Overview of 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware
Contents
89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ is a malicious program that falls into clipboard hijacker category. The way this program works is it automatically changes the clipboard data (the data you copy and then paste somewhere) into the aforementioned string. As a result, attempts to paste something on your computer will always result in unwanted output.
This clipboard hijacker was created with intention to promote a cryptocurrency wallet address in hopes to paste the cybercriminals’ wallet’s address instead the ones that computer user wants to paste. Since these are a long of combination of alphabets and numbers, it is natural that people do not usually type them by hand but use the copy-paste buffer instead. The idea behind such malware is to make the computer paste the criminals’ wallet address so that the funds the user wants to transfer would unintentionally be sent to a wrong wallet address.
However, the main difference is that this malware was developed without additional polishes. Real clipper-type viruses are created with rules to activate themselves when the user visits cryptocurrency-related websites and attempts to make a transaction so that the clipboard hijacking strategy would bring some results. Instead, this novice-level clipboard hijacker initiates 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ copy paste error whenever the user uses the clipboard function, therefore it can be easily noticed.

To avert this dangerous copy and paste manipulation, the user can terminate the malware’s intended fraud by ending the AutoIt v3 Script (for 32 bit) process in Windows Task Manager. Regardless of that, it should be noted that aborting the process only stops it momentarily and does not eliminate the malicious program from the device. Most of the time, during the installation of such malicious programs, they’re assigned to computer startup programs’ list so they could launch automatically whenever the user boots the computer.
AutoIt itself is a freeware tool that can be used to automate tasks in Windows operating system environment. However, it seems that this tool has been used to create various scripts intended for malevolent purposes.
However, our research suggests that usually the installation setup containing the clipboard hijacker is also configured in such a way that other harmful software contents, for example, adware and various potentially unwanted programs (PUPs) can be embedded in it. Due to that, there is a high chance that during installation of 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware, your computer was infected with more threats at the same time. The consequences could manifest in diverse ways, such as theft of sensitive personal information, appearance of bogus ads that intrude your online activities, modification of your browser settings or redirects to dubious sites among other disruptive anomalies.
Therefore, if you have noticed this copy paste error occurring on your PC, we strongly recommend that you remove 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware. You can use whichever antivirus or malware removal tool you prefer. Our team trusts RESTORO (secure download link) that can be used to repair virus damage to Windows OS files. Do not forget to follow instructions presented below the article on how to boot your PC in Safe Mode with Networking.
Threat Summary
| Name | 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware |
| Type | Malware, Clipboard Hijacker, Clipper |
| Similar threats | Extended Clipper, Clipsa, Qulab, E-Clipper, Jester, Frost, PENTAGON, S-400, Allcome |
| Associated program | AutoIt v3 Script (for 32 bit), Toveces.exe, Negumo.exe, Gakode.exe |
| Damage | The clipboard hijacker automatically changes the copy-paste buffer data with a string that is a cryptocurrency wallet address belonging to cybercriminals. Therefore, whenever user copies some data and attempts to paste it somewhere else, the aforementioned string appears instead of data that user copied. |
| Distribution | Software bundles, illegal pirated software versions, fake update ads, malicious email spam attachments |
| Detection names | Riskware.Gen (Webroot), Static AI – Suspicious PE (SentinelOne), Malicious (SecureAge APEX) see all detection name variations on VirusTotal |
| Removal | Remove malware from your PC using trustworthy software. To repair virus damage on Windows OS files, consider scanning with RESTORO (secure download link). |
REPAIR VIRUS DAMAGE
Scan your system for FREE to detect security, hardware and stability issues. You can use the scan results and try to remove threats manually, or you can choose to get the full version of software to fix detected issues and repair virus damage to Windows OS system files automatically. Includes Avira spyware/malware detection & removal engine.
Distribution of similar malware
Many users often wonder how viruses similar to 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ end up in their computer systems. The most common ways used to distribute them include drive-by downloads, malicious attachments or links sent through emails/messages, online torrent listings or rogue third-party sites providing downloads such as dubious software versions including key generators, so-called “cracks”, fake updates and freeware.
Our research showed that malware usually came in archives that contained two files which may be named Gakode.exe, Gakode.bat, Toveces.exe and Toveces.bat, Negumo.exe or Negumo.bat.

You should always remember that malware is typically distributed in disguise or embedded in freeware bundles as secondary attachments. Aside from typical executables, the scammers can embed malicious scripts in various document formats such as DOCX, PDF, XLS and others that support scripts and macros. Such malformed documents are then attached to scam emails and sent out to thousands of potential targets. That said, you should be very careful when checking your email.
How you can prevent installation of malware
The importance of downloading software contents only from authorized channels or platforms can never be overemphasized. Also, activation of new programs or updating of existing ones should only be done using tools developed by genuine software developers.
Likewise, emails or even attachments and links sent from unrecognizable sources shouldn’t be opened because they may be filled with malware.
To safeguard your computer system at all times, it is crucial to install genuine antivirus and keep it up-to-date at all times. You should also schedule regular system scans and and enable real-time protection.
Remove 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware for good
If you have discovered that your clipboard was hijacked by the described malware, you should remove 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ virus without a delay. In order to do it, we recommend opening your Task Manager and stopping a process named AutoIt v3 Script (32 bit) first.

Then, we recommend that you boot your PC in Safe mode with Networking as explained below and then run your antivirus or malware removal software. Our team recommends downloading RESTORO to help repair virus damage on Windows OS files and identify malware remains.
Follow this guide to fix 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ clipboard hijack now:
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software.
REMOVE THREATS WITH ROBUST ANTIVIRUS

Get INTEGO ANTIVIRUS for Windows to remove ransomware, Trojans, adware and other spyware and malware variants and protect your PC and network drives 24/7. This VB100-certified security software uses state-of-art technology to provide protection against ransomware, Zero-Day attacks and advanced threats, Intego Web Shield blocks dangerous websites, phishing attacks, malicious downloads and installation of potentially unwanted programs.
Use INTEGO Antivirus to remove detected threats from your computer.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in Safe Mode with Networking, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to start Windows in Safe Mode:
Instructions for Windows XP/Vista/7 users
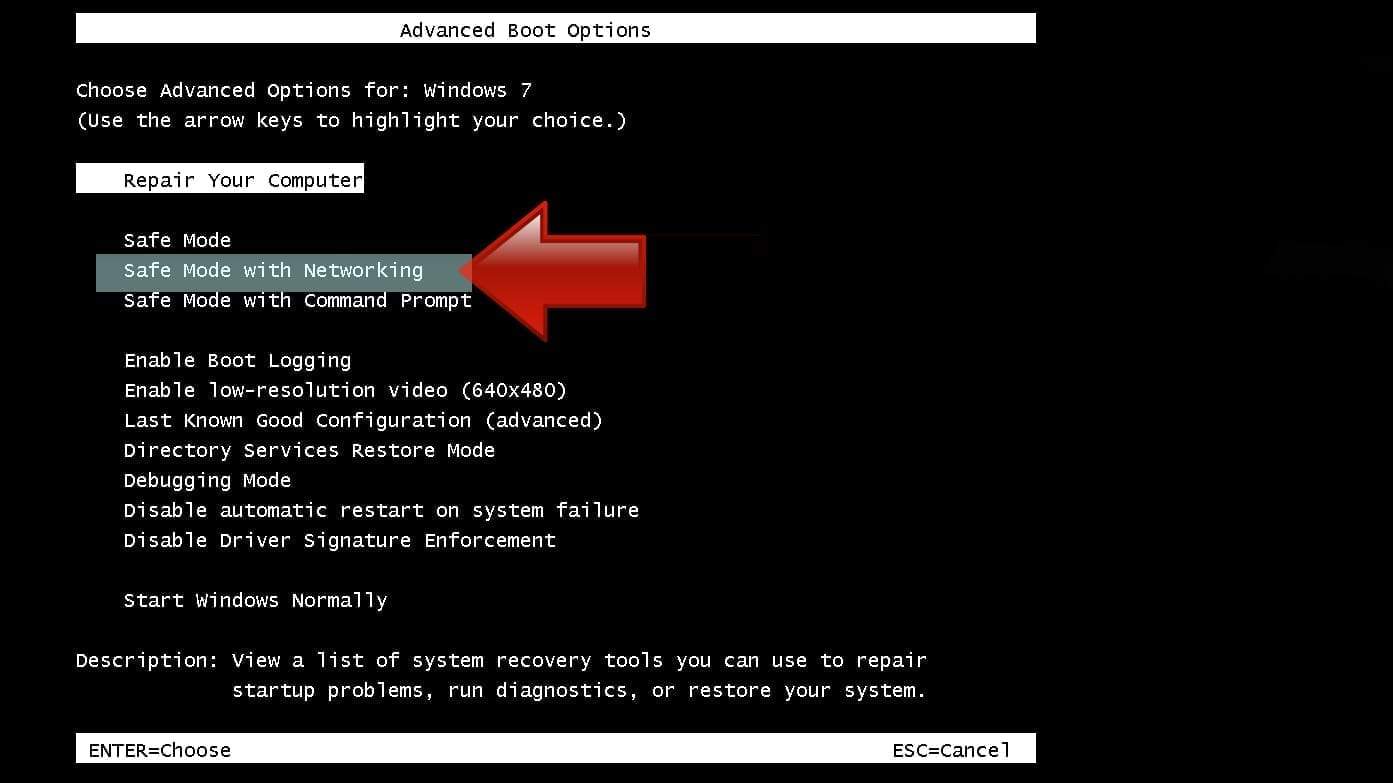
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
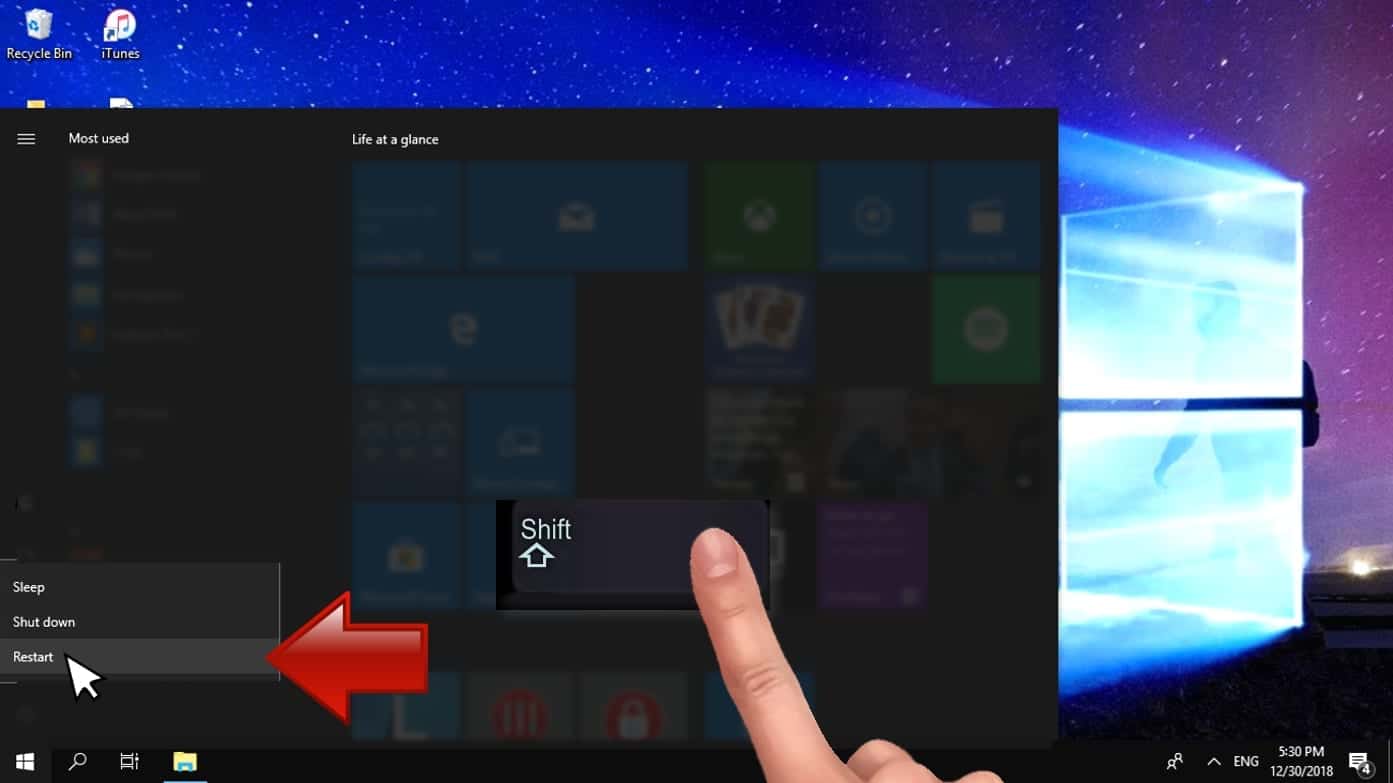
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
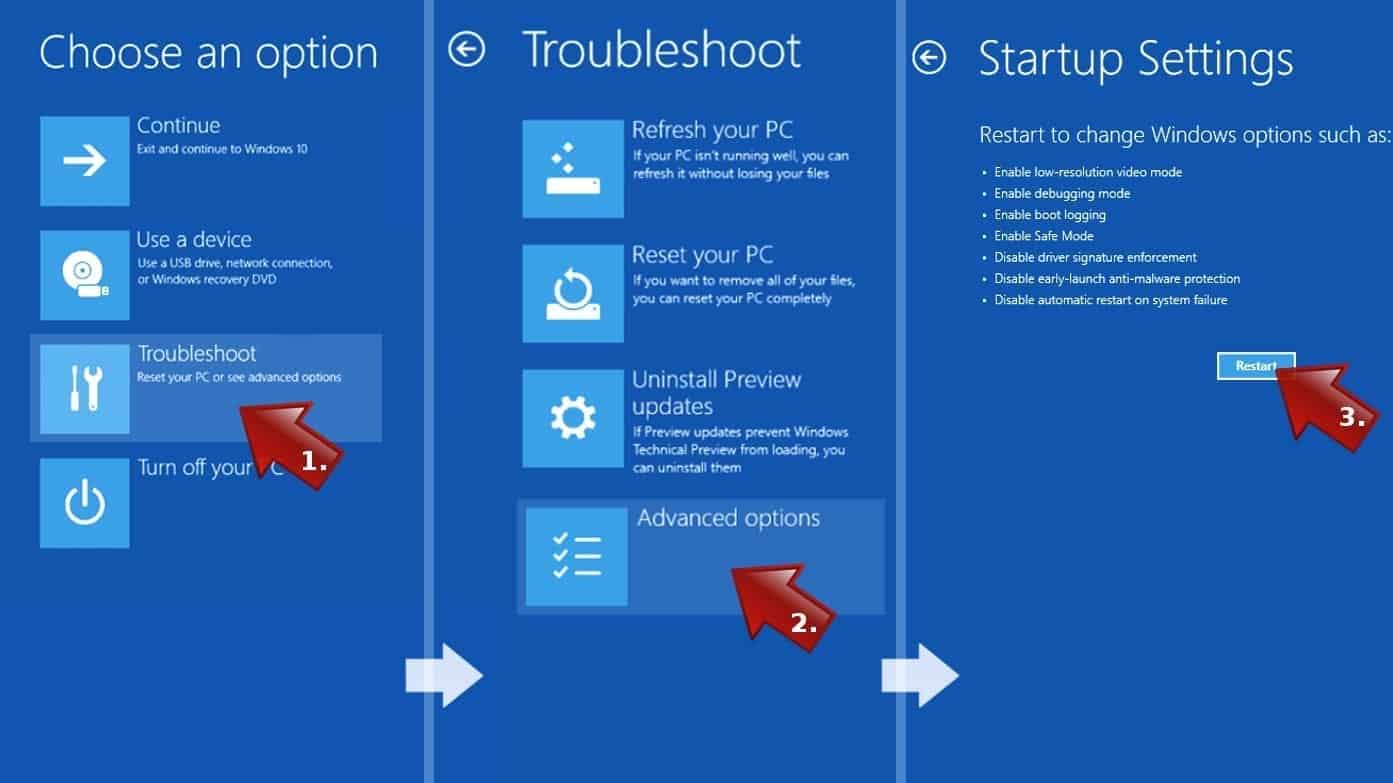
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
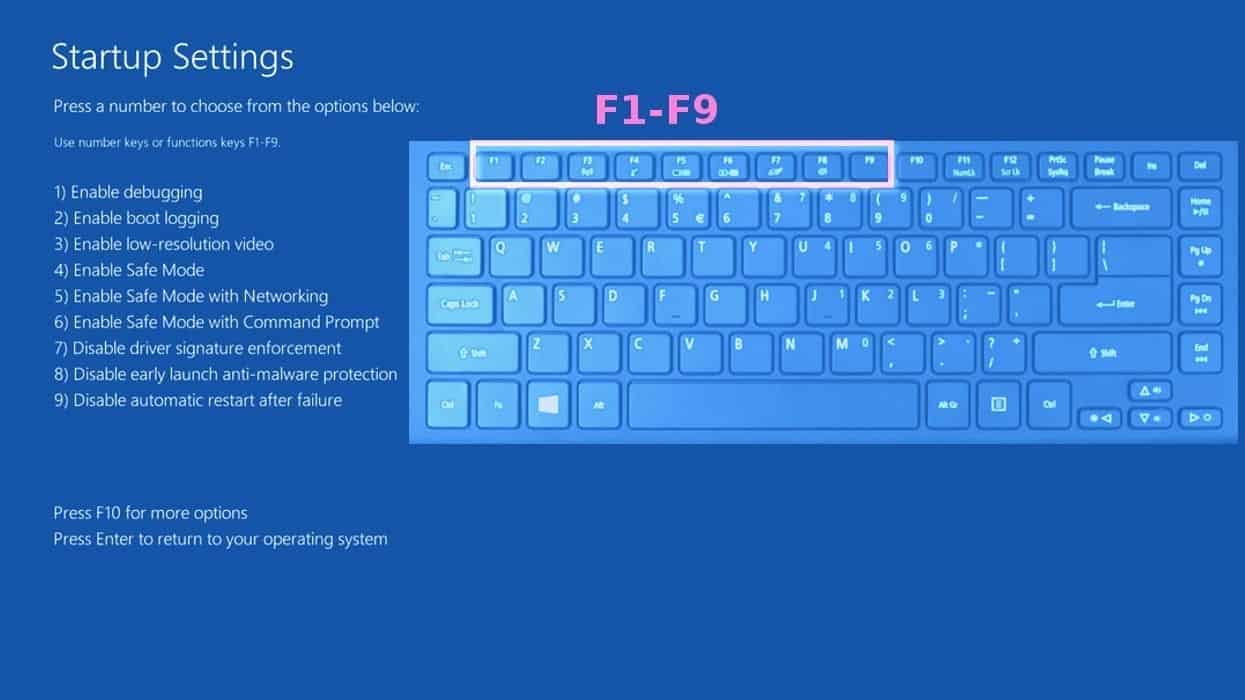
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware files. It is very hard to identify files and registry keys that belong to the virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. We recommend using SYSTEM MECHANIC ULTIMATE DEFENSE , which can also restore deleted files. Additionally. we recommend repairing virus damage using RESTORO.
Special Offer
Compatibility: Microsoft Windows
See Full Review
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
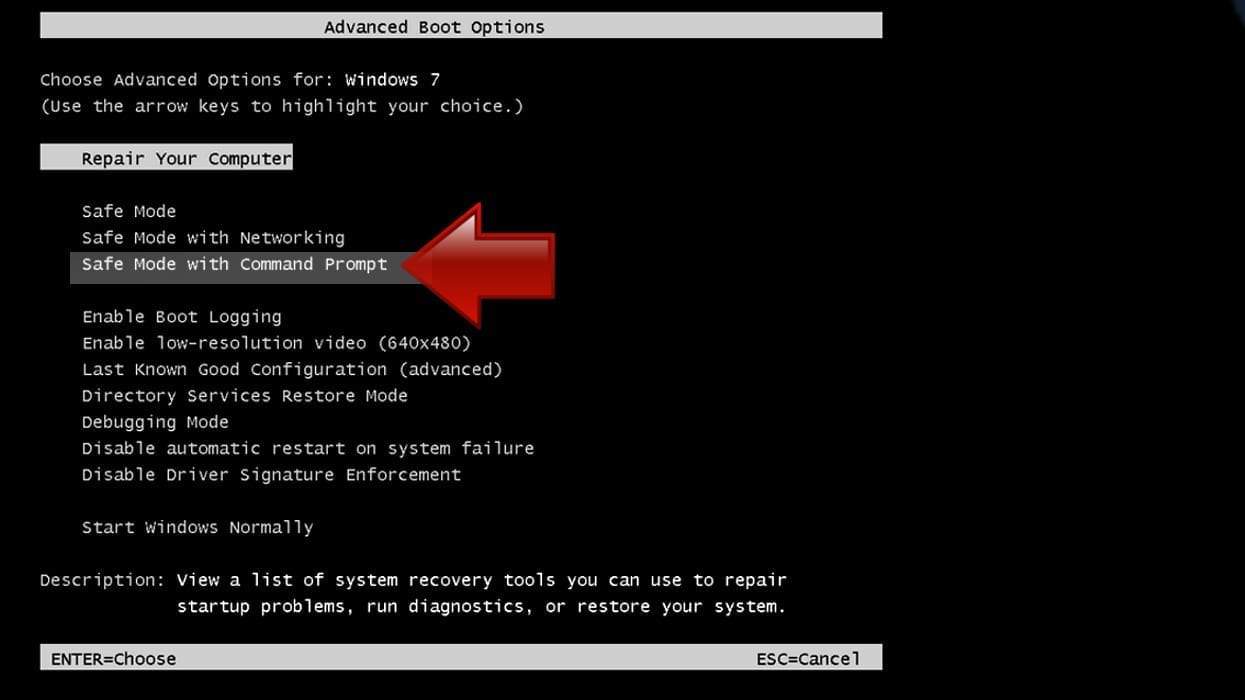
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.

- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before the malware infiltration.
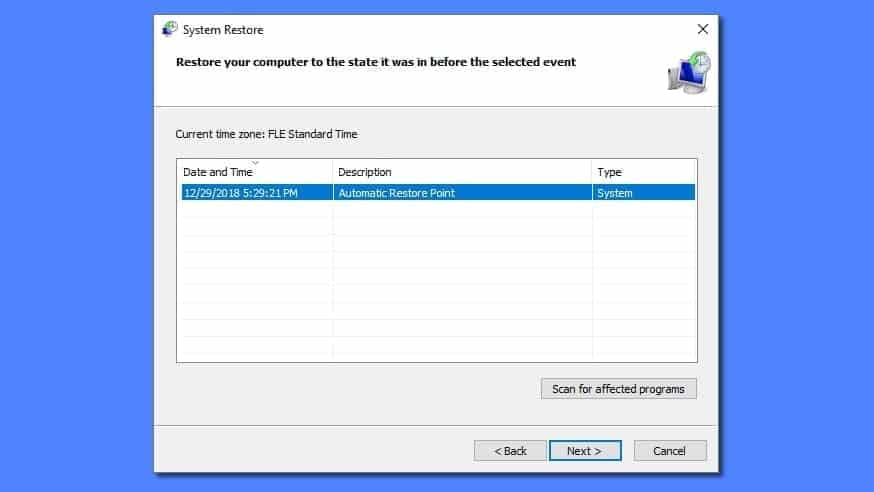
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Leave a Reply