Remove XHAMSTER Ransomware Virus (RECOVER .XHAMSTER FILES)
XHAMSTER ransomware locks your files using encryption
Contents
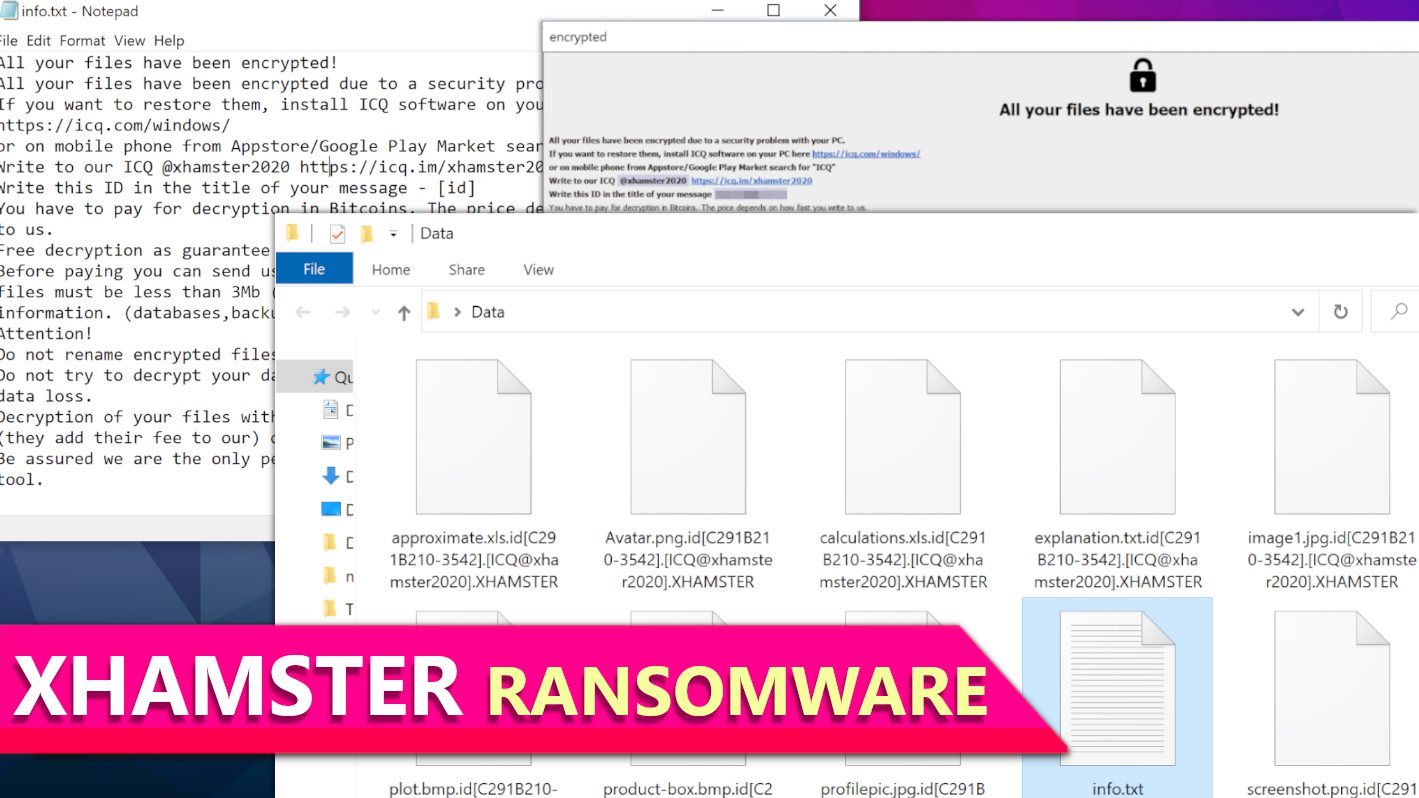
XHAMSTER ransomware is a computer virus designed to encrypt all files on the system, making them impossible to open. This virus is a variant of Phobos ransomware. After locking all data with military-grade encryption, it marks each file with a lengthy extension that contains victim’s ID, cybercriminals’ ICQ username and .XHAMSTER file marker. To illustrate, a file with a name 1.jpg will be renamed to 1.jpg.id[C291B210-3542].[ICQ@xhamster2020].XHAMSTER and the rest of data will be re-labeled in the same way. The ransomware also leaves ransom-demanding notes (info.hta and info.txt) on the computer, suggesting to purchase XHAMSTER file decryption tool for a specified price.
The primary target of XHAMSTER ransomware is to extort the computer user after taking one’s files hostage. The virus encrypts data using AES algorithm using 256-bit key. After being locked, files can be decrypted only using a private decryption key which is held by the attackers. They introduce an option to obtain this key and decryption software from them, however, the virus operators want the victim to pay a hefty ransom for this.
Overview of the ransom notes
This ransomware variant leaves two types of ransom notes on the computer. The first one is a text document called info.txt that claims that victim’s files were encrypted due to “security problem with the PC.” It also states that the victim has to install ICQ software and write to the attackers’ account which has an username @xhamster2020. The note also instructs to write victim’s ID in the title of the message.
As usual, the attackers want to receive the payment in cryptocurrency, or, to be precise, in Bitcoin as this helps them to keep their identity secret. According to the note, the attackers set the price depending on how quickly the victim writes to them after the attack takes place. They also suggest free decryption service on 5 encrypted files to prove that they actually can restore the data.
The second ransom note is called info.hta and it is a HTML application which appears on the screen after the attack. It contains almost identical information as the text note, however, it has a slightly stylised appearance.
It is important to emphasize that paying a ransom doesn’t guarantee data recovery after all. As stated in official FBI’s guidelines regarding ransomware attacks, it only encourages the attackers to continue their activities and infect more victims worldwide. Collecting ransoms regularly also enables them to expand their network and employ more malware developers and distributors.
Protect your computer at the earliest opportunity
It is essential to know that ransomware-type viruses often carry various Trojans that can silently steal your sensitive information, such as login credentials, browsing history, cookies and other data. For this reason, securing your computer should now be your top priority.
To remove XHAMSTER ransomware virus, we recommend following instructions provided below this article. You should boot your computer in Safe Mode with Networking in order to limit the malware’s processes so that your antivirus could do its job without unneeded interferences.
In case you haven’t decided which antivirus to use, our team recommends using a top-notch INTEGO Antivirus, which demonstrates excellent malware detection rates in independent AV lab tests. You can read more about it in its review. In addition, we recommend downloading this tool – RESTORO to scan and identify virus damage to Windows OS files. Paid version of this tool can fix detected damage automatically.
Ransomware Summary
| Name | XHAMSTER Ransomware Virus |
| Type | Ransomware; Crypto-malware; Virtual Extortion Virus |
| Family | PHOBOS |
| Encryption type | AES-256 |
| Extension | .id[victim’s ID].[ICQ@xhamster2020].XHAMSTER |
| Cybercriminal contact | ICQ username @xhamster2020 |
| Damage | The ransomware encrypts all files on the compromised computer and appends extensions to them that consist of victim’s ID, cybercriminals’ ICQ account name, and .XHAMSTER marker. The virus drops ransom notes called info.txt and also displays a HTML version of it on the screen. The ransomware deletes Volume Shadow Copies from the system to prevent easy data recovery for the victim. |
| Ransom note | info.txt, info.hta |
| Ransom demand | Depends on how quickly the victim writes to the attackers |
| Distribution | This ransomware is distributed via malicious email attachments or dropped by the criminals directly into systems with vulnerable RDP configurations |
| Detection names | Ransom:Win32/Phobos.PC!MTB (Microsoft), Gen:Variant.Ransom.Phobos.62 (B) (Emsisoft), HEUR:Trojan.Win32.Generic (Kaspersky), Gen:Variant.Ransom.Phobos.62 (BitDefender), Ransom.Phobos (Malwarebytes), Downloader (Symantec) see all detection name variations on VirusTotal |
| Removal | Remove ransomware and related malware from your PC using professional software of your choice. We highly recommend using INTEGO Antivirus. To repair virus damage on Windows OS files, consider scanning with RESTORO. |
REPAIR VIRUS DAMAGE
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
Screenshot of files encrypted by XHAMSTER ransomware virus:
Screenshot of info.txt ransom note contents:
This is how info.hta ransom note appears.
Ransomware distribution: avoid getting infected
Phobos ransomware variants including XHAMSTER virus and others usually reach target systems via malicious email attachments or after the attackers breaks into the network using weak Remote Desktop Protocol (RDP) credentials. The criminals can get access into systems via RDP by using leaked credentials purchased in dark web forums, using brute-force tools or by exploiting vulnerable and weak RDP connections. After gaining access to the network, the attackers move laterally and plant the ransomware payload manually.
Cybersecurity experts recommend following such security measures when it comes to RDP – placing RDP behind VPN, using multi-factor authentication, limiting login attempts and using allowed IPs list.
Another distribution technique associated with this and many other ransomware families involves phishing methods. The attackers may target victims to reveal RDP credentials by sending deceptive emails, or they may deliver the actual ransomware in a rogue email attachment. Computer users should be very careful when opening email attachments, especially if they come unexpected. The cybercriminals create convincing email messages that urge to open attached contents and reply to the sender as soon as possible. However, even if the email attachment comes in a Word, PDF or Excel format, it can carry malicious code used to download and run the ransomware on the computer and connected drives.
For this reason, we advise to look for red flags such as unfamiliar greeting line, typo mistakes, suspicious-looking logos, spoofed email address signs and urgent message tone. If you have the slightest suspicion that the email sender might have malevolent intentions, do not interact with attached files or inserted URLs.
Finally, we’d like to warn computer users to stay away from illegal online downloads, such as pirated software versions offered by various rogue websites online. Cybercriminals prey for victims by offering a bait – free premium software versions that can be downloaded either as password-secured archives or torrents. These can hide ransomware and other computer threats in them. It is one of the most popular malware distribution techniques nowadays as well.
Remove XHAMSTER Ransomware Virus and Decrypt Your Files
If your computer was compromised by this notorious PHOBOS variant, we recommend you to follow the steps provided below to secure your computer and eliminate all traits of malware from it. To remove XHAMSTER ransomware virus, boot your PC in Safe Mode with Networking as explained below. Then update your antivirus software and run a full system scan. If you haven’t decided on which antivirus to use, consider trying one of the best ones available nowadays – INTEGO Antivirus. It demonstrates excellent malware detection rates in AV lab tests and provides 24/7 computer protection.
Additionally, you may want to download this program – RESTORO which is designed to repair virus damage on Windows OS files without the need to reinstall the operating system.
Additional measures we recommend taking after XHAMSTER ransomware removal is reporting the cybercrime incident to local law enforcement agency and changing all passwords used on the compromised computer. If you had data backup, you can use it to recover your files, however, we’d like to remind you that you should never connect the data storage device to your computer BEFORE removing the malware.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
XHAMSTER Ransomware Virus Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove XHAMSTER Ransomware Virus files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO Antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Recent Posts
MrBeast Giveaway Scam: How to identify it?
Scammers impersonate Mr. Beast and try to lure people with fake giveaways Mr. Beast has…
Remove TCVP Ransomware Virus (DECRYPT .tcvp FILES)
TCVP ransomware encrypts files stored on a computer TCVP ransomware is a new computer virus…
Remove TCBU Ransomware Virus (DECRYPT .tcbu FILES)
TCBU ransomware seeks to lock you out of access to your files TCBU ransomware is…
Remove FATE Ransomware Virus (DECRYPT .fate FILES)
FATE ransomware is a menace to files stored on your computer FATE ransomware is a…
Remove FATP Ransomware Virus (DECRYPT .fatp FILES)
FATP ransomware aims to encrypt files on your computer, demand ransom FATP ransomware is a…
Voicemail Email Scam Explained: Removal and Recovery Guide
Voicemail Email Scam promotes phishing websites and steals user data Voicemail Email Scam is a…