Lucky day for all DJVU ransomware victims – free decryption is available
Contents
STOP (DJVU) ransomware is finally defeated – the unbeatable malware analyst Michael Gillespie contributed to the most desired ransomware decryptor today. The analyst released a STOP DJVU Decrypter together with Emsisoft, and this tool can decrypt files locked by 148 variants out of 160.
According to Emsisoft, the ransomware encryption was broken by attacking the keystream using side-channel. To clarify, it is the first-ever used method to break ransomware encryption and help victims recover their files on a global scale.
The security firm forecasts that STOP Decryption tool will help approximately 70% of ransomware victims restore their files for free. Unfortunately, for the remaining 12 variants of the ransomware (which mostly emerged at the end of August 2019), no decryption solutions are found. Victims of these versions are advised to backup their files and wait.
Emsisoft reports that there are 116,000 confirmed DJVU ransomware victims and it is believed that the real number of victims is nearly half a million.
Decryption rules
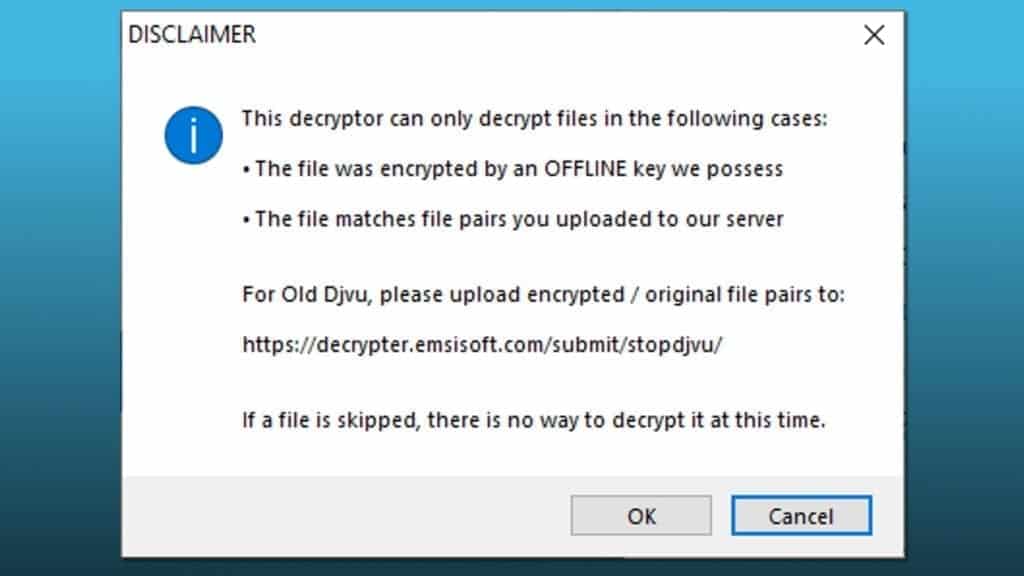
STOP/DJVU Decryptor can recover files using OFFLINE keys obtained by the malware researchers, or using encrypted+original file pairs submitted to Emsisoft’s server. In addition, these files must be over 150KB.
Unfortunately, ransomware variants which were pushed at the end of August 2019 (the new variants) cannot be decrypted at a time. Victims of these versions should backup the encoded data and hope for the best.
Beware of the Azorult Trojan bundled with the ransomware
This ransomware strain is known to bundle Azorult Trojan alongside it, which, once installed on the target system, starts stealing private data from the computer. Data that it steals mainly consists of logins, passwords, and other private information. It can be later used to empty victim’s bank accounts or be sold on the dark web.
Victims infected by STOP variants such as Bora, Reco, Noos, Nesa and others should first remove DJVU ransomware along with Azorult password-stealing trojan and then focus on data decryption.
Decryptable versions list
STOP/DJVU Decryptor can restore files locked by OFFLINE keys, and, if you’re lucky, ONLINE keys too. Check the extensions list below for all supported ransomware extensions.
.bora, .reco, .kuub, noos, .nesa, .karl, .kvag, .moka, .shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudeq, .godes, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovat, .roland, .refols, .grovas, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .rezuc, .stone, .skymap, .mogera, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .herad, .berosuce, .lokas, .budak, .vusad, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote, .gero, .hese, .seto, .peka, .puma, .pumax, .pumas, .DATAWAIT, .INFOWAIT.
If you are one of the people who were hit by this malicious file-encrypting virus, check the guide on how to decrypt STOP/DJVU encrypted files.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
My pc has been infected by the .rugj strain is there software available to decrypt
Fui infectado com o vírus .rugj randsomware e preciso muito recuperar meus arquivos. Qual orientação ?
my system was attacked by and all files got added extension “.zaps”. and now i have taken all dat copy to extern drive and formatted my system. need to recover data. what could be the possibility.
Fui infectado no dia 08 de Agosto de 2021, um vírus da variante STOP DJVU com a extensão .NOOA
Todos meus arquivos foram criptografados com uma onlineID.
Existe alguma esperança em recuperar os meus dados?
fui infectado por stop djvu de uma onlineID é possível recuperer os dados ?
All file encrypted to ORKF can you help me
Hello. My files are infected now, the extension is .ddsg . Can u help me? please!
I have been infected with .pahd randsomware virus and it is vital for me to recover my files. Is there any change to do that ? What`s your advice ? Thank you
i got a new ransomware may be by Djvu that extension file named by .ribd please help me to recovery my all file
moi j’ai ma thèse bloquée par l’extension .vpsh , je ne rien faire, j ‘ai besoin d’aide.