COOL ransomware encrypts personal files on a computer and marks them with new extensions
Contents
- COOL ransomware encrypts personal files on a computer and marks them with new extensions
- Avoid ransomware infections: learn how these viruses are distributed
- More about the ransomware activity on your computer
- Remove COOL ransomware virus and Recover Your Files
- Decrypt COOL files
- Frequently Asked Questions
COOL ransomware is a malicious computer virus originating from STOP/DJVU ransomware virus family. This virus aims to encrypt all files on the target computer and while doing it also appends .cool extension to their filenames. To illustrate, a file originally named 1.jpg becomes 1.jpg.cool after being infected. To inform the computer owner about the ransomware operators’ intentions, the virus drops _readme.txt note in all affected folders. The note suggests that the only way to get COOL file decryption tool is to pay a large ransom to cybercriminals.
The ransom note dropped by COOL ransomware suggests that the victim can still return all files. It also explains that all data including pictures, videos, databases, documents and other file formats have been encrypted with the strongest encryption algorithm and unique key. Although not mentioned in the note, the virus uses Salsa20 + RSA-2048 bit encryption type. The note instructs the victim to contact the criminals via provided email addresses: manager@mailtemp.ch and supporthelp@airmail.cc.
The note suggests that the victim should rush to contact the criminals within 72 hours to get a 50% discount on the decryption service price. If the victim does it, the criminals are willing to set the price to $490. If delayed any longer, the ransom price would be $980 instead. The note also says that the victim can attach one encrypted file that doesn’t contain no valuable information to test the decryption – the attackers promise to send a decrypted test file in return.

After writing an email to the criminals, the victim gets instructions to purchase cryptocurrency such as Bitcoin worth the ransom amount and how to transfer it to the attackers. The crooks usually provide several links to websites that can be used to purchase virtual currency. The reason why such Internet criminals want to receive the ransom in this way is because it helps them to stay anonymous and thus law enforcement agencies have no power to track the parties between such transactions.
Geek’s Advice experts suggest following FBI recommendations about paying up to cybercriminals – DO NOT PAY THE RANSOM. First of all, paying a ransom does not guarantee successful file decryption. Another reason why it is wrongful to do so is because money is the fuel behind these illegal operations as it allows the attackers to employ more malware developers or distributors and therefore infect even more victims worldwide with more sophisticated threats. Criminals behind file-encrypting malware earn millions annually already, which is another factor that lures other people to become affiliates in this fraudulent business.
Another reason why you shouldn’t pay these people is because the ransomware you were infected with has a tendency to drop additional information-stealing Trojans such as AZORULT or VIDAR on infected system. These viruses are capable of allowing criminals to run commands on your computer remotely to steal private details such as browser-saved account passwords as well as login credentials for various applications (Steam, Telegram and others), Skype chat history, cryptocurrency wallets and more. Therefore, even if you pay, the attackers can continue to blackmail you and ask for more money or log into your accounts and cause further damage.
Victims infected with this ransomware variant are advised to scan their computers with robust and up-to-date antivirus software immediately. This should be done while in Safe Mode with Networking as explained in the removal guide below. If you do not have an antivirus software yet, our team strongly recommends using INTEGO Antivirus to remove COOL ransomware virus and related malware. On top of that, you may want to download RESTORO to scan for virus damage on Windows OS files and repair it.
Ransomware Summary
| Name | COOL Ransomware Virus |
| Type | Ransomware; Crypto-malware; Virtual Extortion Virus |
| Family | STOP/DJVU |
| Encryption type | RSA 2048 + Salsa20 |
| Previous versions | KAAA, KIFR, KIOP, KITZ, BOZA, BOTY, COZA (find full list here) |
| Version | 343rd |
| Extension | .cool |
| Cybercriminal emails | manager@mailtemp.ch, supporthelp@airmail.cc |
| Additional malware dropped | Azorult or Vidar Trojan |
| Damage | The ransomware infects the system disguised as a malicious torrent download. It then begins encrypting all data on the hacked computer and appends encrypted files with .cool extension. The virus leaves ransom notes (_readme.txt) behind as it scans through every system directory. It also deletes Volume Shadow Copies so that the user could not use System Restore Points. Additionally, it may add a list of domain names to Windows HOSTS file to prevent victim’s access to them. The ransomware has a tendency to infect the computer with AZORULT Trojan or VIDAR. |
| Ransom note | _readme.txt |
| Ransom demand | $490-$980 in Bitcoin |
| Distribution | Victims often download this ransomware along illegal torrent downloads, cracked software, activators, key generators or tools like KMSPico. |
| Known software cracks to contain this malware | Corel Draw, Tenorshare 4ukey, Adobe Photoshop, Cubase, Adobe Illustrator, Internet Download Manager, Tally, League of Legends. |
| Detection names | Trojan:Win32/Krypter.AA!MTB (Microsoft), Gen:Variant.Fragtor.36858 (B) (Emsisoft), UDS:Trojan.Win32.Scarsi.gen (Kaspersky), Gen:Variant.Fragtor.36858 (BitDefender), MachineLearning/Anomalous.95% (Malwarebytes), Packed.Generic.528 (Symantec) see all detection name variations on VirusTotal |
| Removal | Remove ransomware and related malware from your PC using professional software of your choice. We highly recommend using INTEGO Antivirus. To repair virus damage on Windows OS files, consider scanning with RESTORO. |
REPAIR VIRUS DAMAGE
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
Avoid ransomware infections: learn how these viruses are distributed
It is well-known fact that STOP/DJVU virus versions such as COOL extension virus are distributed via malicious torrents downloads, mostly ones that are supposed to activate paid software versions illegally. Some examples of torrents that can land you this virus on your computer are software cracks, keygens and other tools like KMSPico. Victims of this ransomware strain report getting infected after downloading pirated torrents for these popular programs:
- Adobe Photoshop;
- Fifa 20;
- Tenorshare 4ukey;
- AutoCad;
- Corel Draw;
- Opera browser;
- VMware Workstation;
- Cubase;
- League of Legends;
- Adobe Illustrator;
- Internet Download Manager.
You should avoid heading to various online torrent listings for obtaining programs. Instead, you should visit official developer’s or verified partner’s website for a legitimate copy of the software or game that you’re interested in. Trying to get these things for free can only lead to a severe computer infection and immediate data loss. Besides, doing so is an infringement of legitimate software developers’ copyrights.
Ransomware-type viruses are often distributed via malicious email spam (also known as malspam). The malware gets hidden in files attached to such emails and they can come in popular file formats such as DOCX, PDF, XLS and others. The criminals complement these documents with JavaScript or Macros that, once run, can download the payload from a remote source and launch it on your computer.
Nowadays, advanced cybercriminals rarely make obvious mistakes when sending malicious spam – they hardly ever leave grammar errors or weirdly placed company logos in their emails. They can even spoof the sender’s email address to make it appear like it was sent by an official and well-known sender. Moreover, they might pretend to be your colleague, boss or a company providing services that people user regularly – for instance, eBay, Amazon, DHL, UPS or others. They name the attachments as invoices, order summaries, parcel tracking details and similar, so it can be really hard to identify the malevolent intentions behind them. Our general advice is to avoid opening something that you did not expect to receive, or your curiosity will lead to computer infection. Another tip is to look for unfamiliar greeting line in the email.
Another important ransomware distribution technique is based on fake STOP/DJVU decryption tools. Criminals know that there are hundreds of computer users desperately looking for a solution to decrypt .cool files, so they might upload fake decryption tools promising they can restore your files. In reality, STOP/DJVU ransomware-encrypted files can be restored only in certain conditions explained here. If you try to search for tools that simply do not exist, you might end up infecting your computer again and your files might get double-encrypted. One of ransomware strains that’s been distributed as a fake decryptor is called ZORAB.
More about the ransomware activity on your computer
This section contains more technical details about the ransomware if you are interested in more coverage of what actually happened during the cyberattack. After being executed on the target system, COOL ransomware virus begins as a set of processes called build.exe, build2.exe or build3.exe. Each of these processes have a different set of functions. Before starting the actual data encryption procedure, the virus performs a couple of checks and collects as many details about the target computer as possible.
First of all, the virus checks whether the computer it managed to compromise is eligible for encryption. It has a set of exception countries that it is designed not to attack. Therefore, it connects to https[:]//api.2ip.ua/geo.json domain and the response of it is saved into geo.json file. This file contains information about computer’s country code, zip code, longitude, latitude and time zone. The virus then compares the country code received to its exceptions list and if founds a match, it then terminates itself without encrypting victim’s files. You can see an examples of geo.json files below.

The ransomware tends to avoid encrypting files on computers from these countries: Russian Federation, Armenia, Tajikistan, Ukraine, Kazachstan, Kyrgyzstan, Syria, Uzbekistan and Belarus. Otherwise, it continues the attack and prepares for the data encryption stage.
In the next phase, the ransomware attempts to connect to its Command&Control server and get an unique online encryption key for the victim as well as identification string. The response is then saved to bowsakkdestx.txt file and personal ID is saved to PersonalID.txt file as well. If the attempt to obtain online key fails, the virus uses offline encryption key instead. Victims affected by offline encryption type will have personal IDs ending in t1 characters. Users affected by this key have a chance to decrypt .cool files in the future, which cannot be said about online key encryption victims.

The ransomware also collects information about computer’s hardware and software as well as details like user name, operating system and other data and saves it to information.txt file and sends it to criminals C&C server as well.

Finally, the virus begins encrypting victim’s files stored on the compromised computer. The ransomware uses Salsa20 encryption to secure information and then strengthens it by using RSA-2048 key on it. Each of encrypted files will be assigned an additional extension to make it distinguishable.

A screenshot of _readme.txt note which is left in every folder containing affected files is shown below.

To finalise the attack, the malware gets rid of Volume Shadow Copies from the computer by running the following Command Line task:
vssadmin.exe Delete Shadows /All /Quiet
Additionally, some variations of STOP/DJVU viruses tend to add a list of domain names to block on the target host. The ransomware uploads this list to Windows HOSTS file and maps each of them to localhost IP, thus causing DNS_PROBE_FINISHED_NXDOMAIN error to pop-up whenever the victim tries to access one of these. Moreover, some variants we’ve seen infect the already compromised computer with Trojans like AZORULT or VIDAR.
Remove COOL ransomware virus and Recover Your Files
In case you’ve become a victim of ransomware attack, you should contact your local law enforcement agency and let them know about what happened. Next, it is essential to remove COOL ransomware virus as soon as possible, especially when it or related malware can continue dangerous operations on your PC. We have prepared an easy removal guide which explains how to boot your computer in Safe Mode with Networking from which you should run your chosen antivirus software. Before doing so, ensure that you have one on your computer. If you do not have it, consider using INTEGO Antivirus which is highly recommended by our team. It provides real-time protection and network traffic protection, besides, scores excellent malware detection rates in independent AV lab tests.
After removing malware from your computer, you may want to download RESTORO to repair virus-damaged Windows OS files.
If you’ve already taken care of COOL ransomware virus removal, please read these suggestions from our team:
- Use data backup to restore lost files. Before using it, you must remove all malware from the Windows system first.
- Read about ways you can decrypt or repair files affected by STOP/DJVU versions.
- Change your passwords for as many accounts as you used on your computer, including browser saved ones, also Steam, Telegram and other apps.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software.
REMOVE THREATS WITH ROBUST ANTIVIRUS

Get INTEGO ANTIVIRUS for Windows to remove ransomware, Trojans, adware and other spyware and malware variants and protect your PC and network drives 24/7. This VB100-certified security software uses state-of-art technology to provide protection against ransomware, Zero-Day attacks and advanced threats, Intego Web Shield blocks dangerous websites, phishing attacks, malicious downloads and installation of potentially unwanted programs.
Use INTEGO Antivirus to remove detected threats from your computer.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
COOL Ransomware Virus Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove COOL Ransomware Virus virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, if you prefer a video version of the tutorial, check our guide How to Start Windows in Safe Mode on Youtube.
Instructions for Windows XP/Vista/7 users
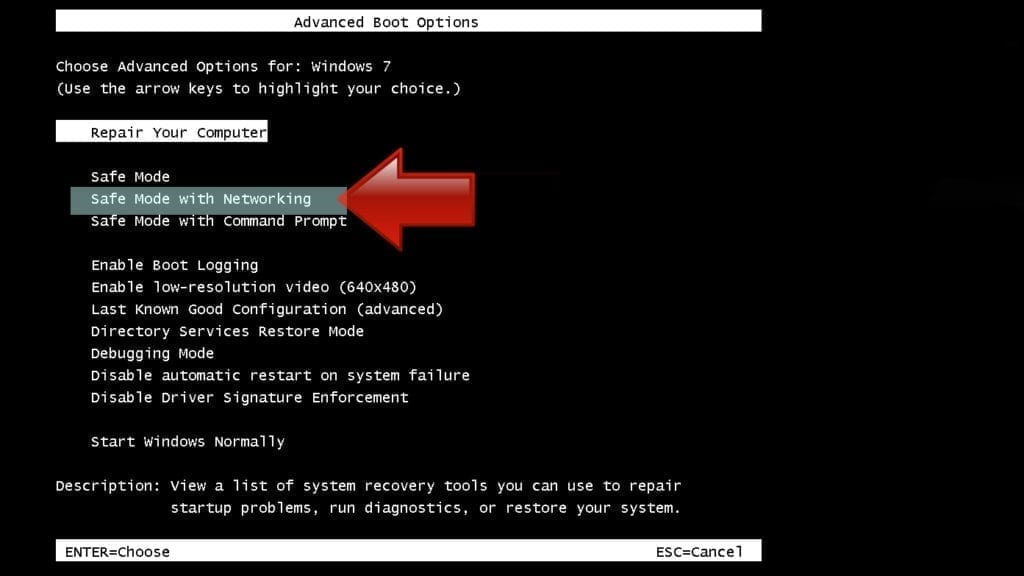
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
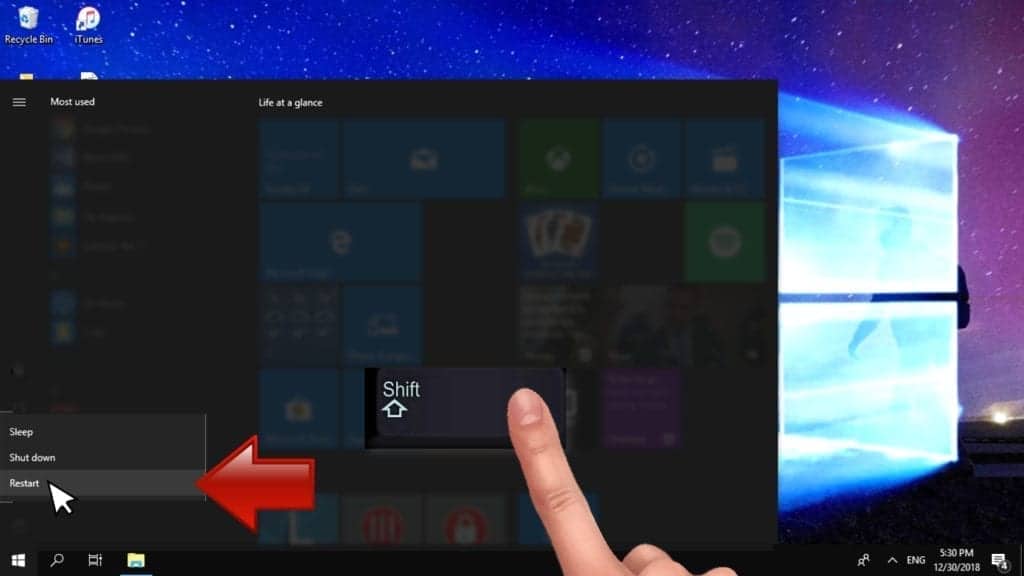
Instructions for Windows 8/8.1/10/11 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
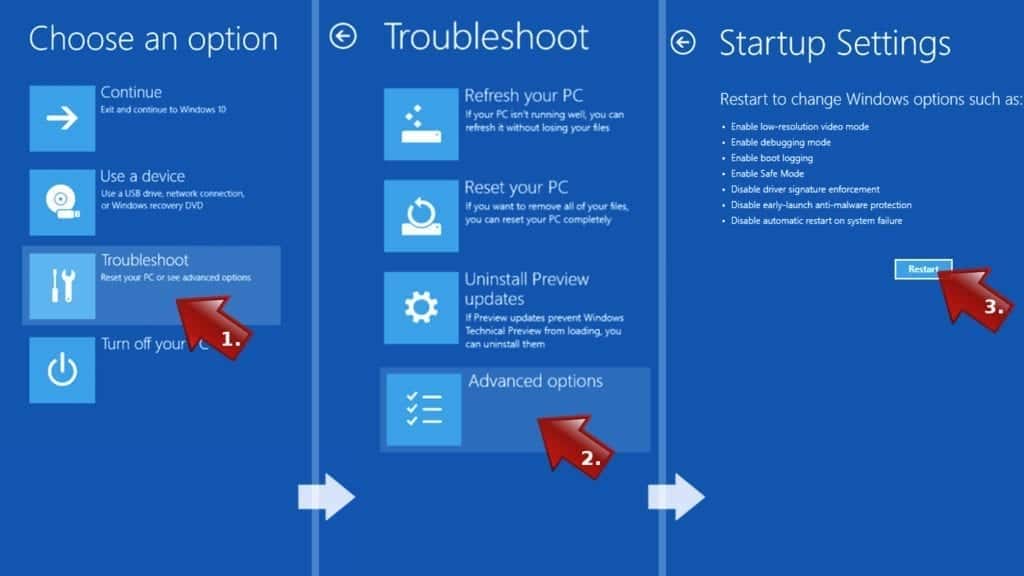
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
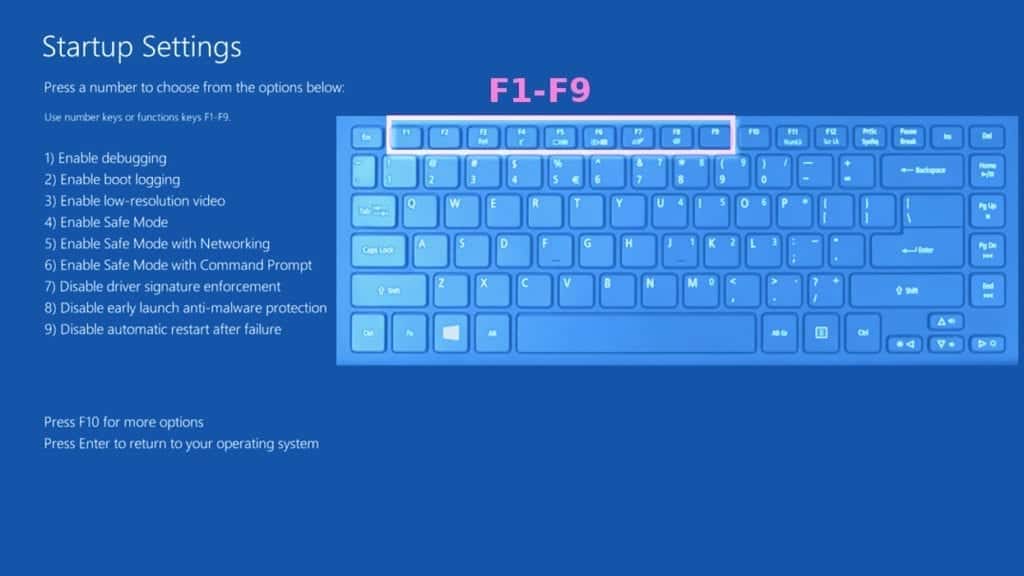
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove COOL Ransomware Virus files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable security program such as INTEGO Antivirus. For virus damage repair, consider using RESTORO.
Special Offer
Compatibility: Microsoft Windows
See Full Review
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
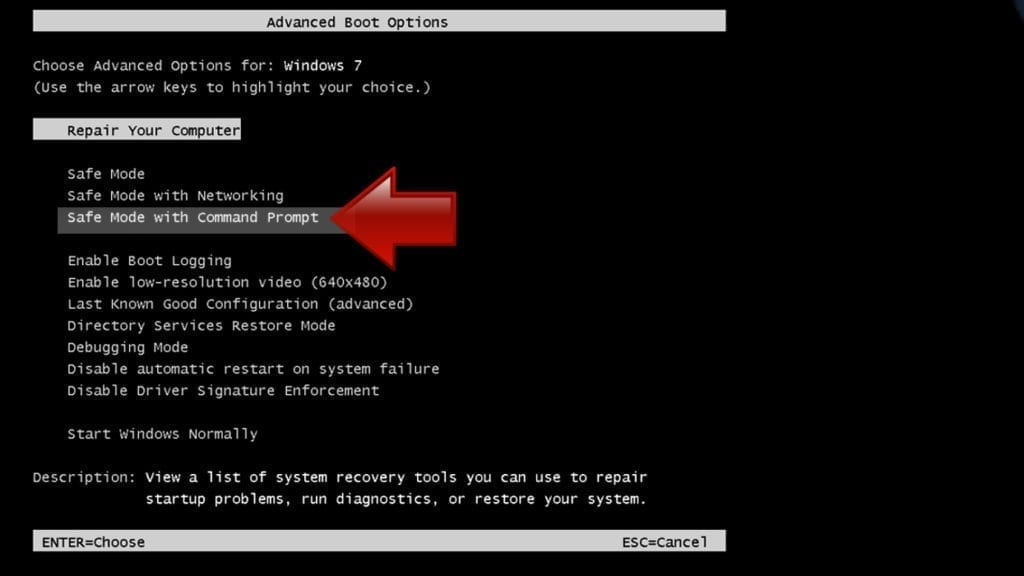
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10/11 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
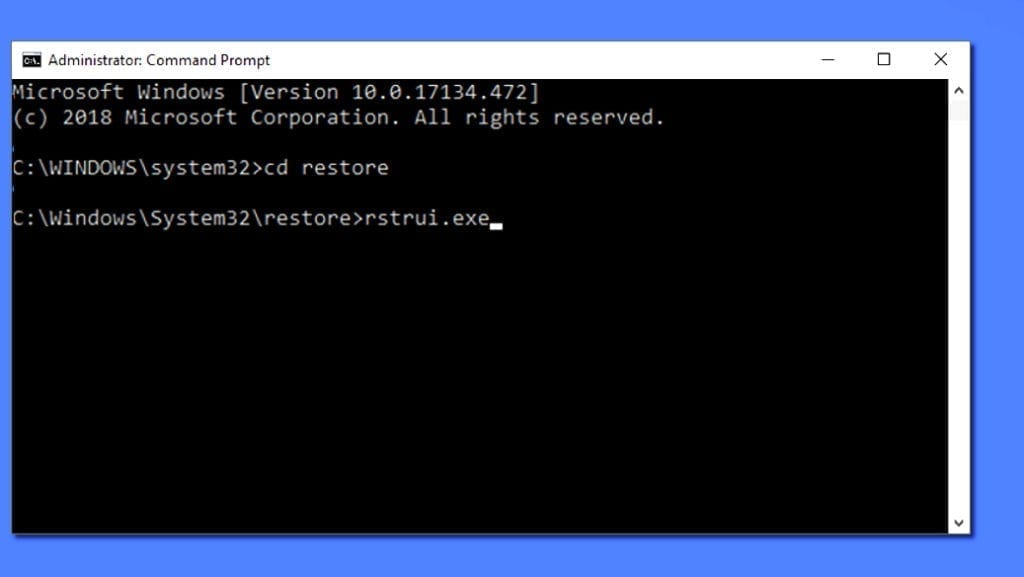
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
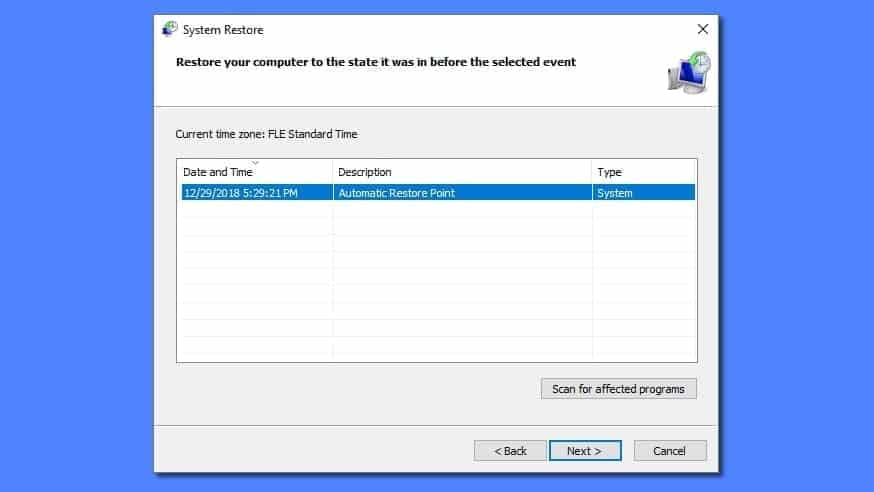
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Decrypt COOL files
Fix and open large COOL files easily:
It is reported that STOP/DJVU ransomware versions encrypt only the beginning 150 KB of each file to ensure that the virus manages to affect all files on the system. In some cases, the malicious program might skip some files at all. That said, we recommend testing this method on several big (>1GB) files first.
- Create a copy of encrypted file to a separate folder using Copy > Paste commands.
- Now, right-click the created copy and choose Rename. Select the COOL extension and delete it. Press Enter to save changes.
- In the prompt asking whether you want to make the changes as file might become unusable, click OK.
- Try opening the file.
STOP/DJVU decryption tool usage guide
STOP/DJVU ransomware versions are grouped into old and new variants. COOL Ransomware Virus is considered the new STOP/DJVU variant, just like KAAA, KIFR, KIOP, KITZ, BOZA, BOTY, COZA (find full list here). This means full data decryption is now possible only if you have been affected by offline encryption key. To decrypt your files, you will have to download Emsisoft Decryptor for STOP DJVU, a tool created and maintained by a genius security researcher Michael Gillespie.
Note! Please do not spam the security researcher with questions whether he can recover your files encrypted with online key - it is not possible.
In order to test the tool and see if it can decrypt COOL files, follow the given tutorial.
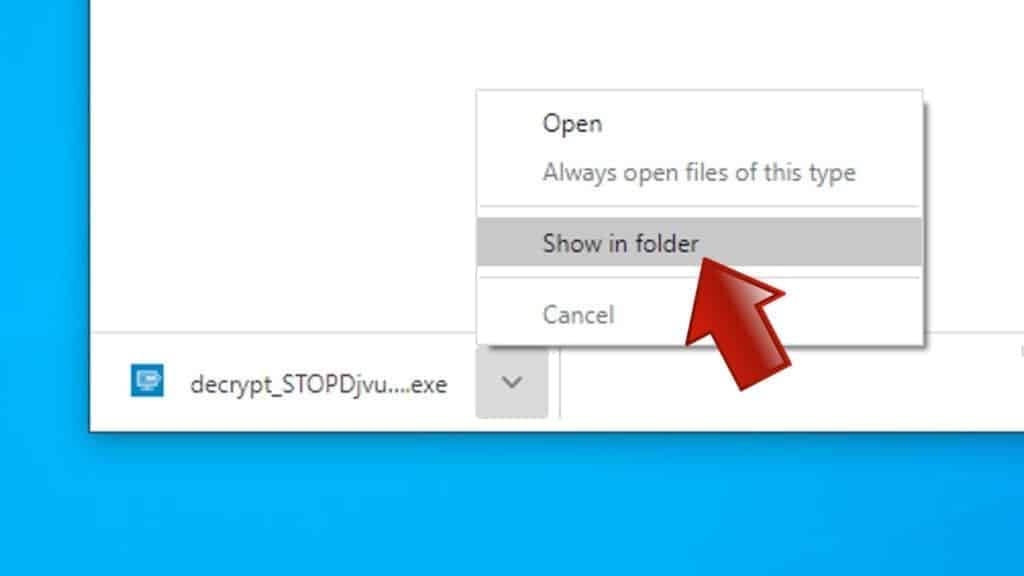
- Download the decryption tool from Emsisoft.
- Click the little arrow next to your download and choose Show in Folder.
- Now, right-click the file and choose Run as Administrator. If asked, enter administrator's password.
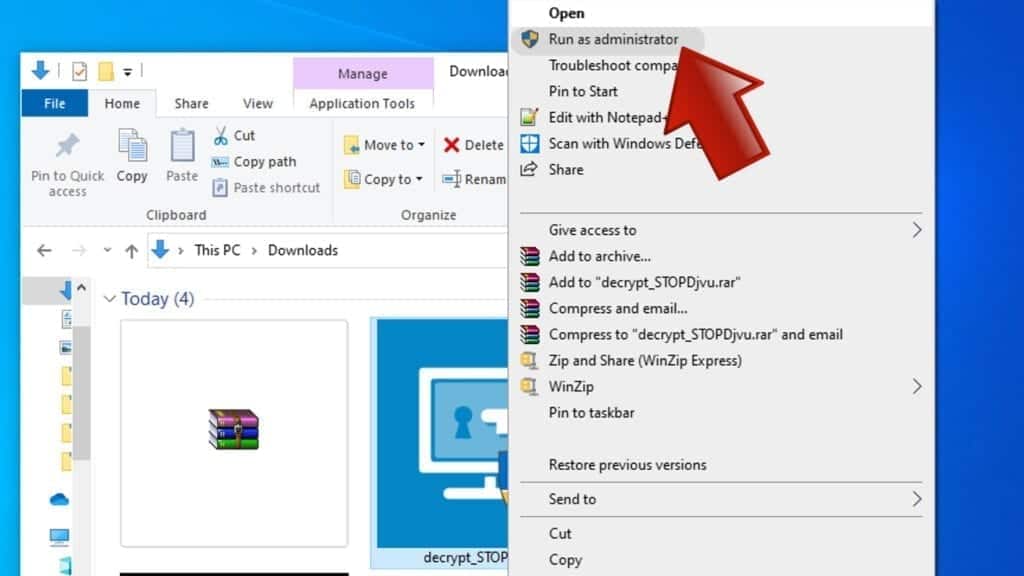
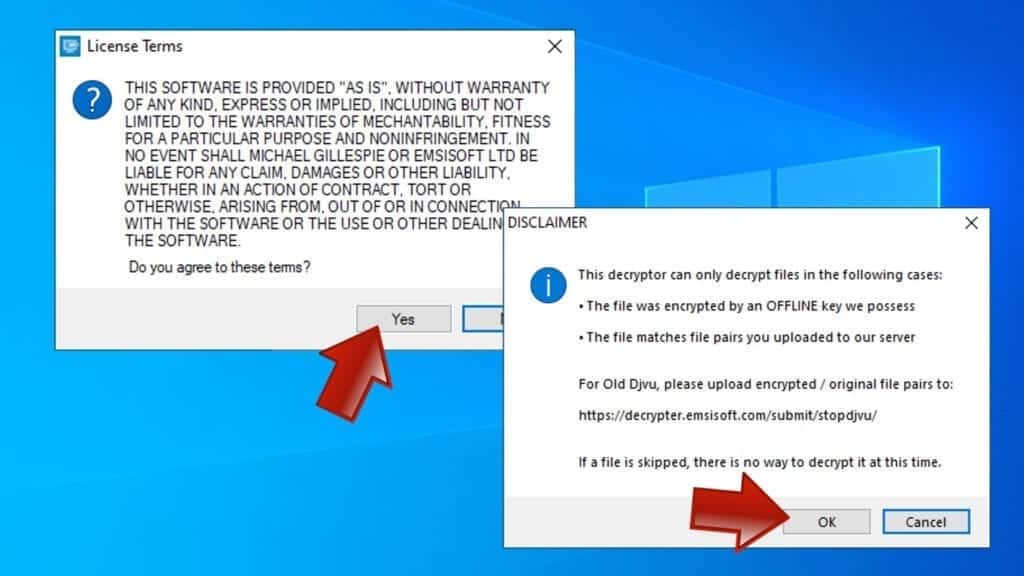
- In UAC window, click Yes.
- Click Yes to agree to software terms in both windows.
- The tool will automatically include C:// disk as a location to decrypt. The file recovery tool will prepopulate the locations to scan, including connected data storage drives or network drives. Click Add folder if you wish to add additional locations.
In Options tab, you can choose to keep encrypted file copies. We recommend leaving this option selected, especially if you do not know if the decryption tool will work.
- Click Decrypt to start restoring COOL files. You will see the progress in the Results tab. Here, you can see messages from the tool, such as whether the decryption procedure is successful, or you need to wait for an update.
You might also be informed that online key was used to encrypt your files. In such case, the decryption tool won't work for you, and the only way to recover your files is to use a data backup.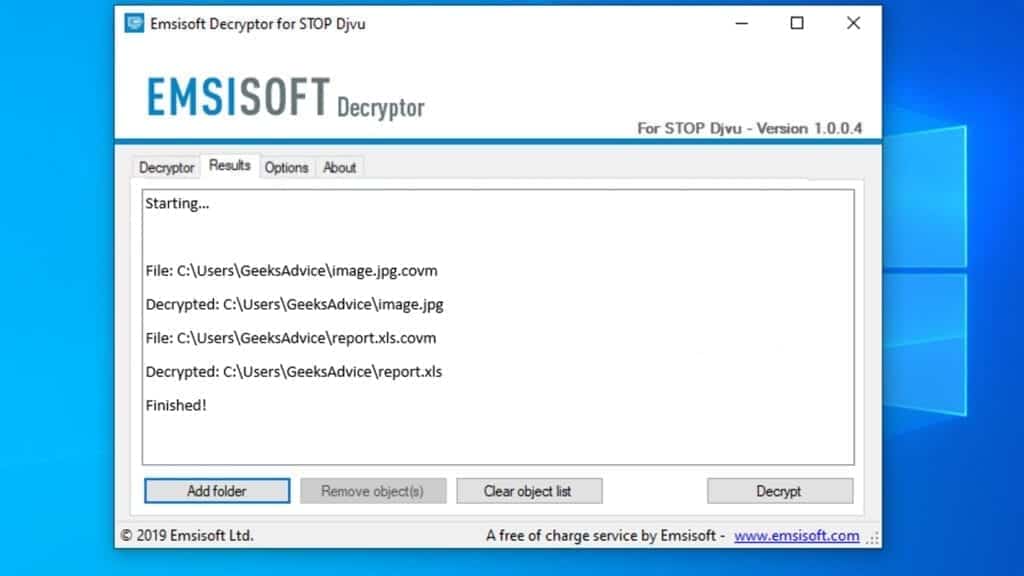
Meanings of decryptor's messages
The COOL decryption tool might display several different messages after failed attempt to restore your files. You might receive one of the following messages:
Error: Unable to decrypt file with ID: [example ID]
This message typically means that there is no corresponding decryption key in the decryptor's database.
No key for New Variant online ID: [example ID]
Notice: this ID appears to be an online ID, decryption is impossible
This message informs that your files were encrypted with online key, meaning no one else has the same encryption/decryption key pair, therefore data recovery without paying the criminals is impossible.
Result: No key for new variant offline ID: [example ID]
This ID appears to be an offline ID. Decryption may be possible in the future.
If you were informed that an offline key was used, but files could not be restored, it means that the offline decryption key isn't available yet. However, receiving this message is extremely good news, meaning that it might be possible to restore your COOL extension files in the future. It can take a few months until the decryption key gets found and uploaded to the decryptor. We recommend you to follow updates regarding the decryptable DJVU versions here. We strongly recommend backing up your encrypted data and waiting.
Report Internet crime to legal departments
Victims of COOL Ransomware Virus should report the Internet crime incident to the official government fraud and scam website according to their country:
- In the United States, go to the On Guard Online website.
- In Australia, go to the SCAMwatch website.
- In Germany, go to the Bundesamt für Sicherheit in der Informationstechnik website.
- In Ireland, go to the An Garda Síochána website.
- In New Zealand, go to the Consumer Affairs Scams website.
- In the United Kingdom, go to the Action Fraud website.
- In Canada, go to the Canadian Anti-Fraud Centre.
- In India, go to Indian National Cybercrime Reporting Portal.
- In France, go to the Agence nationale de la sécurité des systèmes d’information.
If you can't find an authority corresponding to your location on this list, we recommend using any search engine to look up "[your country name] report cyber crime". This should lead you to the right authority website. We also recommend staying away from third-party crime report services that are often paid. It costs nothing to report Internet crime to official authorities.
Another recommendation is to contact your country's or region’s federal police or communications authority.
Frequently Asked Questions
You can only open COOL files if you have the decryption key, or if you were affected by offline encryption type.
To figure out whether you were affected by offline encryption, please go to C:/SystemID/PersonalID.txt and see if the string inside of it ends in t1. You can also try using Emsisoft Decryptor for STOP/DJVU.
Please follow the guidances provided by the official COOL decryption tools and believe what they say. If they say it is impossible to decrypt, it really is so. There is no magic tool or human capable of decrypting your files hiding somewhere. Encryption is a technique created to be nearly impossible to decrypt without a special private key (held by the criminals).
We advise scanning with anti-virus, anti-malware, malware removal tools or software like RESTORO to eliminate virus damage on the system. If you do not trust using a single tool, try running one after another. However, we do not recommend keeping several security programs on a computer at once as they can interfere with each other's work.
Beware of fake COOL decryption tools circulating around the web. Cyber criminals are uploading them to various shady websites, also might be promoting them via suspicious Youtube videos. These programs can infect your computer even more heavily (Trojans, miners, etc.). We suggest being extremely cautious around the web. If there will be an official STOP/DJVU decryption tool available, it will be widely discussed in public media.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Leave a Reply