Some STOP/DJVU ransomware victims can decrypt or repair encrypted files: here’s how
Contents
STOP/DJVU ransomware virus is one of the most widespread crypto-malware that has over 670 variants and has been highly active since 2019. It functions by encrypting files on target computer and demanding a ransom payment in exchange for data decryption tools. Different versions of this virus have reportedly affected more than half a million victims worldwide, leaving people without access to their own files. Naturally, the primary dilemma for each victim of this malware is how to decrypt files locked by STOP/DJVU. Since the malware is complicated, so is the decryption of files locked by it. STOP/DJVU Decryptor is the only tool that is intended to decrypt files locked by STOP/DJVU, while Media_Repair is an utility that can help to repair some audio/video file formats affected by the ransomware. It is important to know that these tools can only be helpful under specific circumstances.
The STOP/DJVU decryptor is an file decryption tool created by Emsisoft and Michael Gillespie and published on October 18, 2019. The tool was initially developed by creating a side-channel attack on ransomware’s keystream. The tool can help victims recover their files without paying a ransom to the cyber criminals.
Furthermore, this decryptor is continuously updated and may be able to decrypt files affected by offline key encryption, but only if victims who have paid the ransom and successfully received the decryption key choose to share it with Emsisoft. When it comes to offline key encryption, all victims of one specific STOP/DJVU variant can decrypt their files with the same decryption key. However, this does not apply to online key victims of the same ransomware variant. The cybersecurity company does not announce when such keys are retrieved due to victim confidentiality. Victims are advised to download the tool and test if the files can be decrypted.
In addition, there is a trustworthy tool that can help you repair specific file types. Media_Repair (released by DiskTuna) is a tool intended to repair audio/videos files. We strongly recommend trying this tool in case STOP/DJVU decryptor cannot help you. This audio/video file recovery tool can also be used no matter which encryption type was applied on your files. The guide below will explain how to use it to recover part of your data.
The STOP/DJVU ransomware is mostly distributed using malicious keygens, software cracks and tools like KMSPico. The malicious payload was strategically hidden in these popular, yet illegal files used to activate paid software for free. Our analysis shows that the malicious files that dropped the ransomware also contained additional malware, namely Vidar, Azorult and RedLine stealers.
In 2019, Emsisoft has released STOP/DJVU decryptor, and at the time, Emsisoft claimed that it was capable of restoring data for about 70% of all victims. Unfortunately, 12 versions of the ransomware were the “improved” ones and these couldn’t be fully recovered. It appears that the tougher ransomware versions started emerging around August 2019.
DJVU ransomware victims should be aware that the virus’ versions based on their extensions are categorized into Puma, Uppercase, old and new variants (see detailed description below). It’s been a while and all the current versions can be decrypted ONLY if offline encryption was used. Additionally, despite online or offline encryption used, you can repair certain file types using DiskTuna’s tool Media_Repair (find the usage guide below).
UPDATE 2022, October 25th. The latest STOP ransomware versions and possibility to recover files based on the key type are listed below. Versions with retrieved offline keys are also included.
DJVU versions that can be decrypted (offline encryption) – UPDATED LIST
Currently, Emsisoft Decryptor for STOP DJVU database includes decryption keys for the following ransomware variants (only for offline key encryption victims – see how to determine what encryption type was used on your files). Here is the updated extension list:
.gero, .hese, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .noos, .kuub, .reco, .bora, .nols, .werd, .coot, .derp, .meka, .mosk, .peet, .mbed, .kodg, .zobm, .msop, .hets, .mkos, .nbes, .reha, .topi, .repp, .alka, .nppp, .npsk, .opqz, .mado, .covm, .usam, .vawe, .maas, .nile, .geno, .omfl, .sspq, .iqll, .ddsg, .wiot
Please be patient because offline keys for the latest 2022/2023 versions – COZA, BOTY, BOZA, KIOP, KIFR, KITZ, KIWM, NIWM, NITZ, NIFR, JYCX, JYOS, JYWD, JYPO, TYPO, TYOS, TYWD, TYCX, DARJ, DAZX, DAPO, QARJ, QAZX, QAPO, CRAA, COBA, COAQ, COSW, GOBA, GOAQ, GOSW, QOTR, QOWD, QOQA, IOWD, IOQA, IOTR, HHEE, HHOO, HHMM, VVOO, VVMM, EROP, ERQW, ASSM, MZTU, MZOP, MZQW, POUU, POQW, ZOUU, ZOQW, BPTO, BPWS, BPSM, ZNTO, ZNSM, ISAL, ISWR, ISZA, MANW, BTTU, BTOS, BTNW, MAOS, MATU, MPPN, MBTF, UYIT, UYRO, KCBU, KCVP, TCVP, TCBU, FATE, FATP, ZATP, ZATE, BOWD, POZQ, BOZQ, POWD, NUIS, NURY, TURY, TUIS, POHJ, POWZ, TOWZ, TOHJ, ADLG, ADWW, OFWW, OFLG, OFOQ, AAWT, AAMV, AABN, AAYU, EEYU, EEMV, EEWT, EEBN, MMDT, MMVB, MMPU, OOPU, OODT, OOVB, QQKK, QQPP, QQJJ, QQRI, QQLC, QQLO, QQMT, CCZA, CCEO, CCEW, CCYU, VVYU, VVEW, VVWQ, VVEO, HHYU, OOXA, OORI, GGEO, GGWQ, GGEW, HHEO, HHWQ, HHEW, JJWW, JJYY, GHSD, DKRF, EIUR, LLQQ, LLEE, LLTT, LLOO, EIJY, EFVC, HKGT, BBZZ, BBII, BBYY, EEFG, BNRS, RRYY, RRBB, RRCC, ZFDV, EWDF, UIHJ, ZPPS, QLLN, NNUZ, FEFG, FDCV, DFWE, ERRZ, IFLA, BYYA, KRUU, SIJR, BBNM, EGFG, XCVF, MINE, HHJK, TTII, MMOB, JHGN, JHBG, DEWD, JHDD, DMAY, MSJD, NUHB, YGVB, DWQS, QPSS, HAJD, QALL, GHAS, UYJH, TUID, UDLA, GTYS, MPAG, VOOM, KXDE, WDLO, PPHG, RGUY, SSOI, KKIA, HFGD, MMUZ, RGUY, UIGD, EYRV, VLFF, BPQD, XCBG, KQGQ, VTYM, QBAA, FOPA, VYIA, IIOF, SDJM, FGNH, FGUI, JJTT, RTGF, OOII, GCYI, EUCY, CKAE, QNTY, CCPS, IIPS, AVYU, CUAG, BBBE, BBBR, QQQR, MAIV, BBBW, YOQS, QQQE, QQQW, MAAK, FHKF, VFGJ, YBER, ZAQI, NQHD, VGKF, DEHD, LOOV, MIIA, SBPG, XCMB, NNQP, HUDF, SHGV, YJQS, MLJX, YQAL, MOIA, ROBM, RIGJ, PQGS, IISA, FUTM, QMAK, QDLA, STAX, IRFK, PALQ, COOL, RIVD, RUGJ, ZAPS, MAQL, VTUA, IRJG, NQSQ, TISC, RIGD, KOOM, EFDC, LQQW, IWAN, ORKF, HOOP, REQG, MUUQ, NOOA, GUER, AEUR, HHQA, MOQS, UFWJ, GUJD, WWKA, ZZLA, LSSR, POOE, ZQQW, MIIS, NEER, LEEX, PIIQ, QSCX, MPPQ, PAHD, PAAS, EHIZ, NUSM, IGVM, PCQQ, REJG, WRUI, LMAS, URNB, FDCZ, YTBN, EKVF, ENFP, TIRP, REIG, RIBD, CADQ, YGKZ, PLAM, .COSD, POLA, WBXD, COOS, QLKM, ATEK, IGAL, BOOA, IGDM, NOBU, WEUI, LISP, SGLH, EPOR, VVOA, AGHO, VPSH, JDYI, IISS, NYPG, EFJI, MMPA, FOQE, MOSS, LYLI, COPA, KOLZ, NPPH, OGDO, KASP, NORD, BOOP, VARI, OONN, KOOK, ERIF, KUUS, REPL, ZIDA, MOBA, PYKW, TABE, NYPD, ZWER, KKLL, NLAH, ZIPE, PEZI, KOTI, MZLQ, SQPC, MPAL, QEWE, LEZP, LALO, MPAJ, JOPE, OPQZ, REMK, FOOP, LOKD, REZM, MOOL, OOSS, MMNN, ROOE, BBOO, BTOS, NPSG, NOSU, KODC, LLOO, LLTT, LLEE ransomware versions may not be uploaded to the Emsisoft’s server yet.
For these versions, the tool may be capable to decrypt files locked by OFFLINE key only (if Emsisoft’s server contains the key for the variant that affected your files). Keep in mind that these decryption keys may take a while to emerge, so the very last versions such as .pouu or .poqw might not be decryptable at the moment.
IMPORTANT. Due to victim confidentiality, Emsisoft no longer announces when new offline keys are uploaded to their server, so in order to find out whether your files can be decrypted, you need to download Emsisoft Decryptor and run a scan with it.
Please note that you must remove DJVU ransomware virus remains before you try to recover your files. We strongly recommend using a robust antivirus like INTEGO Antivirus for this task. In addition, we strongly recommend scanning with RESTORO to repair virus damage on Windows OS files.

Intego Antivirus for Windows
Award-winning antivirus solution for your PC.
Robust security software that provides robust 24/7 real-time protection, Web Shield that stops online threats/malicious downloads, and Prevention engine that wards off Zero-Day threats. Keep your PC safe and protected against ransomware, Trojans, viruses, spyware and other forms of dangerous programs.
Before you proceed into the article, check the list of supported extensions to determine whether you can decrypt STOP DJVU files.
Please remember that some versions can be decrypted only if offline key was used. If your files were affected with online key and the decryption is impossible, you will see the following message: No key for New Variant.
Before we dive into the solutions on how to decrypt your files, we suggest overviewing STOP/DJVU variants and the chances on recovering your files so that you would know what to expect and which tools to use.
STOP/DJVU ransomware variants and chances to recover data
STOP/DJVU versions are generally categorized into 4 types and each of them have different level of decryptability.
- Puma variants (.puma, .pumax, pumas). All versions can be decrypted after providing one encrypted/original file pair exceeding 150KB in size. Victims should use STOP Puma decryptor as explained in method 3.
- Uppercase variants (.INFOWAIT, .DATAWAIT, .KEYPASS and others). For these variants, only some of them can be decrypted, again using STOP Puma decryptor given that a pair of encrypted/original file pair exeeding 150KB is provided. See method 3 for instructions.
- Old variants (.djvu, .djvuu, .udjvu, .uudjvu, .djvuq and others). These variants are known to increase encrypted file size by 78 bytes. Files with all known extensions of these old STOP/DJVU can be decrypted using STOP/DJVU Decryptor in these cases: if offline encryption was used and if the victim can provide some encrypted/original file pairs exceeding 150KB in size. Offline encryption victims should see Method 1: Decrypt files locked with OFFLINE Key section and those affected by online encryption should refer to Method 2: Decrypt files encrypted with ONLINE Key section.
- New variants (.poqw, .pouu, .bnto, zoqw and others). All ransomware variants that started emerging in August 2019 and continue to appear nowadays. The encrypted files usually appear to be 334 bytes larger once encrypted. These versions can only be decrypted if offline encryption was used, so in such case, you should refer to Method 1: Decrypt files locked with OFFLINE Key section.
Before you explore methods to decrypt your files, you need to determine whether online or offline key was used to lock your files.
How to check if online or offline key was used in encryption
The updated ransomware encrypts files using online keys (different for each victim) if it manages to connect to its Command & Control Server during the attack. Otherwise, it uses an offline key, which is the same one for all victims of one ransomware variant (with the same extension).
If an offline key was used, you have chances to restore data now or in the near future. Unfortunately, we cannot say the same about victims affected by the online keys.
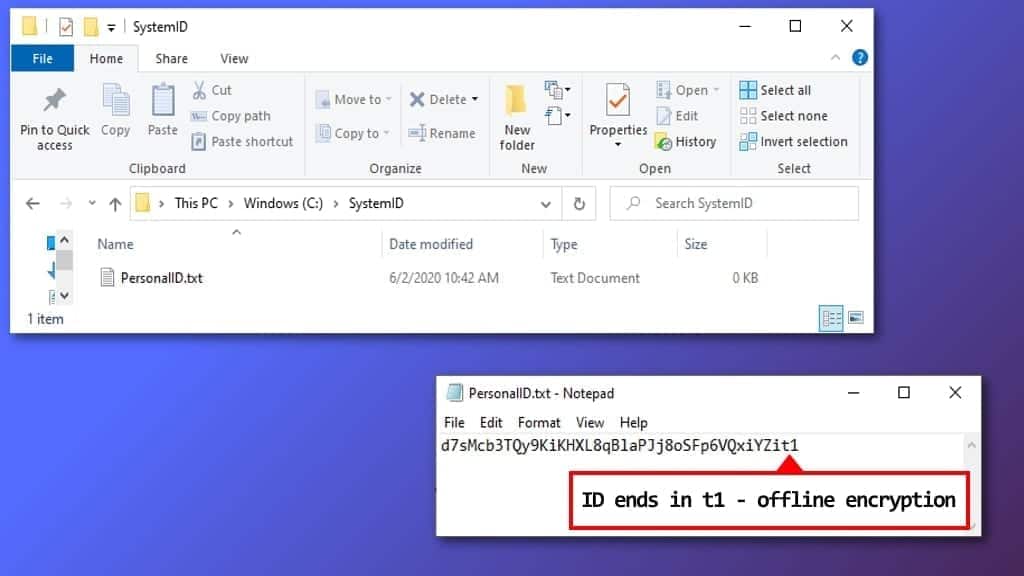
To determine what keys were used, follow these steps.
- Go to C: disk and then open SystemID folder.
- Here, open PersonalID.txt file and look at the keys listed here.
- If ANY of them end with t1, it means you can recover at least part of the data using STOP Decryptor.
Another simple method to determine what encryption type was used by ransomware on your computer is to simply run Emsisoft’s STOP/DJVU Decryptor.
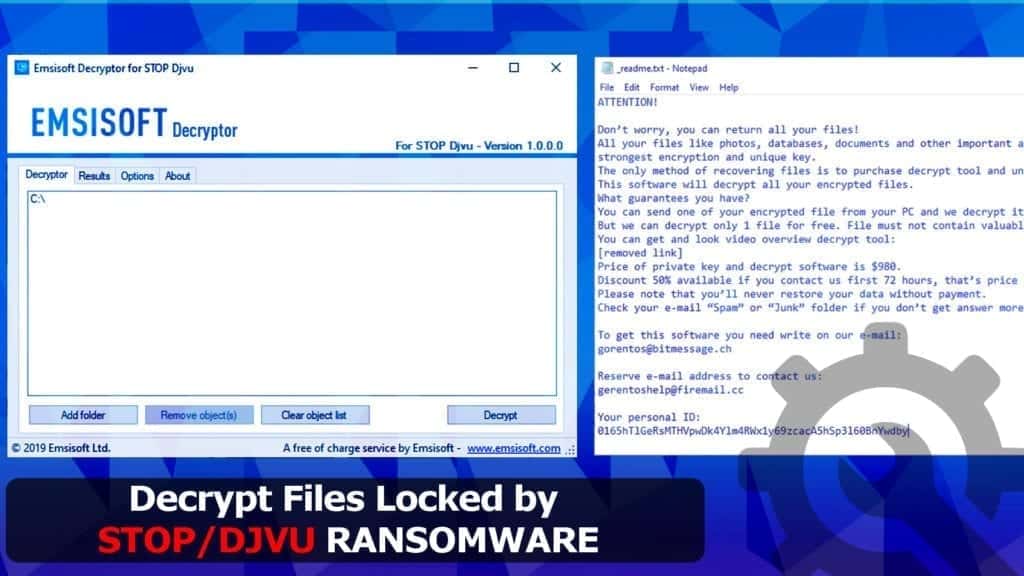
Decrypt Files Locked by STOP/DJVU Ransomware
See the guide below on how to decrypt DJVU files using the decrypted by Emsisoft. This guide explains how to decrypt files locked by OFFLINE and ONLINE keys. Please check the next part of the tutorial if you’re infected with .puma, .pumax or .pumas variant.
Method 1. Decrypt Files Locked With OFFLINE Key
The guide described below helps to decrypt files locked with OFFLINE key for all DJVU ransomware versions created prior to August 2019.
Victims of these versions received ransom notes called _readme.txt with such contents. Please note that new versions like .nypd or .zwer use new contact emails: helpmanager@mail.ch or restoreadmin@firemail.cc.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
[removed link]
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
gorentos@bitmessage.ch
Reserve e-mail address to contact us:
gerentoshelp@firemail.cc
Your personal ID:
9315hTlGeRsMht5nsgsaoejm4RWx1y69zcacA5hSp3l60BnY8f3q
asd3SGd8723bqD7SH8JmYm298WxkjhasiuSDFS35Qaidkhantjt1
If you were attacked with both ONLINE and OFFLINE keys, complete these steps and proceed to the next part of the tutorial.
- Download STOP/DJVU Decryptor.
- Open the decryptor. You will have to click Yes in User Account Control window.
- Agree to License Terms by clicking Yes.
- Next, add locations to decrypt by clicking Add Folder and selecting locations from your computer. By default, C:\ partition is added.
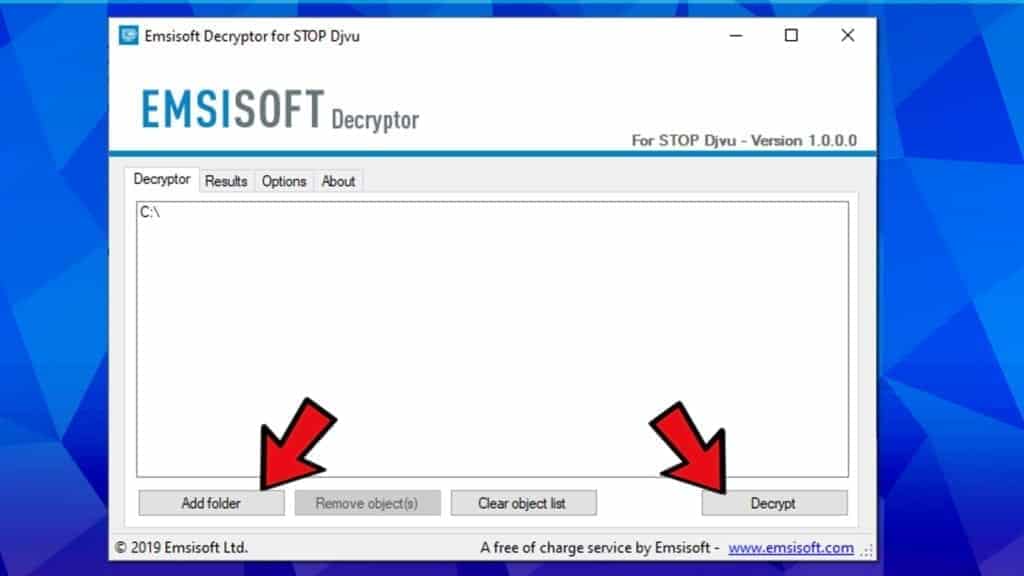
- Click Decrypt to start decrypting your files.
Method 2. Decrypt Files Encrypted with ONLINE KEY
This method works for old STOP/DJVU versions and requires collecting encrypted/original file samples for each data format you’re trying to recover. The decryptable ransomware variants based on extensions used are listed below.
Known decryptable DJVU virus extensions list (using file pairs method)
.shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote
There are three requirements for file pairs:
- Must be at least 150Kb in size;
- Must be the same file that was encrypted;
- To decrypt different file types, you need file pairs for them, for example, .jpg, .doc, .mp3, etc.
How to find data pairs
An easy way to find some pairs is to check encrypted files in your downloads and trace the source where you downloaded them from. For instance, if you have downloaded some files from email or specific website recently, you can download a copy from email and check for encrypted version in your downloads.
Your downloads are likely to contain various file types that you have downloaded from the Internet. Try to remember exactly where you got them from so that you could download them again and have data pairs for as many different file extensions as possible.
For example, you need image.jpg to pair with image.jpg.reco, video.mp4 to pair with video.mp3.reco, and so on.
As soon as you have some pairs of encrypted and original files, follow the steps below to decrypt files locked by STOP/DJVU ransomware.
- Upload a pair of original and encrypted files via Emsisoft Decryption page and click SUBMIT. The form will inform you if you’re uploading too small files.
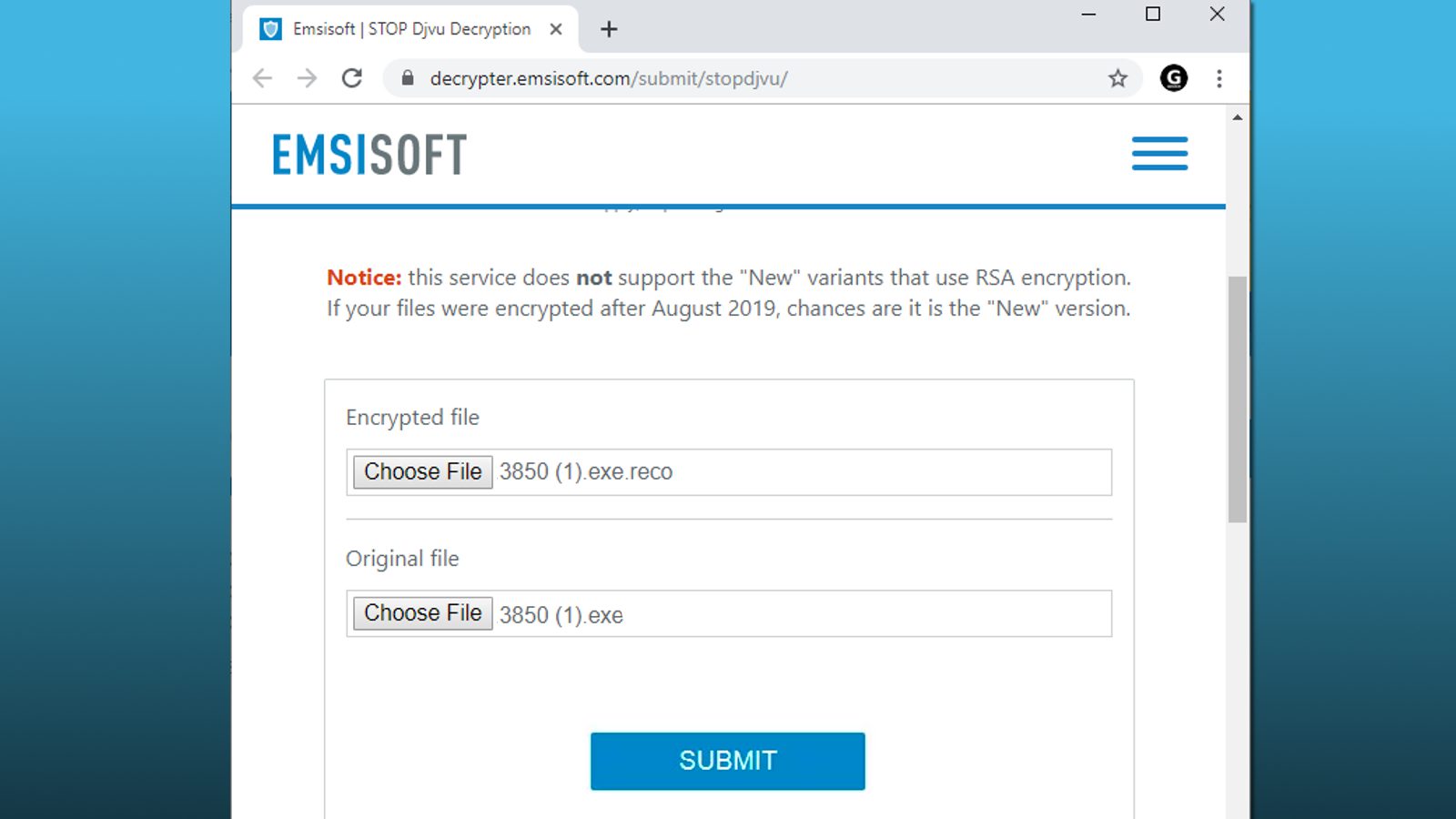
- Once you click SUBMIT, wait patiently until your files are processed.
- At this point, you will be provided with STOP/DJVU decrypt tool download link. Download it and, once complete, open it.
- In UAC prompt, press Yes.
- Next, click Add folder and choose file locations you want to scan and decrypt files with specific file extension.

- Click Decrypt.
- If the decryptor won’t be capable of recovering specific file types, train it by uploading another file pair to the link provided in Step#1. Repeat with different file type pairs until you restore as many files as possible.
Method 3. Decrypt .puma, .pumas, .pumax, .INFOWAIT, .DATAWAIT files
Victims whose files were infected with .puma, .pumax, .pumas, .INFOWAIT and .DATAWAIT ransomware versions can use STOP Puma decrypter to recover their files.
Victims of this ransomware variants received ransom notes called !readme.txt with such contents:
================ !ATTENTION PLEASE! ================
Your databases, files, photos, documents and other important files are encrypted and have the extension: .puma
The only method of recovering files is to purchase an decrypt software and unique private key.
After purchase you will start decrypt software, enter your unique private key and it will decrypt all your data.
Only we can give you this key and only we can recover your files.
You need to contact us by e-mail pumarestore@india.com send us your personal ID and wait for further instructions.
For you to be sure, that we can decrypt your files – you can send us a 1-3 any not very big encrypted files and we will send you back it in a original form FREE.
Discount 50% avaliable if you contact us first 72 hours. =========================================
E-mail address to contact us: pumarestore@india.com
Reserve e-mail address to contact us:
BM-2cXonzj9ovn5qdX2MrwMK4j3qCquXBKo4h@bitmessage.ch Your personal id: 3346se9RaIxXF9m45nsmx7nL3bVudn91w4SNY8URDVa
To Decrypt files locked by STOP/DJVU Puma variants, follow these instructions:
- Create file pairs as explained in Method#2.
- Download DJVU Puma Decryptor by Emsisoft.
- Open the decryptor and click Yes in the User Account Control prompt.
- Agree with Terms Of Use.
- Upload encrypted and original file copies to the decryptor and, if required, ransom note file. Click Start.
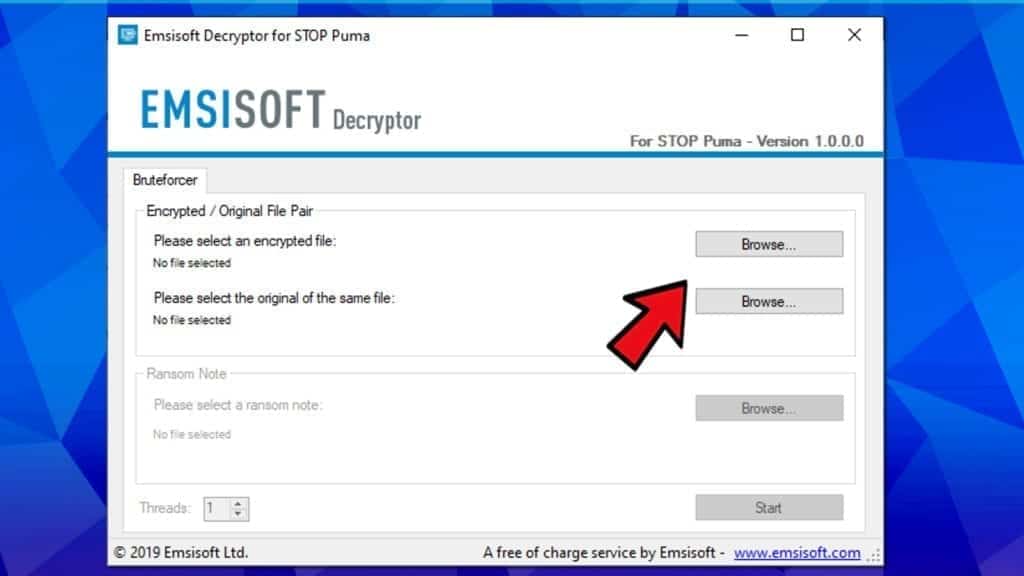
- The STOP/DJVU Decryptor will display decryption details. Press OK.
- Choose Add folder and choose to include files, locations or simply partitions to scan and recover locked files.
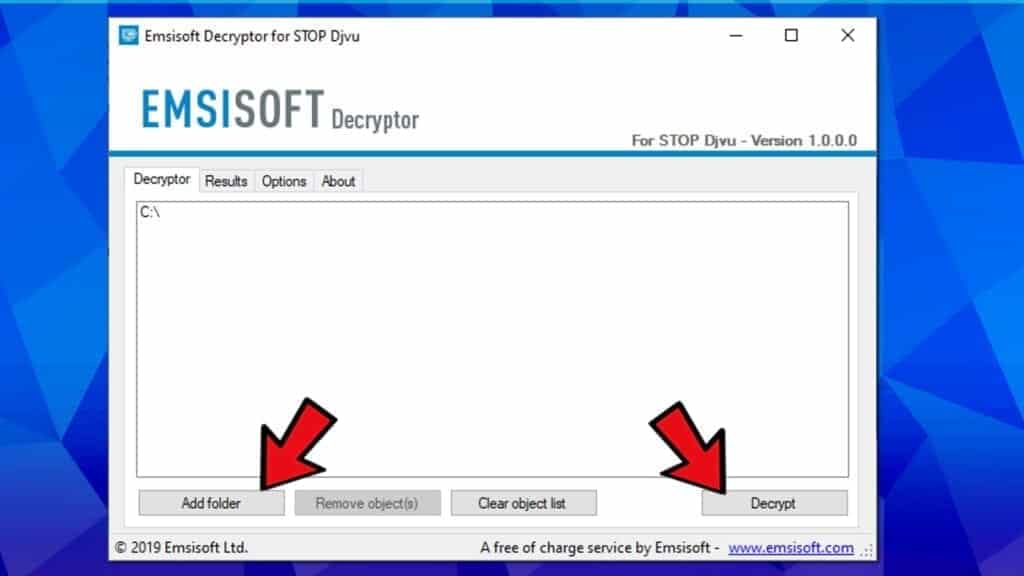
- Click Decrypt.
BONUS: REPAIR files encrypted by STOP/DJVU
Repair audio/video files using Media_Repair by DiskTuna
Media_Repair by DiskTuna is a free and secure tool that can help to repair a limited range of encrypted files. Since DJVU ransomware encrypts only 150kb of the files, Media_Repair attempts to fix them by making the non-encrypted part of the file playable again. The tool isn’t meant to decrypt the files. Currently, the software is capable of repairing file types listed below. Please pay attention that for formats marked with *, a reference file is required.
- WAV*;
- MP3;
- MP4*;
- M4V*;
- MOV*;
- 3GP*.
Just like Emsisoft’s tool, Media_Repair requires a reference file, in other words, a full, unaffected example file created on the same device or with the same software. That said, if you had videos encrypted that were shot with your camera, you should use the same settings used to create that video to create a reference video file for file repair. Same example goes with video editing software – try to duplicate video settings used to create a specific video you had encrypted.
Please be aware that the tool won’t be capable of fixing absolutely all kinds of files. For example, videos optimized for online streaming (fast start), can’t be repaired at the moment. The tool is also known to fail with large files, although this issue is likely to be fixed in future updates.
Media_Repair was made available thanks to researchers Nguyễn Vũ Hà and Joep van Steen.
How to use Media_Repair to fix encrypted files
Please follow the given steps carefully to attempt encrypted file repair using Media_Repair.
- Download the tool from DiskTuna (official download link).
- Open the location of the downloaded file, then right-click it and choose Extract to Media_Repair\.
- Double-click the Media_Repair.exe file.
- First, select file type you’re trying to repair.
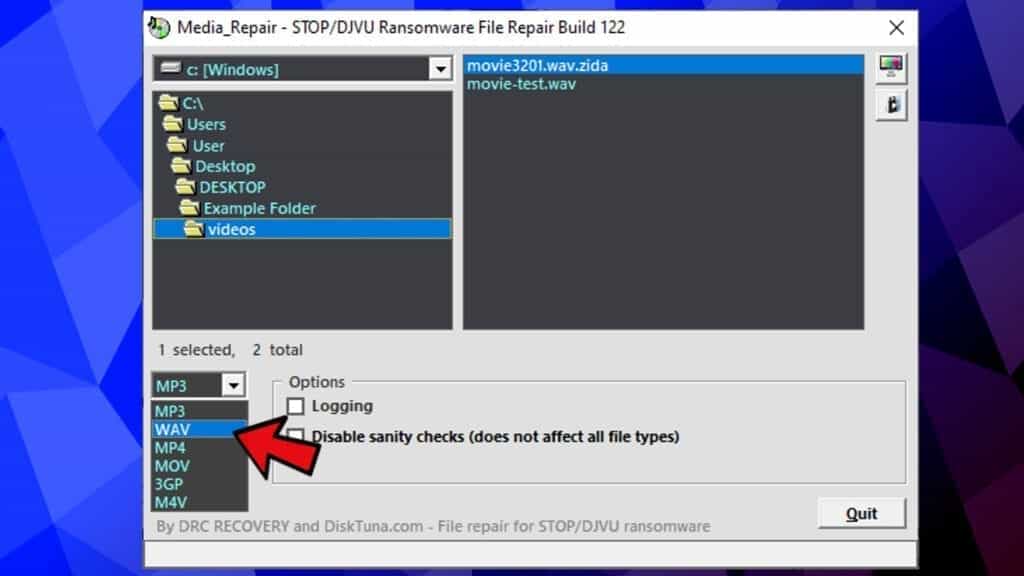
- Then, browse to the folder containing encrypted files or the reference file. You can use one or another to see whether the tool will succeed in repairing desired files.
- Click the Test button in the upper right corner to see if the file can be repaired.
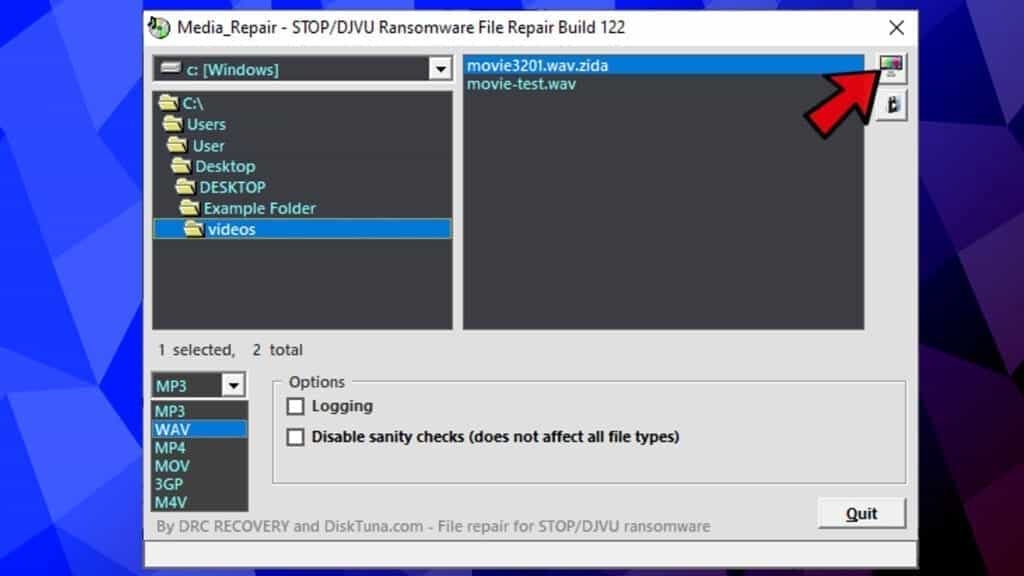 At this point, the repair success depends on several factors. Even if the tool repairs that the file can be fixed, it does not immediately guarantee the success.
At this point, the repair success depends on several factors. Even if the tool repairs that the file can be fixed, it does not immediately guarantee the success.
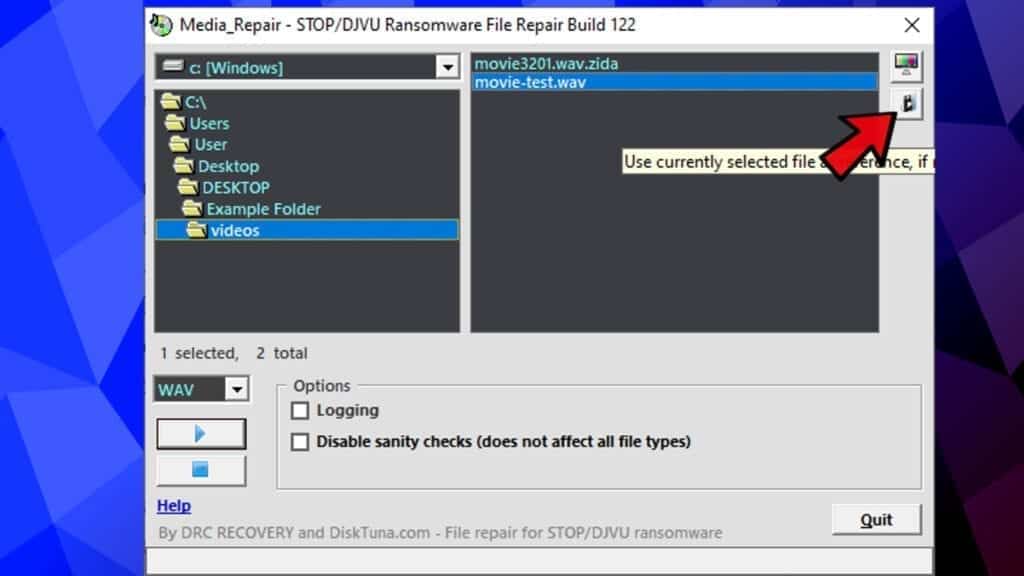
It depends on things such as the example correctness as the reference file and the size of the encrypted file. In case you receive a message that the file can’t be repaired, then most likely it can’t. - Now, select the reference file, and click the second button in the upper right corner. This will confirm the reference file to be used for corrupt data fixing. Please proceed only after the tool tells you that file pair is correct in step #6.
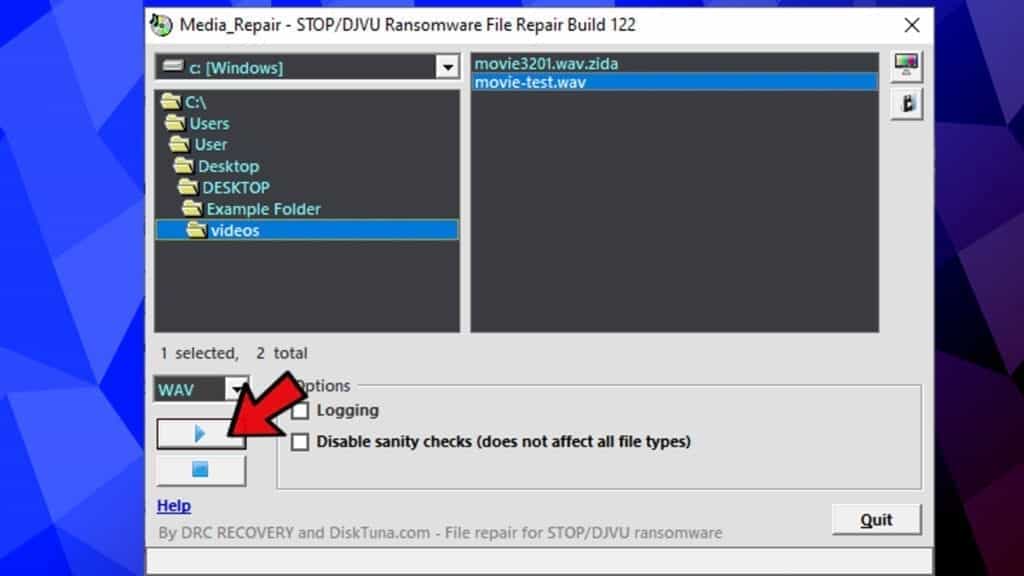
- Click the Play button to start repairing. If you wish to stop, click the Stop button to cancel the repair.
Important things to know about the repair tool:
- You must have a reference file. If you do not have it or can create it, no one else can make it for you.
- If you do not know the settings used to create the encrypted file, unfortunately, no one else will. Try experimenting and creating different reference files, then try the repair tool again.
- More supported file formats might be available in the future, although this is not promised.
- Please remember that the tool repairs the files, but doesn’t decrypt them. Some information loss might be expected;
- It doesn’t matter whether online or offline encryption was used by the ransomware, you can try the tool on the listed file formats.
- For more information about Media_Repair, please visit its developer’s website.
We hope that you found this tutorial helpful and you managed to decrypt files infected by DJVU ransomware successfully. We strongly recommend you to read ransomware prevention tips to avoid similar malware attacks in the future.

Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Since how my information is encrypted 2020 December, I still looking for a decryptor for SGLH. All my important documents were encrypted with this extension, including my own projects that I have been developing for many years… and in just a moment it was all locked with SGLH… I have been looking for a decryptor for 2 years now, but so far I can’t find it… Also the encryption was done with an online key… So I hope someone can help.
Hello friends
The extension of all the files on my laptop has been changed to avyu.
Encrypting is online. Can anyone help?
thank you
How can decrypt ransomware ZATP? Please provide any guideline and decryptor
My file in both PC and external hard disk is infected by .dkrf, can anyone help or give any suggestion on how to solve and get my files back? I got a few TBs of files affected, please help. Thank you.
(Invalid file pair; file encrypted by newer version of STOP Djvu)
this is the message i receive whine i send the encrypted and original flies
it also affected my 1 TB disk with the extension qqjj and it cannot be restored
How can decrypt ransomware QSCX? Please provide any guideline and decryptor
My file in both PC and external hard disk is infected by .dkrf, can anyone help or give any suggestion on how to solve and get my files back? I got a few TBs of files affected, please help. Thank you.
last 1/1.55 years i didnt find any tools for retrivieng my files.
please help me.
Error: No key for New Variant online ID: [removed for privacy reasons]
orkf