Voicemail Email Scam promotes phishing websites and steals user data
Contents
Voicemail Email Scam is a new mass-scale fraudulent operation that cybercriminals use to trick unsuspecting computer users into visiting phishing websites. The email suggests that the user has received a new voicemail, and suggests previewing it via provided link. The button provided in the notification hides a phishing link that leads to a deceptive website mimicking email login page. If the user fails to identify the deceit and provides requested login credentials (email address and the password), these will be sent straight to the cybercriminals’ server and will be used to steal your account.
There are many different email design templates, subject lines, message variations and phishing page designs that are being used by cybercriminals to trick unsuspecting users into fake login portals and steal the user-provided login credentials. Additionally, these emails can include malicious attachments named as voicemail recordings.

How Voicemail Email Scam Works?
As mentioned previously, there are two ways these emails seek to inflict damage – either via attached links or files. In this section, we will explain in detail how the attack works in each of these scenarios.
Malicious links leading to phishing pages
Such voicemail scam emails inform the victim about a new voicemail received, and include some fictive details about the recording (such as the sender’s phone number, recording duration and time stamp when it was sent). The message includes a button that invites the user to preview or play the audio recording.
Unfortunately, the button includes a deceptive link leading to a phishing website that mimics the design of well-known email service provider pages (such as Microsoft, Hotmail, or others). The site asks to login to the email or confirm the password to proceed. However, if the victim doesn’t notice the suspicious URL of such website, one might get tricked into typing in the login credentials. Sadly, no matter how many times the victim attempts to login, there will be no success, since the web page is only meant to collect the information the user provides and send it to cybercriminals.
Malicious attachments hiding malware
Another scenario that threat actors use is attaching the alleged voicemail as an email attachment. Judging from samples we collected during our research, the criminals may use music icon in the file name, or add a fake .mp3 extension, and name the file as “Voicemail Audio [date]” or “Voicemail Audio Transcription” or similar.
The actual file format is typically a .htm file which usually opens via web browser. When this happens, the user will be redirected to a phishing page that can also ask to enter email login credentials, or, the file may contain malware.
Therefore, it is important to recognize such scam emails and never open links or attachments that accompany them. If you have already done so, and suspect that your computer may have been compromised by malware, we recommend that you download INTEGO Antivirus to remove threats from the system. Additionally, software like RESTORO (secure download link) can be used to repair virus damage on Windows OS files. Most importantly, change the login credentials for the email account that you have exposed credentials of to cybercriminals.
Threat Summary
| Name | Voicemail Email Scam |
| Type | Email Scam, Phishing |
| Email subject line | Voice notification, (1) Unread Voicemail Message, New Voice Message from [name], New Audio Message Received From Your Contact, Monday, 14 November 2022 [“VoiceMail Notification”], [name] shared a voicemail message to [name], (1) UNREAD VOICE MAIL MESSSAGE and similar. |
| Deceptive statement | The email claims the user has received a new voicemail message that needs to be reviewed. The email invites the user either to click on a deceptive link leading to a phishing website, or download a file that either contains malware or opens a phishing site in web browser window. |
| Scammers’ email addresses | don@dvs-sales.com, vm@voicemailteam.info, ash.wyn@agoraquebec.com and many others |
| Potential damage | If the victim clicks on a malicious URL or attachment added to the email, one might be taken to a phishing website that asks to re-login to email account. Unfortunately, after providing the login credentials, these will be sent to cybercriminals. Additionally, these emails might contain deceptive attachments containing malware. |
| Distribution | Email spam campaigns |
| Removal | If you suspect that you have downloaded malware to your PC, remove it from your PC using trustworthy software. To repair virus damage on Windows OS files, consider scanning with RESTORO (secure download link). |
| Recovery | Change the login credentials you provided via phishing link AS SOON AS possible. |

Intego Antivirus for Windows
Award-winning antivirus solution for your PC.
Robust security software that provides robust 24/7 real-time protection, Web Shield that stops online threats/malicious downloads, and Prevention engine that wards off Zero-Day threats. Keep your PC safe and protected against ransomware, Trojans, viruses, spyware and other forms of dangerous programs.
Examples of Voicemail Scam Emails
Example no. 1: Scam targeting Microsoft 365 credentials
One of the Voicemail Email Scam campaigns appeared in June 2022, and appeared to target Microsoft 365 credentials. The email subject is V_audio missed on [date] and claims that the user has a new voice mail from a random number. The email recommends opening the enclosed attachment to listen to the voicemail.

The attachment itself is a HTML file that contains a music note icon in its name along with alleged date that the recording was made. It is believed that such name is given to the deceptive file to convince the victim that it is an audio file rather than HTML document.
However, once opened, the file releases an obfuscated JavaScript that redirects the victim to a phishing website. The victim will have to complete a CAPTCHA check, which is added as an extra step to bypass anti-phishing tools.

After passing the check, the user will be taken to a phishing website that mimics Microsoft Office 365 sign in page. Whatever credentials the victim types in, the criminals will grab them and use them to steal the user’s account.

Another example of phishing page that such emails can redirect you is provided below.

Example no. 2: Scams targeting other email login accounts
This email scam involves a simplistic email message that claims the user has received a new voicemail. It also includes the phone numbers of the caller and receiver, as well as caller name and duration of the voice message.

Another sample of similar scam email suggesting the user has received a voicemail:

After clicking on the provided button that says Preview voicemail / Play VM, the user gets taken to a phishing website asking to enter email login credentials. The website design can differ and mimic various email provider websites.

Example no. 3: Whatsapp New Private Voicemail Scam
Another example involving voicemail theme is Whatsapp New Incoming Voicemessage, or New Private Voicemail scam. The deceptive email states there is a voicemail available for the recipient, and includes the time it was sent and duration of it. There is a green Play button, one that hides a malicious URL.

Clicking it takes the user to a Russian domain mailman.cbddmo.ru, according to Armorblox research. The phishing page attempts to install a Trojan known as JS/Kryptik, a JavaScript-based code injected into HTML pages and used to redirect victims to malicious URL and attempt to use a particular exploit.

The web page also asks to click on Allow button to allegedly confirm that user is not a robot; however, what this actually does is it enables the malicious website to send push-notifications for the user daily.
How to identify Voicemail email scam?
Our team advises computer users to inspect the design and typography of the email to understand whether it comes from a trustworthy entity. Often times, these emails include weirdly aligned text, images, or buttons.
Another noticeable detail is that scammers hardly ever pay attention to prepare the text to be flawless – so it often contains typo mistakes, grammar errors, misplaced punctuation marks, etc.
It is also important to hover your mouse over sender’s email and inspect the address of it. If you can see that it is a random email address and not an official-looking one, just delete the email.
Voicemail recordings are not usually sent in a form of an email attachment, unless the user specifically enables this feature. Therefore, if you haven’t enabled such feature and haven’t previously receive voicemails via your email inbox, it is best if you do not interact with such email attachments at all.
If you clicked on a link provided in an email, it is strongly advisable to inspect the URL of the page that you land on. If you can see that it is an extremely lengthy URL that doesn’t look like it belongs to an official email service provider, close that page immediately.
What you can also do is simply copy the link hidden in the email and paste it into online malware scanning engines such as VirusTotal. It will help you determine whether the URL or email attachment has been marked as phishing or malicious by various AV systems.
Remove Malware and Protect Your Data
If you have encountered a similar scam email, we strongly advise that you remove Voicemail Email Scam instance by deleting the message. Worse still, if you have provided sensitive information via phishing link included in the message, or opened its attachments, we recommend that you remove malware using the guide provided below.
It is ideal to boot the computer at risk in Safe Mode with Networking and running an up-to-date antivirus software, such as INTEGO Antivirus to cleanse malware components automatically. Afterward, you may want to download RESTORO to repair virus damage on Windows OS files.
Once you’re done, we recommend that you visit the official sign-in page of the email account that you have revealed the sign-in information for, and change your login credentials immediately, before cybercriminals did it before you. Additionally, we strongly recommend setting up 2FA authentication for more secure logins. This way, the perpetrators won’t be able to access your account even if your password is breached.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software.
REMOVE THREATS WITH ROBUST ANTIVIRUS

Get INTEGO ANTIVIRUS for Windows to remove ransomware, Trojans, adware and other spyware and malware variants and protect your PC and network drives 24/7. This VB100-certified security software uses state-of-art technology to provide protection against ransomware, Zero-Day attacks and advanced threats, Intego Web Shield blocks dangerous websites, phishing attacks, malicious downloads and installation of potentially unwanted programs.
Use INTEGO Antivirus to remove detected threats from your computer.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
malware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in Safe Mode with Networking, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to start Windows in Safe Mode:
Instructions for Windows XP/Vista/7 users
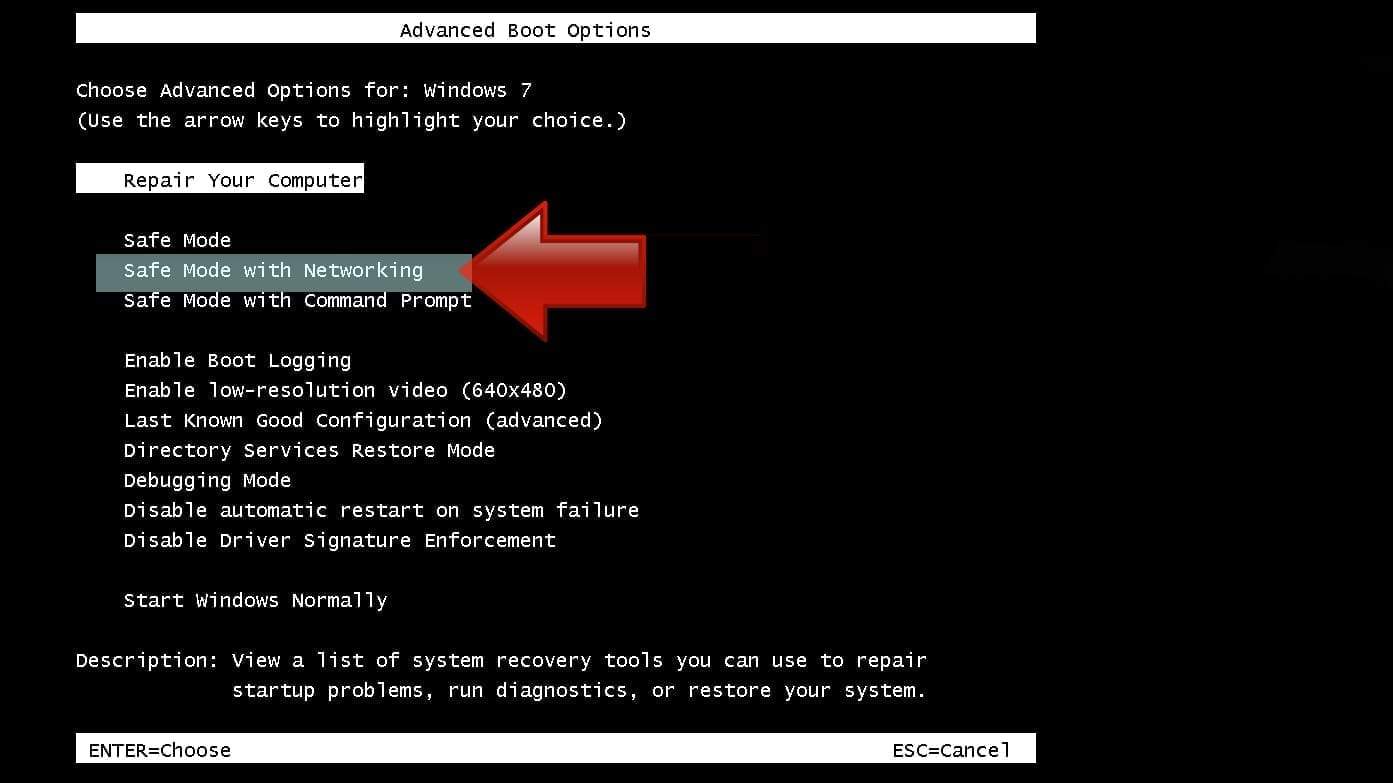
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
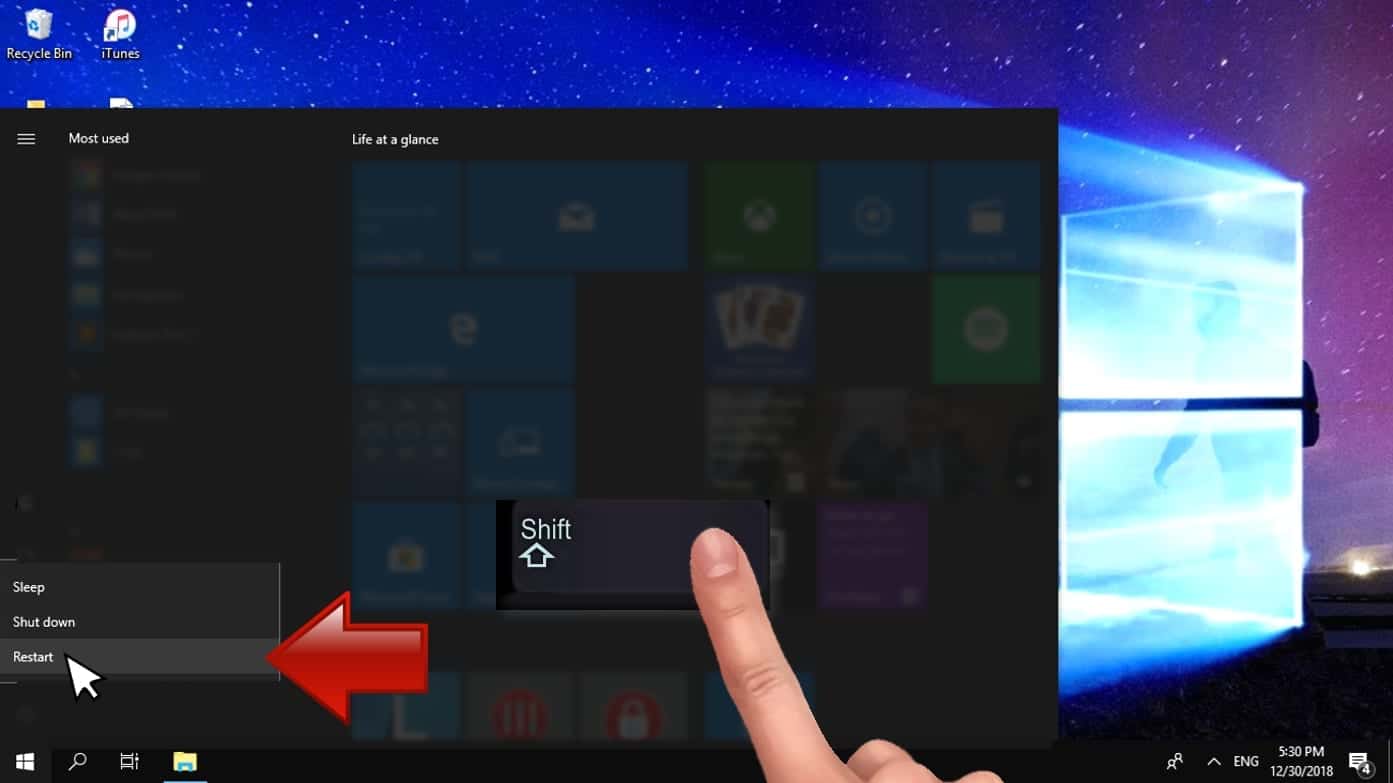
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
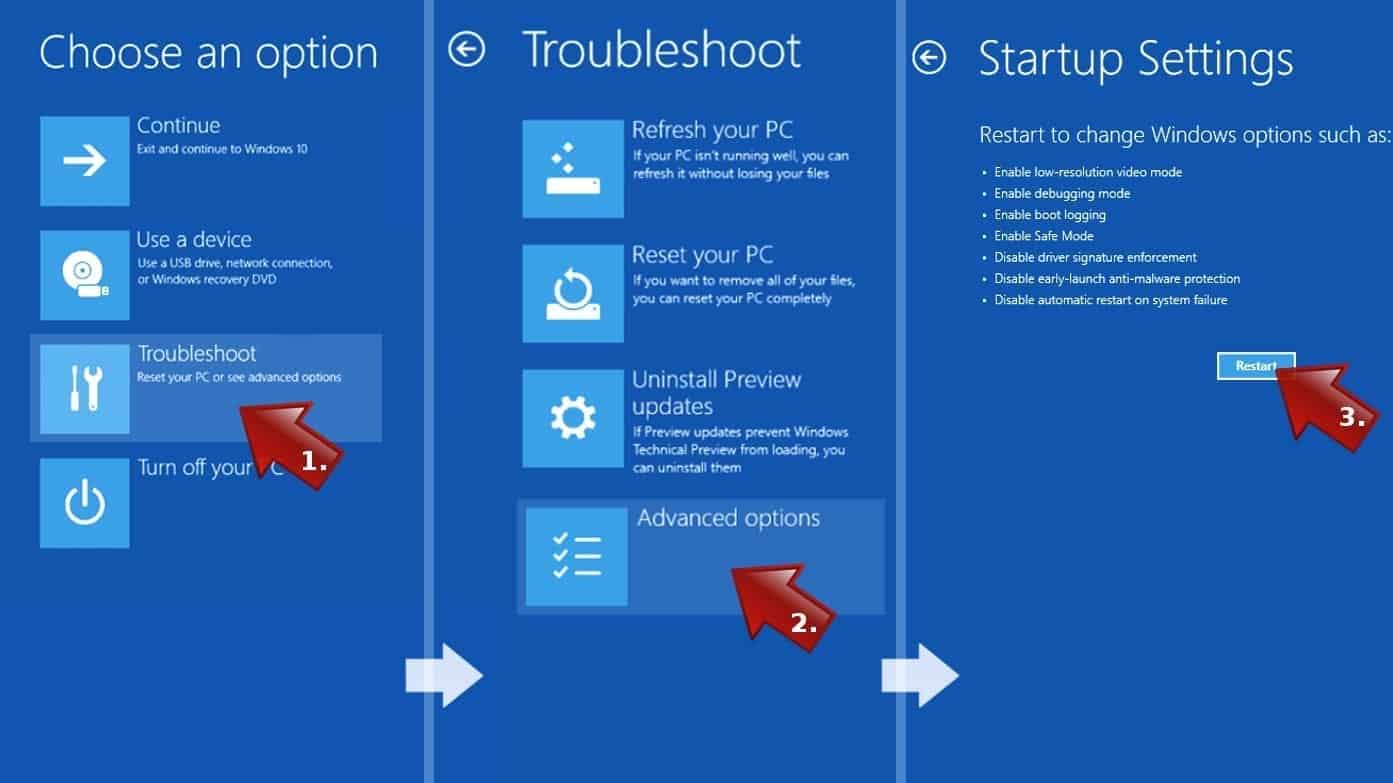
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
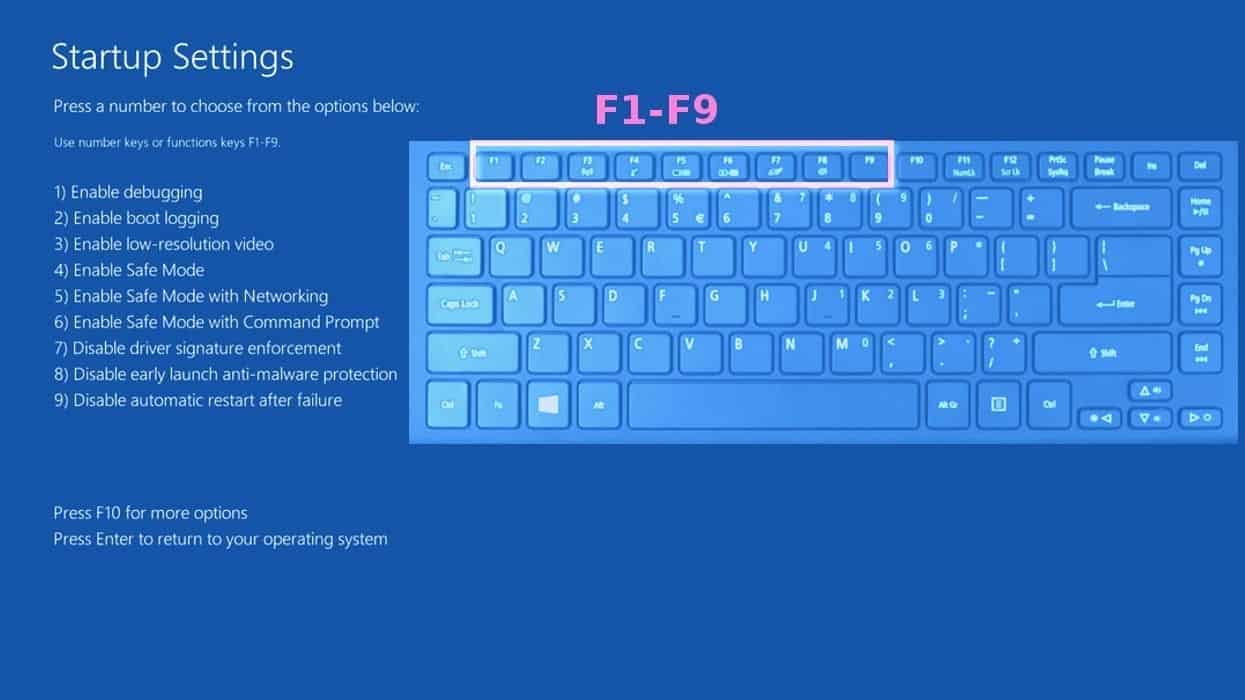
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove malware files. It is very hard to identify files and registry keys that belong to the virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. We recommend using SYSTEM MECHANIC ULTIMATE DEFENSE , which can also restore deleted files. Additionally. we recommend repairing virus damage using RESTORO.
Special Offer
Compatibility: Microsoft Windows
See Full Review
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
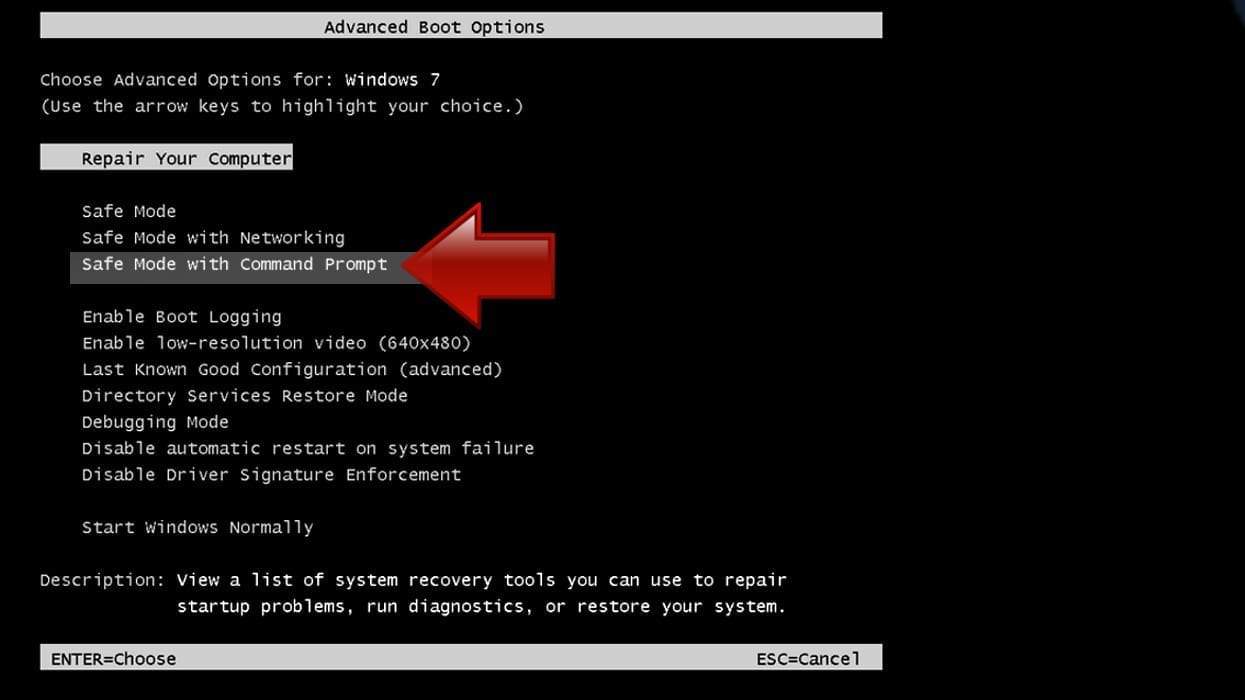
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.

- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before the malware infiltration.
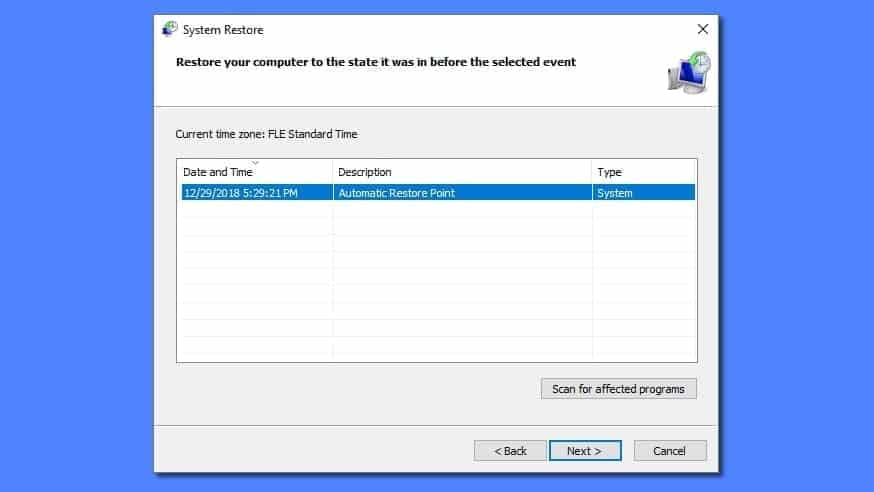
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Matt Corey is passionate about the latest tech news, gadgets and everything IT. Matt loves to criticize Windows and help people solve problems related to this operating system. When he’s not tinkering around with new gadgets he orders, he enjoys skydiving, as it is his favorite way to clear his mind and relax.
Leave a Reply