienced computer users should not attempt to complete it without a help of a computer technician or a decent anti-malware (or antivirus) software. We suggest using automatic malware removal tool – it will help you to clean the entire system and won’t cost you as much as a computer technician’s service. The malicious virus often spreads in tandem with Kovter click-fraud malware, which is a fileless malware example. The ransomware is easy to notice and remove compared to this silent malware variant.
To remove Cerber virus as well as additional viruses that came with it at once, we highly recommend using a professional anti-malware software removal tool. You must be using the latest version of a security product so that it could detect the most recent version of the virus. Our advice is, always update your antivirus or anti-malware before scanning the system. This way, you will update it with the latest malware definitions. If you do not have security software at the moment, you can read our security software reviews on our site and choose whichever looks best to you.
Most ransomware variants delete themselves after encrypting system files. However, each virus is different, and we want to ensure that there is no danger before starting the file decryption process. Therefore, we suggest following the given steps to remove Cerber from your computer entirely.
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in Safe Mode with Networking, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to start Windows in Safe Mode:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can’t find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove Cerber files. It is very hard to identify files and registry keys that belong to the ransomware virus, besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable antivirus program. Update and use the security program you already have or choose a new one. If you wish, you can check the security software reviews on our site.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can’t find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%\system32\restore\rstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won’t be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Recover files encrypted by Cerber
The majority of ransomware variants described in the article leave no ways to decrypt data. However, some of them appeared to be weak enough to be cracked by malware analysts. Currently, there is only one decryptor created by TrendMicro:
TrendMicro Ransomware File Decryptor. This tool can decrypt files locked by the first version of Cerber. It decrypts files that have such filenames – [10 random characters].cerber. Download the decryptor and follow the usage instructions provided by the developer.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
Remove UIGD Ransomware Virus (DECRYPT .uigd FILES)
UIGD ransomware encrypts all files on a computer, asks for a ransom UIGD ransomware is…
Remove EYRV Ransomware Virus (DECRYPT .eyrv FILES)
EYRV ransomware takes your computer files hostage, demands a ransom EYRV ransomware is a destructive…
Private Internet Access Review 2022: Fast, Secure & Cheap VPN
Private Internet Access (PIA) VPN maintains its long-term role as a leader Private Internet Access…
Remove XCBG Ransomware Virus (DECRYPT .xcbg FILES)
XCBG ransomware aims to lock your files and demand a ransom XCBG ransomware is a…
Remove BPQD Ransomware Virus (DECRYPT .bpqd FILES)
BPQD ransomware encrypts all computer files, demands a ransom from the user BPQD ransomware is…
Remove KQGS Ransomware Virus (DECRYPT .kqgs FILES)
KQGS ransomware is a hostile computer virus designed to encrypt all of your files KQGS…
View Comments
Hallo! Jemand in meinewm Facebook Gruppe teilte diese Website mitt unss soo zzu schu es Dir kam ich.
Icch bin definitiv liieb Informationen. Ich bin Seite verlinken und mein Nachfolger werden tweeting
this! Ausegezeichnete und ausgezaeichneten design.