Geek Squad Email Scam falsely claims that a costly subscription renewal has been completed
Contents
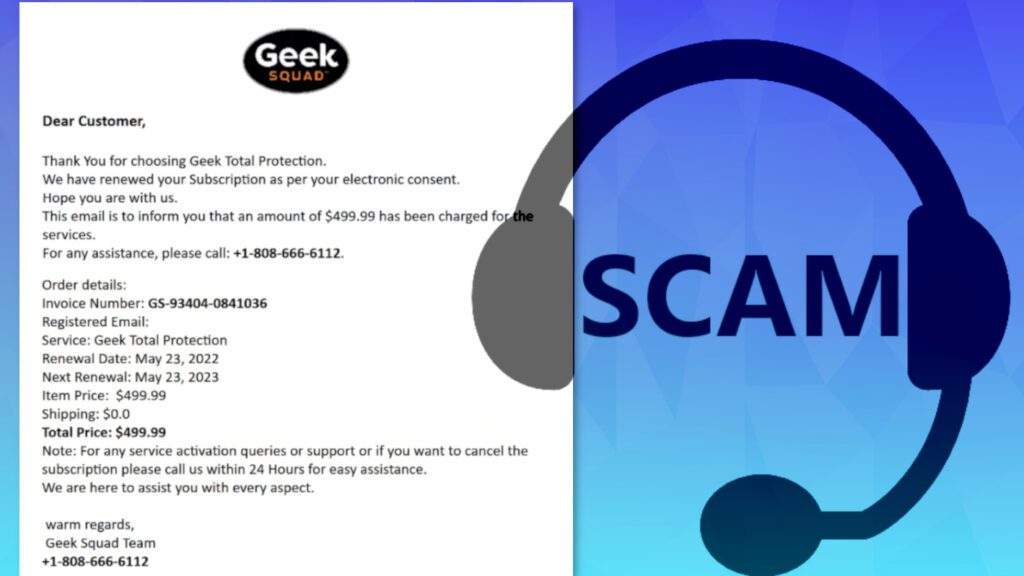
Geek Squad Email Scam is an actively distributed email spam campaign. It provides false claims about user’s renewal of Geek 360 or Total Protection Subscription. The email contains a subject line stating “Transaction Confirmation” and its contents suggest that the user’s subscription to Geek Squad services has been renewed “as per electronic consent” allegedly provided by the computer user. The email also falsely states that a high amount of money, for example, $499.99 has been charged for the services. Finally, the email includes a scammer’s phone number (1+808-666-6112).
Geek Squad (Best Buy subsidiary) is a company that provides support through in-store, on-site, over the Internet via remote access, and also via telephone regarding all consumer electronics. However, this company has nothing to do with the scammers who use its name for committing fraud. Another noticeable detail is that these emails are usually sent from bot email accounts, typically Gmail, iCloud and similar.
Since legitimate companies usually assign email addresses with the company’s domain, this is yet another reason not to trust the sender’s claims. Therefore, if you have received a similar email to the described ones, just ignore it.
Geek Squad Email Scam is meant to scare you. Your bank account is not, and will not be charged, no matter what the email says. Ignore it – the threat actors send the same email to thousands of people daily. The scammers are trying to scare you and trick you into calling them, so they could tell more lies to you. Their aim is usually to convince you to purchase gift cards or pay for services by deceit.
Norbert Webb
What happens if you call the phone number provided in Geek Squad Email Scam?
If the victim falls for Geek Squad Renewal Email Scam and tries contacting the scammers via provided number, several things can happen. Typically, the victims rush to get some explanation on why they have been charged – sometimes even without checking their bank balance first.
After calling the provided number, the victim may be greeted by a scammer who pretends to be a Geek Squad’s employee. From this point onward, the scammer acts according to several scenarios prepared in advance. Therefore, the situation can go in variety of ways. For example, the scammer might try to swindle valuable information from the victim – including full name, credit card details, social security number, and other data.
In other scenarios, if the victim insists on cancelling the subscription, they might request a cancellation fee to be paid to them.
On top of that, the scammer might create stories why the victim needs this subscription or claim that there was a problem detected on victim’s computer or home network. At this point, they may request to connect to victim’s computer remotely. They may detect an issue, pretend to fix it and require payment for applying the “fix.”
After gaining remote access to victim’s PC, the crooks may also silently install malware on the computer. If this is the case, you may want to use a robust antivirus solution like INTEGO Antivirus to remove the malware and then download RESTORO to repair virus damage on Windows OS files. Read the instructions provided below the article on how to delete malware via Safe Mode with Networking on Windows.
TIP: Do not provide the scammer with valuable information, whether it is your personal information, credit card information, or data required to access your computer remotely.
Threat Summary
| Name | Geek Squad Email Scam |
| Type | Email Scam, Phishing, Telephone Scams |
| Email subject line | Transaction Confirmation, Your Order Receipt From [date], Check Your Invoice, Thank You |
| Deceptive statement | We have renewed your subscription as per your electronic consent. This email is to inform you that an amount of $499.99 has been charged for the services. |
| Scammers’ email addresses | imocor@consulnetti.com, martinelllinkergmuv8596@gmail.com, frankthomas7887@gmail.com, Lily.sheppard44@icloud.com, virgiliostutzmanq169@gmail.com, hodgwesbrian@gmail.com, info@geek-squadservices24.co and others |
| Contact phones | +1-808-666-6112, +1-888-738-8146, +1-888-695-6573, +1-888-992-0664, +1-888-576-9533, +1-802-321-0108, +1-888-593-3963, +1-808-809-5897, +1-888-459-2122, +1-888-229-6276, +1-802-214-8676, +1-818-483-4225, +1-888-526-2865, +1-888-682-2165, +1-818-221-1901, +1-844-232-6022 and others |
| Potential damage | After communicating with the scammers via email, the victim may be tricked into revealing personal information, credit card details, or credentials to remotely access one’s computer. As a consequence, the criminals might actually swindle money from your or even drop malware on your computer. |
| Distribution | Email spam campaigns |
| Removal | If you suspect that scammers dropped malware on your computer via remote desktop connection, remove it from your PC using trustworthy software. To repair virus damage on Windows OS files, consider scanning with RESTORO (secure download link). |

Intego Antivirus for Windows
Award-winning antivirus solution for your PC.
Robust security software that provides robust 24/7 real-time protection, Web Shield that stops online threats/malicious downloads, and Prevention engine that wards off Zero-Day threats. Keep your PC safe and protected against ransomware, Trojans, viruses, spyware and other forms of dangerous programs.
Examples of Geek Squad Email Scam emails
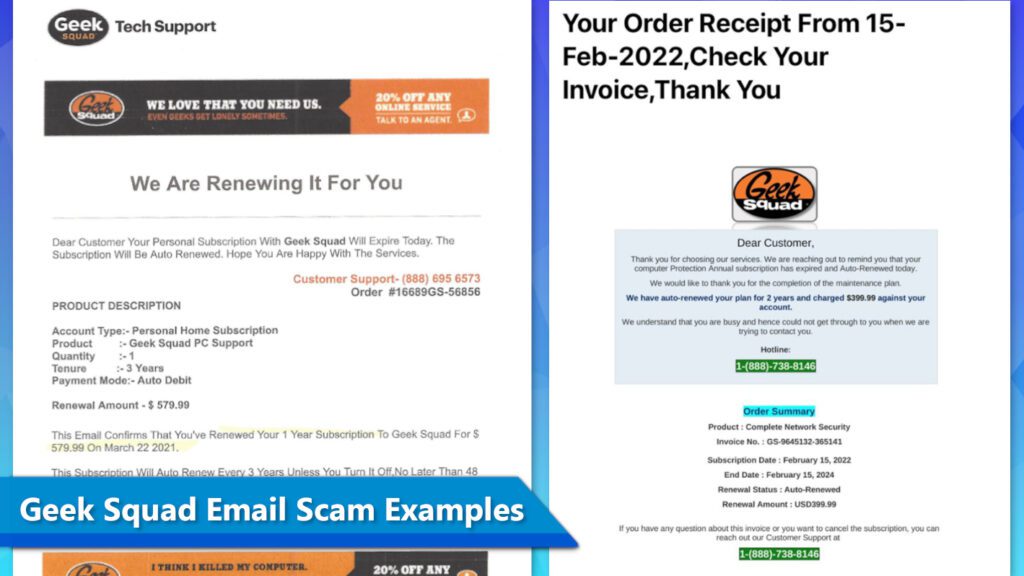
The design of Geek Squad Email Scam campaigns is similar, and so are the messages from the criminals. Here is an example of a scam that claims the user will be charged $579.99 for a 3-year subscription. The number provided by the scammers is 1-888-695-6573.
We Are Renewing It For You
Dear Customer Your Personal Subscription With Geek Squad Will Expire Today. The Subscription Will Be Auto Renewed. Hope Your Are Happy With The Services.
Another scam claims the user will be charged $399.99 due to auto-renewal of plan for 2 years. The scammers also include a fake order summary and provide a hotline phone number – 1-888-738-8146.
Dear Customer
Thank you for choosing our services. We are reaching out to remind you that your computer Protection Annual subscription has expired and Auto-Renewed today.
We would like to thank you for the completion of the maintenance plan.
You can see screenshots of these scam emails below.
An example text from one of these scam emails is shown below.
Wednesday, September 21, 2022
Geek Squad Email Scam example
Order Number: tYTcX-mwL3Bt-bGHn
Helpline: (808) 809-5897
logo
[Name] Thank you for our support!
Your membership at Geek Squad is about to expire on Sunday, August 21, 2022. We hope you’ve enjoyed benefits of your membership for the last five year.
Good news!! Now we have one time renewal membership at low price of $678.99. As the membership is an auto-renewal so it has been renewed for the next five year.
Your Order Is On Its Way
ORDER DETAILS:
Transaction No: WJD7890UR9980US
Item: Geek Squad Personal Home Membership
Renewal Amount: $678.99
Tenure: 5 Year Support
CLIENT DETAILS:
Client: [Name]
Client ID: 435869452
Client Email: [ E-mail]
If you have any questions regarding your membership, benefits, or renewal, please don’t hesitate to reach out by replying to this email or calling us at (808) 809-5897.
Copyright @ 2022 Geek Squad All rights reserved.
Accounts Head: KOSAL BOV
Our Mailing Address: 620 3rd st3rd fl Gainesville GA 30501 United States
Unsubscribe – Unsubscribe Preferences
Yet another example of such scam emails reports about renewal of Geek 360 Subscription. The email suggests that user’s account has been debited for $249.89. In case the recipient needs additional information or wants to cancel the subscription, the scammer suggests calling a provided number, which is +1 844 232 6022. Again, if you have received this message, simply delete it.
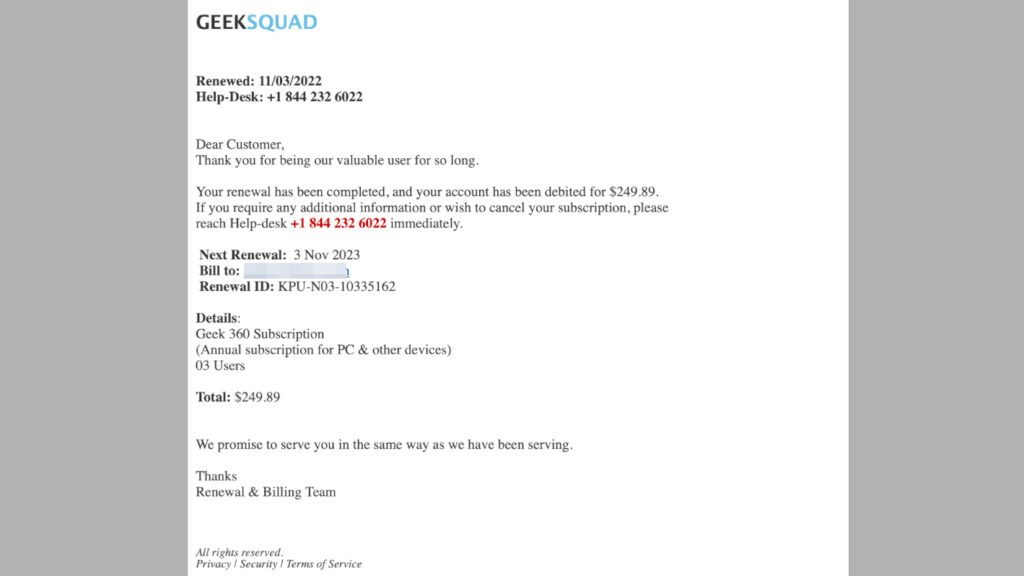
Another sample of this scam that has reached our email warns about renewal of Geek Secure 360 Protect plan and claims $385.99 will be deducted from our account. The provided scammer’s number is +1 (818) 221-1901. This fake email sender is info[at]geek-squadservices24.co.
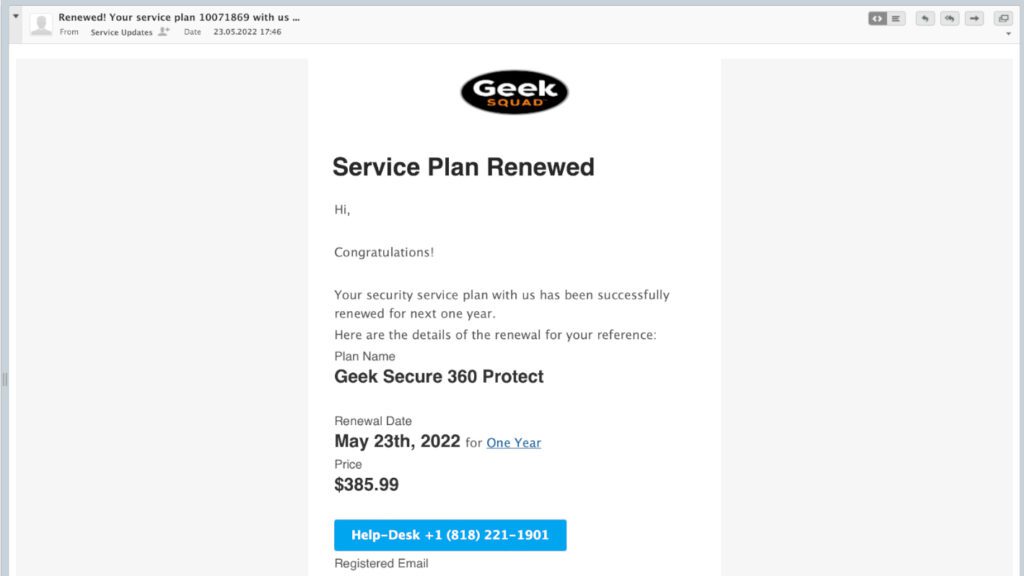
Here’s another example of this scam email. An interesting detail that often reveals the sender isn’t who he claims to be is errors in the message body – in this case, you can see the inconsistency of capitalization of the words.

There are many more examples of this scam as the perpetrators keep changing the design regularly. However, as it can be seen from these examples, the perpetrators are trying to replicate the design of the real Geek Squad emails as they include the official logo and promotional banners used by the company.
These emails usually claim that a certain amount of money will be deducted from the user’s bank account, which causes fear for the target and prompts them to call the phone number provided.
How to identify and avoid phishing emails?
In general, scammers use phishing emails to extract sensitive information or gain remote access to victim’s computer to perform some illegal actions on it. The analysis of such emails over time showed that threat actors use similar patterns of deceptive social engineering tactics. Let us provide you with some tips on how to recognize such emails and avoid them.
- Do not trust that the sender’s email is legitimate – it might be spoofed. If you have some concerns regarding the email you just received, but the sender’s email appears to be coming from a well-known company or a person – check if it wasn’t spoofed. Email spoofing is a technique that allows the attacker to display a different sender’s email for the recipient rather than the original one.
- Look out for urgent calls for action or threats. Scammers try to create a false sense of urgency to trick the target into acting without thinking. They seek to force the victim to search for solution to avoid potential problems described in the email even without checking the facts or researching the credibility of the sender’s statements.
- Check for text errors. Scammers rarely know a thing about perfect grammar. Although they try their best to compose convincing emails that also include backgrounds, images and logos, it is still easy to spot that the email wasn’t sent by a reputable company since there are some easily noticeable typographical, spelling, preposition or punctuation errors.
- Inspect the greeting line. Most of scam emails are sent out using automatic tools that are programmed to insert the recipient’s name using the prefix part of the email address. That said, you should know that legitimate companies usually know your real first and last name and address you by your full name. For instance, if your email address is sunflower99@exampleemail.com, the scammer most likely will greet you with “Dear Sunflower99” or similar line rather than using your real name. Likewise, some scammers simply use “Dear valued customer” or “Dear Sir/Madam” when addressing potential victims.
- Ask yourself if you have any connection with the sender of the email. For example, think whether you have ordered any products or services from the respective online store that the email sender claims you did so. If you didn’t, do not interact with the email attachments, links, and do not call numbers provided in it. If you want to investigate further, find the company’s contact information online rather than using those provided by the suspected spammer. Reach out to the company and ask if it has sent you this email.
- Do not rush to click on links or open email attachments. Lastly, avoid interacting with URLs or files attached to the email. Phishing emails often include attachments that seem to be regular documents. Unfortunately, they may contain scripts that are used to download and run malware on victim’s computer. In general, if you are sure that the email isn’t dangerous and you want to open the attached file, make sure you do not open it directly, but save it and scan with an antivirus first.
Remove malware from your computer
In case you have had interactions via telephone with scammers and even worse, if you were tricked to provide remote desktop connection to your computer, we strongly advise that you scan your PC with a robust antivirus solution to remove malware and other threats that may have been installed by the criminals. You can find a comprehensive and free tutorial below.
OUR GEEKS RECOMMEND
Our team recommends removing malware using a professional antivirus software.
REMOVE THREATS WITH ROBUST ANTIVIRUS

Get INTEGO ANTIVIRUS for Windows to remove ransomware, Trojans, adware and other spyware and malware variants and protect your PC and network drives 24/7. This VB100-certified security software uses state-of-art technology to provide protection against ransomware, Zero-Day attacks and advanced threats, Intego Web Shield blocks dangerous websites, phishing attacks, malicious downloads and installation of potentially unwanted programs.
Use INTEGO Antivirus to remove detected threats from your computer.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
malware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in Safe Mode with Networking, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to start Windows in Safe Mode:
Instructions for Windows XP/Vista/7 users
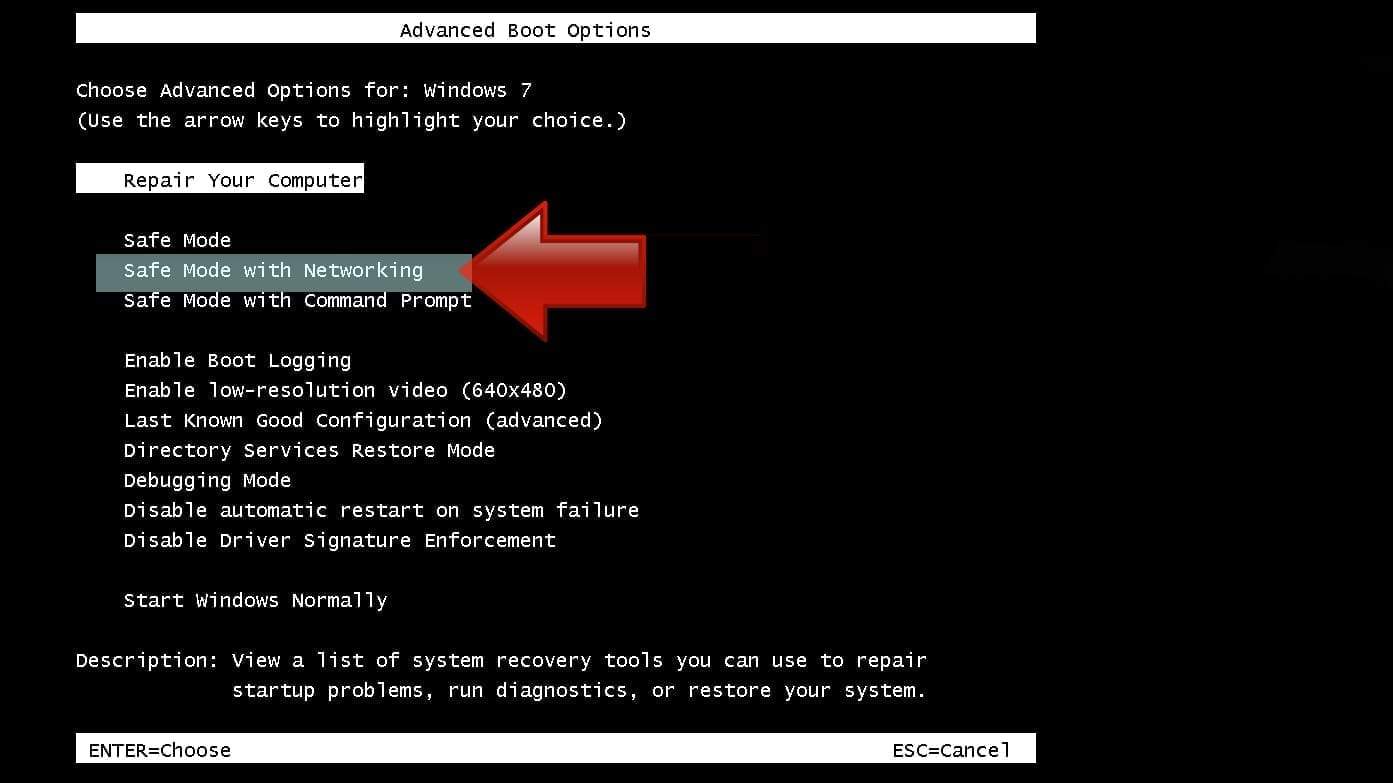
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
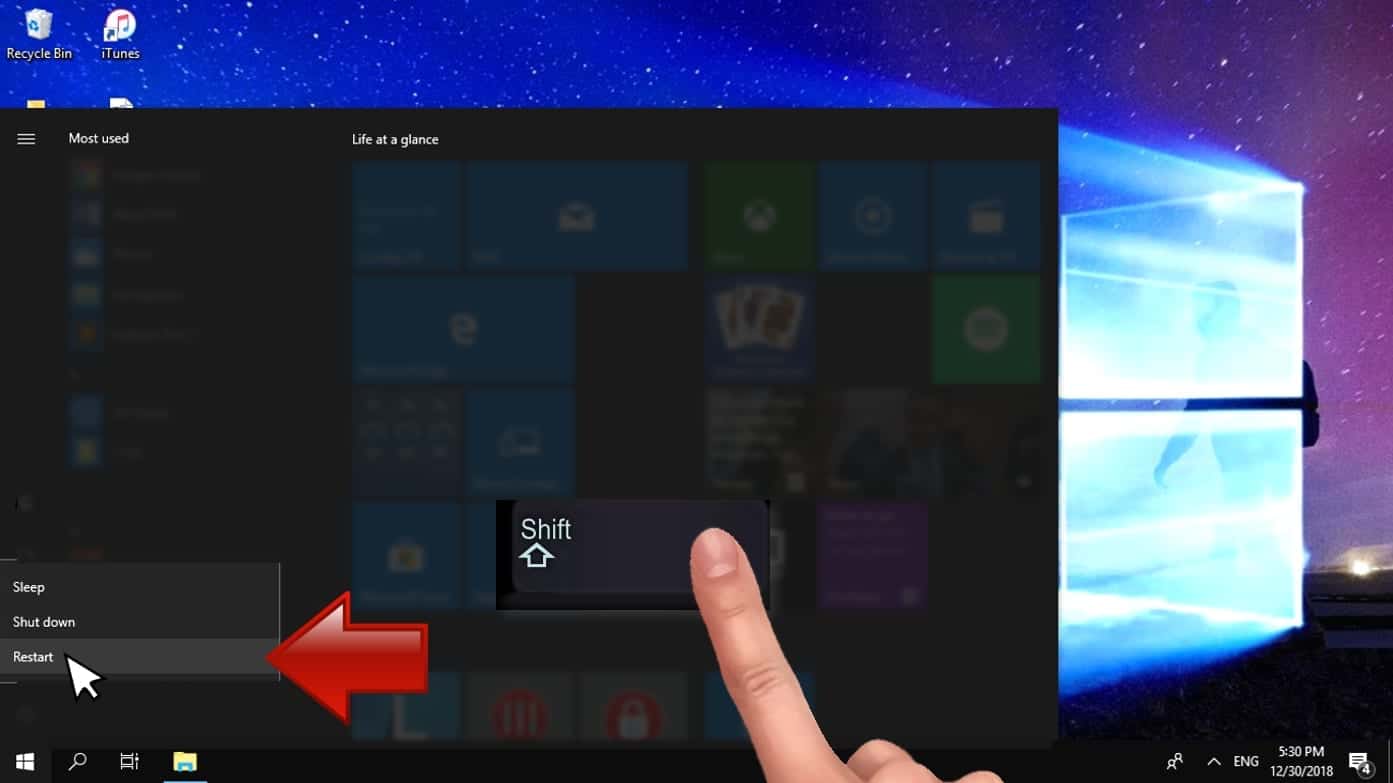
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
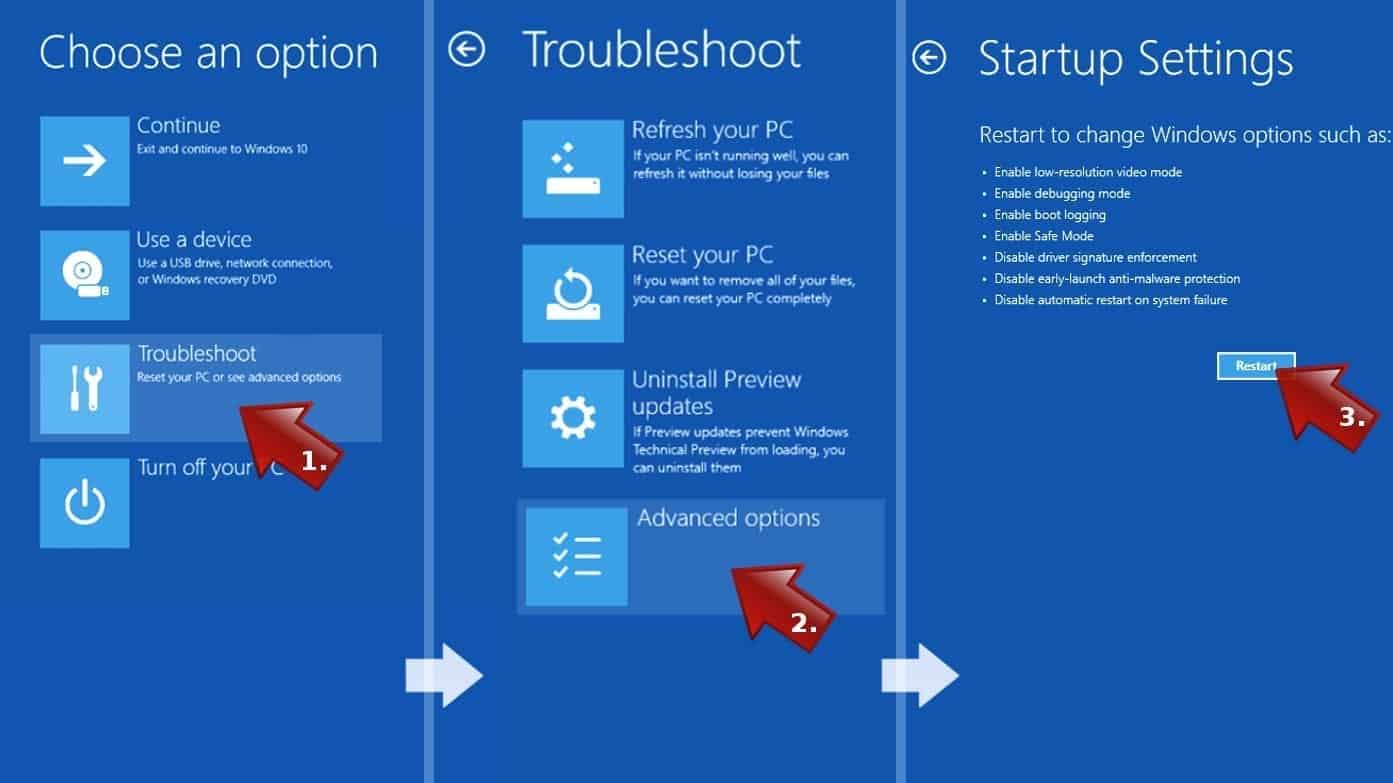
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.
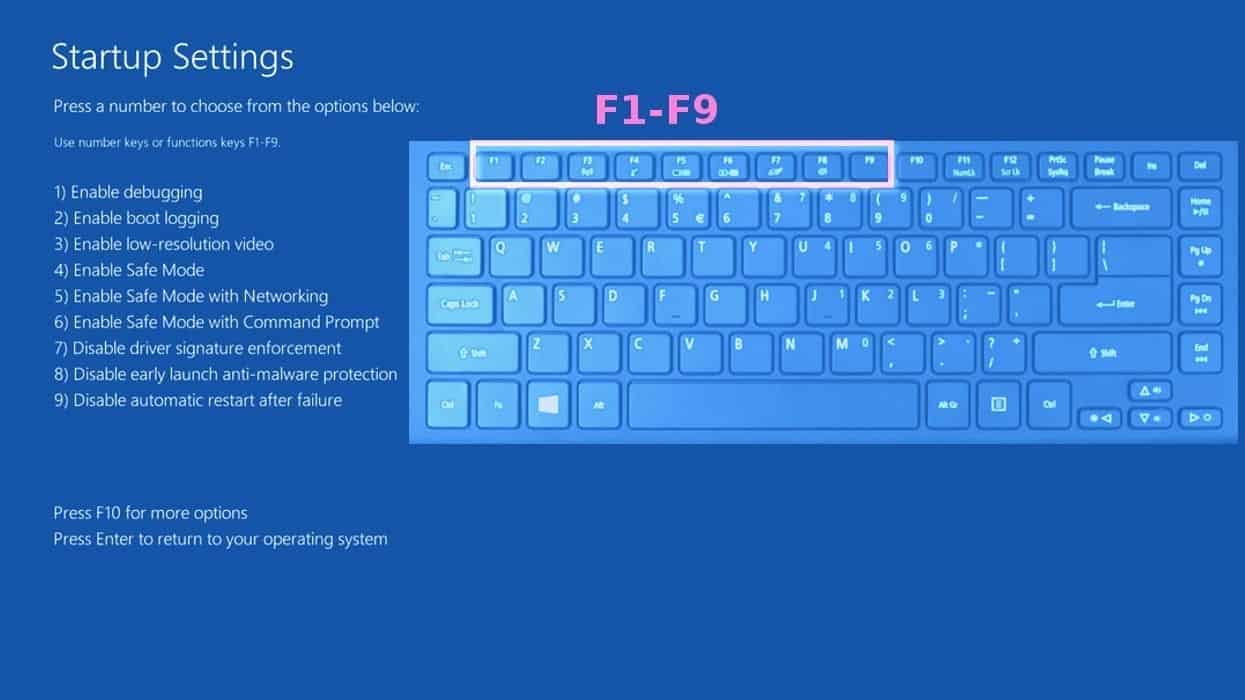
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove malware files. It is very hard to identify files and registry keys that belong to the virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. We recommend using SYSTEM MECHANIC ULTIMATE DEFENSE , which can also restore deleted files. Additionally. we recommend repairing virus damage using RESTORO.
Special Offer
Compatibility: Microsoft Windows
See Full Review
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
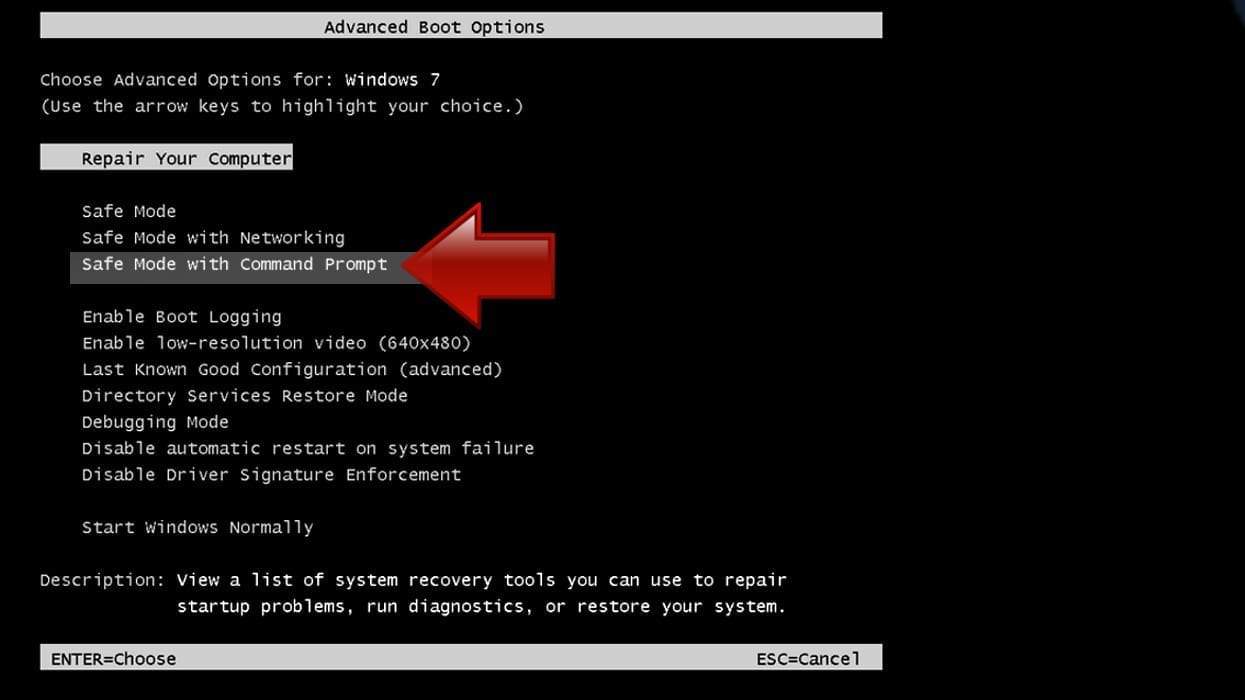
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.

- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart. Tip: If you can't find Startup Settings, click See more recovery options.

- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.

Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.

- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before the malware infiltration.
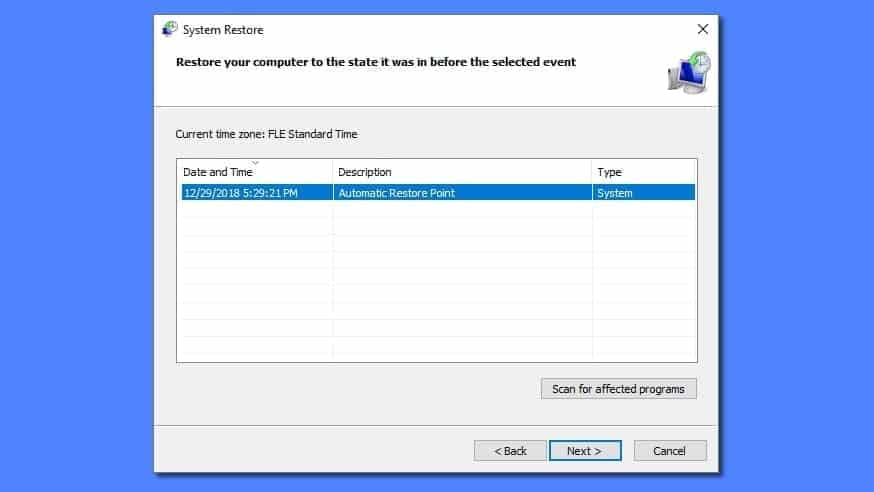
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
I received the e-mail scam on 04/11/2023 and the phone number to call 1-805-421-4748. I am so disgusted with people who try to steal from people.
Thank you. I found you before I opened the email. Just couldn’t figurer it out, so went looking. Much appreciate your detailed explanation.
Got very similar email today…. $399.99 for 3 years protection. I already Knew it was a scam especially when the final line stated “This email is to confirm your order. We will send you another email as soon as it ships.”
Shipping computer protection plan!! 😂
I received an email on my account and an urgent message to call immediately to avert my account from being locked. Not that both are the same predator.
Geek Squad Renewal Confirmation Order #CeGvX-fWGsh-tdZ8
December 2, 2022 on Auto Pay $573.59
Account Mgr: Alma Cornish
Help Desk (888)347-0866
CALL IMMEDIATELY within 1 day to report a Transaction Problem
Received this today from: mnuji lkoi
Subject: Instructions are included below
Message (misspelled the way they misspelled it):
Dear customer,
As a registered customer, we are pleased to assist you. We have premium security services available for installation. According to our contact with you. Your plan will be auto renewed with in 24hrs and you will be charged $413.00
Phone #: 1(808) 556-6295