NAKW ransomware hits hundreds of victims, encrypts personal data
Contents
NAKW ransomware is a malicious file-encrypting computer virus that originates from STOP (DJVU) ransomware family. The virus is created with the intention to corrupt all files on the target system using the RSA encryption method, add .nakw extensions to filenames and leave a ransom-demanding note called _readme.txt. In this note, the attackers explain that the victim has to contact them via provided emails and pay a specified sum of money to decrypt files. In other words, the cybercriminals demand a ransom.
The ransom note suggests contacting salesrestoresoftware@firemail.cc or salesrestoresoftware@gmail.com to get instructions regarding .nakw file decryption software. To prove that such a tool exists, the ransomware developers suggest decrypting one file for free. However, to recover all files, the ransomware virus demands paying a hefty price. The attackers suggest a 50% discount if the ransom is paid within 72 hours – $490. Otherwise, the price is $980.

No ways to decrypt files – at least for now
Speaking of data recovery, you must first acknowledge the encryption routine this virus uses. Once installed on the target machine, it attempts to establish a connection with its server to obtain an online key. Otherwise, if it can’t establish this connection, it encrypts files using an offline key. In addition, the virus might use both online and offline keys. A typical indicator that files were locked with the offline key is a personal ID ending in t1.
NAKW ransomware virus is a new variant of DJVU (STOP). This ransomware family started producing new versions that use an upgraded encryption algorithm since August 2019. These versions include RECO, NOLS, COOT, DERP, and others.
Unfortunately, if you were attacked and your files were encrypted with online key, there are no chances to recover your files. If encrypted with an offline key, you might have a chance to recover some of them in the future. Security researchers need to extract the offline key first. Therefore, please be patient – such things do not happen quickly.
Please keep checking for updates in this tutorial on how to decrypt files locked by STOP ransomware.
Another thing you should be aware of is that NAKW ransomware can install an information-stealing Trojan named Azorult. This malicious virus is designed to steal passwords saved in your browsers. Therefore, you need to take action to delete it along with the ransomware virus remains.
To remove NAKW ransomware virus successfully, consider using the guidelines given below this post. To automatically clean your computer system, use powerful antivirus software.
Ransomware Summary
| Name | NAKW virus |
| Type | Ransomware |
| Malware Family | STOP ransomware (DJVU) |
| Encryption Method | RSA |
| File Extension | .nakw |
| Ransom Note | _readme.txt |
| Ransom Amount | $490-$980 |
| Contact Emails (Cyber criminals) | salesrestoresoftware@firemail.cc; reserve email: salesrestoresoftware@gmail.com |
| Decryption available? | Impossible. If encrypted with offline key, might be decryptable in the future |
| Removal | Remove using antivirus of your choice in Safe Mode (see instructions below) |
Distribution means and ways to protect yourself
Victims of STOP ransomware all are attacked due to insecure practices when it comes to software installation. It is a well-known fact that this ransomware is bundled with illegal software activation tools such as software cracks, keygens, KMSPico viruses and so on. Therefore, if your files are encrypted and have .nakw extensions now, it means that you have attempted to install paid software illegally, or, in other words, without paying for its license.
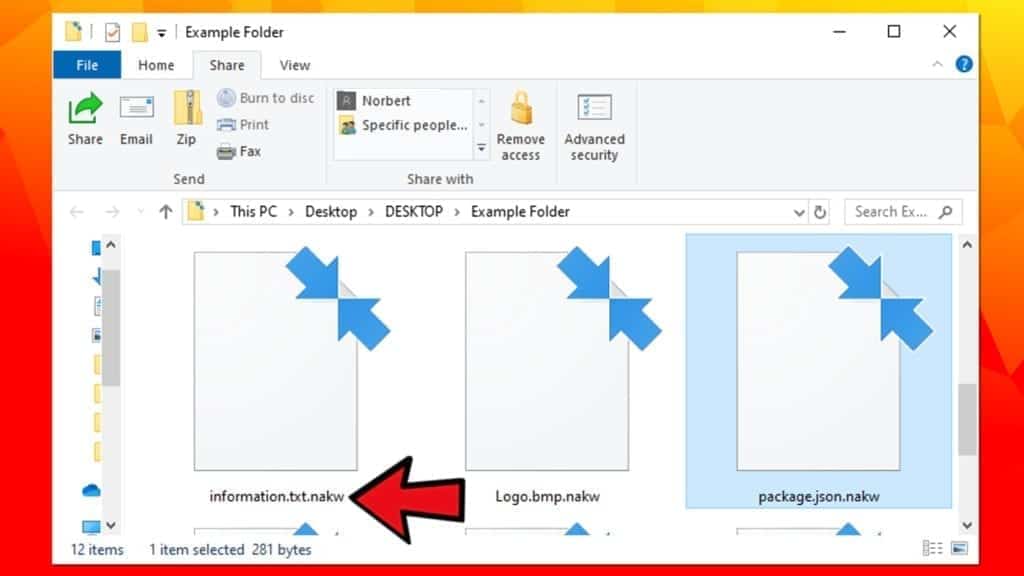
Please remember that such illegal activators are used as bait by cybercriminals. They can modify programs to make them launch different files and run executives that bear a malicious payload (in other words, ransomware). What is more, software licenses cost way less than ransoms. Besides, we believe that your data was extremely important to you, so please do not take such decisions in the future. As you can see, the results are nerve-wracking, to say at least.
You can learn more about ransomware distribution tricks used by cyber attackers in this prevention guide.
Ways to remove NAKW ransomware virus
A safe way to clean up your computer system and remove NAKW ransomware along with Azorult is to boot your computer in Safe mode and run an antivirus software then. Additionally, we recommend refreshing the antivirus database first and installing suggested updates for it. This ensures that your antivirus will have a definition of this specific ransomware variant and will be able to eliminate it safely.
You can find instructions regarding NAKW virus removal down below. Please note that you can also remove malware from your system by reinstalling Windows, which is not a recommended option as you can lose all of your data immediately.
Once you complete the given steps, change all your passwords to prevent hackers from stealing more sensitive data or potentially emptying your bank account. Finally, we recommend you to backup .nakw extension files in case there’s an update to the STOP decrypter tool in the future.
OUR GEEKS RECOMMEND
Our team recommends a two-step rescue plan to remove ransomware and other remaining malware from your computer, plus repair caused virus damage to the system:
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
NAKW Ransomware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
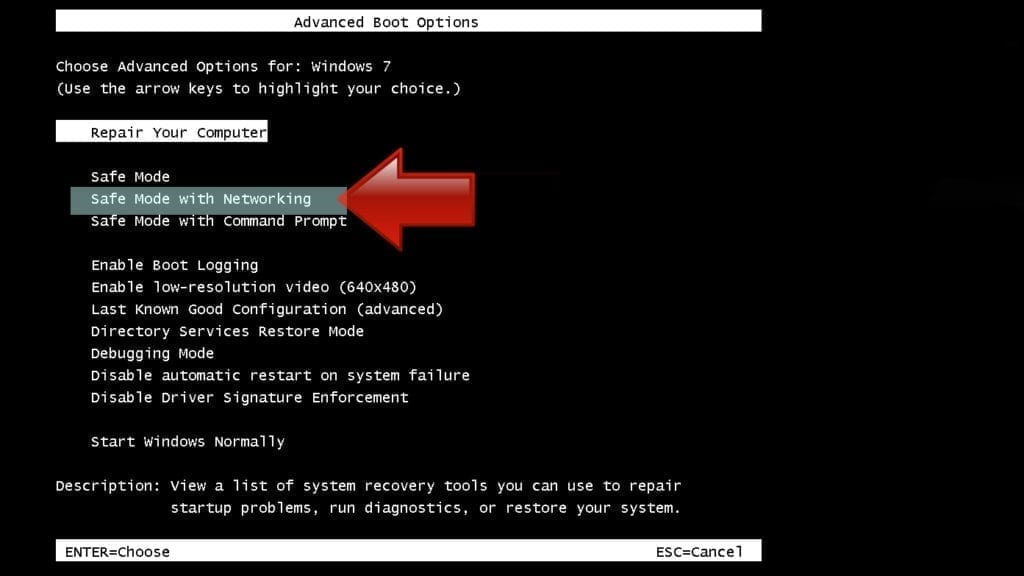
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
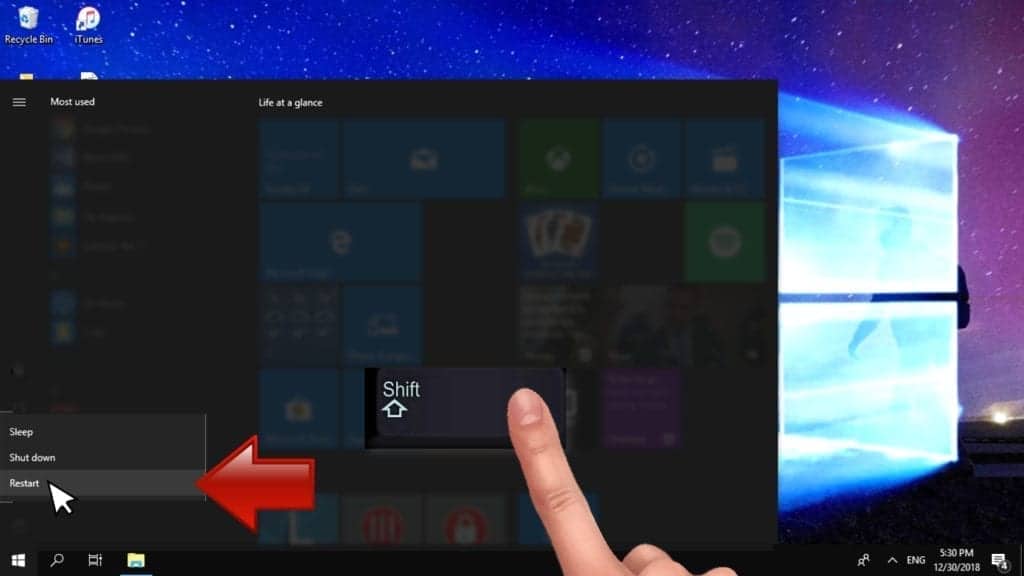
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
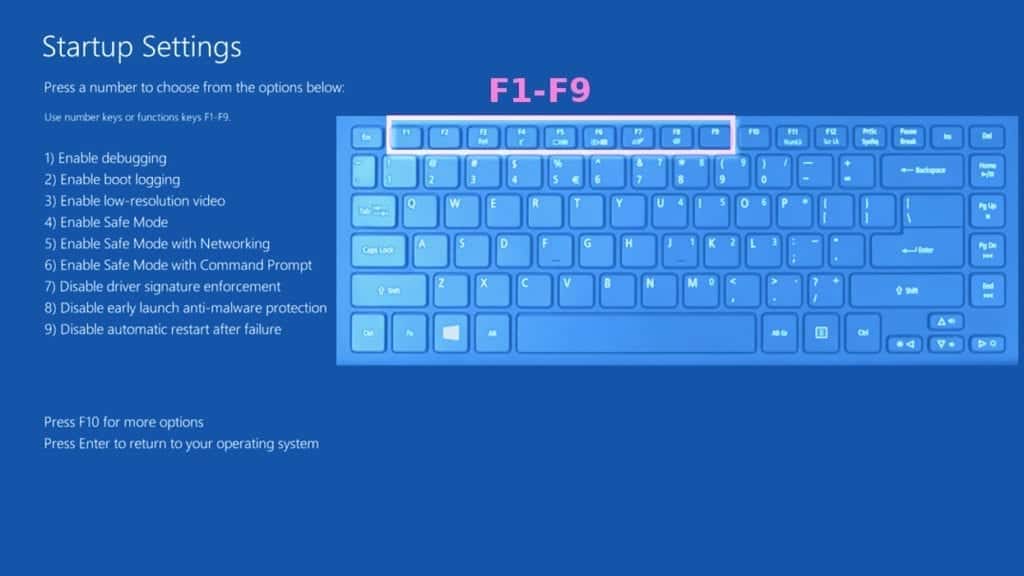
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
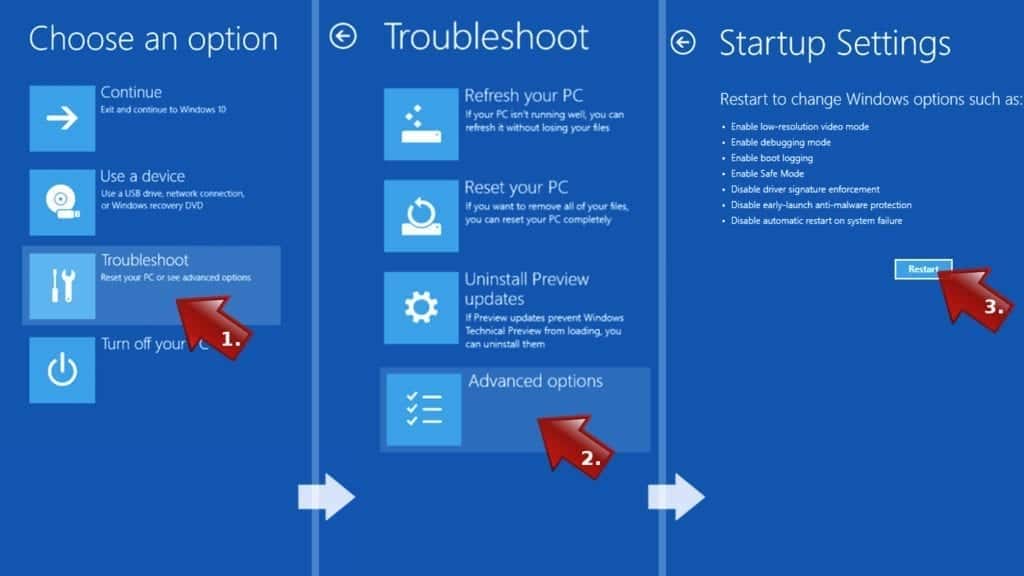
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove NAKW Ransomware files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying a combination of INTEGO Antivirus (removes malware and protects your PC in real-time) and RESTORO (repairs virus damage to Windows OS files).
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
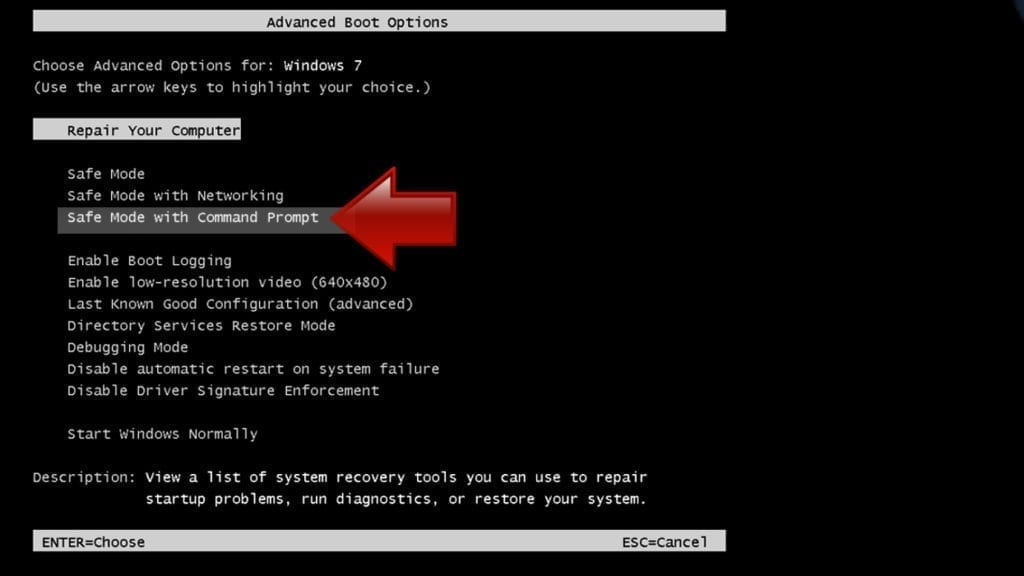
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
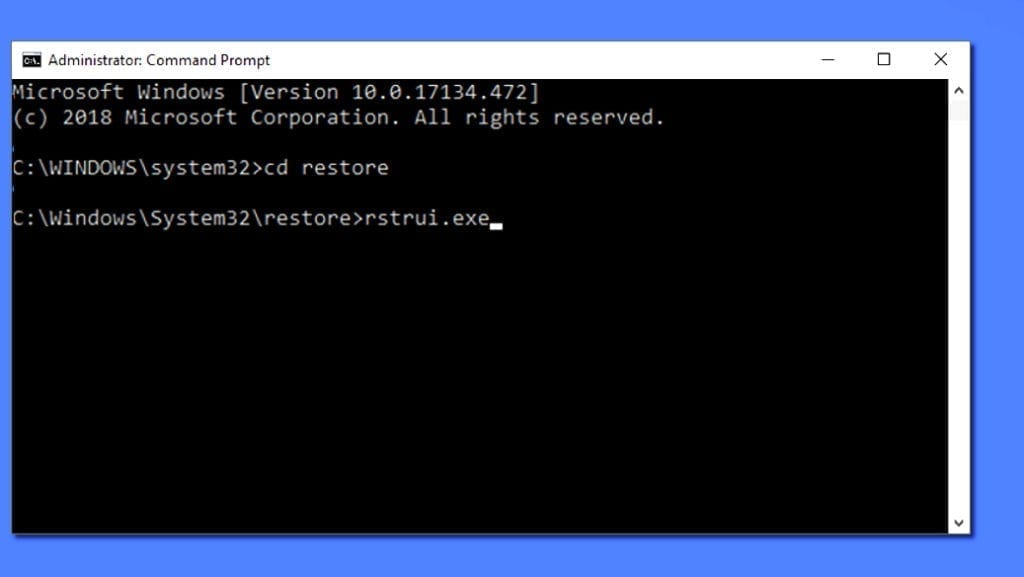
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
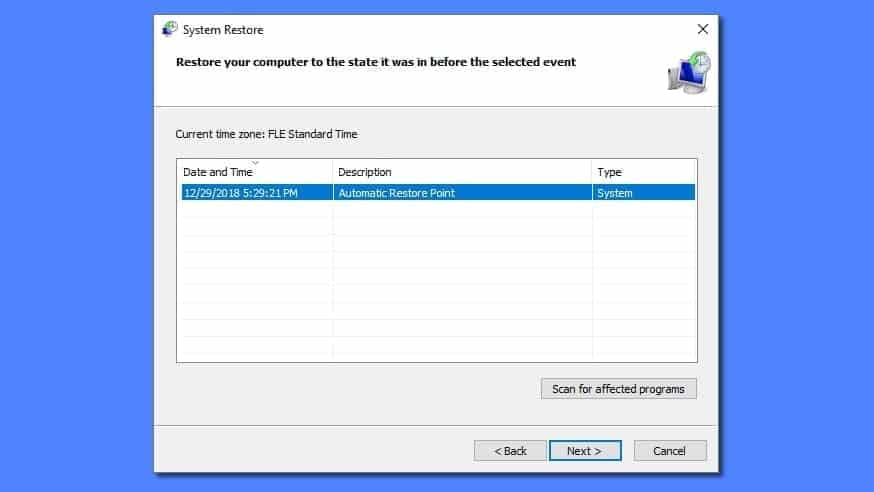
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.


please notify me if decrypter for nakw extention is available