YOUR IPHONE HAS BEEN COMPROMISED pop-up shows up after clicking suspicious links
Contents
Your iPhone Has Been Compromised is a fake virus alert that appears after visiting a deceptive website via your iOS device. It suggests that the user’s browser is completely infected with a Trojan virus picked on recently visited websites. Typically the deceptive pop-up also has a line stating “Immediate Action is Required!” The sole aim of these deceptive pop-ups is to scare the user and force one to visit the App Store and download a recommended potentially unwanted app for virus removal. Keep in mind that the described notification is a scam, and a web page hardly can tell whether there are viruses on your device.
Users typically run into “Your iPhone has been Compromised. Immediate Action is Required” after visiting untrustworthy online websites, such as adult-only, gambling or gaming sites. Some examples of the domains related to this scam or redirecting to it are system-message24.com, reportsystem24.com, datinglocate.com, protect-os.com, fliter-er.com and others. However, you might also start receiving these pop-ups if you actually have some kind of adware-type infection on your device. Additionally, another way to run into such scam pages is by clicking on a web search result that leads to an expired domain that redirects to a deceptive website. No matter how you end up visiting the deceptive website, you should refrain from clicking anything on it and try to close it as soon as possible.

The Your iPhone has been compromised scam has several versions that provide different claims to scare the user. One of these suggests that user’s device has been infected with a Trojan virus, which needs to be removed as soon as possible. According to the scam pop-up, failure to follow pop-up’s instructions will result in private data loss, including victim’s bank card details, social network accounts, browser history and more. Another scam scheme suggests that there is hacker tracking the victim, thus victim’s Internet connections aren’t secure. This scam is used to promote questionable VPNs.
Such and similar pop-up scams including Your iPhone has been hacked or VIRUS ALERT FROM APPLE have been used to promote various adware, browser hijackers and other potentially unwanted programs. If you have got a pop-up saying you have a virus on your phone, we recommend running a device scan with a legitimate antivirus rather than some suspicious applications promoted in such shady ways. One tool to ensure Your iPhone has been compromised pop-up virus removal is INTEGO, a confirmed Mac antivirus with ability to scan your iOS devices and detect 100% of OS-specific threats. You can read its review here.
Remove iPhone virus using INTEGO ANTIVIRUS for Mac (includes scanning for iOS devices). The one-of-a-kind security suite provides VirusBarrier X9 real-time protection against Mac and Windows-based malware, removes existing threats and scans for malware in popular e-mail clients. Includes NetBarrier X9, an intelligent firewall for home, work and public connections.
Threat Summary
| Name | Your iPhone Has Been Compromised pop-up |
| Type | iPhone virus, Mac virus, Phishing, Scam |
| Description | Fake pop-ups stating that your iPhone has been compromised with Trojan virus and immediate action is required appear during browsing sessions. The pop-ups suggest installing various suspicious programs that supposedly should remove the “virus”. Another scam claims there is a hacker tracking the victim and promotes a VPN |
| Associated domains | datinglocate.com, flirter-er.com, sexyfinders.com, ok-yourlovers.com, vpnprotectors.com, erotclub.com, flirty-dates.com, adultlockator.com, systemtechnotify.com, protect-os.com, ios-protector.com, reportsbrowser.com, browsereport.com, app-reports.com, systemmobi.com, reportsystem24.com, thesingledate.com, myhotsingles.com, safesystemapp.com, tech-notify24.com, oc-systemnotice.com, system-message24.com, geparvpn.com, vpnios.com and others |
| Symptoms | Unwanted pop-ups appear during browsing sessions, device acts slower than usual, you see suspicious ads for software updates or alleged security programs |
| Distribution | You can get redirected to scam websites while browsing through untrustworthy websites, downloading illegal content or clicking on various links on dating, adult-only or gambling websites |
| Removal | If your iPhone has been compromised (actually) you can remove threats using confirmed Mac antivirus capable of scanning iOS devices – INTEGO. |

Avoid websites known to serve highly untrustworthy ads
Our security experts have agreed that iPhone users typically run into these ads after visiting untrustworthy websites. As mentioned earlier, you should avoid clicking on advertisements while browsing through adult-only, torrents, gambling or dating sites, unless you are visiting a well-known and legitimate website only. These types of sites tend to serve ads from ad networks that provide all sorts of not-so-reputable third-party sources. That said, you might encounter pop-up or pop-under ads, banners or lay-over ads while visiting them or clicking on link in them.
Moreover, be careful when you visit sites that provide all sorts of illegal downloads, including cracked software or copyright-protected movies. These kinds of websites often have resources full of malware, so cybersecurity experts advise staying away from them. Please download copyright-protected content from respective owners/developers only.
Finally, you can download various Mac viruses via fake ads that pose as legitimate software update suggestions. Most of the time, these arise as Java or Adobe Flash Player updates, but the fake installer behind these is designed to drag all sorts of adware (such as Adload) to your computer. Again, we recommend installing software updates from official sources only, in this case, from java.com or adobe.com, respectively.
Remove Your iPhone Has Been Compromised Pop-Up and secure your device
If you’re wondering what to do if you have encountered the fake pop-up, we recommend you to remove Your iPhone Has Been Compromised pop-up by closing the web page that displays it. Next, we recommend downloading INTEGO to your Mac, connecting the potentially infected iOS device and scanning it thoroughly.
We also present a manual Your iPhone has been compromised removal guide to prevent from seeing it ever again. Remember – this guide works if you’re dealing with a simple and not persistent version of Mac virus only.
- Unlock your iPhone and open Settings;

- Scroll down to find Safari and click on it;

- Find Block Pop-ups and Fraudulent Website Warning and swipe right to enable them;
- Navigate to the Advanced at the bottom;

- Click on Website Data and then press the Remove All Website Data button.
The following guide explains how to remove Mac viruses in general, block various pop-up ads and push notifications.
OUR GEEKS RECOMMEND
Keep your Mac virus-free with INTEGO, an exceptional antivirus with an option to scan other iOS devices. The VirusBarrier X9 offers 24/7 real-time protection against Mac and Windows malware, includes intelligent firewall (NetBarrier X9) for protecting your incoming/outgoing connections at home, work or public hotspots and more.
INTEGO antivirus is one of the leading security products for Mac that includes VirusBarrier X9 and NetBarrier X9 features allowing detection of viruses, ransomware, adware, browser hijackers, Trojans, backdoors and other threats and blocks suspicious network connections. If any detections are found, the software will eliminate them. Learn more about the software's features in its full review.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
Your iPhone has been hacked virus Removal Tutorial
Use the following guidelines to get rid of Your iPhone has been hacked virus on Mac. You will need to eliminate suspicious components from several system folders, move unwanted applications to Trash, delete shady profiles and login items created by the potentially unwanted program. Once you complete these steps, follow the instructions how to clean each affected web browser individually.
Eliminate components of unwanted program from Mac system folders
- Click Go in the Mac's Finder toolbar and select Utilities.
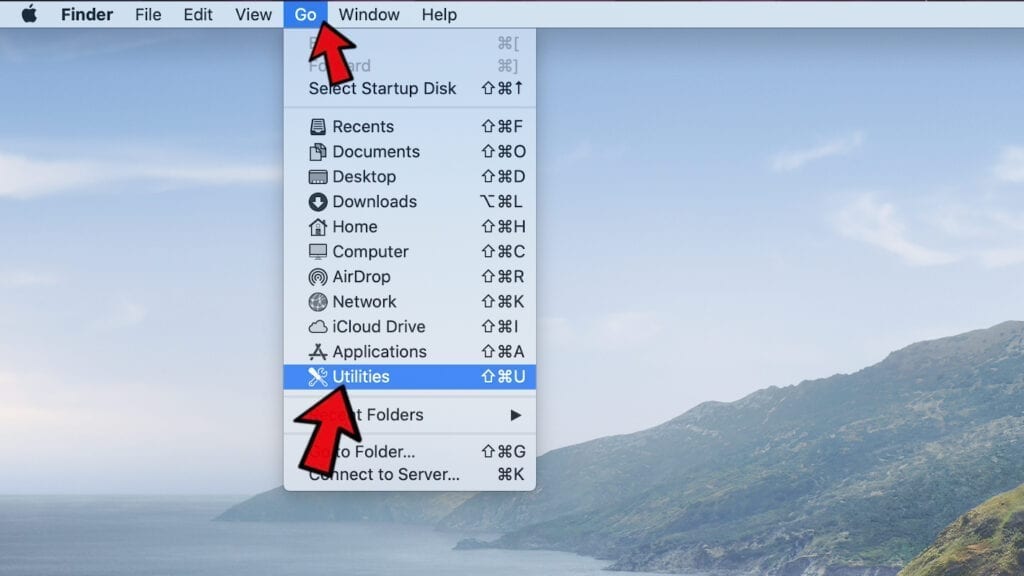
- Here, double-click Activity Monitor app.
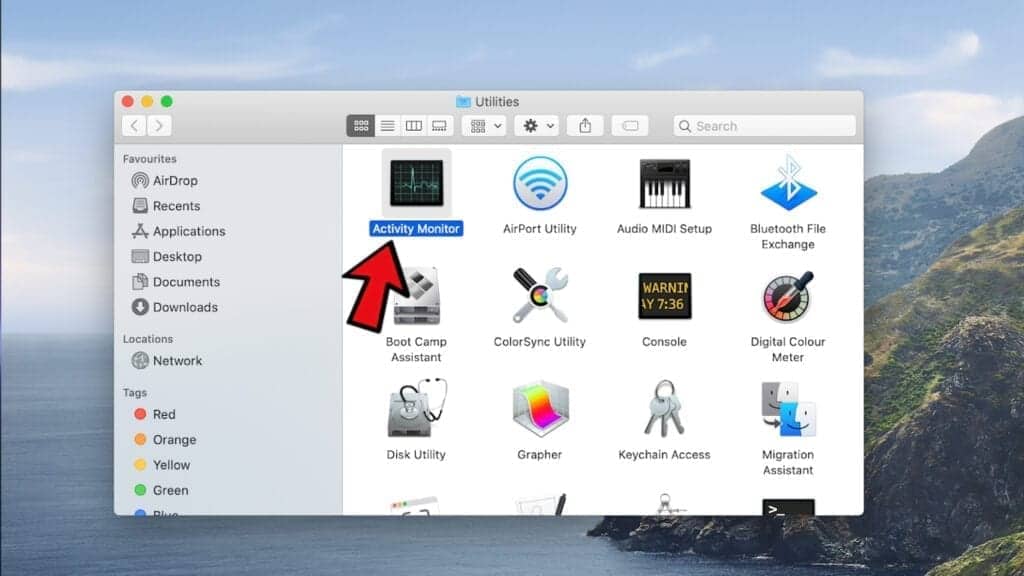
- In Activity Monitor, you will need to identify suspicious and resource-consuming apps, select them and click the X (Stop) button in the upper left corner of the window. Our suggestion is to search for Mac Security Plus, Spaces, BeAware, ScreenCapture or ScreenSaver apps and similar ones.
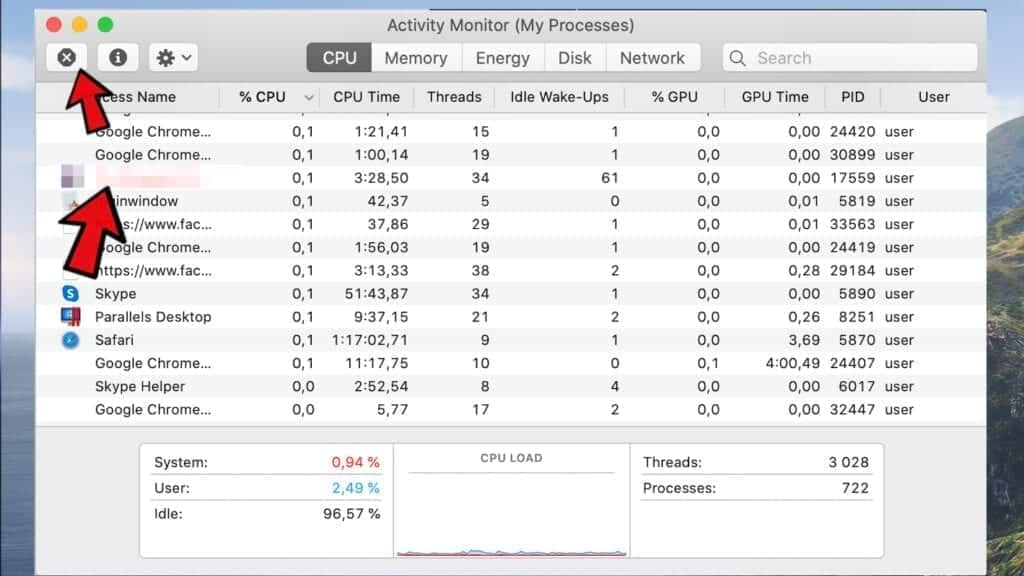
- After clicking the Stop button for an app, you will see a prompt asking do you really want to quit this process. Click Force Quit to continue.
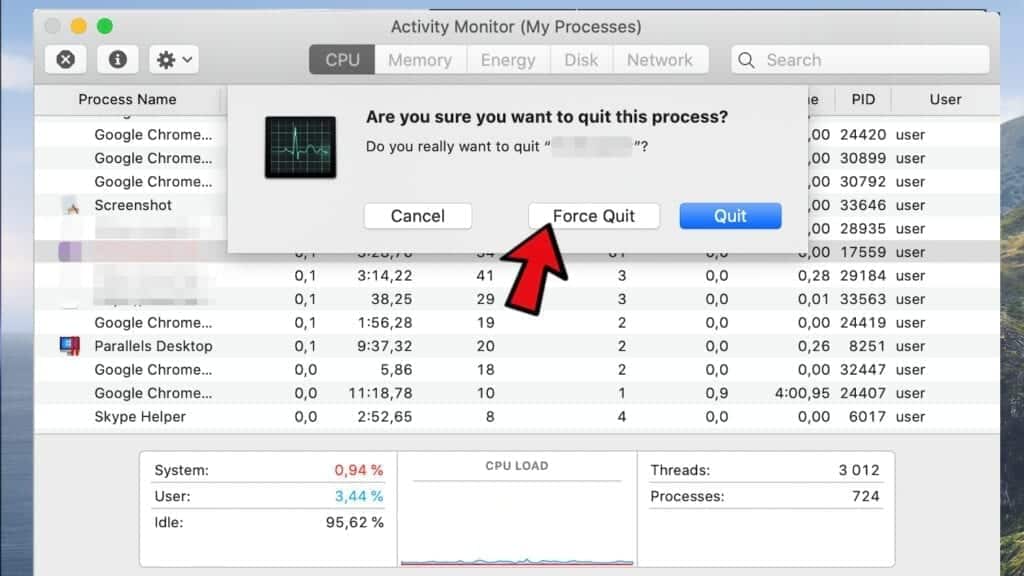
- Now, click the Go button in Mac's Finder toolbar and select Go to Folder...
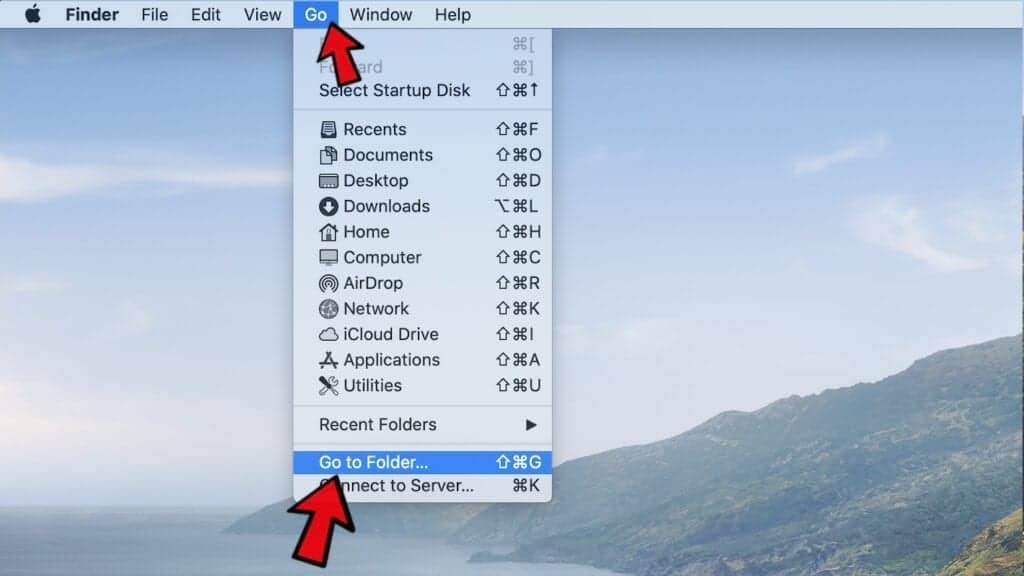
- Here, enter /Library/LaunchAgents and click Go.
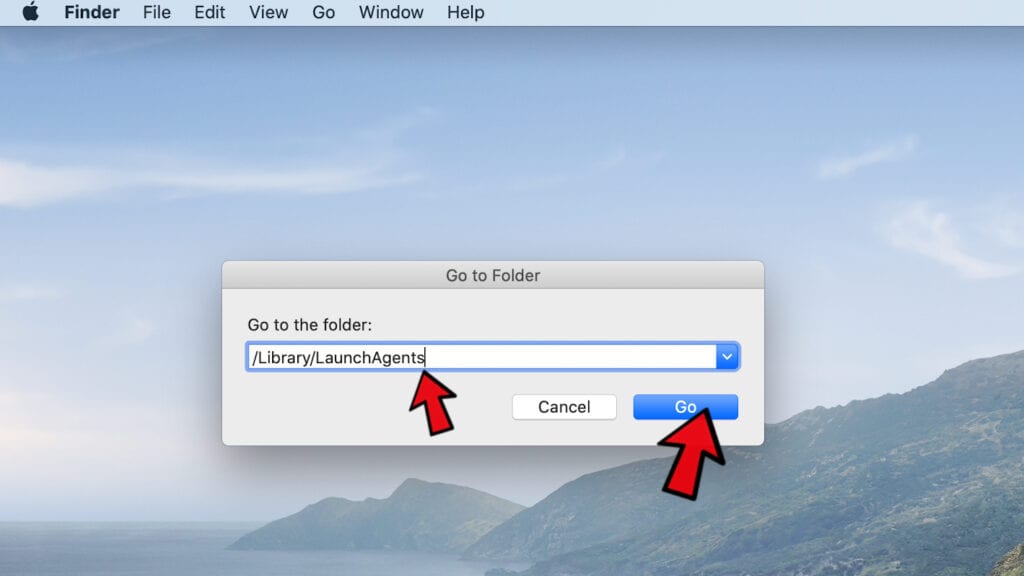
- Look through the opened folder for suspicious components that possibly belong to the Your iPhone has been hacked virus. Our recommendation is to look for unrecognized and recently added files. Then, move them to Trash/Bin.
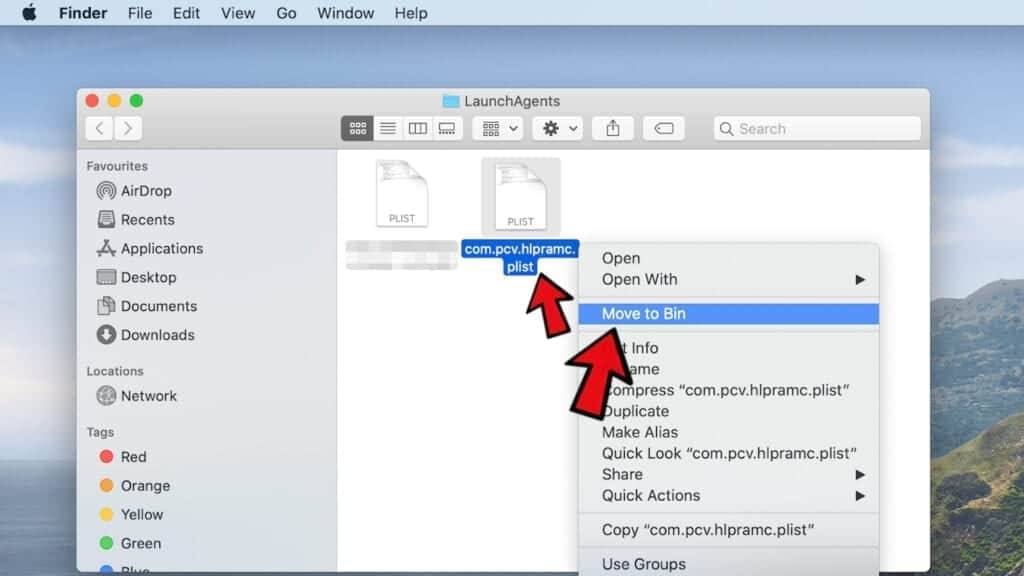 However, malware names hardly ever signal that they are somehow malicious, so you might want to check some questionable names online. For instance, examples of Mac malware related files include com.DataSearch.plist, com.ExpertModuleSearchP.plist, com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, com.msp.agent.plist and similar.
However, malware names hardly ever signal that they are somehow malicious, so you might want to check some questionable names online. For instance, examples of Mac malware related files include com.DataSearch.plist, com.ExpertModuleSearchP.plist, com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, com.msp.agent.plist and similar. - Using the Go to Folder feature, navigate to a location called ~/Library/Application Support. You can simply copy and paste this path to the go to Folder window and click Go.
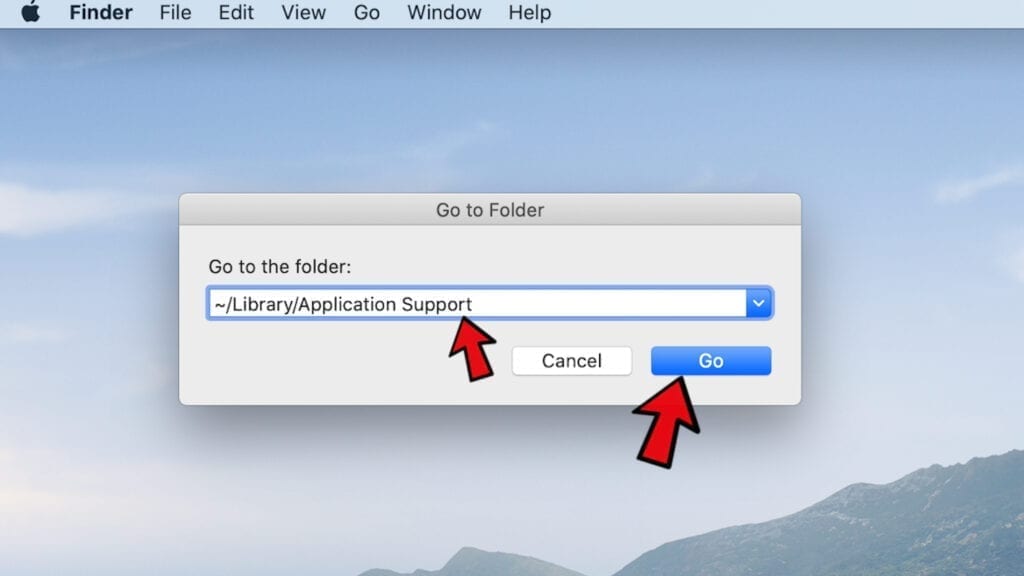
- Here, identify suspicious folders and move them to Trash. Again, you need to use your common sense and look for recently added programs that aren't related to Mac OS or apps you installed willingly. Examples of unwanted folders include SystemSpecial, IdeaShared, ProgressMatch and DataSearch.
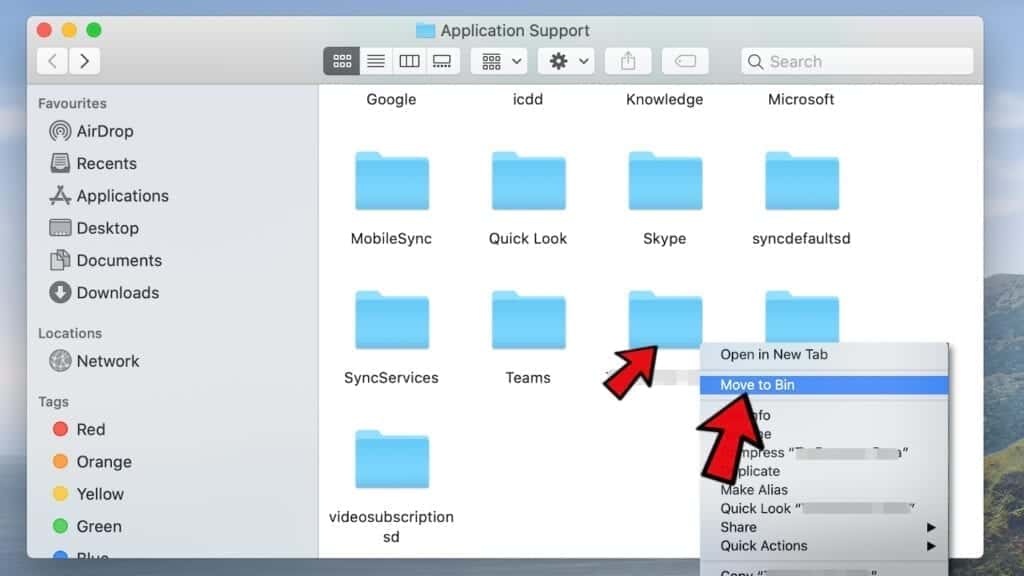
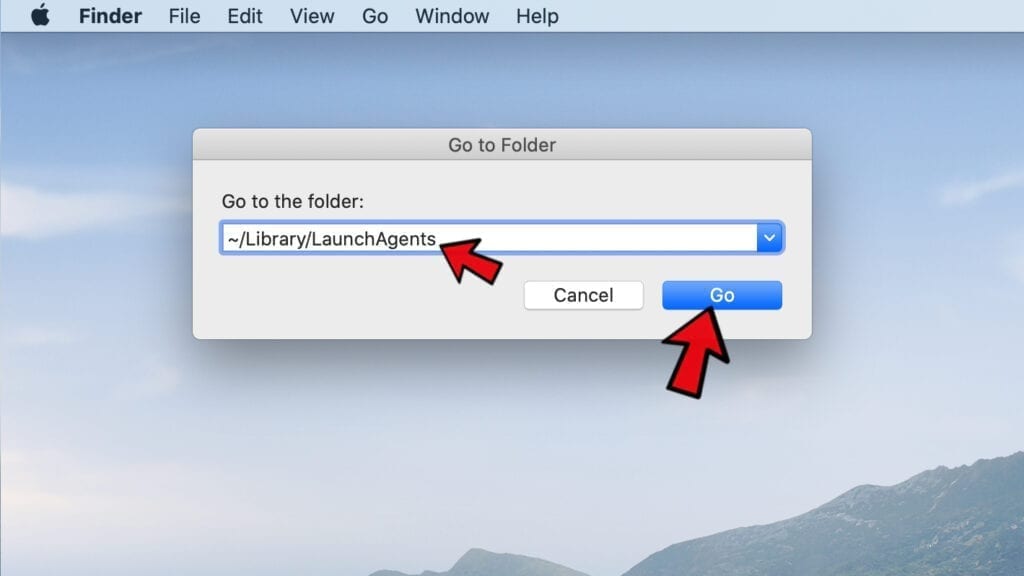
- Use Go to Folder feature once more to navigate to ~/Library/LaunchAgents.
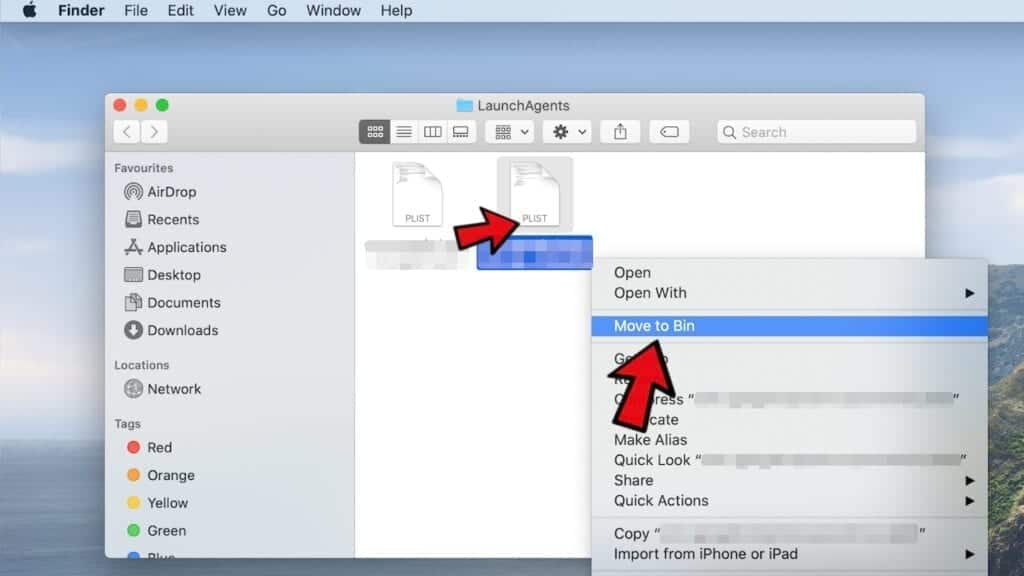
- Here, identify suspicious components and move them to Trash.
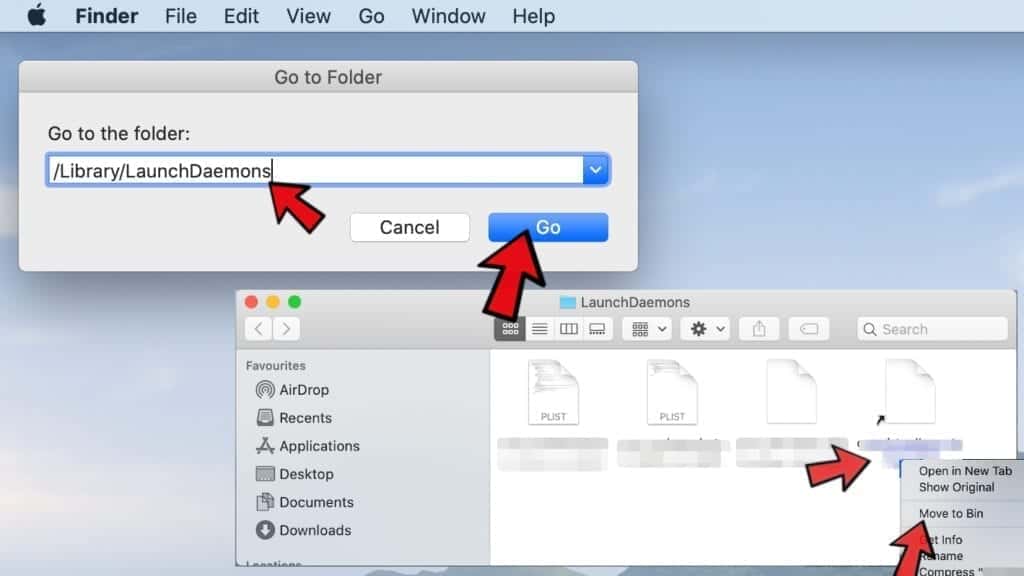
- Now, navigate to /Library/LaunchDaemons and eliminate strange or suspicious-looking components possibly related to Your iPhone has been hacked virus. Known examples of Mac-related malware store com.pplauncher.plist, com.ExpertModuleSearchDaemon.plist, com.DataSearchP.plist, com.startup.plist and similarly named files here.
Move unwanted applications to Trash
- Click on Finder.
- Go to Applications folder.
- Look for suspicious applications you can't remember installing. Right-click them and select Move to Trash.
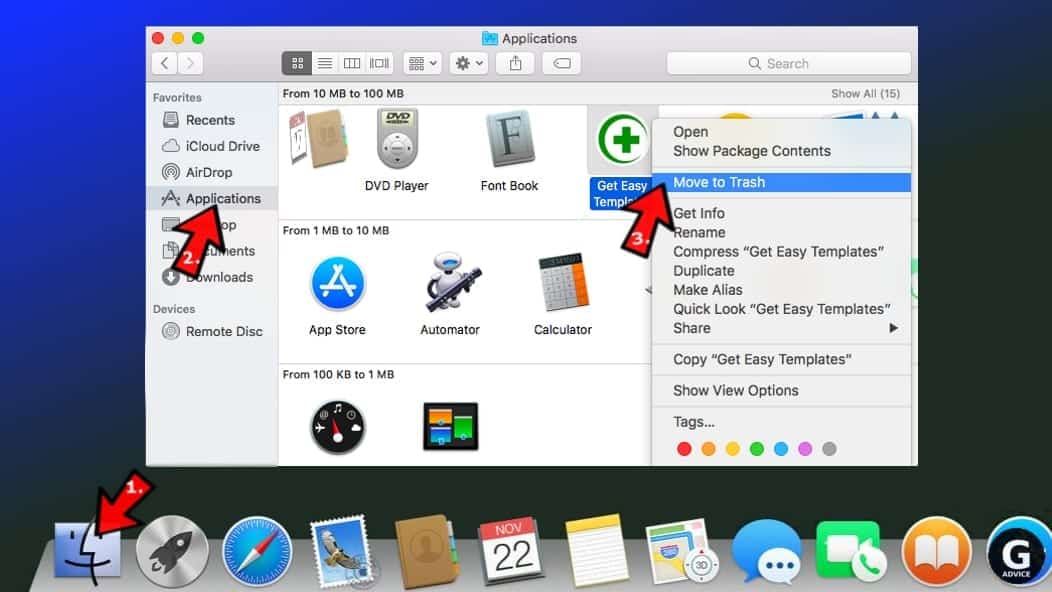
- After moving all suspicious apps to Trash, right-click the Trash bin in Mac's Dock and select Empty Trash.
Remove unwanted startup applications on Mac
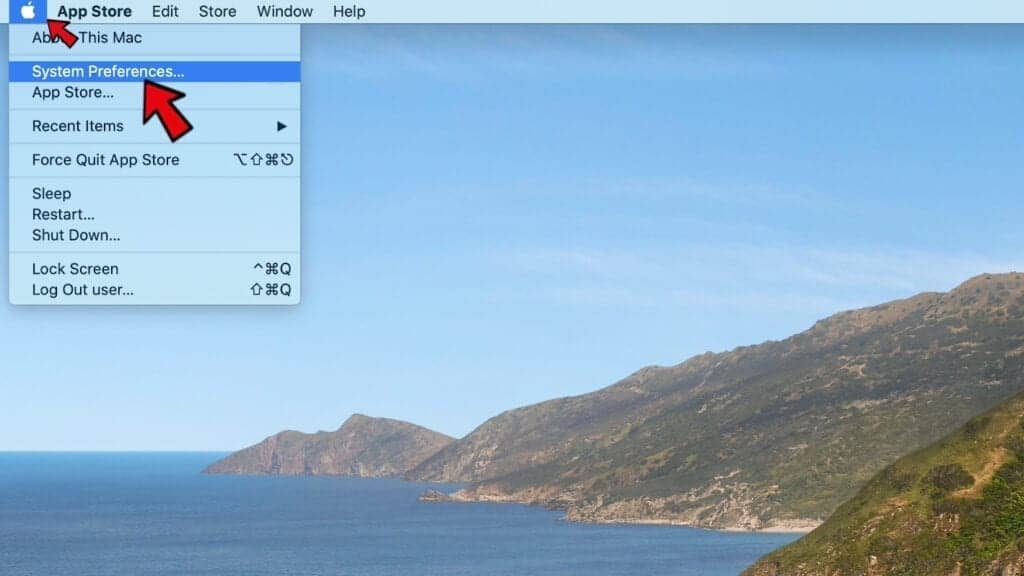
- Click on the Apple logo in the upper left corner and open System Preferences.
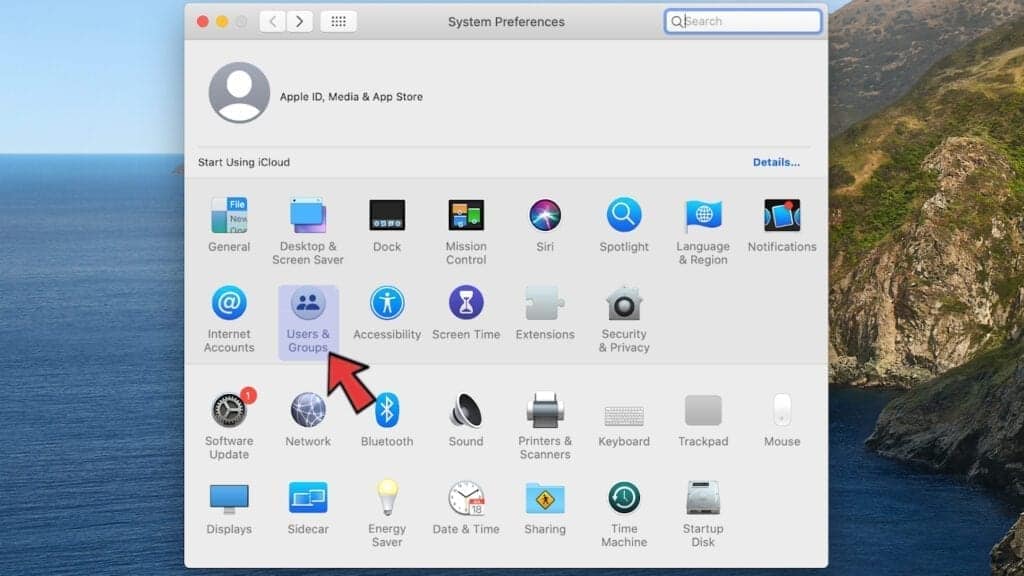
- In System Preferences, go to Users & Groups.
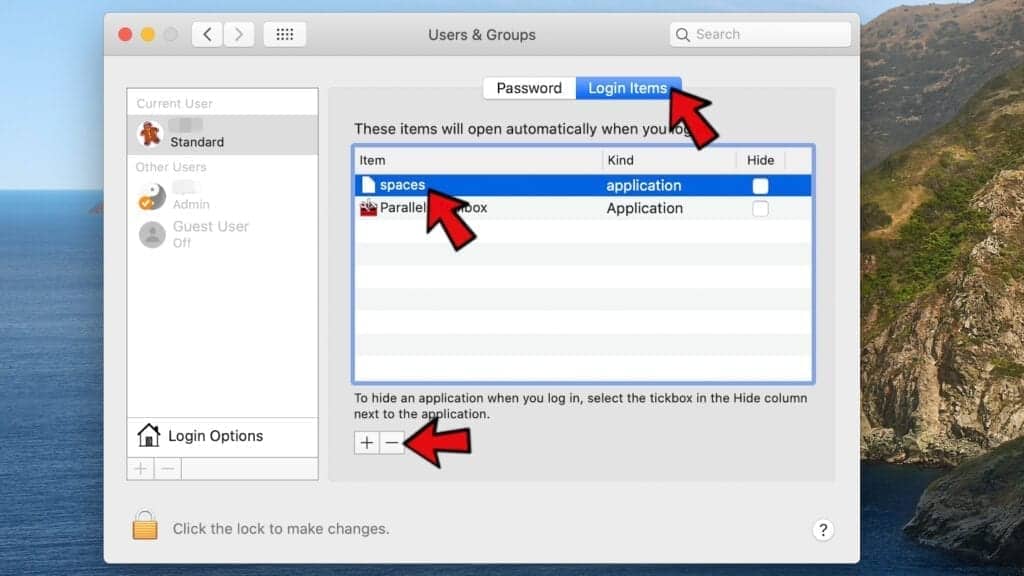
- Open Login items tab and look for suspicious applications that start during the Mac startup. Select unwanted app and click on minus (-) button to remove it from the list.
Delete malicious configuration profiles
- Go back by clicking < or close the window and reopen System Preferences via Mac toolbar. Go to Profiles.
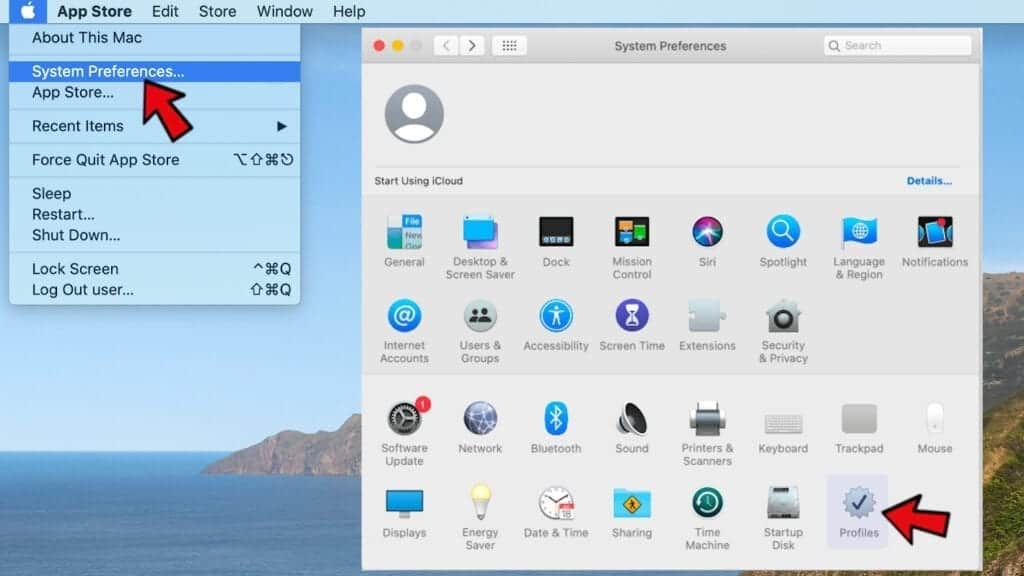
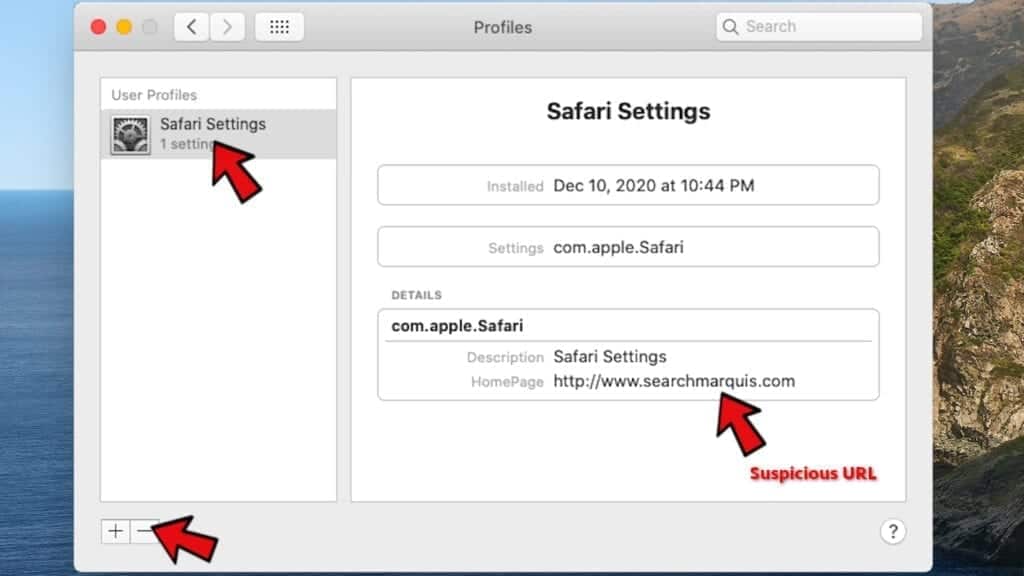
- In Profiles, inspect entries on the left pane. Look for suspicious configuration profiles hijacking your browsers' settings and click the minus (-) button to remove them. Examples of known malicious profiles include Chrome Settings, AdminPrefs, Safari Settings, MainSearchPlatform, TechSignalSearch, TechLetterSearch and similar. In example below, the profile includes a suspicious link, although it can contain a function to force browser changes when user tries to revert them.
Remove Your iPhone has been hacked virus from Safari
Uninstall suspicious Safari extensions
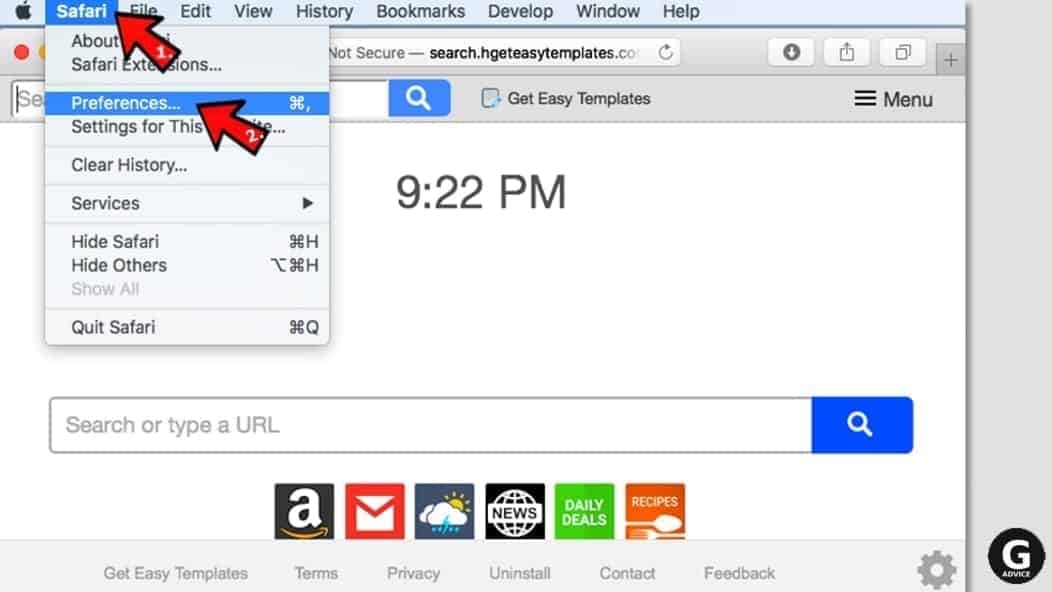
- Open Safari and click on Safari button in the top left corner. Select Preferences in the menu that appears on the screen.
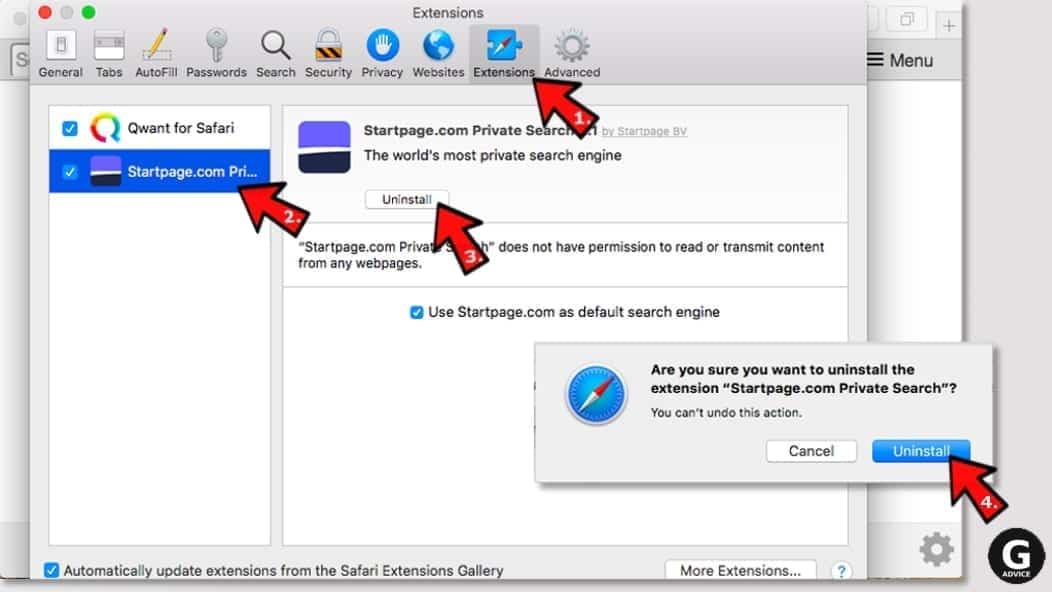
- Now, go to Extensions tab. Look at the left to see all installed extensions, click on suspicious ones and hit that Uninstall button as shown in the picture. Confirm your choice by clicking Uninstall again. Repeat until you get rid of all unwanted extensions.
Change Safari Homepage and default search engine
- In Preferences, open the General tab. Here, check what URL is set as your homepage. Delete it and type in whatever URL you want to set as your Safari Start Page.
- Next, go to the Search tab. Here, choose what Search engine you want to set as default.
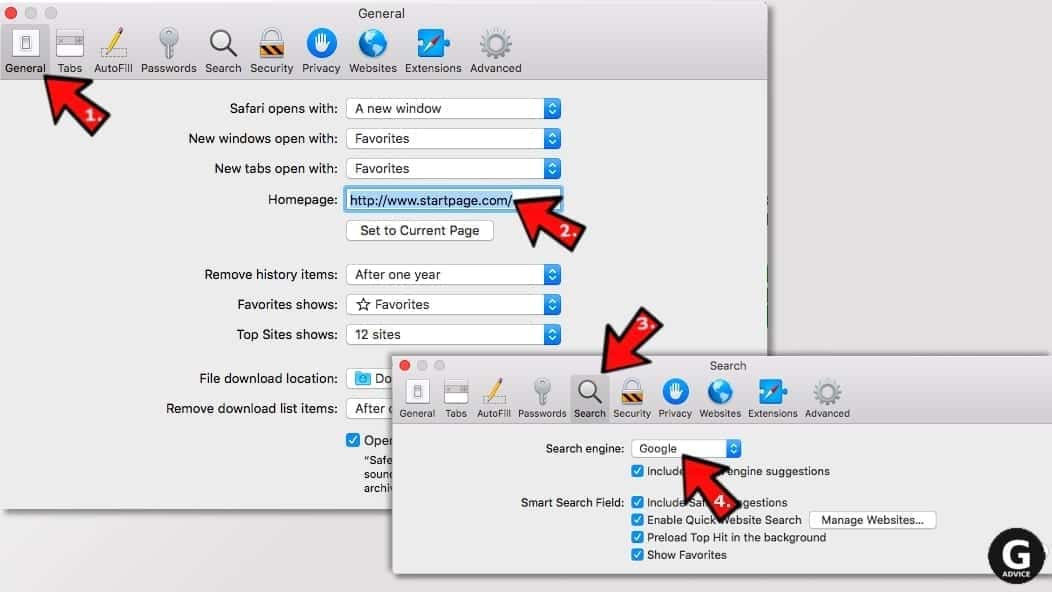
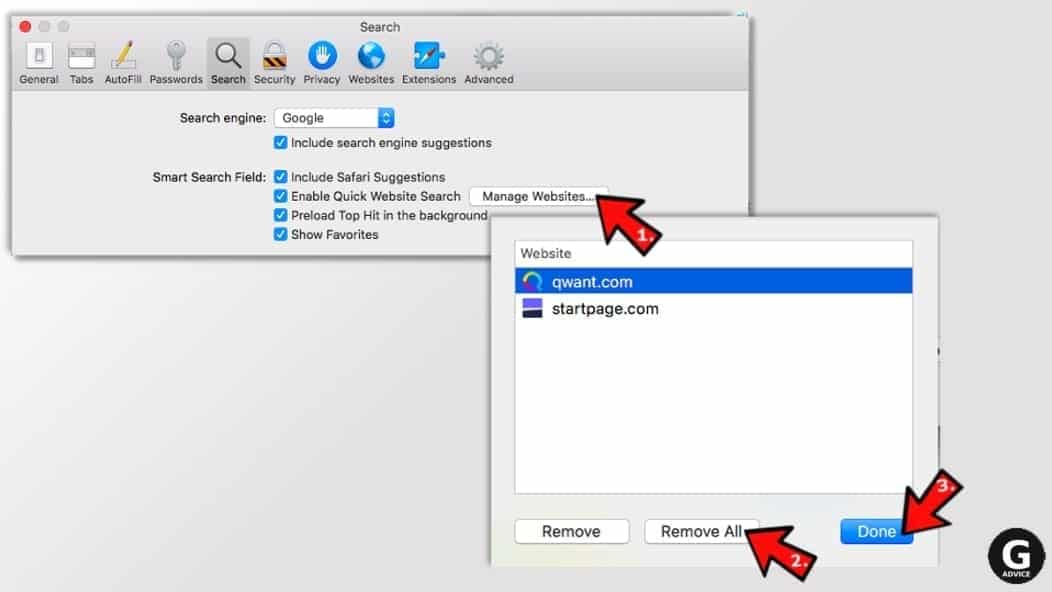
- Next, click on Manage websites... then Remove all... and then Done.
Remove push notifications on Safari
Some suspicious websites can try to corrupt your Safari by asking to enable push notifications. If you have accidentally agreed, your browser will be flooded with various intrusive advertisements and pop-ups. You can get rid of them by following this quick guide:
- Open Safari and click on Safari button in the top-left corner of the screen to select Preferences;
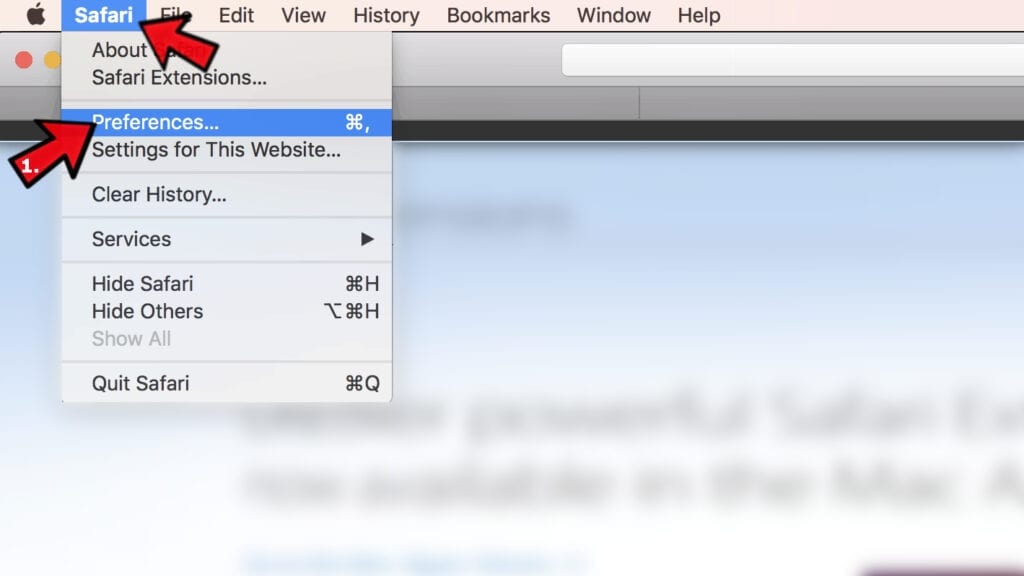
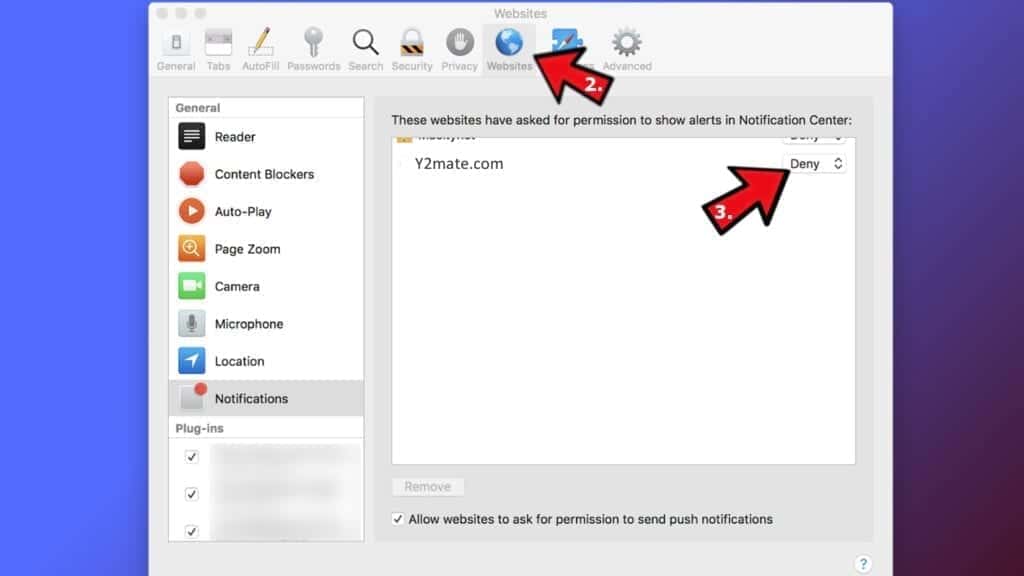
- Go to Websites tab and navigate to Notifications on the left side toolbar.
Reset Safari
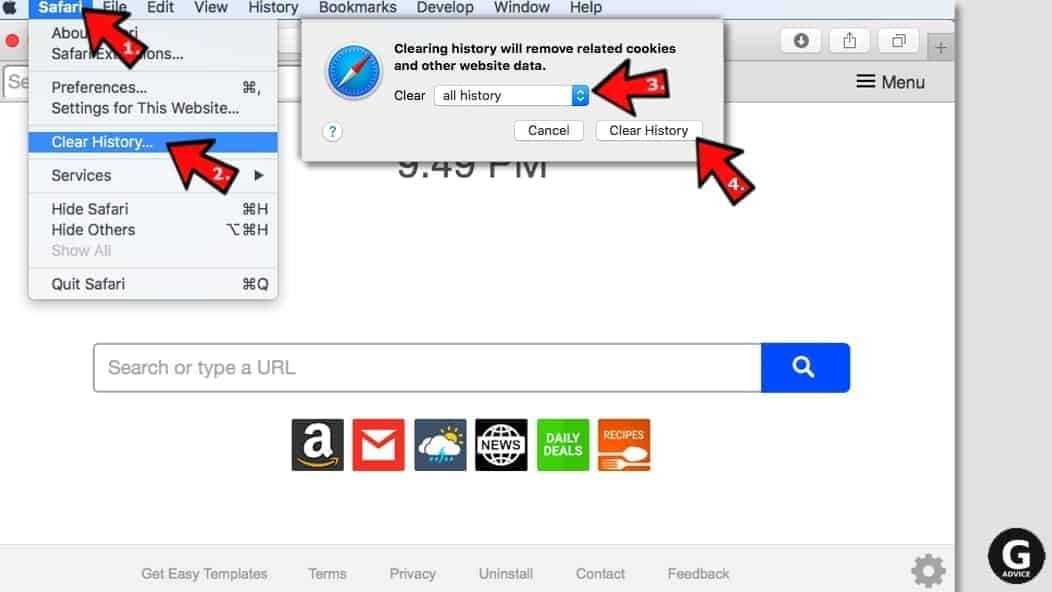
- Click on Safari > Clear History...
- Then choose to clear All history and hit Clear History button to confirm.
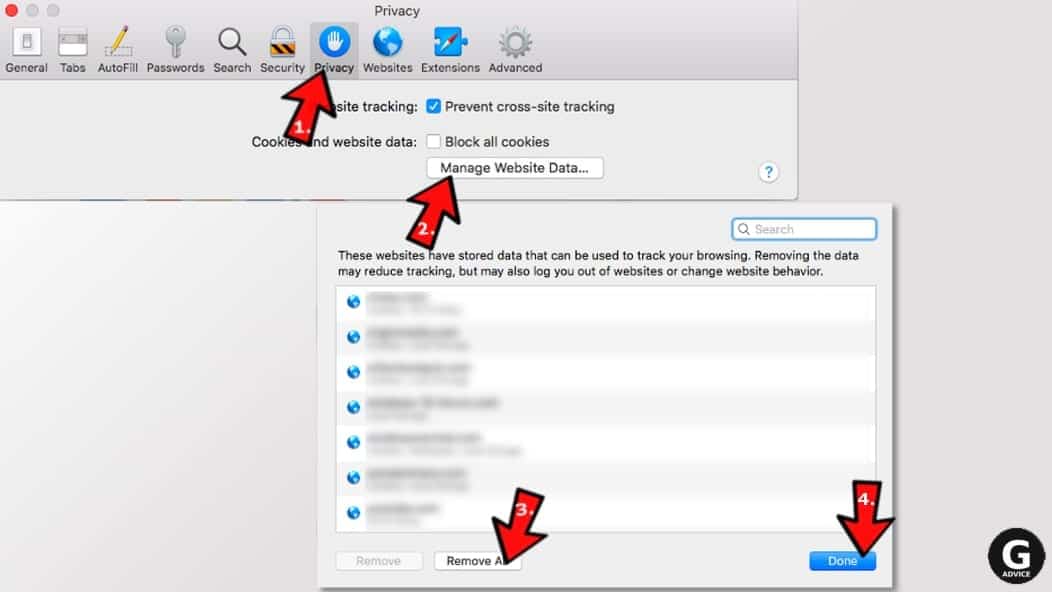
- Go to Safari > Preferences and then open Privacy tab.
- Click Manage Website Data... then Remove All. To finish, click Done.
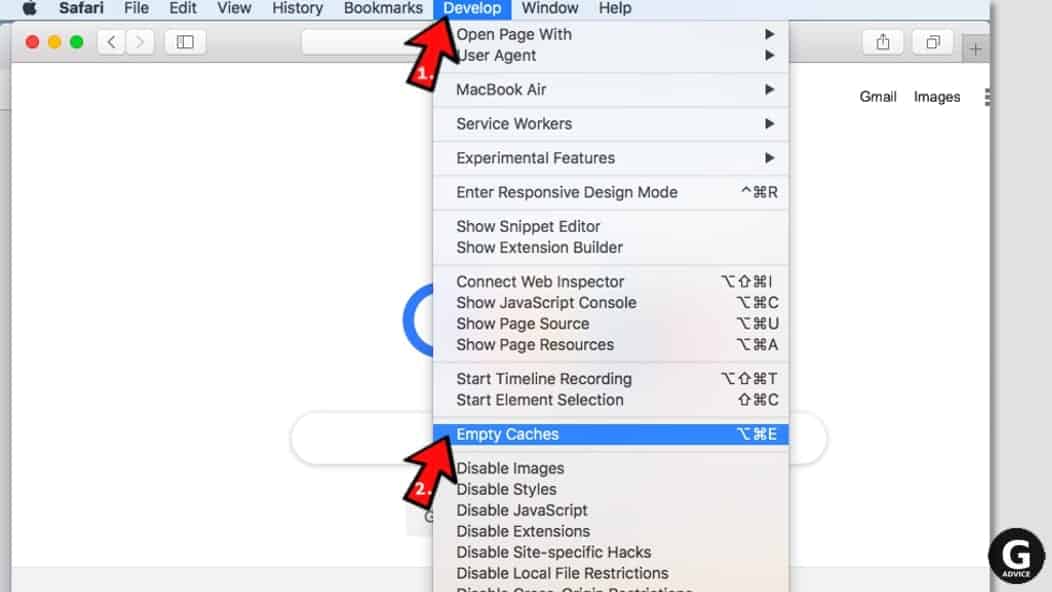
- Finally, clear Safari cache. In Safari Menu, click Develop > Clear Cache.
Remove Your iPhone has been hacked virus from Google Chrome
Remove suspicious Chrome extensions
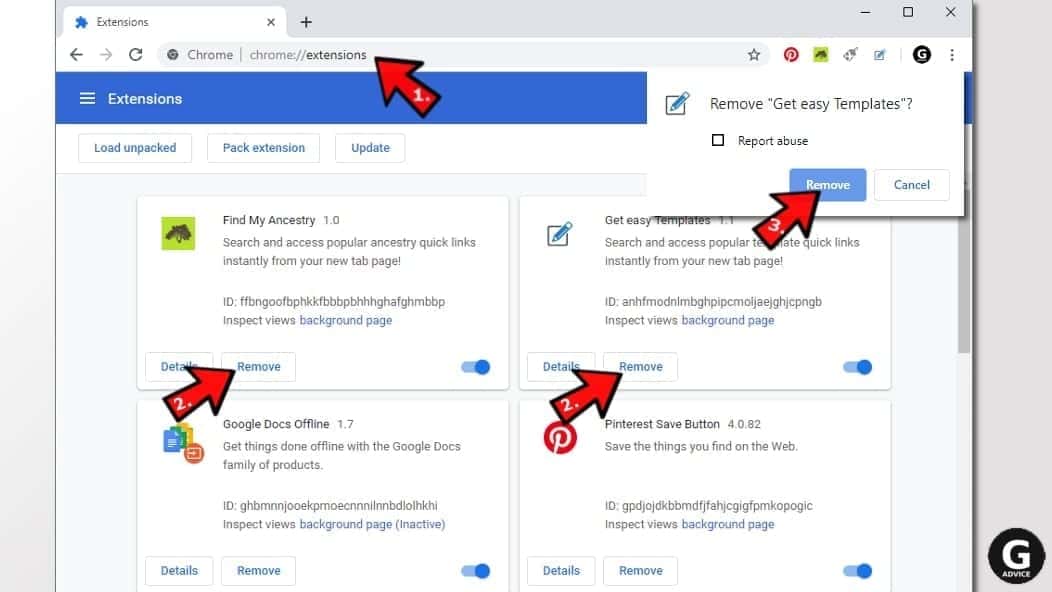
- Open Chrome and type chrome://extensions into address bar and press Enter.
- Here, look for suspicious extensions, and Remove them.
- Don't forget to confirm by pressing Remove in the confirmation pop-up.
Change Start Page settings
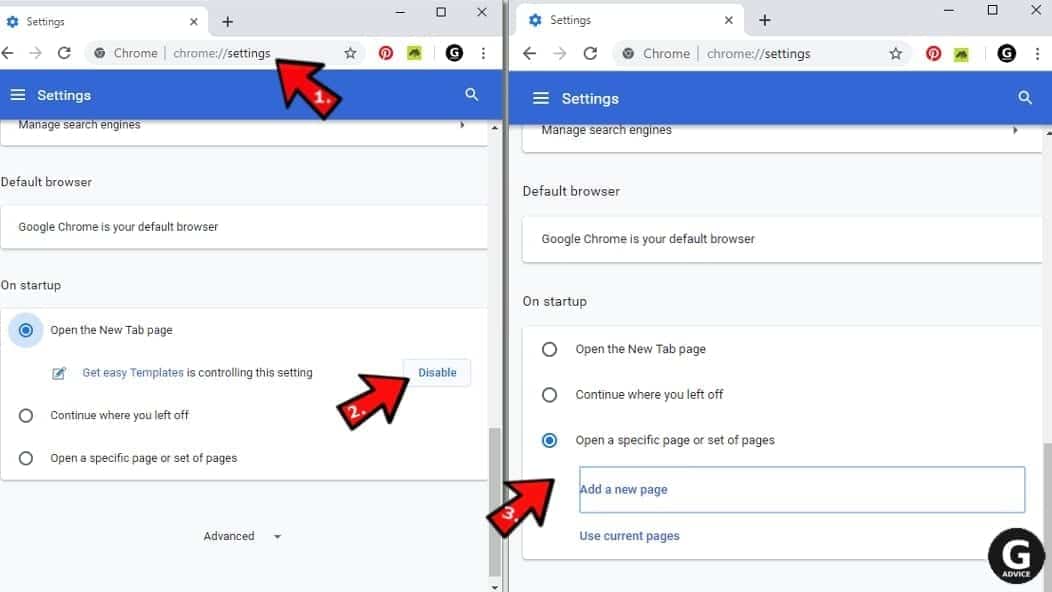
- In Chrome address bar, type chrome://settings and press Enter.
- Scroll down to the On startup section. Check for suspicious extensions controlling these settings, and Disable them.
- Additionally, you can set browser to Open a specific page or set of pages via these settings. Simply choose this option, click Add a new page, enter your preferred URL (f.e. www.google.com) and press Add.
Change default search settings
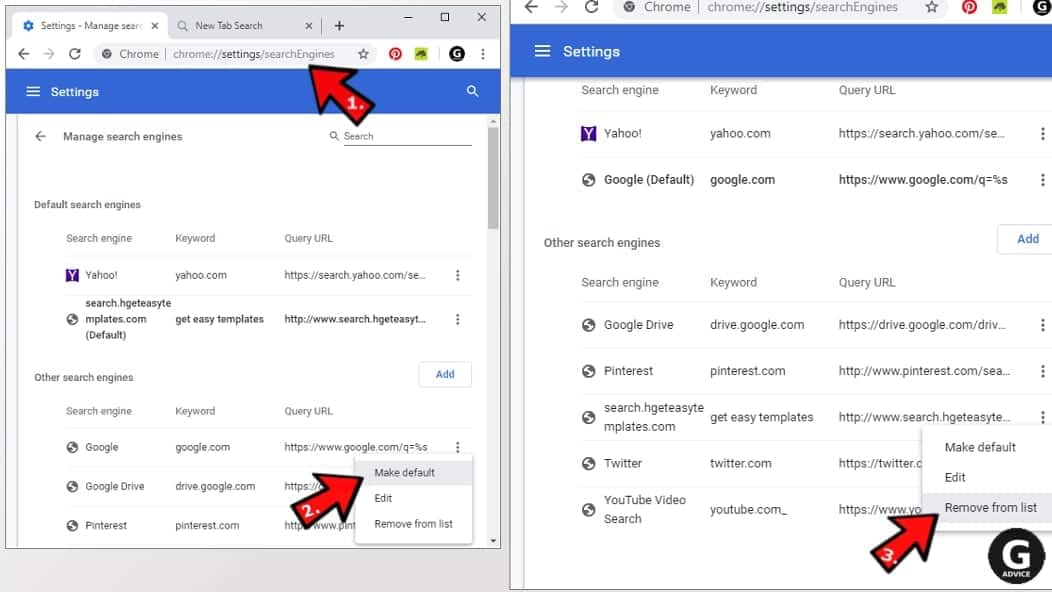
- In Chrome URL bar, type chrome://settings/searchEngines and press Enter. Make sure you type searchEngines, not searchengines. Additionally, you can go to chrome://settings and find Manage search engines option.
- First, look at the list of search engines and find the one you want to set as default. Click the three dots next to it and select Make Default.
- Finally, look through the list and eliminate suspicious entries. Right-click the three dots and select Remove from the list.
Remove push notifications from Chrome
If you want to get rid of the annoying ads and so-called push-notifications viruses, you must identify their components and clean your browser. You can easily remove ads from Chrome by following these steps:
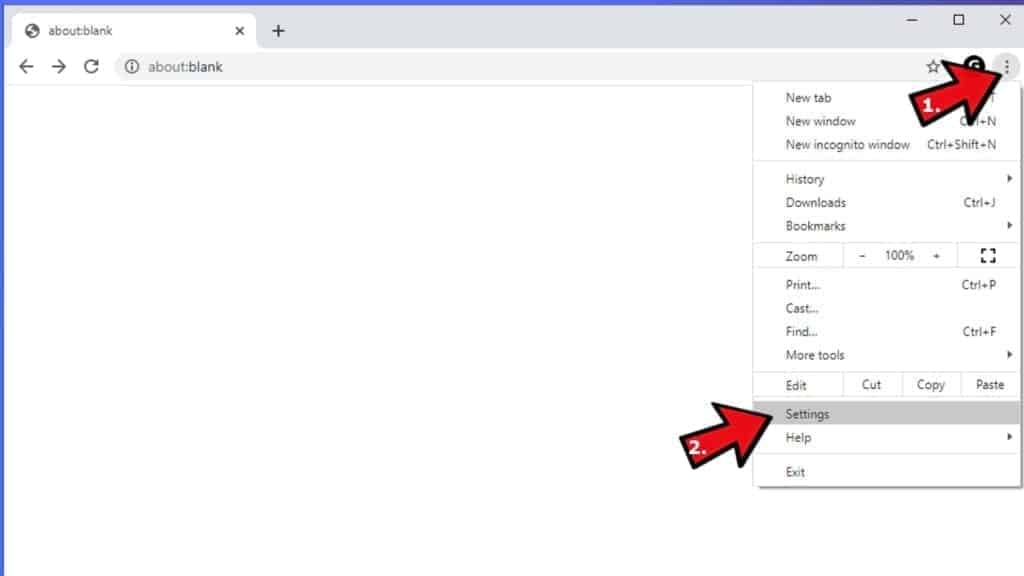
- In Google Chrome, press on Menu (upward arrow) in the top-right corner of the window.
- Select Settings.
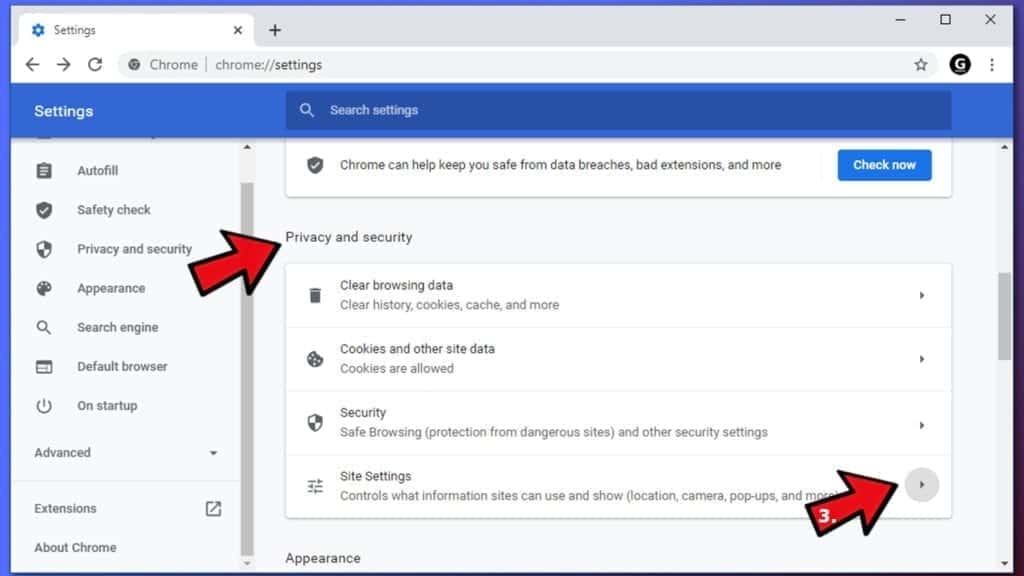
- Go to Privacy and Security > Site Settings.
- Open Notifications.
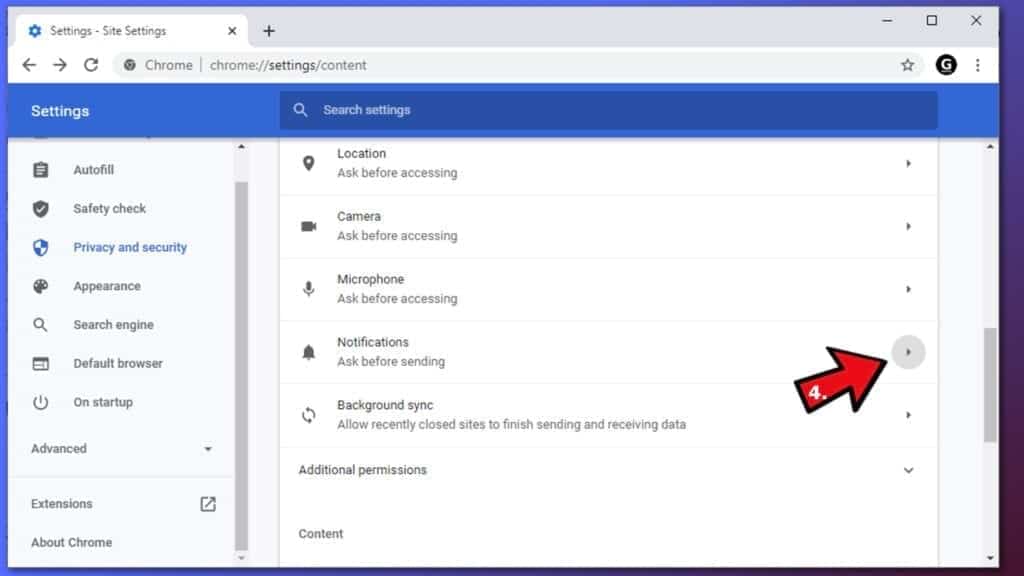
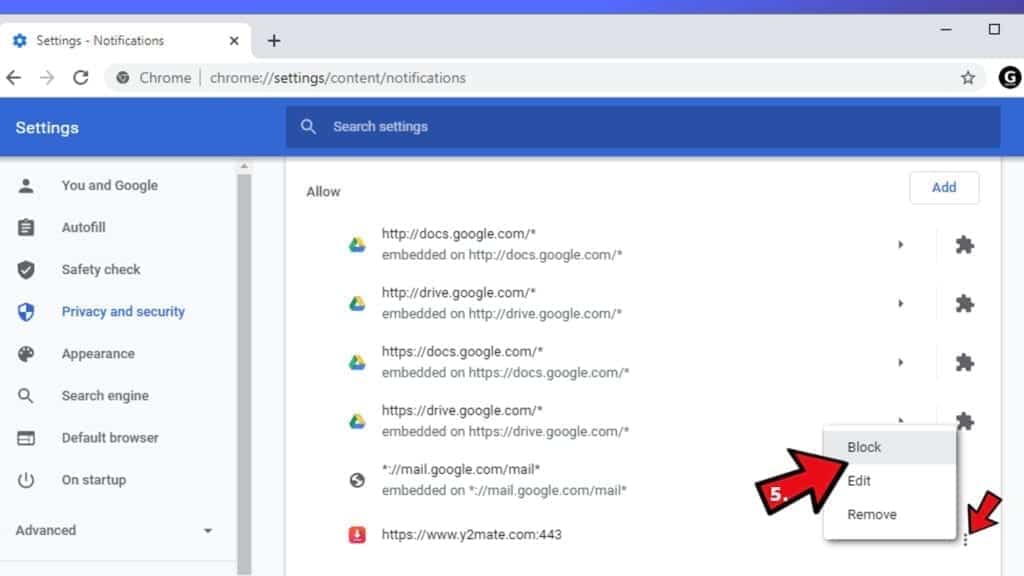
- Here, go to the Allow list and identify suspicious URLs. You can either Block or Remove by pressing on the three vertical dots on the right side of the URL. However, we suggest the Block option, so the site won't ask you to enable the notifications if you ever visit it again.
Reset Google Chrome browser
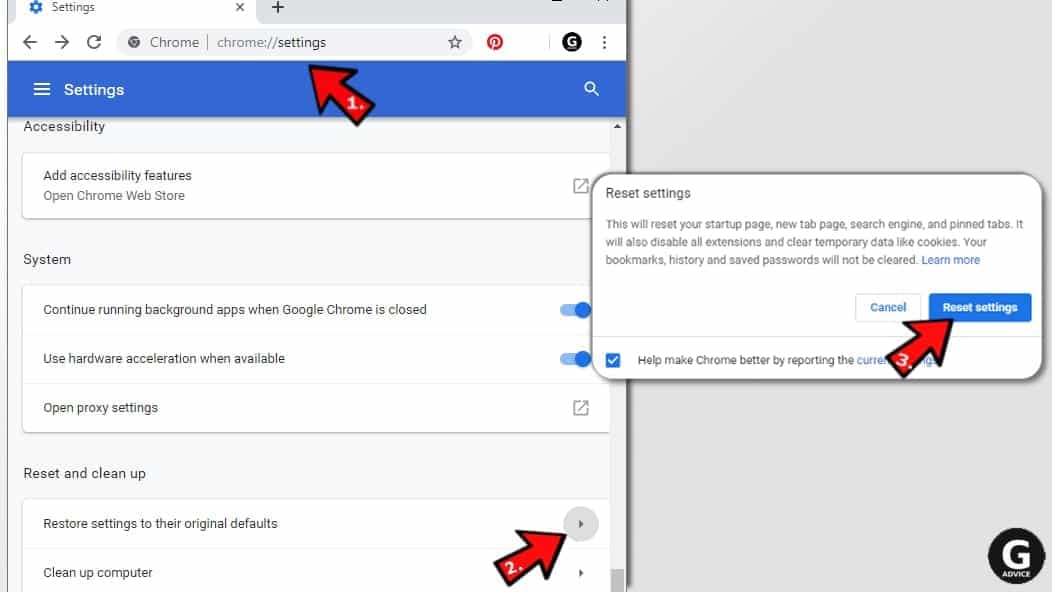
- The final option is to reset Google Chrome. Type chrome://settings in the URL bar, press Enter and then scroll down until you see Advanced option. Click it and scroll to the bottom of the settings.
- Click Restore settings to their original defaults.
- Click Restore settings to confirm.
Remove Your iPhone has been hacked virus from Mozilla Firefox
Remove unwanted add-ons from Firefox
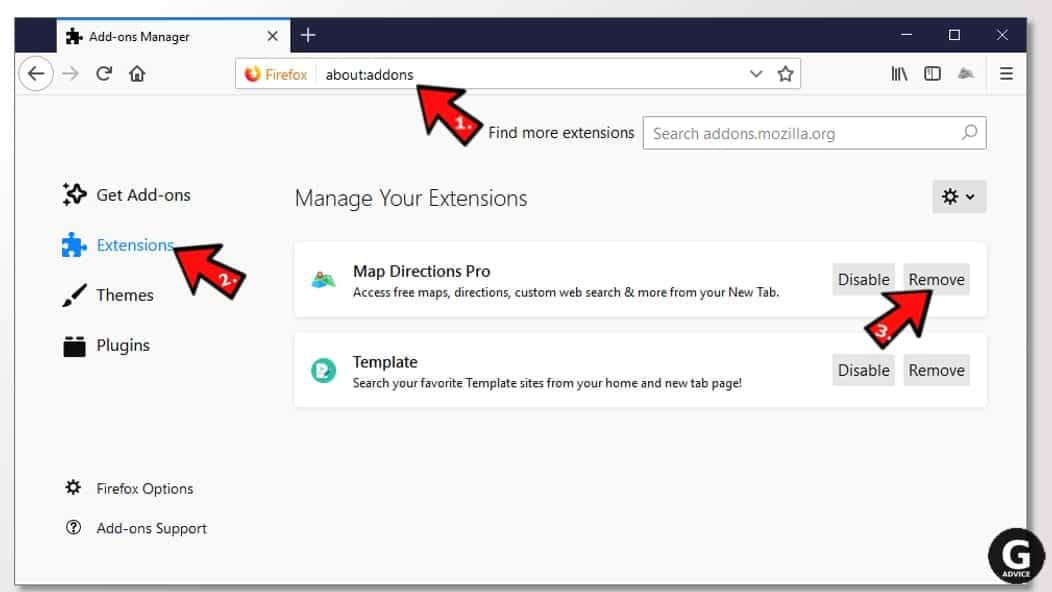
- Open Firefox and type about:addons in the URL bar. Press Enter.
- Now, click on Extensions (in the left section).
- Click Remove next to every suspicious browser add-on that you can't remember installing.
Change Firefox Homepage
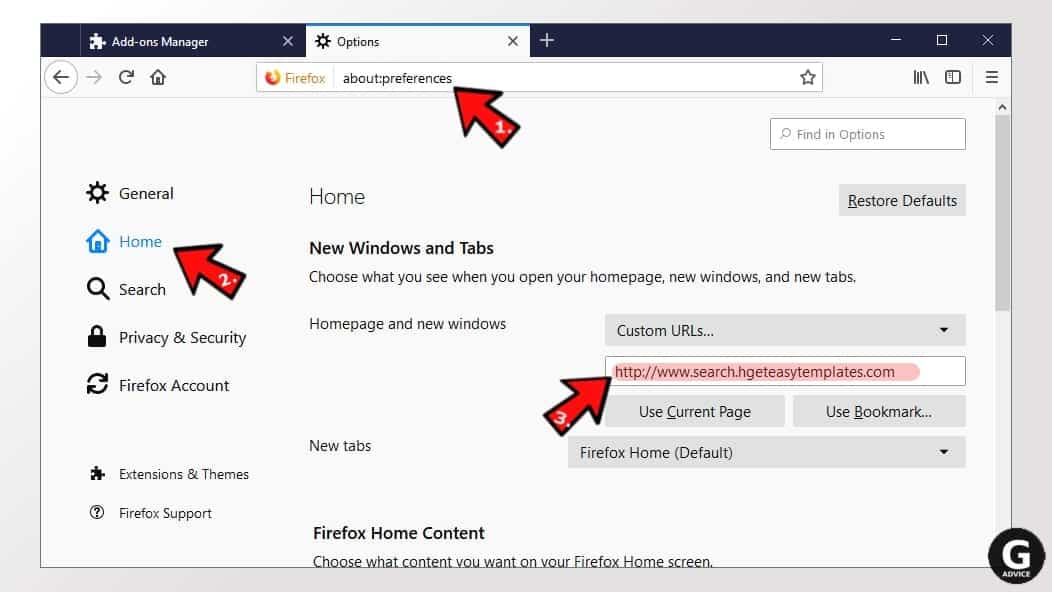
- In Firefox address bar, type about:preferences and hit Enter.
- Look at the left and click the Home tab.
- Here, delete the suspicious URL and type or paste in the URL of a website you'd like to set as your homepage.
Alter preferences in Firefox
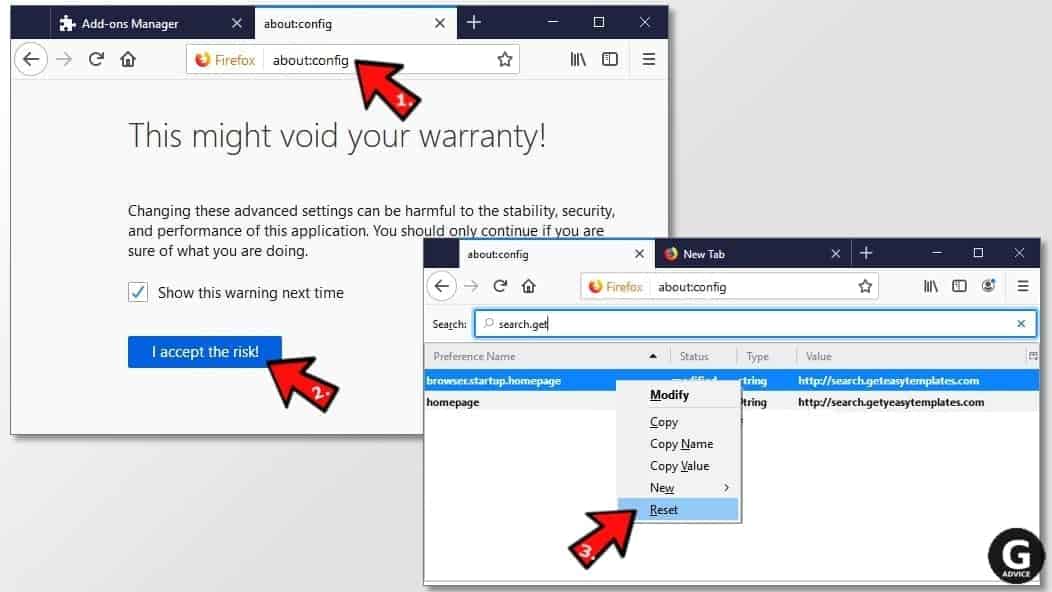
- Type about:config in Firefox address bar and hit Enter.
- Click I accept the risk! to continue.
- Here, type in the URL which has taken over your browser without your knowledge. Right-click each value that includes it and choose Reset.
Remove annoying push notifications from Firefox
Suspicious sites that ask to enable push notifications gain access to Mozilla's settings and can deliver intrusive advertisements when browsing the Internet. Therefore, you should remove access to your browser by following these simple steps:
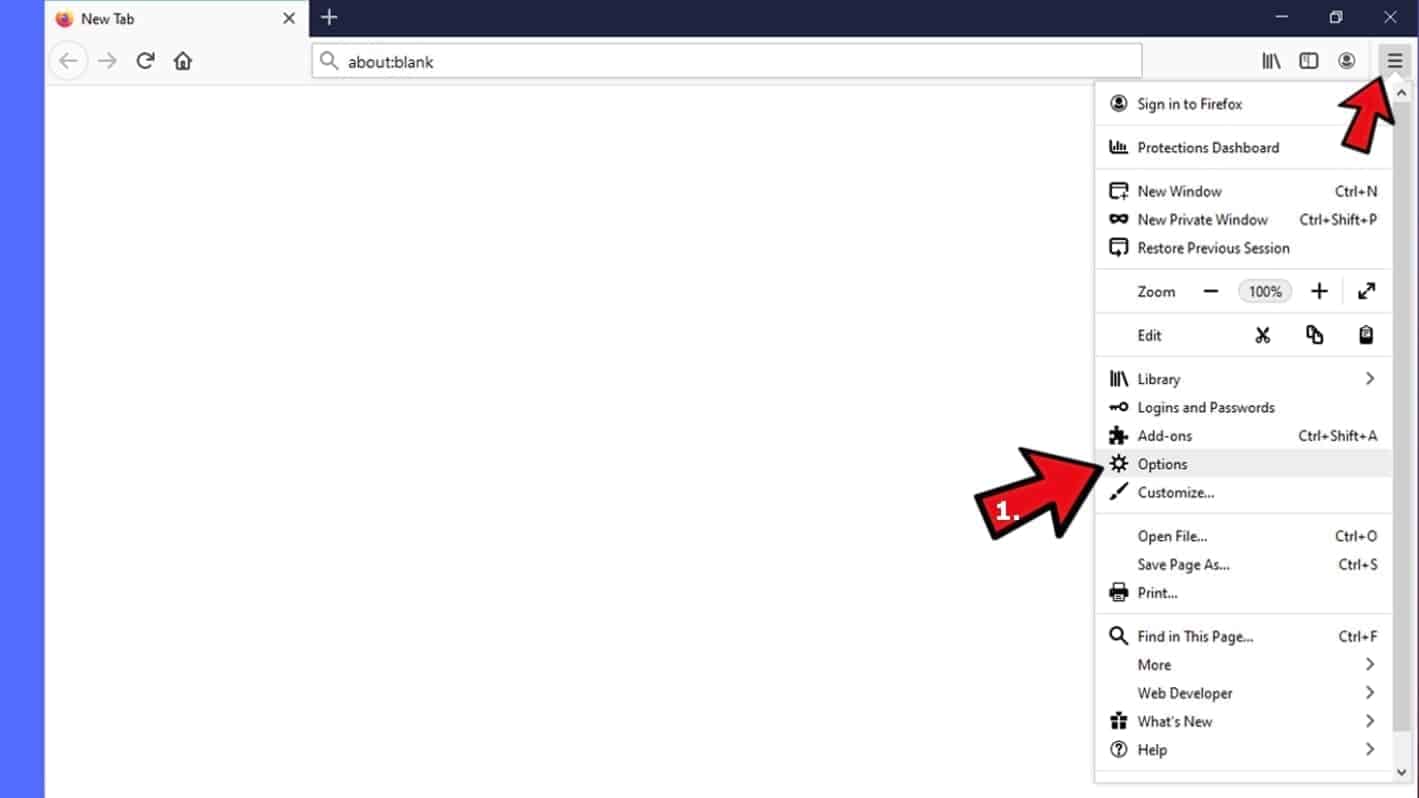
- In Mozilla Firefox, click on Menu (the three horizontal bars) on the top-right corner of the window, then choose Options.
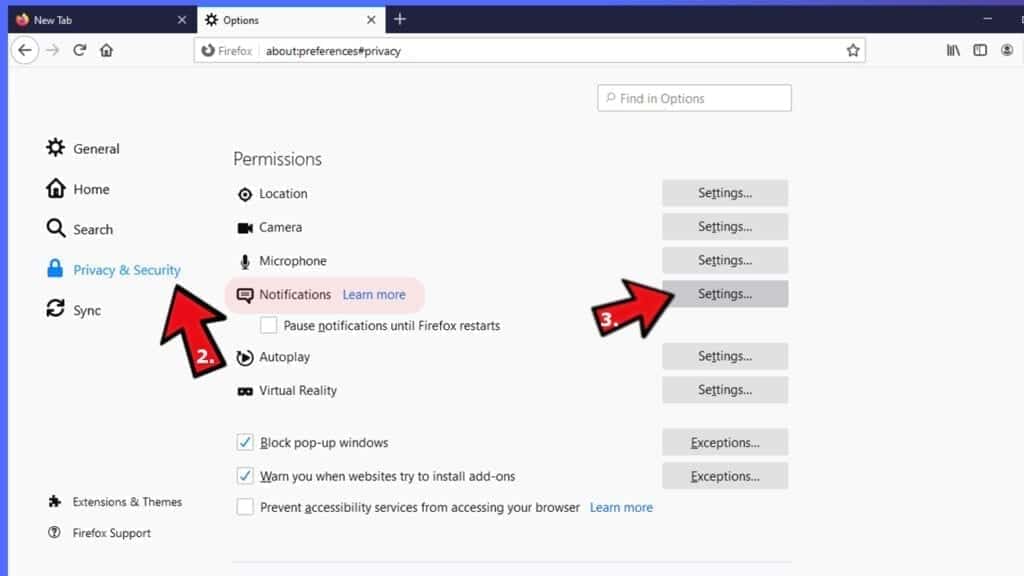
- Click on Privacy and Security, then scroll down to Permissions section.
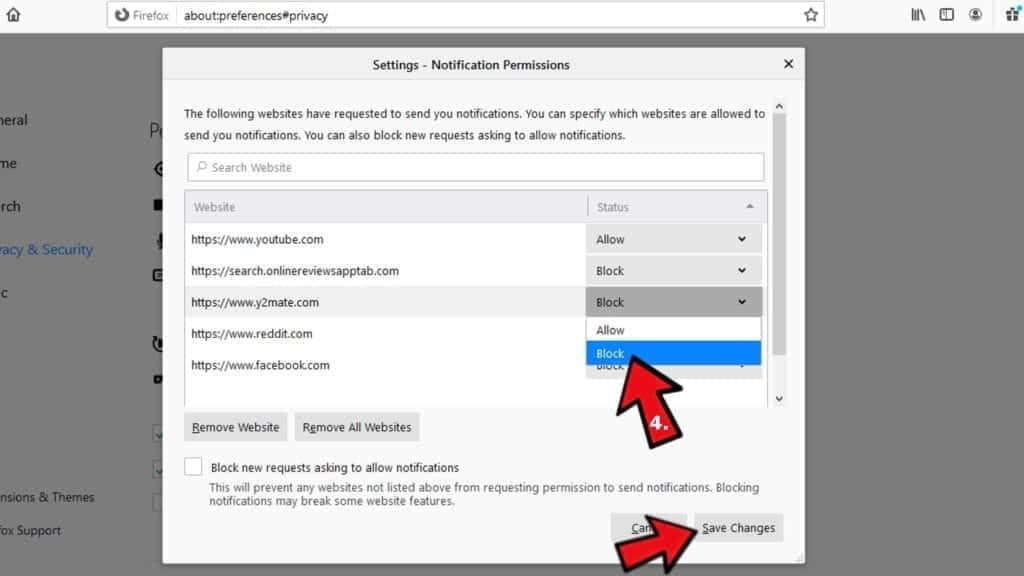
- Here, find Notifications and click Settings button next to it.
- Identify all unknown URLs and choose to Block them. Click Save Changes afterward.
Reset Mozilla Firefox
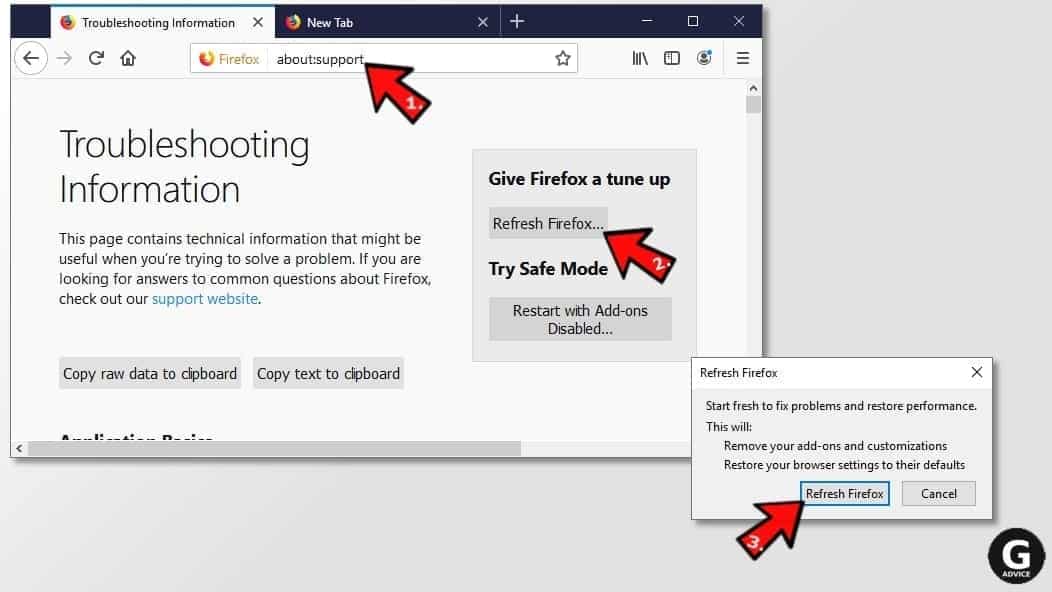
- In Firefox, type about:support in the address bar and press Enter.
- Click on Refresh Firefox...
- Click Refresh Firefox again to confirm.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Leave a Reply